学校里的破事终于只剩下考试了,终于有时间接着学了。先复习一下以前学的
在Windows xp中3环函数API进入0环函数,是有两种方法进入的:1.syscall、2.int
在正式进行实验时,先介绍一点东西
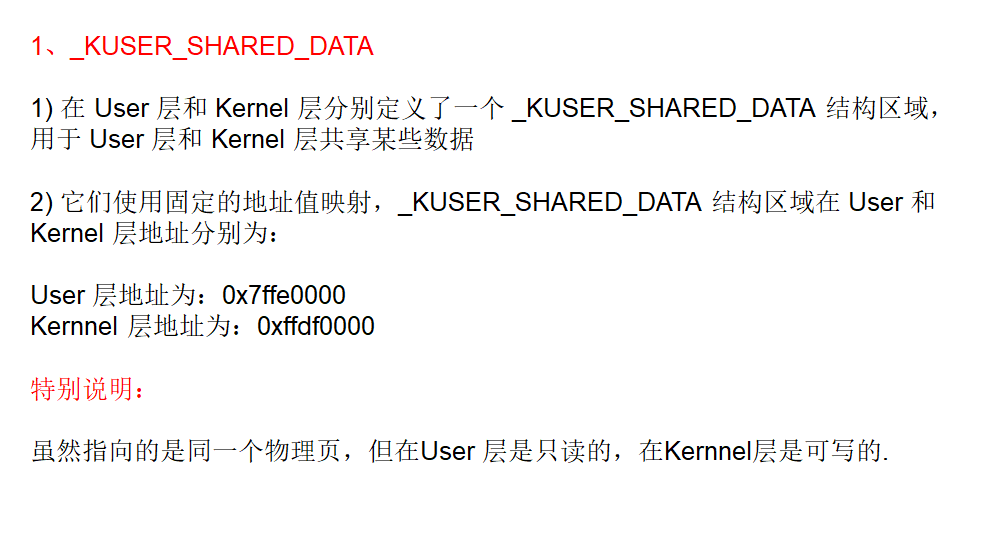
_KUSER_SHARED_DATA结构体
共享区,3环和0环都映射的同一块物理页
中断门进0环

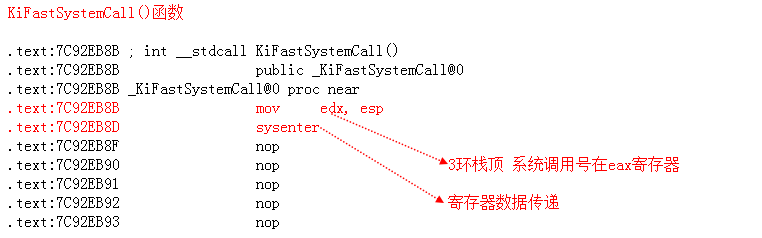
快速调用进0环

ReadProcessMemory
我们可以拿一个API函数ReadProcessMemory来验证一下:
在kernel32中Alt+T进行搜索函数,找到后查看其代码:
.text:7C8021D0 ; BOOL __stdcall ReadProcessMemory(HANDLE hProcess, LPCVOID lpBaseAddress, LPVOID lpBuffer, SIZE_T nSize, SIZE_T *lpNumberOfBytesRead) .text:7C8021D0 public ReadProcessMemory .text:7C8021D0 ReadProcessMemory proc near ; CODE XREF: GetProcessVersion+2F12F↓p .text:7C8021D0 ; GetProcessVersion+2F14E↓p ... .text:7C8021D0 .text:7C8021D0 hProcess = dword ptr 8 .text:7C8021D0 lpBaseAddress = dword ptr 0Ch .text:7C8021D0 lpBuffer = dword ptr 10h .text:7C8021D0 nSize = dword ptr 14h .text:7C8021D0 lpNumberOfBytesRead= dword ptr 18h .text:7C8021D0 .text:7C8021D0 mov edi, edi .text:7C8021D2 push ebp .text:7C8021D3 mov ebp, esp .text:7C8021D5 lea eax, [ebp+nSize] .text:7C8021D8 push eax ; NumberOfBytesRead .text:7C8021D9 push [ebp+nSize] ; NumberOfBytesToRead .text:7C8021DC push [ebp+lpBuffer] ; Buffer .text:7C8021DF push [ebp+lpBaseAddress] ; BaseAddress .text:7C8021E2 push [ebp+hProcess] ; ProcessHandle .text:7C8021E5 call ds:NtReadVirtualMemory .text:7C8021EB mov ecx, [ebp+lpNumberOfBytesRead] .text:7C8021EE test ecx, ecx .text:7C8021F0 jnz short loc_7C8021FD .text:7C8021F2 .text:7C8021F2 loc_7C8021F2: ; CODE XREF: ReadProcessMemory+32↓j .text:7C8021F2 test eax, eax .text:7C8021F4 jl short loc_7C802204 .text:7C8021F6 xor eax, eax .text:7C8021F8 inc eax .text:7C8021F9 .text:7C8021F9 loc_7C8021F9: ; CODE XREF: ReadProcessMemory+3C↓j .text:7C8021F9 pop ebp .text:7C8021FA retn 14h
查看导入表,得知调用的ntdll文件
查看ntdll,通过查找,找到ntReadVirtualMemory函数
很容易发现他通过调用0x7ffe0300,至于这里的eax其实是系统调用号的意思(跟ssdt表)
.text:7C92D9E0 public ZwReadVirtualMemory .text:7C92D9E0 ZwReadVirtualMemory proc near ; CODE XREF: LdrFindCreateProcessManifest+1CC↓p .text:7C92D9E0 ; LdrCreateOutOfProcessImage+7C↓p ... .text:7C92D9E0 mov eax, 0BAh ; NtReadVirtualMemory .text:7C92D9E5 mov edx, 7FFE0300h .text:7C92D9EA call dword ptr [edx] .text:7C92D9EC retn 14h .text:7C92D9EC ZwReadVirtualMemory endp
通过上述的介绍,并查看后,我们可以看到类似如下代码:
0: kd> dt _KUSER_SHARED_DATA 0x7ffe0000 ntdll!_KUSER_SHARED_DATA +0x000 TickCountLow : 0x83114 +0x004 TickCountMultiplier : 0xfa00000 +0x008 InterruptTime : _KSYSTEM_TIME +0x014 SystemTime : _KSYSTEM_TIME +0x020 TimeZoneBias : _KSYSTEM_TIME +0x02c ImageNumberLow : 0x14c +0x02e ImageNumberHigh : 0x14c +0x030 NtSystemRoot : [260] 0x43 +0x238 MaxStackTraceDepth : 0 +0x23c CryptoExponent : 0 +0x240 TimeZoneId : 0 +0x244 Reserved2 : [8] 0 +0x264 NtProductType : 1 ( NtProductWinNt ) +0x268 ProductTypeIsValid : 0x1 '' +0x26c NtMajorVersion : 5 +0x270 NtMinorVersion : 1 +0x274 ProcessorFeatures : [64] "" +0x2b4 Reserved1 : 0x7ffeffff +0x2b8 Reserved3 : 0x80000000 +0x2bc TimeSlip : 0 +0x2c0 AlternativeArchitecture : 0 ( StandardDesign ) +0x2c8 SystemExpirationDate : _LARGE_INTEGER 0x0 +0x2d0 SuiteMask : 0x110 +0x2d4 KdDebuggerEnabled : 0x3 '' +0x2d5 NXSupportPolicy : 0x2 '' +0x2d8 ActiveConsoleId : 0 +0x2dc DismountCount : 0 +0x2e0 ComPlusPackage : 0xffffffff +0x2e4 LastSystemRITEventTickCount : 0x7f50a6 +0x2e8 NumberOfPhysicalPages : 0xbff6a +0x2ec SafeBootMode : 0 '' +0x2f0 TraceLogging : 0 +0x2f8 TestRetInstruction : 0xc3 +0x300 SystemCall : 0x7c92e4f0 +0x304 SystemCallReturn : 0x7c92e4f4 +0x308 SystemCallPad : [3] 0 +0x320 TickCount : _KSYSTEM_TIME +0x320 TickCountQuad : 0 +0x330 Cookie : 0xe996c383
查看偏移为0x300的systemcall成员,说明当前我是用的快速调用进入的0环
0: kd> u 0x7c92e4f0 ntdll!KiFastSystemCall: 7c92e4f0 8bd4 mov edx,esp 7c92e4f2 0f34 sysenter
这里有几个点,查看MSR寄存器


如下是快速调用的代码
0: kd> rdmsr 176 msr[176] = 00000000`80542520 0: kd> u 80542520 ReadVirtual: 80542520 not properly sign extended 80542520 b923000000 mov ecx,23h 80542525 6a30 push 30h 80542527 0fa1 pop fs 80542529 8ed9 mov ds,cx 8054252b 8ec1 mov es,cx 8054252d 648b0d40000000 mov ecx,dword ptr fs:[40h] 80542534 8b6104 mov esp,dword ptr [ecx+4] 80542537 6a23 push 23h
不过我再来看看Int进入0环试试
0: kd> u KiIntSystemCall ntdll!KiIntSystemCall: 7c92e500 8d542408 lea edx,[esp+8] 7c92e504 cd2e int 2Eh 7c92e506 c3 ret
下面就是该int对应的代码区
0: kd> u 80542451 80542451 6a00 push 0 80542453 55 push ebp 80542454 53 push ebx 80542455 56 push esi 80542456 57 push edi 80542457 0fa0 push fs 80542459 bb30000000 mov ebx,30h 8054245e 668ee3 mov fs,bx 0: kd> u KiSystemService nt!KiSystemService: 80542451 6a00 push 0 80542453 55 push ebp 80542454 53 push ebx 80542455 56 push esi 80542456 57 push edi 80542457 0fa0 push fs 80542459 bb30000000 mov ebx,30h 8054245e 668ee3 mov fs,bx