In my previously article "EnCase missed some USB activities in the evidence files", I mentioned about that EnCase could only "see" few USB records. Actually not only EnCase may not see all USB records, some other forensic tools got the same problems.
What else could help us to find the missing USB Records? Take Windows 10 for example, we could take a look at the event log file named "Microsoft-Windows-Kernel-PnP%4Configuration.evtx" as below. You could know the brand, model and serial number and the timestamp etc.
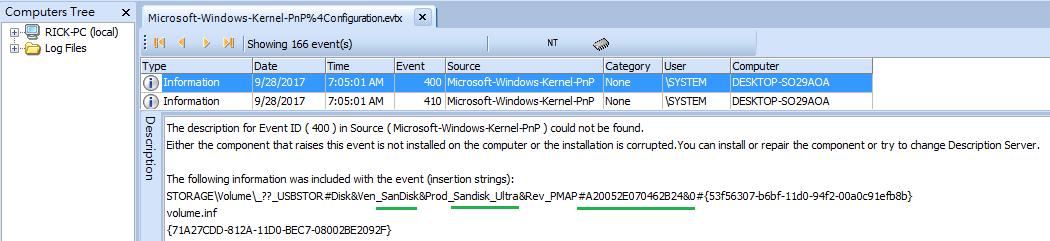
Actually there is more than one USB device that suspect used as below. It's Seagate BUP_BK, but what's wrong with the serial number? All the digit is zero? That's not gonna happen,right?
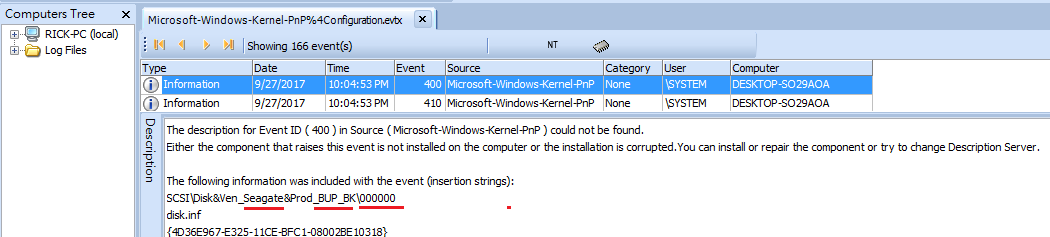
Don't worry~ Just take a look at the following record and you will see its actual serial number.
