Secure CRT 7.0远程Kali 2020版本时,报错
Key exchange failed. No compatible key exchange method. The server supports these methods: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256
错误原因是SecureCRT 7.0客户端支持的和kali作为ssh服务端支持的SSH秘钥交换算法不匹配。
Secure CRT 7.0的默认支持key exchange算法:
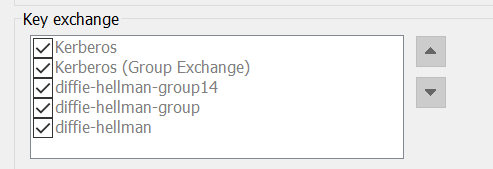

显然是不在Kali 2020版本默认支持的dh-g1-sha256,dh-g16-sha512,dh-g18-sha512,dh-g14-sha256这些组合范围内的。
处理办法
修改/etc/ssh/sshd_config配置文件,增加如下一行,使新版本的Kali Linux支持老版本的秘钥交换算法。
KexAlgorithms curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha1,diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1
补充内容
查看服务器支持的秘钥交换算法
nmap --script ssh2-enum-algos -sV -p <port> <host>
root@kali:~# nmap --script ssh2-enum-algos -sV -p 22 localhost Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-10 02:08 CDT Nmap scan report for localhost (127.0.0.1) Host is up (0.000064s latency). Other addresses for localhost (not scanned): ::1 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.3p1 Debian 1 (protocol 2.0) | ssh2-enum-algos: | kex_algorithms: (8) | curve25519-sha256@libssh.org | ecdh-sha2-nistp256 | ecdh-sha2-nistp384 | ecdh-sha2-nistp521 | diffie-hellman-group-exchange-sha256 | diffie-hellman-group14-sha1 | diffie-hellman-group-exchange-sha1 | diffie-hellman-group1-sha1 | server_host_key_algorithms: (5) | rsa-sha2-512 | rsa-sha2-256 | ssh-rsa | ecdsa-sha2-nistp256 | ssh-ed25519 | encryption_algorithms: (6) | chacha20-poly1305@openssh.com | aes128-ctr | aes192-ctr | aes256-ctr | aes128-gcm@openssh.com | aes256-gcm@openssh.com | mac_algorithms: (10) | umac-64-etm@openssh.com | umac-128-etm@openssh.com | hmac-sha2-256-etm@openssh.com | hmac-sha2-512-etm@openssh.com | hmac-sha1-etm@openssh.com | umac-64@openssh.com | umac-128@openssh.com | hmac-sha2-256 | hmac-sha2-512 | hmac-sha1 | compression_algorithms: (2) | none |_ zlib@openssh.com Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel