71. Your database instance is started using the server parameter file (SPFILE). Control files are multiplexed and stored on different disks. Because of a disk failure, you lost one of these control files. You replaced the damaged disk. What is the correct sequence of steps that you would follow to recover the control file?
1. shut down the instance, if not already done.
2. Copy one of the remaining control files to a new location.
3. Change the value of the CONTROL_FILES initialization parameter to correspond to the new location of the control files.
4. Start up the database instance to the NOMOUNT stage.
5. Recover the database to the point of failure of the control file.
6. Open the database.
A) 5,2,3,4
B) 1, 2,4,3,5
C) 2, 4,3,4,5
D) 4, 5,6,2,3
答案:B
72. The SAVE_AMT column in the ACCOUNTS table contains the balance details of customers in a bank. As part of the year-end tax and interest calculation process, all the rows in the table need to be accessed. The bank authorities want to track access to the rows containing balance amounts exceeding $200,000, and then send an alert message to the administrator. Which method would you suggest to the bank for achieving this task?
A) implementing value-based auditing by using triggers
B) implementing fine-grained auditing with audit condition and event handler
C) performing standard database auditing to audit object privileges by setting the AUDIT_TRAIL parameter to EXTENDED
D) performing standard database auditing to audit SQL statements with granularity level set to ACCESS
答案:B
73. The user SCOTT executes the following command successfully to increase the salary values in one of his sessions:
SQL> UPDATE emp SET sal=sal*1.15 WHERE deptno=20;
Before SCOTT ends the transaction, user HR who has the privileges on EMP table executes a query to fetch the salary details but finds the old salary values instead of the increased values.
Why does HR still see the old data?
A) because of redo data from redo log file
B) because of data from database buffer cache
C) because of data from a temporary tablespace
D) because of undo data from the undo tablespace
答案:D
74. View the Exhibit and examine the output.

Which statement describes the conclusion?
A) The users should use bind variables instead of literals in the query.
B) The dictionary cache is consuming more space than the library cache.
C) The shared pool size should be increased to accommodate the SQL statements.
D) Preparing indexes on the tables used in the SQL statements would improve the library cache performance.
答案:A
Oracle 绑定变量
http://blog.csdn.net/tianlesoftware/archive/2009/10/17/4678335.aspx
75. In your database, the Log Writer (LGWR) process is unable to write to a member of a current redo log group due to read/write failure. Which two effects would you see in your database? (Choose two.)
A) The database instance aborts.
B) The database operation temporarily halts till the member becomes available.
C) Writing proceeds as normal. LGWR writes to the available members of a group and ignores the unavailable members.
D) The member would be marked as STALE and an error message would be written to the alert log file and LGWR trace file.
E) The status of the group changes to INACTIVE and an error message would be written to the alert log file and LGWR trace file.
答案:CD
76. Your database is not configured for session failover. Your tnsnames.ora file contains the following details:
test.us.oracle.com=
(DESCRIPTION=
(ADDRESS_LIST=
(LOAD_BALANCE=off)
(FAILOVER=ON)
(ADDRESS= (PROTOCOL=tcp) (HOST=test1-server) (PORT=1521))
(ADDRESS= (PROTOCOL=tcp) (HOST=test2-server) (PORT=1521)))
(CONNECT_DATA= (SERVICE_NAME=test.us.oracle.com)))
Which feature is enabled in this case?
A) Load balancing
B) Instance failover
C) Database failover
D) Connect-time failover
E) Transparent Application Failover (TAF)
答案:D
77. On which three can you use Recovery Manager (RMAN) to perform incremental backup? (Choose three.)
A) data files
B) control files
C) tablespaces
D) password file
E) parameter file
F) whole database
G) flashback log file
H) archived log files
I) change tracking file
答案:ACF
78. You define an alert to be raised when the USERS tablespace usage has reached 80% of the total space.
Which area would you refer to, in order to confirm that the alert has been raised due the event?
A) the alert.log file
B) the DBA_ALERTS view
C) the Database Control Home page
D) the Database Control performance page
E) the Database Control Maintenance page
答案:C
79. A user complains that he gets the following error message repeatedly after executing some SQL statements. The error message forces the user to log off from and log on to the database to continue his work.
ORA-02392: exceeded session limit on CPU usage, you are being logged off
Which action would you take to increase the session limit on CPU usage?
A) Modify the profile assigned to the user.
B) Modify the roles assigned to the users.
C) Modify the object privileges assigned to the user.
D) Modify the system privileges assigned to the users.
E) Modify the value for the RESOURCE_LIMIT parameter in the parameter file.
答案:A
80. You execute the following command to audit the database activities:
SQL> AUDIT DROP ANY TABLE BY scott BY SESSION WHENEVER SUCCESSFUL;
What is the effect of this command?
A) One audit record is created for the whole session if user SCOTT successfully drops one or more tables in his session.
B) One audit record is created for every session when any user successfully drops a table owned by SCOTT.
C) One audit record is created for each successful DROP TABLE command executed by any user to drop tables owned by SCOTT.
D) One audit record is generated for the session when SCOTT grants the DROP ANY TABLE privilege to other users in his session.
E) One audit record is created for each successful DROP TABLE command executed in the session of SCOTT.
答案:A
81. Which three descriptions are correct about the effects of the TRUNCATE command on a table? (Choose three.)
A) The corresponding indexes for the table are also truncated.
B) Delete triggers on the table are fired during the execution of the TRUNCATE command.
C) Very little or no undo data is generated during the execution of the TRUNCATE command.
D) The child table is truncated when the TRUNCATE command is applied on the parent table.
E) The high-water mark (HWM) is set to point to the first useable data block in the table segment.
答案:ACE
If table is not empty, then the database marks UNUSABLE all nonpartitioned indexes and all partitions of global partitioned indexes on the table. However, when the table is truncated, the index is also truncated, and a new high water mark is calculated for the index segment. This operation is equivalent to creating a new segment for the index. Therefore, at the end of the truncate operation, the indexes are once again USABLE.
http://download.oracle.com/docs/cd/E11882_01/server.112/e10592/statements_10007.htm#SQLRF01707
82. Which is the correct description of the significance of the ORACLE_HOME environmental variable?
A) It specifies the directory containing the Oracle software.
B) It specifies the directory containing the Oracle-Managed Files.
C) It specifies the directory for database files, if not specified explicitly.
D) It specifies the base directory of Optimal Flexible Architecture (OFA) .
答案:A
83. Your test database is running in NOARCHIVELOG mode. What are the implications of this?
A) You can perform open database backups.
B) You can perform closed database backups.
C) You cannot perform schema-level logical backups.
D) You can perform the backup of only the SYSTEM tablespace when the database is open.
答案:B
84. View the Exhibit to observe the roles assigned to the SCOTT user.
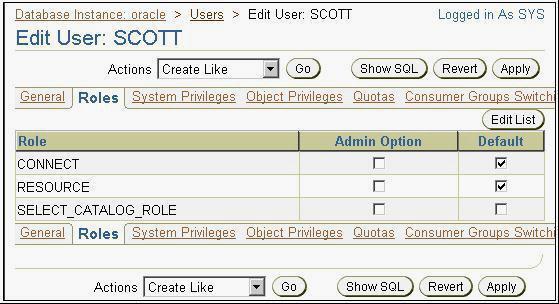
Which statement is true about the assignment of the SELECT_CATALOG_ROLE role to the SCOTT user?
A) The user cannot use the role at all.
B) The user can grant the role to other users.
C) The user needs to enable the role explicitly.
D) The user can start using the role immediately.
答案: C
85. You are using flat files as the data source for one of your data warehousing applications. You plan to move the data from the flat file structures to an Oracle database to optimize the application performance. In your database you have clustered tables. While migrating the data, you want to have minimal impact on the database performance and optimize the data load operation. Which method would you use to load data into Oracle database?
A) use the external table population
B) use the Oracle Data Pump export and import utility
C) use the conventional path data load of SQL*Loader utility
D) use the direct path data load of Oracle export and import utility
答案:C
86. You are working on a database created with the Oracle Database 10g software in which the initialization parameter COMPATIBLE is set to 10.0.0. The hr_tbs tablespace in the database is created as follows:
CREATE TABLESPACE hr_tbs DATAFILE '/oracle/oradata/hr_tbs.dbf' SIZE 50M;
View the Exhibit to see the properties of the database.

Which statement is correct in this scenario?
A) hr_tbs is a bigfile tablespace.
B) hr_tbs is a dictionary-managed tablespace.
C) All the tablespaces in the database will be locally managed by default.
D) All the tablespaces in the database must be of the smallfile tablespace type.
E) The tablespace type bigfile or smallfile must be mentioned in the command.
答案:C
87. View the Exhibit and analyze the CREATE TABLE statements used to create the ITEMS and ORDERS tables. The ITEMS table has 50 rows and ORDERS table has 500 rows. Because you decide to not deal with the item code 188 in future, you execute the following command to remove the item:
SQL> DELETE FROM items WHERE item_code=188;

What is the effect of this command?
A) The command fails with integrity violation error.
B) The row containing the value 188 corresponding to the ITEM_CODE column is deleted from the ITEMS table, and the foreign key constraint is disabled in the ORDERS table.
C) The row containing the value 188 corresponding to the ITEM_CODE column is deleted from the ITEMS table, and the dependent rows in the ORDERS table are also deleted automatically.
D) The row containing the value 188 corresponding to the ITEM_CODE column is deleted from the ITEMS table, and the dependent rows in the ORDERS table are populated with NULL values in their ITEM_CODE columns.
答案: C
88. A user receives the following error while executing a query:
ORA-01555: snapshot too old
Which two options can be the solutions to avoid such errors in future? (Choose two.)
A) increase the size of redo log files
B) increase the size of the undo tablespace
C) increase the size of the Database Buffer Cache
D) increase the size of the default temporary tablespace
E) enable the retention guarantee for the undo tablespace
答案:BE
Oracle ORA-01555快照过旧
http://blog.csdn.net/tianlesoftware/archive/2009/10/31/4745898.aspx
89. You have a text file that maintains information on thousands of items. The end-user application requires the transfer of that information into a table in the database. What would you use to achieve this task? (Choose two.)
A) Oracle Text
B) Data Pump
C) SQL*Loader
D) Oracle Import
E) External table
答案:CE
90. Redo log files are not multiplexed in your database. Redo log blocks are corrupted in group 2, and archiving has stopped. All the redo logs are filled and database activity is halted. Database writer has written everything to disk.
Which command would you execute to proceed further?
A) RECOVER LOGFILE BLOCK GROUP 2;
B) ALTER DATABASE DROP LOGFILE GROUP 2;
C) ALTER DATABASE CLEAR LOGFILE GROUP 2;
D) ALTER DATABASE RECOVER LOGFILE GROUP 2;
E) ALTER DATABASE CLEAR UNARCHIVED LOGFILE GROUP 2;
答案:E
91. Your database is open and you plan to perform Recovery Manager (RMAN) backups. Which three statements are true about these backups? (Choose three.)
A) The backups would be consistent.
B) The backups would be inconsistent.
C) The backups need to be restored and database has to be recovered in case of a media failure.
D) The backups need not be restored during recovery in case of a media failure.
E) The backups would be possible only if the database is running in ARCHIVELOG mode.
F) The backups would be possible only if the database is running in NOARCHIVELOG mode.
答案:BCE
92. You want the user APP_DBA to administer the Oracle database from a remote machine. APP_DBA is granted the SYSDBA privilege to perform administrative tasks on the database.
Which file is used by the Oracle database server to authenticate APP_DBA?
A) control file
B) password file
C) listener controller file
D) control file and password file
答案:B
Sysdba的密码是保存在密码文件中的。
93. Your database is having two control files, three redo log file groups with two members in each group. Failure of which file would cause an instance to shut down?
A) any control file
B) any archive log file
C) one of the redo log members
D) loss of the initialization parameter file
E) any data file belonging to the default permanent tablespace
答案:A
94. The UNDO_RETENTION parameter in your database is set to 1000 and undo retention is not guaranteed.
Which statement regarding retention of undo data is correct?
A) Undo data becomes obsolete after 1,000 seconds.
B) Undo data gets refreshed after every 1,000 seconds.
C) Undo data will be stored permanently after 1,000 seconds.
D) Committed undo data would be retained for 1,000 seconds if free undo space is available.
E) Undo data will be retained in the UNDO tablespace for 1,000 seconds, then it gets moved to the TEMPORARY tablespace to provide read consistency.
答案:D
Oracle undo 表空间管理
http://blog.csdn.net/tianlesoftware/archive/2010/07/11/5689558.aspx
95. Your database is functional with peak load for one hour. You want to preserve the performance statistics collected during this period so that they can be used for comparison while analyzing the performance of the database in the future. What action would you take to achieve this task?
A) Set the STATISTICS_LEVEL initialization parameter to ALL.
B) Create a baseline on a pair of snapshots that have the statistics of the peak-load period in the database.
C) Decrease the snapshot interval in the AWR to collect more number of snapshots during the peak-load period.
D) Set the snapshot retention period in the Automatic Workload Repository (AWR) to zero to avoid the automatic purging of the snapshots.
答案:B
96. Which statement is true when you run the SQL Tuning Advisor with limited scope?
A) Access path analysis is not performed for the SQL statements.
B) SQL structure analysis is not performed for the SQL statements.
C) SQL Profile recommendations are not generated for the SQL statements.
D) The staleness and absence of the statistics are not checked for the objects in the query supplied to the SQL Tuning Advisor.
答案:C
97. You specified segment space management as automatic for a tablespace. What effect would this have on space management?
A) Extents would be managed by the freelists.
B) The segment would be managed by bitmaps.
C) The segment would be managed by the freelists.
D) Free space would be managed by the data dictionary.
答案:B
98. Which two statements about bigfile tablespaces are true? (Choose two.)
A) The bigfile tablespace have only one data file.
B) The segment space management is automatic.
C) The extent management is dictionary managed.
D) The database can have only one bigfile tablespace.
E) The bigfile tablespace can be converted to a smallfile tablespace.
答案:AB
99. You want to set up the Oracle Database 10g installation to follow the French language, with France as the territory, and the date to be displayed in French for all users' sessions. Which environmental variable would you set to achieve this objective?
A) NLS_LANG
B) NLS_LANGUAGE
C) NLS_TERRITORY
D) NLS_CHARACTERSET
E) NLS_DATE_LANGUAGE
F) NLS_LENGTH_SEMANTICS
G) NLS_NCHAR_CHARACTERSET
答案:A
Oracle 字符集的查看和修改
http://blog.csdn.net/tianlesoftware/archive/2009/12/02/4915223.aspx
100. You want to refer the employee personal information stored in operating system(OS) files in EMPLOYEE table. You plan to add a new column to EMPLOYEE table to achieve this.
Which data type would you use for the new column?
A) BLOB
B) CLOB
C) BFILE
D) LONG RAW
答案: C
The BFILE data type enables access to binary file LOBs that are stored in file systems outside Oracle Database. A BFILE column or attribute stores a BFILE locator, which serves as a pointer to a binary file on the server file system. The locator maintains the directory name and the filename.
http://download.oracle.com/docs/cd/E11882_01/server.112/e10592/sql_elements001.htm#SQLRF50996
101. View the Exhibit.
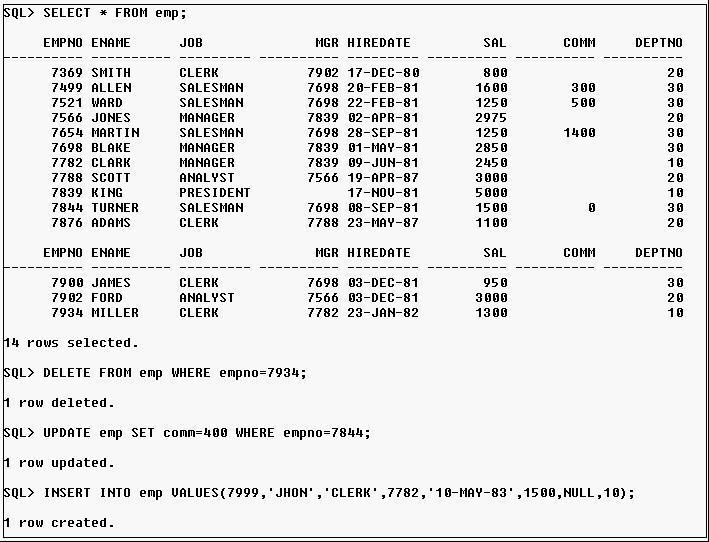
Which statement causes more undo generation?
A) SELECT * FROM emp;
B) DELETE FROM emp WHERE empno=7934;
C) UPDATE emp SET comm=400 WHERE empno=7844;
D) INSERT INTO emp VALUES (7999,'JHON','CLERK', 7782,'10-MAY-83', 1500, NULL, 10);
答案:B
102. In which situation would you use the Oracle Shared Server configuration?
A) when performing export and import using Oracle Data Pump
B) when performing backup and recovery operations using Oracle Recovery Manager
C) when performing batch processing and bulk loading operation in a data warehouse environment
D) in an online transaction processing (OLTP) system where large number of client sessions are idle most of the time
答案:D
103. The session of user SCOTT receives the following error after executing an UPDATE command on the EMP table:
ERROR at line 1:
ORA-00060: deadlock detected while waiting for resource
On investigation, you find that a session opened by user JIM has a transaction that caused the deadlock.
Which two statements are true regarding the session of SCOTT in this scenario? (Choose two.)
A) It is terminated after receiving the error and JIM can continue with his transaction.
B) The transaction in it is terminated after receiving the error and JIM can continue with his transaction.
C) SCOTT should perform a COMMIT or ROLLBACK to allow JIM to continue with his transaction.
D) SCOTT has to reexecute the last command in the transaction after he commits the transaction.
答案:CD
104. A constraint in a table is defined with the INITIALLY IMMEDIATE clause. You executed the ALTER TABLE command with the ENABLE VALIDATE option to enable the constraint that was disabled. What are the two effects of this command? (Choose two.)
A) It fails if any existing row violates the constraint.
B) It does not validate the existing data in the table.
C) It enables the constraint to be enforced at the end of each transaction.
D) It prevents insert, update, and delete operations on the table while the constraint is in the process of being enabled.
答案:AD
The INITIALLY clause establishes the default checking behavior for constraints that are DEFERRABLE. The INITIALLY setting can be overridden by a SET CONSTRAINT(S) statement in a subsequent transaction.
Specify INITIALLY IMMEDIATE to indicate that Oracle should check this constraint at the end of each subsequent SQL statement. If you do not specify INITIALLY at all, then the default is INITIALLY IMMEDIATE.
If you declare a new constraint INITIALLY IMMEDIATE, then it must be valid at the time the CREATE TABLE or ALTER TABLE statement is committed or the statement will fail.
Specify INITIALLY DEFERRED to indicate that Oracle should check this constraint at the end of subsequent transactions.
This clause is not valid if you have declared the constraint to be NOT DEFERRABLE, because a NOT DEFERRABLE constraint is automatically INITIALLY IMMEDIATE and cannot ever be INITIALLY DEFERRED.
http://download.oracle.com/docs/cd/E11882_01/server.112/e10592/clauses002.htm#SQLRF52180
105. Which statement regarding the contents of the V$PARAMETER view is true?
A) displays only the list of default values
B) displays only the list of all basic parameters
C) displays the currently in effect parameter values
D) displays only the list of all advanced parameters
E) displays the list of all the parameter files of a database
F) displays the current contents of the server parameter file
答案:C
106. The HR user owns the EMP table. The HR user grants privileges to the SCOTT user by using this command:
SQL> GRANT SELECT, INSERT, UPDATE ON emp TO scott WITH GRANT OPTION;
The SCOTT user executes this command to grant privileges to the JIM user:
SQL> GRANT SELECT, INSERT, UPDATE ON hr.emp TO jim;
Now the HR user decides to revoke privileges from JIM by using this command:
SQL> REVOKE SELECT, INSERT, UPDATE ON emp FROM jim;
Which statement is true after HR issues the REVOKE command?
A) The command succeeds and privileges are revoked from JIM.
B) The command fails because SCOTT still has privileges with him.
C) The command fails because HR cannot revoke the privileges from JIM.
D) Only HR can perform SELECT, INSERT, and UPDATE operations on the EMP table.
答案: C
107. Your database is running under automatic undo management and the UNDO_RETENTION parameter is set to 900 sec. You executed the following command to enable retention guarantee:
SQL> ALTER TABLESPACE undotbs1 RETENTION GUARANTEE;
What effect would this statement have on the database?
A) The extents in undo tablespace retain data until the next full database backup.
B) The extents containing committed data in the undo tablespace are never overwritten.
C) The extents which no longer contain uncommitted data in the undo tablespace are not overwritten for at least15 minutes.
D) The extents containing committed data in the undo tablespace are not overwritten until the instance is shut down.
答案:C
108. In your database, the snapshot interval is set to 10 minutes for the Automatic Workload Repository (AWR). The database instance is running for the past 30 days.
View the Exhibit to examine the Automatic Database Diagnostic Monitor (ADDM) task.
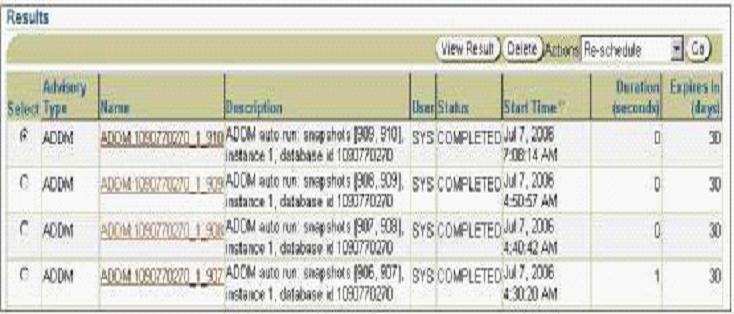
The ADDM task is performed every 10 minutes, except the last task. What could be the reason for this?
A) The snapshot retention period for the AWR was increased before the last task.
B) The optimizer statistics for few objects in the database were locked before the last task.
C) The STATISTICS_LEVEL initialization parameter was changed to BASIC and reset to TYPICAL before the last task.
D) The optimizer statistics was collected manually by using the DBMS_STATS package before the last task.
答案:C
STATISTICS_LEVEL specifies the level of collection for database and operating system statistics. The Oracle Database collects these statistics for a variety of purposes, including making self-management decisions.
The default setting of TYPICAL ensures collection of all major statistics required for database self-management functionality and provides best overall performance. The default value should be adequate for most environments.
When the STATISTICS_LEVEL parameter is set to ALL, additional statistics are added to the set of statistics collected with the TYPICAL setting. The additional statistics are timed OS statistics and plan execution statistics.
Setting the STATISTICS_LEVEL parameter to BASIC disables the collection of many of the important statistics required by Oracle Database features and functionality,
http://download.oracle.com/docs/cd/E11882_01/server.112/e10820/initparams247.htm#REFRN10214
109. Which two statements about Flashback Query are true? (Choose two.)
A) It is generated by using the redo log files.
B) It helps in row-level recovery from user errors.
C) It can be performed to recover ALTER TABLE statements
D) It fails when undo data pertaining to the transaction is overwritten.
E) The database has to be opened with the resetlogs option after performing Flashback Query.
答案:BD
110. What are the consequences of executing the SHUTDOWN ABORT command? (Choose two.)
A) The database files are synchronized.
B) Uncommitted changes are not rolled back.
C) The database is closed, but the instance is still started.
D) Database buffers and redo buffers are not written to the disk.
E) The database undergoes automatic media recovery during the next startup.
答案:BD
111. Which three statements are correct about temporary tables? (Choose three.)
A) Indexes and views can be created on temporary tables.
B) Both the data and the structure of temporary tables can be exported.
C) Temporary tables are always created in a user's temporary tablespace.
D) The data inserted into a temporary table in a session is available to other sessions.
E) Data manipulation language (DML) locks are never acquired on the data of temporary tables.
答案:ACE
Oracle 临时表
http://blog.csdn.net/tianlesoftware/archive/2009/10/21/4705283.aspx
112. A user wants to connect to the database instance from an application that is running on a remote machine. Which tools should the DBA use to establish the required configuration to ensure that the user is able to connect to the database instance? (Choose two.)
A) Data Pump
B) Oracle Net Manager
C) Oracle Enterprise Manager
D) Oracle Universal Installer (OUI)
E) Database Configuration Assistant (DBCA)
答案:BC
113. While planning to manage more than one database in your system, you perform the following activities:
1. Organize different categories of files into independent subdirectories.
2. Use consistent naming convention for database files.
3. Separate administrative information pertaining to each database.
Which option corresponds to the type of activities performed by you?
A) Oracle Managed Files
B) Oracle Grid Architecture
C) Optimal Flexible Architecture
D) Oracle database architecture
答案:C
The Optimal Flexible Architecture standard helps you to organize database software and configure databases to allow multiple databases, of different versions, owned by different users to coexist. Optimal Flexible Architecture assists in identification of ORACLE_BASE with its Automatic Diagnostic Repository (ADR) diagnostic data to properly collect incidents.
All Oracle components on the installation media are compliant with Optimal Flexible Architecture. This means, Oracle Universal Installer places Oracle Database components in directory locations, assigning the default permissions that follow Optimal Flexible Architecture guidelines.
Oracle recommends that you use Optimal Flexible Architecture, specially if the database will grow in size, or if you plan to have multiple databases.
http://download.oracle.com/docs/cd/E11882_01/install.112/e10848/appendix_ofa.htm#sthref698
114. You specified extent management as local for a tablespace. How will it affect space management in the tablespace?
A) All the extents will be of the same size.
B) Bitmap will be used to record free and allocated extents.
C) Free extents will be managed by the data dictionary tables.
D) The tablespace will be system managed and the users cannot specify the extent size.
答案:B
115. View the Exhibit to examine the output of the DBA_OUTSTANDING_ALERT view.
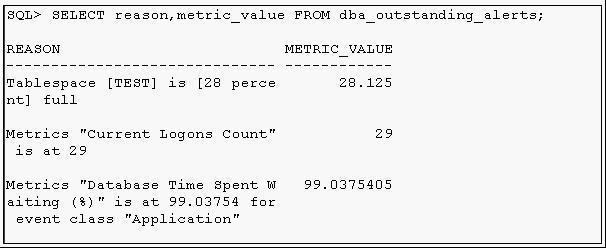
After 30 minutes, you executed the following command:
SQL> SELECT reason,metric_value FROM dba_outstanding_alerts;
REASON METRIC_VALUE
------------------------------------------------------- ----------------------
Tablespace [TEST] is [28 percent] full 28.125
What could be the two reasons for the elimination of the other rows in the output? (Choose two.)
A) The threshold alert conditions are cleared.
B) The threshold alerts are transferred to DBA_ALERT_HISTORY.
C) The non-threshold-based alerts are transferred to DBA_ALERT_HISTORY.
D) The threshold alerts related to database metrics are permanently stored in DBA_ALERT_HISTORY but not the threshold alerts related to instance metrics.
答案:AB
116. Which two statements are true regarding the SGA_TARGET initialization parameter? (Choose two.)
A) It can be increased up to the value of the SGA_MAX_SIZE parameter.
B) Increasing the value of SGA_TARGET up to the value of SGA_MAX_SIZE disables the automatic shared memory management feature.
C) Reducing the value of the SGA_TARGET parameter takes away memory from both autotuned and manually sized components.
D) Increasing the value of the SGA_TARGET parameter distributes the increased memory among all the autotuned components.
答案:AD
117. You work in a data warehouse environment that involves the execution of complex queries. The current content of the SQL cache holds the ideal workload for analysis.
You want to analyze only few most resource-intensive statements. What would be your suggestion to receive recommendations on the efficient use of indexes and materialized views to improve query performance?
A) Run the SQL Access Advisor.
B) Run the SQL Tuning Advisor (STA).
C) Run the Automatic Workload Repository (AWR) report.
D) Run the Automatic Database Diagnostic Monitor (ADDM).
答案:A
118. You notice this warning in the alert log file:
ORA-19815: WARNING: db_recovery_file_dest_size of 3221225472 bytes is 100.00% used, and has 0 remaining bytes available.
What would you do to reclaim the used space in the Flash Recovery Area?
A) Back up the Flash Recovery Area.
B) Increase the retention time for the files.
C) Decrease the retention time for the files.
D) Manually delete all the archived log files from the Flash Recovery Area by using operating system (OS) commands.
答案:AC
119. View the Exhibit to observe the message received while trying to drop the SL_REP user in Oracle Enterprise Manager. The SL_REP user owns objects and is currently connected to the database instance.
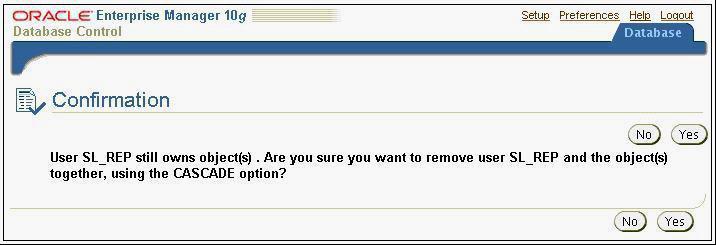
What would happen if you click YES in the Exhibit?
A) An error is returned, and the user is not dropped.
B) The drop operation waits until the session started by the user ends.
C) The user is dropped successfully, and the session started by the user is killed.
D) The user is dropped, and the objects owned by the user are transferred to the recycle bin.
答案:A
120. In the PROD database you have granted the RESUMABLE system privilege to the CONNECT role. Resumable space operation has been enabled for all user sessions. You want users NOT to be aware of any kind of space-related problems while performing transactions. Instead, you want the problem to be resolved by a database trigger automatically. Which combination of triggering time and event would you use to achieve this objective?
A) AFTER CREATE
B) AFTER SUSPEND
C) BEFORE CREATE
D) AFTER TRUNCATE
E) BEFORE SUSPEND
F) AFTER INSERT OR DELETE OR UPDATE
G) BEFORE INSERT OR DELETE OR UPDATE
答案:B
------------------------------------------------------------------------------
Blog: http://blog.csdn.net/tianlesoftware
网上资源: http://tianlesoftware.download.csdn.net
相关视频:http://blog.csdn.net/tianlesoftware/archive/2009/11/27/4886500.aspx
DBA1 群:62697716(满); DBA2 群:62697977
DBA3 群:63306533; 聊天 群:40132017