不多说,直接上干货!
snort的规则啊,是基于文本的,它通常存在于snort程序目录中或者子目录中,规则文件按照不同的组,进行分类存放的。
snort的安装目录
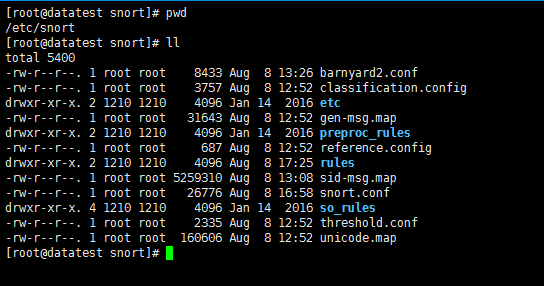
[root@datatest snort]# pwd /etc/snort [root@datatest snort]# ll total 5400 -rw-r--r--. 1 root root 8433 Aug 8 13:26 barnyard2.conf -rw-r--r--. 1 root root 3757 Aug 8 12:52 classification.config drwxr-xr-x. 2 1210 1210 4096 Jan 14 2016 etc -rw-r--r--. 1 root root 31643 Aug 8 12:52 gen-msg.map drwxr-xr-x. 2 1210 1210 4096 Jan 14 2016 preproc_rules -rw-r--r--. 1 root root 687 Aug 8 12:52 reference.config drwxr-xr-x. 2 1210 1210 4096 Aug 8 17:25 rules -rw-r--r--. 1 root root 5259310 Aug 8 13:08 sid-msg.map -rw-r--r--. 1 root root 26776 Aug 8 16:58 snort.conf drwxr-xr-x. 4 1210 1210 4096 Jan 14 2016 so_rules -rw-r--r--. 1 root root 2335 Aug 8 12:52 threshold.conf -rw-r--r--. 1 root root 160606 Aug 8 12:52 unicode.map [root@datatest snort]#
/etc/snort/rules
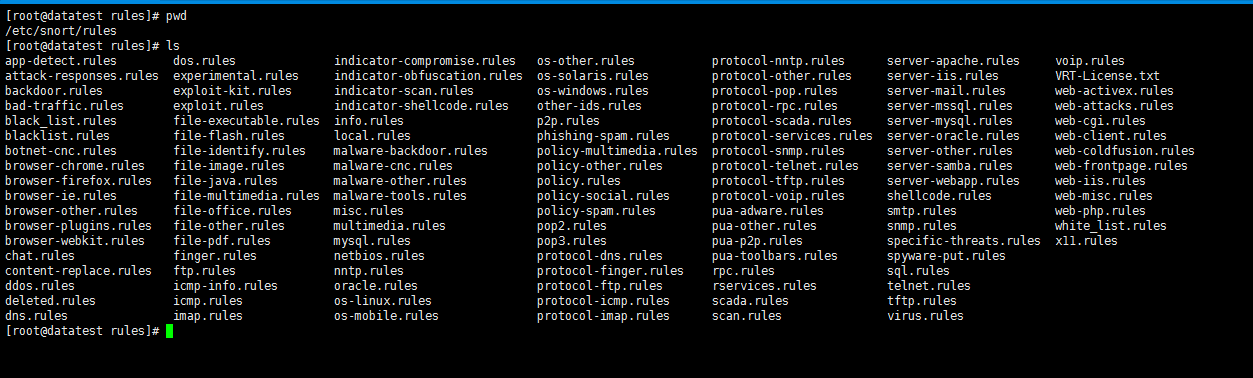
[root@datatest rules]# pwd /etc/snort/rules [root@datatest rules]# ls app-detect.rules dos.rules indicator-compromise.rules os-other.rules protocol-nntp.rules server-apache.rules voip.rules attack-responses.rules experimental.rules indicator-obfuscation.rules os-solaris.rules protocol-other.rules server-iis.rules VRT-License.txt backdoor.rules exploit-kit.rules indicator-scan.rules os-windows.rules protocol-pop.rules server-mail.rules web-activex.rules bad-traffic.rules exploit.rules indicator-shellcode.rules other-ids.rules protocol-rpc.rules server-mssql.rules web-attacks.rules black_list.rules file-executable.rules info.rules p2p.rules protocol-scada.rules server-mysql.rules web-cgi.rules blacklist.rules file-flash.rules local.rules phishing-spam.rules protocol-services.rules server-oracle.rules web-client.rules botnet-cnc.rules file-identify.rules malware-backdoor.rules policy-multimedia.rules protocol-snmp.rules server-other.rules web-coldfusion.rules browser-chrome.rules file-image.rules malware-cnc.rules policy-other.rules protocol-telnet.rules server-samba.rules web-frontpage.rules browser-firefox.rules file-java.rules malware-other.rules policy.rules protocol-tftp.rules server-webapp.rules web-iis.rules browser-ie.rules file-multimedia.rules malware-tools.rules policy-social.rules protocol-voip.rules shellcode.rules web-misc.rules browser-other.rules file-office.rules misc.rules policy-spam.rules pua-adware.rules smtp.rules web-php.rules browser-plugins.rules file-other.rules multimedia.rules pop2.rules pua-other.rules snmp.rules white_list.rules browser-webkit.rules file-pdf.rules mysql.rules pop3.rules pua-p2p.rules specific-threats.rules x11.rules chat.rules finger.rules netbios.rules protocol-dns.rules pua-toolbars.rules spyware-put.rules content-replace.rules ftp.rules nntp.rules protocol-finger.rules rpc.rules sql.rules ddos.rules icmp-info.rules oracle.rules protocol-ftp.rules rservices.rules telnet.rules deleted.rules icmp.rules os-linux.rules protocol-icmp.rules scada.rules tftp.rules dns.rules imap.rules os-mobile.rules protocol-imap.rules scan.rules virus.rules [root@datatest rules]#
比如,文件ftp.rules所包含了FTP攻击内容。
在启动的时候,snort会读取所有的规则文件,并且建立一个三维的链表。
/etc/snort/so_rules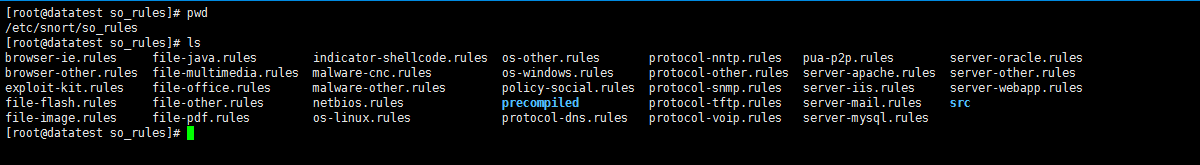
[root@datatest so_rules]# pwd /etc/snort/so_rules [root@datatest so_rules]# ls browser-ie.rules file-java.rules indicator-shellcode.rules os-other.rules protocol-nntp.rules pua-p2p.rules server-oracle.rules browser-other.rules file-multimedia.rules malware-cnc.rules os-windows.rules protocol-other.rules server-apache.rules server-other.rules exploit-kit.rules file-office.rules malware-other.rules policy-social.rules protocol-snmp.rules server-iis.rules server-webapp.rules file-flash.rules file-other.rules netbios.rules precompiled protocol-tftp.rules server-mail.rules src file-image.rules file-pdf.rules os-linux.rules protocol-dns.rules protocol-voip.rules server-mysql.rules [root@datatest so_rules]#