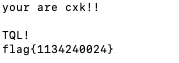
[GUET-CTF2019]number_game
这题似乎是与二叉树相关,但我想试试爆破的方法
可以看出输入要求在0和4之间,长度为10,5^10可以接受
from itertools import *
import subprocess
list="01234"
for i in product(list,repeat=10):
flag ="".join(i)
p = subprocess.Popen(["./number"], stdin=subprocess.PIPE, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
p.stdin.write(flag)
p.stdin.close()
out=p.stdout.read()
p.stdout.close()
print out
if "your" not in out:
exit()
大概用了一个小时吧
[V&N2020 公开赛]CSRe
加了混淆的c#,用dnspy打开
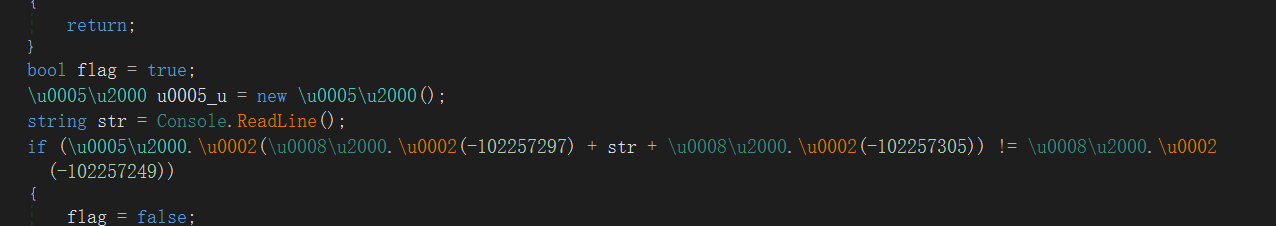
可以参考https://www.52pojie.cn/thread-958680-1-1.html
用de4dot去混淆(de4dot要新一点的版本,我用的是https://www.52pojie.cn/thread-912541-1-1.html)

逻辑很清晰了,在线解个sha1,得到flag
crackME
32exe,根据用户名构建了一张表,具体细节不去管,关键在于
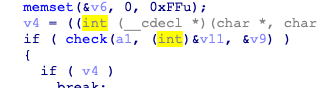
进check,
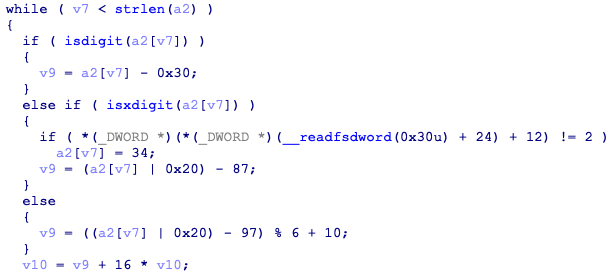
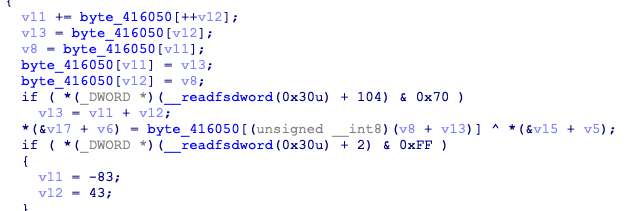
密码被处理后与表异或为v17,需要注意的是_readfsdword处为反调,可改为如下跳过


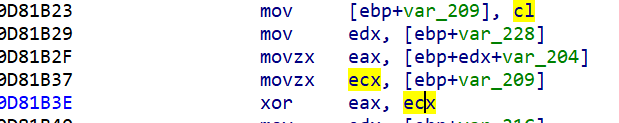
表可从下图中ecx动调得到
之后进入
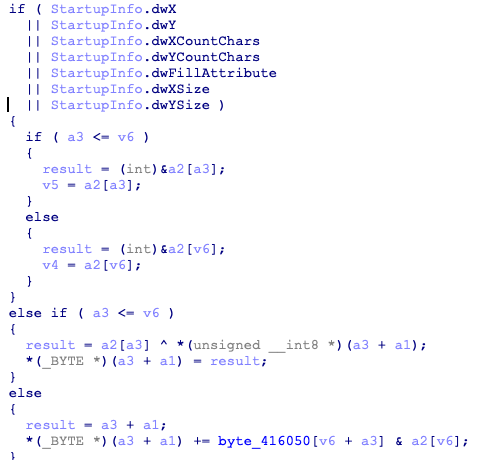
此处又有反调,调试中会有异或的操作,下图里随便找个jnz改成jmp
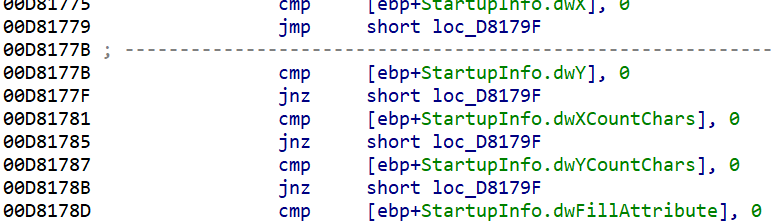
最后

v17需等于dbappsec
# -*- coding:utf-8 -*-
a="dbappsec"
d=[0x2a,0xd7,0x92,0xe9,0x53,0xe2,0xc4,0xcd]
for i in range(8):
print(hex(ord(a[i])^d[i]).replace("0x",""),end="")
MD5得flag
[BJDCTF2020]easy
32exe,ida可找到关键函数为_ques,但程序并没用到这函数
od打开,

可以直接利用jmp跳到_ques运行后会打印出flag
[BJDCTF2020]BJD hamburger competition
unity逆向,参考了Unity游戏逆向及破解方法介绍
找到BJD hamburger competition_DataManagedAssembly-CSharp.dll,用dnspy打开
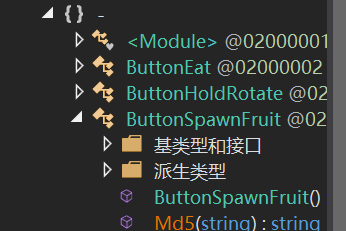
在ButtonSpawnFruit里
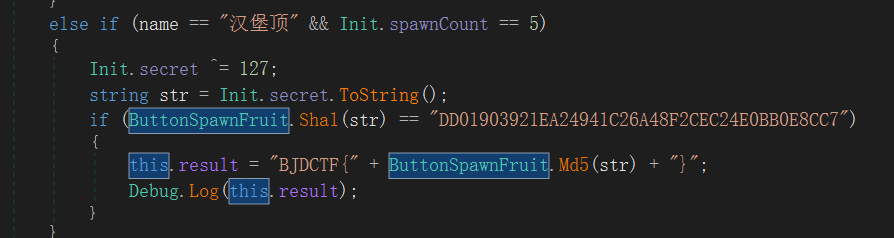
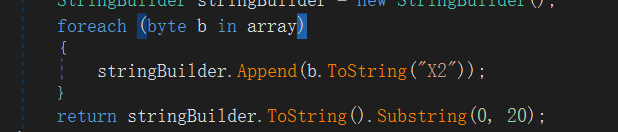
解sha1后md5,这里的md5只取了前20位
最后,flag是大写真滴难受
[2019红帽杯]xx
64exe,从youwin找到关键函数
加密可分为三个部分,
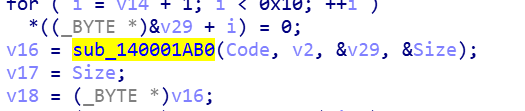
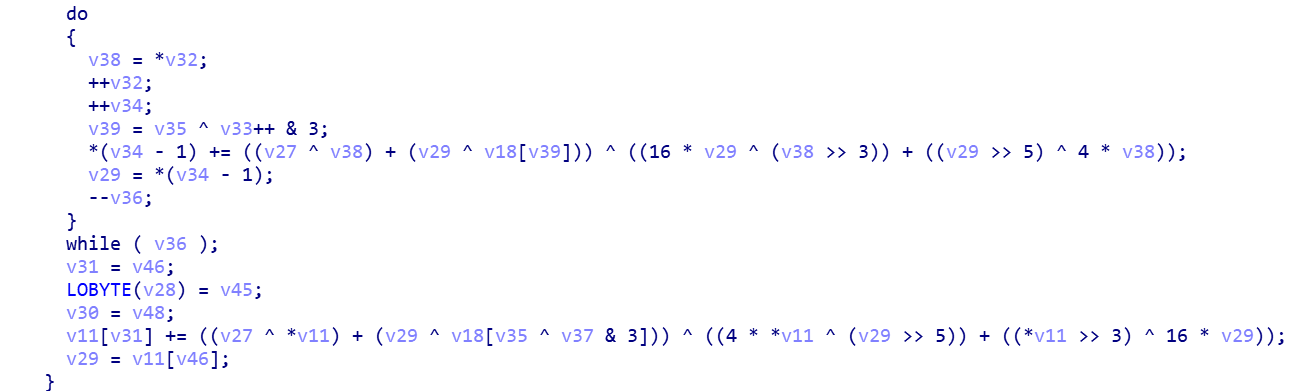
此处可看出是一个xxtea,之后

对位置进行了变换,

按一定规律进行了异或,最终得到的结果与
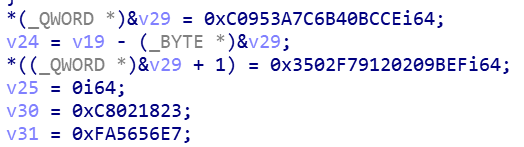
对比,思路就是从后往前推回去
# -*- coding:utf-8 -*-
v18=[0xce,0xbc,0x40,0x6b,0x7c,0x3a,0x95,0xc0,0xef,0x9b,0x20,0x20,0x91,0xf7,0x02,0x35,0x23,0x18,0x02,0xc8,0xe7,0x56,0x56,0xfa]
v19=[]
for i in range(24):
v19.append(0)
for i in range(len(v18)-1,-1,-1):
if i>=3:
for j in range(i//3):
v18[i]^=v18[j]
print(v18)
v19[2] = v18[0]
v19[0] = v18[1];
v19[3] = v18[2];
v19[1] = v18[3];
v19[6] = v18[4];
v19[4] = v18[5];
v19[7] = v18[6];
v19[5] = v18[7];
v19[10] = v18[8];
v19[8] = v18[9];
v19[11] = v18[10];
v19[9] = v18[11];
v19[14] = v18[12];
v19[12] = v18[13];
v19[15] = v18[14];
v19[13] = v18[15];
v19[18] = v18[16];
v19[16] = v18[17];
v19[19] = v18[18];
v19[17] = v18[19];
v19[22] = v18[20];
v19[20] = v18[21];
v19[23] = v18[22];
v19[21] = v18[23]
print(v19)
for i in range(len(v19)):
v19[i]=hex(v19[i])
print(v19)
得到的结果进行xxtea解密,此处来自于TEA、XTEA、XXTEA加密解密算法
#include <stdio.h>
#include <stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z)))
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n > 1) /* Coding Part */
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
else if (n < -1) /* Decoding Part */
{
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
int main()
{
uint32_t v[6] = {0x40cea5bc,0xe7b2b2f4,0x129d12a9,0x5bc810ae,0x1d06d73d,0xdcf870dc};
uint32_t const k[4] = { 0x67616c66,0x0,0x0,0x0 };
int n = 6;
btea(v, -n, k);
printf("解密后的数据:%x %x %x %x %x %x
", v[0], v[1],v[2],v[3],v[4],v[5]);
return 0;
}
得到flag
[FlareOn4]IgniteMe
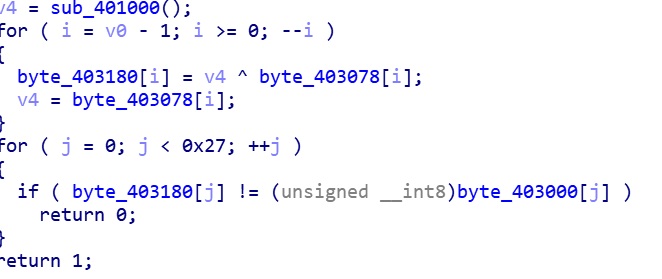
很简单的题,关键部分就是输入异或后与byte_400300比较
flag=[0x0D,0x26,0x49,0x45,0x2A,0x17,0x78,0x44,0x2B,0x6C,0x5D,0x5E,0x45,0x12,0x2F,0x17,0x2B,0x44,0x6F,0x6E,0x56,0x09,0x5F,0x45,0x47,0x73,0x26,0x0A,0x0D,0x13,0x17,0x48,0x42,0x01,0x40,0x4D,0x0C,0x02,0x69]
flag[len(flag)-1]^=4
for i in range(len(flag)-2,-1,-1):
flag[i]^=flag[i+1]
for i in range(len(flag)):
print(chr(flag[i]),end="")
[安洵杯 2019]crackMe
32exe,用die查一下
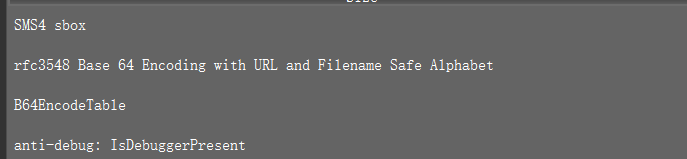
大概有sm4和base,拖进ida

MessageBoxW做了个hook,
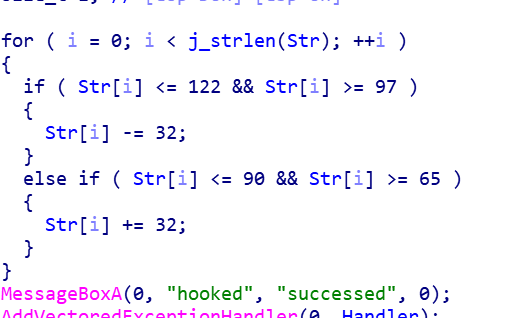
hook使base表的大小写转换,之后在0x1283458处人为了一个非法访问异常,跳到异常处理

进入sub可以知道这就是之前查出来的sm4,密钥为v2
之后继续看异常
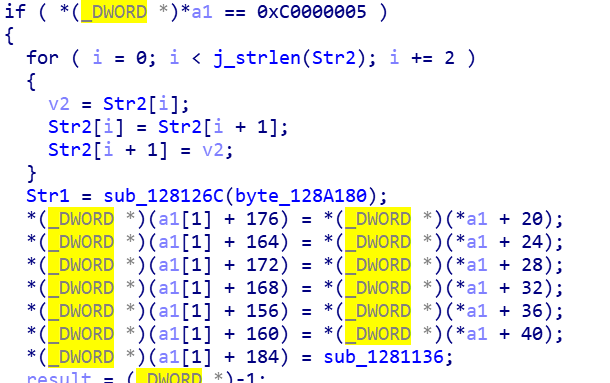
这个sub_1281136是检验的函数
进入sub_128126c,

base64,经过了一点小的变动,“=”换成了“!”,在换表时做了移位
import base64
import pysm4
str2="U1ATIOpkOyWSvGm/YOYFR4"
str1=""
flag=""
table="yzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789+/abcdefghijklmnopqrstuvwx"
table2="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
for i in str2:
for j in range(len(table)):
if i==table[j]:
str1+=table2[j]
str1=str1+"=="
str1=base64.b64decode(str1)
str1=0x59d095290df2400614f48d276906874e
key=0x77686572655F6172655F755F6E6F773f
flag=hex(pysm4.decrypt(str1,key))[2:].replace("L","")
for i in range(0,len(flag)-1,2):
print(chr(eval("0x"+flag[i:i+2])))
[WUSTCTF2020]level1
64elf,拖进ida
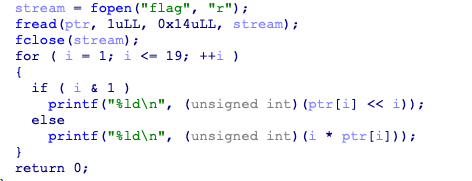
从 flag文件里读了20个字,只对后19个加密后输出
flag=[0,198,232,816,200,1536,300,6144,984,51200,570,92160,1200,565248,756,1474560,800,6291456,1782,65536000]
for i in range(1,20):
if(i&1):
flag[i]=flag[i]>>i
else:
flag[i]=flag[i]//i
for i in range(1,20):
print(chr(flag[i]),end="")
[GWCTF 2019]re3
64exe,DIE里看一看
有AES,进ida看看

这里本来应该有个smc,这里放的是我patch后的图,smc脚本如下
#include <idc.idc>
static main() {
auto i,x,key,from;
from=0x402219;
key = 0x99;
for ( i=0; i != 224; i=i+1 ) {
x = Byte(from);
x = (x^key);
PatchByte(from,x);
from = from + 1;
}
}
关键在于smc藏的这个sub_402219,
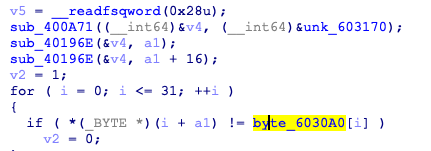
以unk_603170为密钥,将输入AES加密后与byte_6030A0比较,密钥可直接动调得到
from Crypto.Cipher import AES
from binascii import b2a_hex, a2b_hex
key=a2b_hex('CB8D493521B47A4CC1AE7E62229266CE')
c="BC0AADC0147C5ECCE0B140BC9C51D52B46B2B9434DE5324BAD7FB4B39CDB4B5B"
mode = AES.MODE_ECB
cryptos = AES.new(key, mode)
plain_text = cryptos.decrypt(a2b_hex(c))
print plain_text