Kubernetes附加组件Dashboard部署实战篇
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.Kubernetes的附加组件Dashboard概述
在Kubernetes有一个著名的附加组件叫面板(Dashboard),该组件实现了Kubernetes的WebUI,通过该组件我们可以实现对Kubernetes集群的管理。
Kubernetes支持多用户管理,换句话说,就是你可以使用不同权限的用户通过Dashboard进行登录从而获得不同的角色权限对Kubernetes集群进行管理,但是Dashborad组件本身并不做任何的认证功能,Dashboard仅仅将认证请求代理至Kubernetes。
由于Dashboard组件是以Pod形式运行在Kubernetes集群之上,因此他通过ServiceAccount的用户账号进行认证。
由于Dashboard组件一般都是在集群外部需要进行访问,因此我们应该将Dashboard组件的网络设置为NodePort类型,或者使用Ingress进行代理,生产环境中推荐使用后者。
二.基于Kubernetes自建ca证书进行证书认证
1>.创建私钥
[root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# openssl genrsa -out dashboard.key 2048

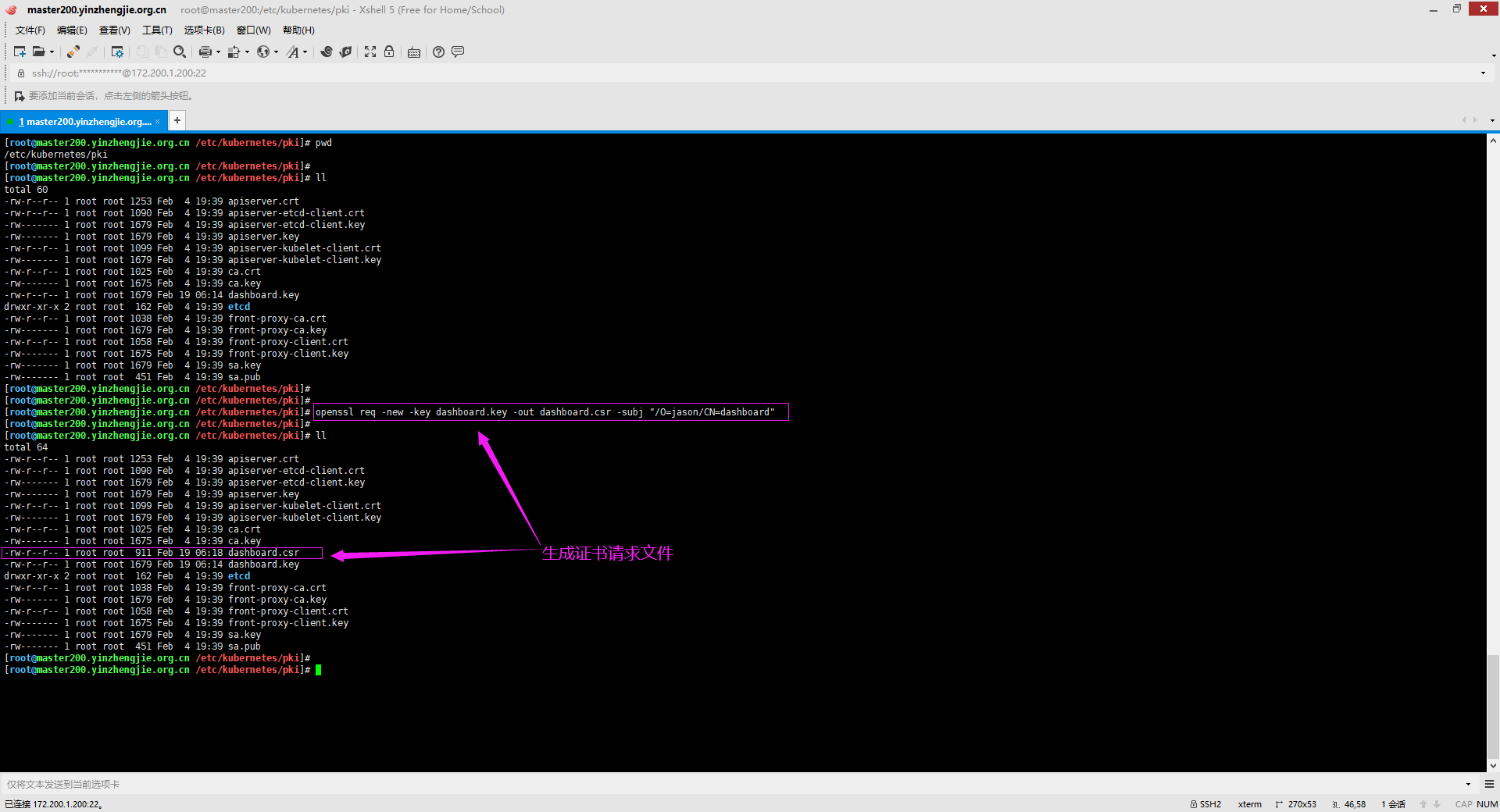
2>.创建证书请求
[root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=jason/CN=dashboard"
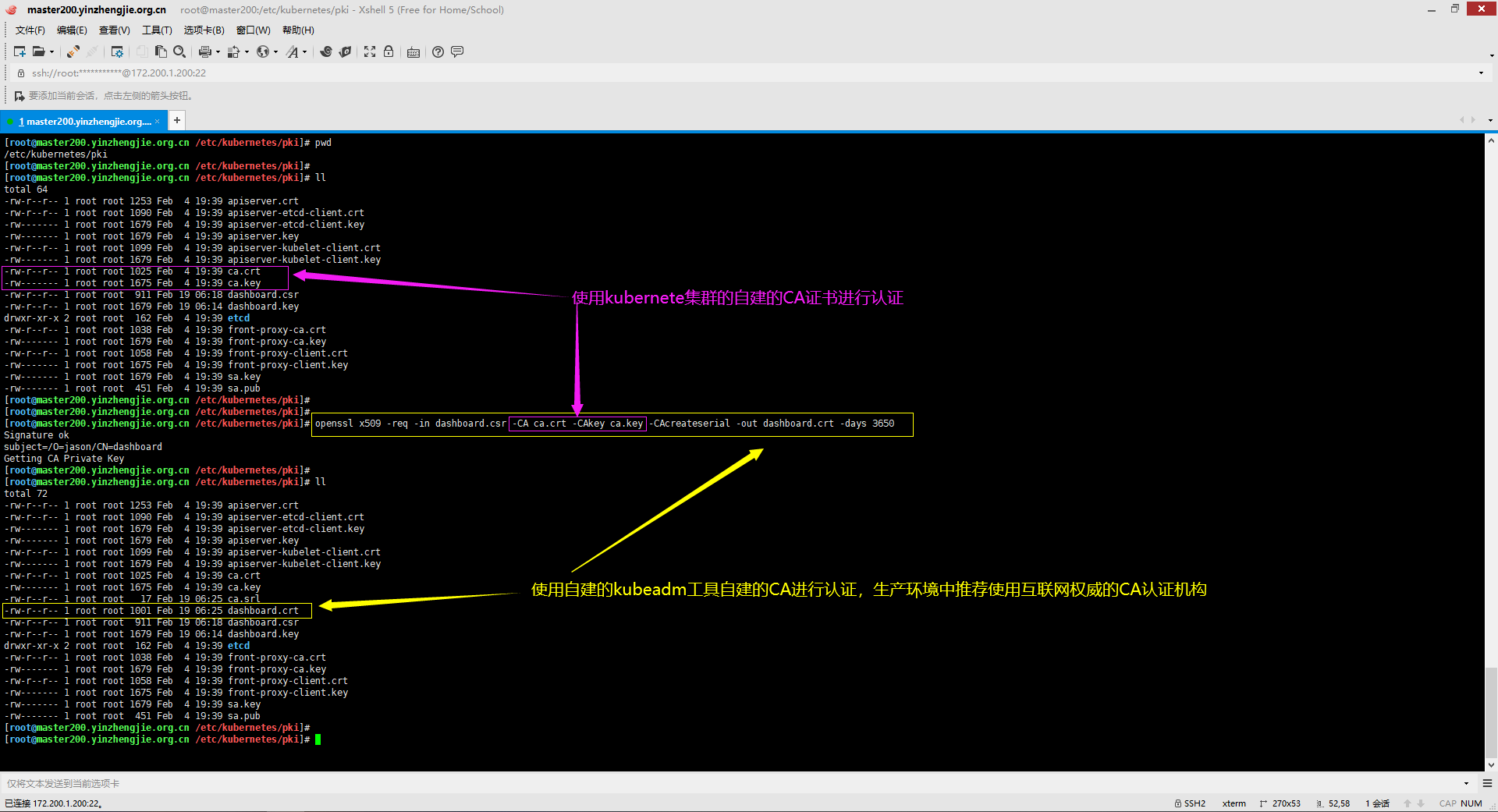
3>.使用kubernetes自建的ca证书进行认证
[root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 3650
三.基于自建的证书和私钥创建secret用于Dashborad
1>.创建用于Dashboard组件的Secret资源
[root@master200.yinzhengjie.org.cn /etc/kubernetes/pki]# kubectl create secret generic kubernetes-dashboard-certs -n kube-system --from-file=dashboard.crt --from-file=dashboard.key
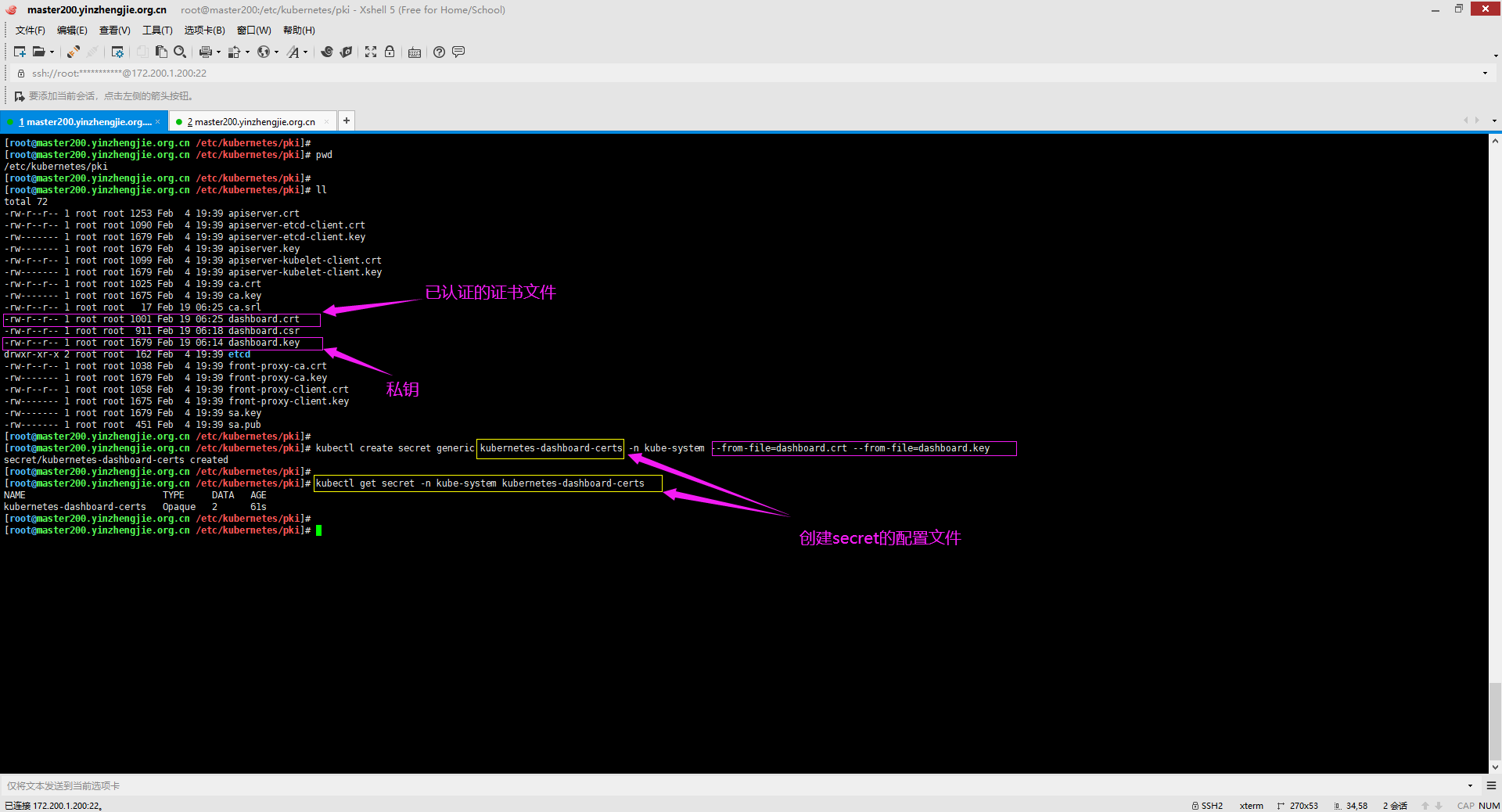
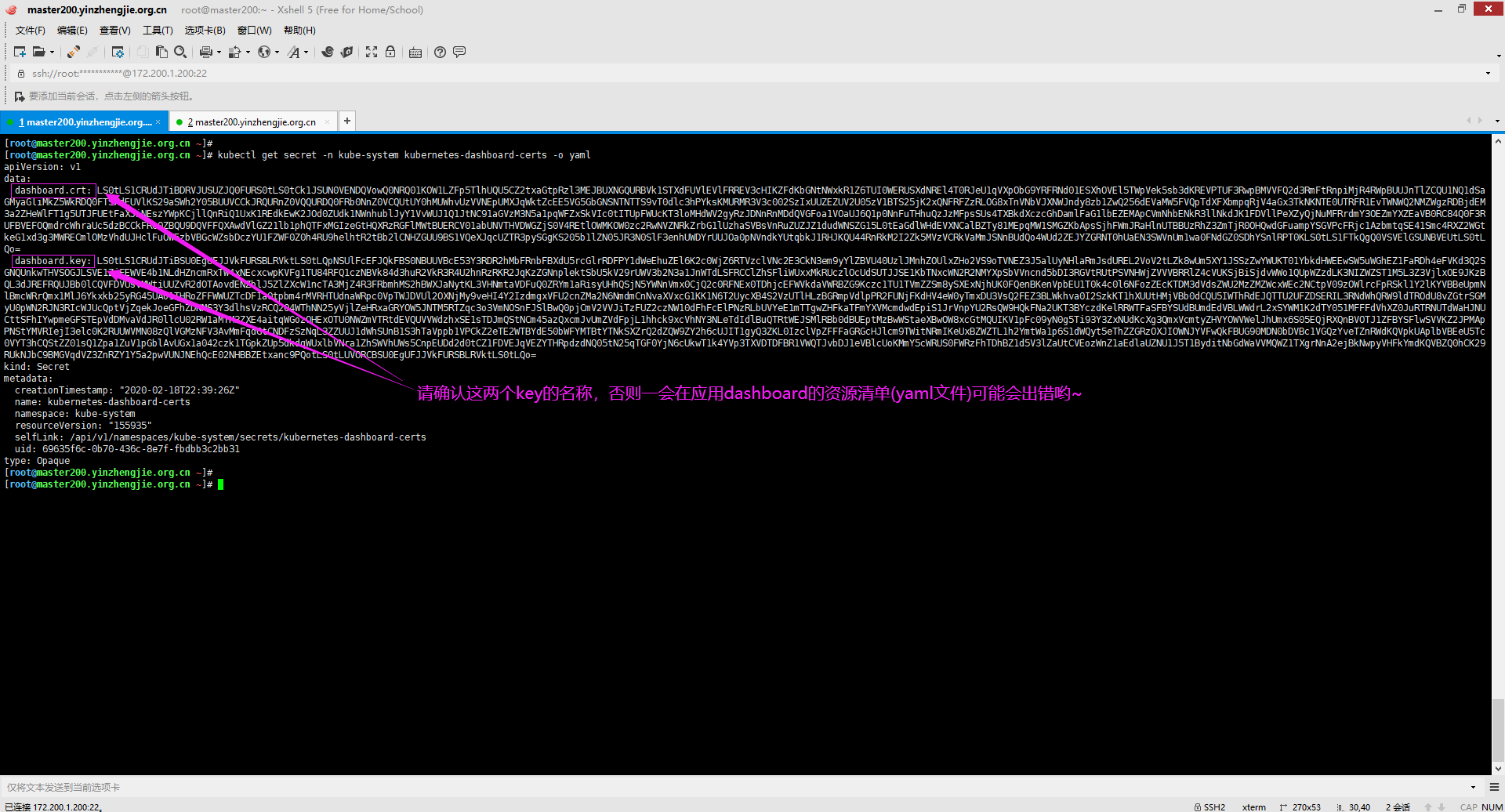
2>.查看Dashboard的secret文件
[root@master200.yinzhengjie.org.cn ~]# kubectl get secret -n kube-system kubernetes-dashboard-certs -o yaml
四.部署Dashboard
1>.参考官方文档
博主推荐阅读: https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/#deploying-the-dashboard-ui
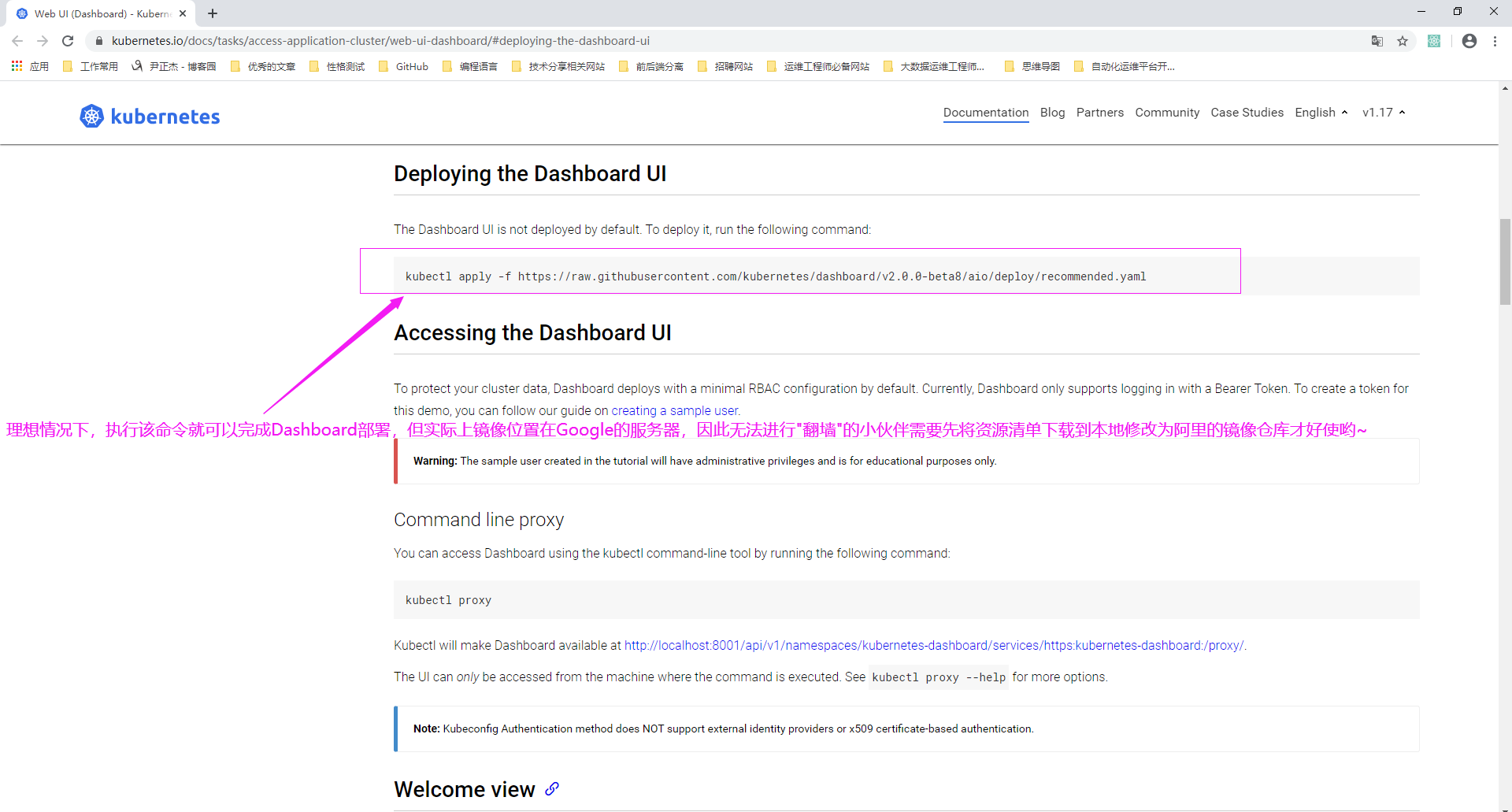
2>.查看官方的资源清单
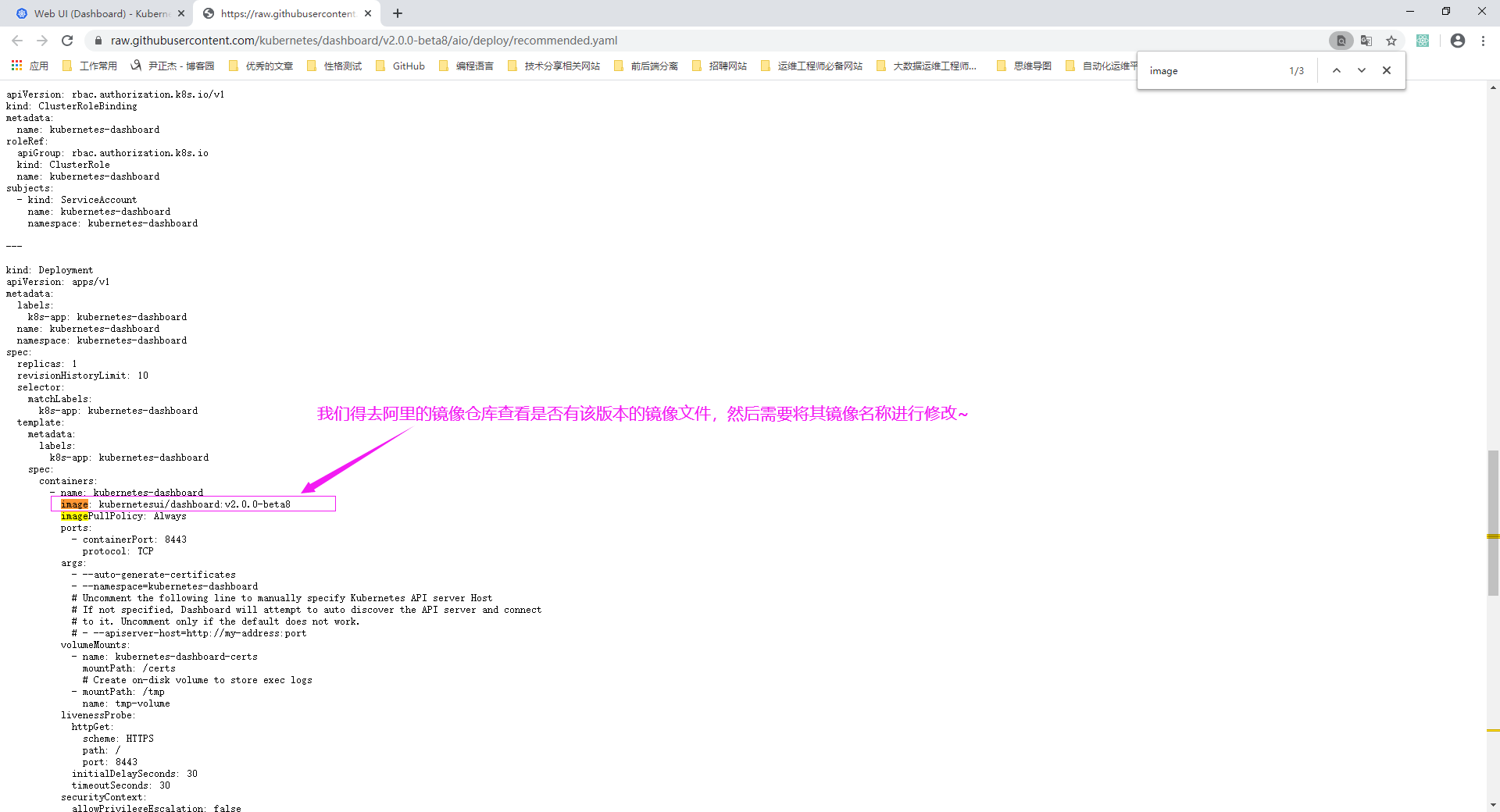
3>.如下图所示,将Google官网的镜像指向国内的阿里镜像仓库(需要登录阿里官网查看)

4>.将修好后的yaml文件上传到服务器(window如果使用另存为的网页文件的后缀名是".txt",需要我们上传到服务器后进行更名)并应用

[root@master200.yinzhengjie.org.cn ~]# cat recommended.yaml # Copyright 2017 The Kubernetes Authors. # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Namespace metadata: name: kubernetes-dashboard --- apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kubernetes-dashboard type: Opaque --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-csrf namespace: kubernetes-dashboard type: Opaque data: csrf: "" --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-key-holder namespace: kubernetes-dashboard type: Opaque --- kind: ConfigMap apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-settings namespace: kubernetes-dashboard --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard rules: # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster", "dashboard-metrics-scraper"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"] verbs: ["get"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard rules: # Allow Metrics Scraper to get metrics from the Metrics server - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard #image: kubernetesui/dashboard:v2.0.0-beta8 image: registry.cn-hangzhou.aliyuncs.com/wez-kubeadmi/dashboard:v2.0.0-beta8 imagePullPolicy: Always ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kubernetes-dashboard # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard nodeSelector: "beta.kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule --- kind: Service apiVersion: v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: ports: - port: 8000 targetPort: 8000 selector: k8s-app: dashboard-metrics-scraper --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: dashboard-metrics-scraper template: metadata: labels: k8s-app: dashboard-metrics-scraper annotations: seccomp.security.alpha.kubernetes.io/pod: 'runtime/default' spec: containers: - name: dashboard-metrics-scraper #image: kubernetesui/metrics-scraper:v1.0.1 image: registry.cn-hangzhou.aliyuncs.com/marmot-k8s/kubernetesui-metrics-scraper:v1.0.1 ports: - containerPort: 8000 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8000 initialDelaySeconds: 30 timeoutSeconds: 30 volumeMounts: - mountPath: /tmp name: tmp-volume securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 serviceAccountName: kubernetes-dashboard nodeSelector: "beta.kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule volumes: - name: tmp-volume emptyDir: {} [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# ll total 8 -rw-r--r-- 1 root root 7755 Feb 19 07:31 recommended.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl apply -f recommended.yaml namespace/kubernetes-dashboard created serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created [root@master200.yinzhengjie.org.cn ~]#

[root@master200.yinzhengjie.org.cn ~]# kubectl get all -n kubernetes-dashboard NAME READY STATUS RESTARTS AGE pod/dashboard-metrics-scraper-76978898b7-hh7pp 1/1 Running 0 75s pod/kubernetes-dashboard-5677747d9d-k8h4n 1/1 Running 0 75s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/dashboard-metrics-scraper ClusterIP 10.105.15.32 <none> 8000/TCP 75s service/kubernetes-dashboard ClusterIP 10.103.133.58 <none> 443/TCP 75s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/dashboard-metrics-scraper 1/1 1 1 75s deployment.apps/kubernetes-dashboard 1/1 1 1 75s NAME DESIRED CURRENT READY AGE replicaset.apps/dashboard-metrics-scraper-76978898b7 1 1 1 75s replicaset.apps/kubernetes-dashboard-5677747d9d 1 1 1 75s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

5>.修改service的类型

[root@master200.yinzhengjie.org.cn ~]# cat recommended.yaml # Copyright 2017 The Kubernetes Authors. # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. apiVersion: v1 kind: Namespace metadata: name: kubernetes-dashboard --- apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: type: NodePort ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kubernetes-dashboard type: Opaque --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-csrf namespace: kubernetes-dashboard type: Opaque data: csrf: "" --- apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-key-holder namespace: kubernetes-dashboard type: Opaque --- kind: ConfigMap apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-settings namespace: kubernetes-dashboard --- kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard rules: # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster", "dashboard-metrics-scraper"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"] verbs: ["get"] --- kind: ClusterRole apiVersion: rbac.authorization.k8s.io/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard rules: # Allow Metrics Scraper to get metrics from the Metrics server - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: kubernetes-dashboard subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard #image: kubernetesui/dashboard:v2.0.0-beta8 image: registry.cn-hangzhou.aliyuncs.com/wez-kubeadmi/dashboard:v2.0.0-beta8 imagePullPolicy: Always ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kubernetes-dashboard # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard nodeSelector: "beta.kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule --- kind: Service apiVersion: v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: ports: - port: 8000 targetPort: 8000 selector: k8s-app: dashboard-metrics-scraper --- kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboard spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: dashboard-metrics-scraper template: metadata: labels: k8s-app: dashboard-metrics-scraper annotations: seccomp.security.alpha.kubernetes.io/pod: 'runtime/default' spec: containers: - name: dashboard-metrics-scraper #image: kubernetesui/metrics-scraper:v1.0.1 image: registry.cn-hangzhou.aliyuncs.com/marmot-k8s/kubernetesui-metrics-scraper:v1.0.1 ports: - containerPort: 8000 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8000 initialDelaySeconds: 30 timeoutSeconds: 30 volumeMounts: - mountPath: /tmp name: tmp-volume securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 serviceAccountName: kubernetes-dashboard nodeSelector: "beta.kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule volumes: - name: tmp-volume emptyDir: {} [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
[root@master200.yinzhengjie.org.cn ~]# kubectl get all -n kubernetes-dashboard NAME READY STATUS RESTARTS AGE pod/dashboard-metrics-scraper-76978898b7-hh7pp 1/1 Running 0 5m23s pod/kubernetes-dashboard-5677747d9d-k8h4n 1/1 Running 0 5m23s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/dashboard-metrics-scraper ClusterIP 10.105.15.32 <none> 8000/TCP 5m23s service/kubernetes-dashboard ClusterIP 10.103.133.58 <none> 443/TCP 5m23s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/dashboard-metrics-scraper 1/1 1 1 5m23s deployment.apps/kubernetes-dashboard 1/1 1 1 5m23s NAME DESIRED CURRENT READY AGE replicaset.apps/dashboard-metrics-scraper-76978898b7 1 1 1 5m23s replicaset.apps/kubernetes-dashboard-5677747d9d 1 1 1 5m23s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl edit service/kubernetes-dashboard -n kubernetes-dashboard service/kubernetes-dashboard edited [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get all -n kubernetes-dashboard NAME READY STATUS RESTARTS AGE pod/dashboard-metrics-scraper-76978898b7-hh7pp 1/1 Running 0 8m24s pod/kubernetes-dashboard-5677747d9d-k8h4n 1/1 Running 0 8m24s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/dashboard-metrics-scraper ClusterIP 10.105.15.32 <none> 8000/TCP 8m24s service/kubernetes-dashboard NodePort 10.103.133.58 <none> 443:32242/TCP 8m24s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/dashboard-metrics-scraper 1/1 1 1 8m24s deployment.apps/kubernetes-dashboard 1/1 1 1 8m24s NAME DESIRED CURRENT READY AGE replicaset.apps/dashboard-metrics-scraper-76978898b7 1 1 1 8m24s replicaset.apps/kubernetes-dashboard-5677747d9d 1 1 1 8m24s [root@master200.yinzhengjie.org.cn ~]#
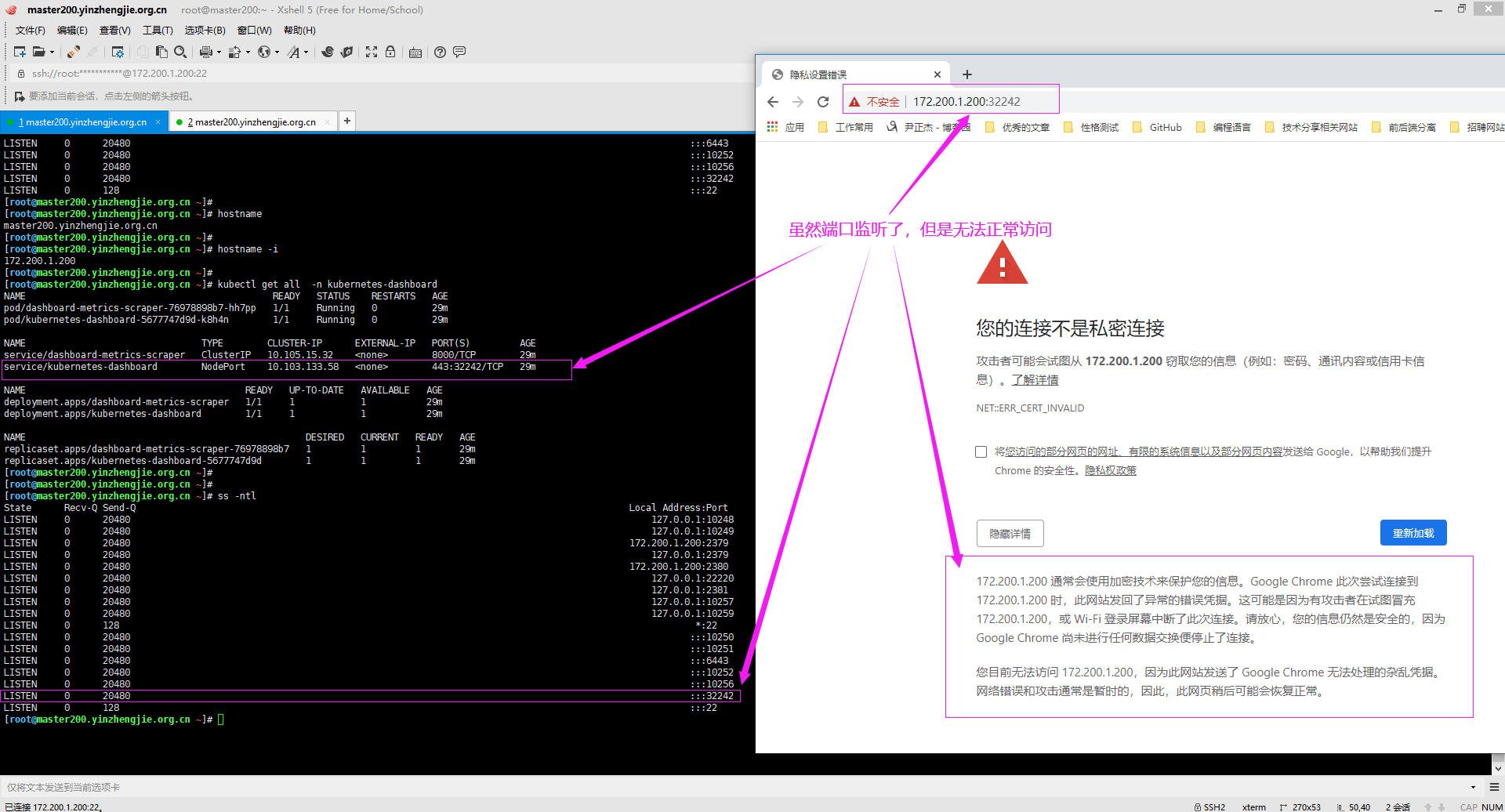
6>.使用Google浏览器访问Dashboard的WebUI失败,但是使用360的浏览器访问正常
如下图所示,使用Google浏览器访问Dashboard的WebUI时失败:
https://master200.yinzhengjie.org.cn:31797/#/login

如下图所示,使用浏览器浏览器访问Dashboard的WebUI时成功: https://master200.yinzhengjie.org.cn:31797/#/login
7>.于是从互联网找到较老的yaml版本并做简要修改(还是中文版本的哟~,接下来的试验我就是用这个版本试验了,毕竟母语看起来舒服点~)

[root@master200.yinzhengjie.org.cn ~]# vim kubernetes-dashboard.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# cat kubernetes-dashboard.yaml # Copyright 2017 The Kubernetes Authors. # # Licensed under the Apache License, Version 2.0 (the "License"); # you may not use this file except in compliance with the License. # You may obtain a copy of the License at # # http://www.apache.org/licenses/LICENSE-2.0 # # Unless required by applicable law or agreed to in writing, software # distributed under the License is distributed on an "AS IS" BASIS, # WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. # See the License for the specific language governing permissions and # limitations under the License. # ------------------- Dashboard Secret ------------------- # apiVersion: v1 kind: Secret metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kube-system type: Opaque --- # ------------------- Dashboard Service Account ------------------- # apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system --- # ------------------- Dashboard Role & Role Binding ------------------- # kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: name: kubernetes-dashboard-minimal namespace: kube-system rules: # Allow Dashboard to create 'kubernetes-dashboard-key-holder' secret. - apiGroups: [""] resources: ["secrets"] verbs: ["create"] # Allow Dashboard to create 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] verbs: ["create"] # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics from heapster. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:"] verbs: ["get"] --- apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: kubernetes-dashboard-minimal namespace: kube-system roleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboard-minimal subjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kube-system --- # ------------------- Dashboard Deployment ------------------- # kind: Deployment apiVersion: apps/v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system spec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard #image: k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1 image: registry.cn-hangzhou.aliyuncs.com/gaven_k8s/kubernetes-dashboard-amd64:v1.10.1 ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule --- # ------------------- Dashboard Service ------------------- # kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system spec: type: NodePort ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
[root@master200.yinzhengjie.org.cn ~]# ll total 16 -rw-r--r-- 1 root root 4689 Feb 19 08:29 kubernetes-dashboard.yaml -rw-r--r-- 1 root root 7772 Feb 19 08:11 recommended.yaml [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl apply -f kubernetes-dashboard.yaml secret/kubernetes-dashboard-certs created serviceaccount/kubernetes-dashboard created role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created deployment.apps/kubernetes-dashboard created service/kubernetes-dashboard created [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get service -n kube-system | grep dashboard kubernetes-dashboard NodePort 10.110.69.244 <none> 443:31358/TCP 14s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

五.登录dashboard
1>.创建服务账户(serviceaccount)资源
[root@master200.yinzhengjie.org.cn ~]# kubectl create serviceaccount ui-admin -n kube-system serviceaccount/ui-admin created [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get sa -n kube-system ui-admin NAME SECRETS AGE ui-admin 1 63s [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
2>.创建集群角色绑定
[root@master200.yinzhengjie.org.cn ~]# kubectl get sa -n kube-system ui-admin NAME SECRETS AGE ui-admin 1 135m [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get clusterrole -n kube-system cluster-admin NAME AGE cluster-admin 14d [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl create clusterrolebinding cluster-ui-admin --clusterrole=cluster-admin --serviceaccount=kube-system:ui-admin clusterrolebinding.rbac.authorization.k8s.io/cluster-ui-admin created [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl get clusterrolebinding cluster-ui-admin NAME AGE cluster-ui-admin 26s [root@master200.yinzhengjie.org.cn ~]#

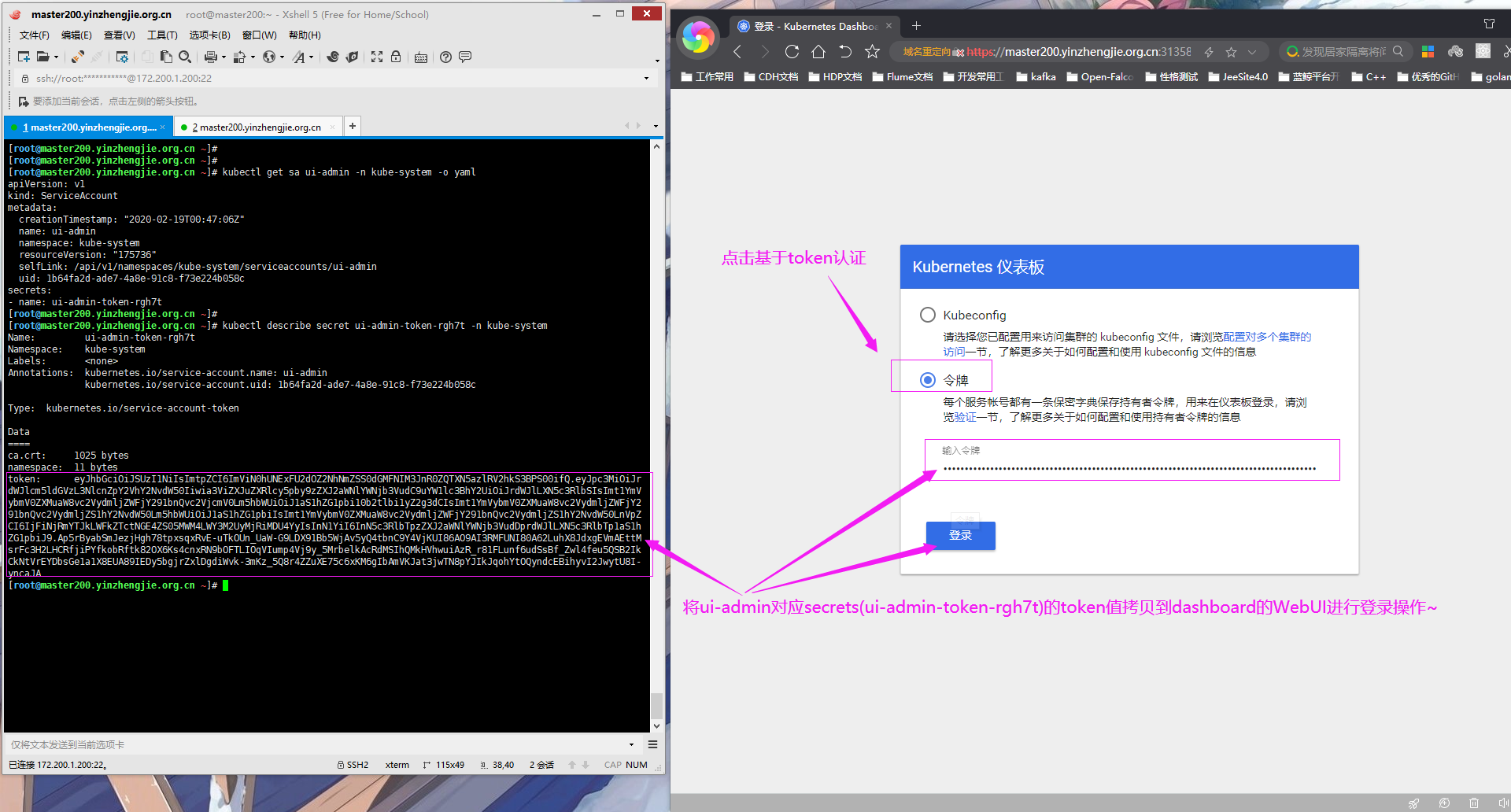
3>.获取ui-admin的token
[root@master200.yinzhengjie.org.cn ~]# kubectl get sa ui-admin -n kube-system -o yaml apiVersion: v1 kind: ServiceAccount metadata: creationTimestamp: "2020-02-19T00:47:06Z" name: ui-admin namespace: kube-system resourceVersion: "175736" selfLink: /api/v1/namespaces/kube-system/serviceaccounts/ui-admin uid: 1b64fa2d-ade7-4a8e-91c8-f73e224b058c secrets: - name: ui-admin-token-rgh7t [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl describe secret ui-admin-token-rgh7t -n kube-system Name: ui-admin-token-rgh7t Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: ui-admin kubernetes.io/service-account.uid: 1b64fa2d-ade7-4a8e-91c8-f73e224b058c Type: kubernetes.io/service-account-token Data ==== ca.crt: 1025 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImViN0hUNExFU2dOZ2NhNmZSS0dGMFNIM3JnR0ZQTXN5azlRV2hkS3BPS00ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV 0Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi1yZ2g3dCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjFiNjRmYTJkLWFkZTctNGE4ZS05MWM4LWY3M2UyMjRiMDU4YyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.Ap5rByabSmJezjHgh78tpxsqxRvE-uTkOUn_UaW-G9LDX91Bb5WjAv5yQ4tbnC9Y4VjKUI86AO9AI3RMFUNI80A62LuhX8JdxgEVmAEttMsrFc3H2LHCRfjiPYfkobRftk82OX6Ks4cnxRN9bOFTLIOqVIump4Vj9y_5MrbelkAcRdMSIhQMkHVhwuiAzR_r81FLunf6udSsBf_Zwl4feu5QSB2IkCkNtVrEYDbsGe1a1X8EUA89IEDy5bgjrZxlDgdiWvk-3mKz_5Q8r4ZZuXE75c6xKM6gIbAmVKJat3jwTN8pYJIkJqohYtOQyndcEBihyvI2JwytU8I-yncaJA[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#

4>.基于ui-admin绑定的secrets的token进行认证,如下图所示
5>.创建kubeconfig的配置文件并在dashboard的WebUI中选择以kubeconfig的方式登录
[root@master200.yinzhengjie.org.cn ~]# kubectl get sa ui-admin -n kube-system -o yaml apiVersion: v1 kind: ServiceAccount metadata: creationTimestamp: "2020-02-19T00:47:06Z" name: ui-admin namespace: kube-system resourceVersion: "175736" selfLink: /api/v1/namespaces/kube-system/serviceaccounts/ui-admin uid: 1b64fa2d-ade7-4a8e-91c8-f73e224b058c secrets: - name: ui-admin-token-rgh7t [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl describe secret -n kube-system ui-admin-token-rgh7t Name: ui-admin-token-rgh7t Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: ui-admin kubernetes.io/service-account.uid: 1b64fa2d-ade7-4a8e-91c8-f73e224b058c Type: kubernetes.io/service-account-token Data ==== namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImViN0hUNExFU2dOZ2NhNmZSS0dGMFNIM3JnR0ZQTXN5azlRV2hkS3BPS00ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV 0Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi1yZ2g3dCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjFiNjRmYTJkLWFkZTctNGE4ZS05MWM4LWY3M2UyMjRiMDU4YyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.Ap5rByabSmJezjHgh78tpxsqxRvE-uTkOUn_UaW-G9LDX91Bb5WjAv5yQ4tbnC9Y4VjKUI86AO9AI3RMFUNI80A62LuhX8JdxgEVmAEttMsrFc3H2LHCRfjiPYfkobRftk82OX6Ks4cnxRN9bOFTLIOqVIump4Vj9y_5MrbelkAcRdMSIhQMkHVhwuiAzR_r81FLunf6udSsBf_Zwl4feu5QSB2IkCkNtVrEYDbsGe1a1X8EUA89IEDy5bgjrZxlDgdiWvk-3mKz_5Q8r4ZZuXE75c6xKM6gIbAmVKJat3jwTN8pYJIkJqohYtOQyndcEBihyvI2JwytU8I-yncaJAca.crt: 1025 bytes [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-cluster yinzhengjie-k8s --server="https://172.200.1.200:6443" --certificate-authority=/etc/kubernetes/pki/ca.crt --embed-certs=true --kubeconfig=/tmp/ui-admin.kubeconfig Cluster "yinzhengjie-k8s" set. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-credentials ui-admin --token=eyJhbGciOiJSUzI1NiIsImtpZCI6ImViN0hUNExFU2dOZ2NhNmZSS0dGMFNIM3JnR0ZQTXN5azlRV2hkS3BPS00ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi1yZ2g3dCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjFiNjRmYTJkLWFkZTctNGE4ZS05MWM4LWY3M2UyMjRiMDU4YyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.Ap5rByabSmJezjHgh78tpxsqxRvE-uTkOUn_UaW-G9LDX91Bb5WjAv5yQ4tbnC9Y4VjKUI86AO9AI3RMFUNI80A62LuhX8JdxgEVmAEttMsrFc3H2LHCRfjiPYfkobRftk82OX6Ks4cnxRN9bOFTLIOqVIump4Vj9y_5MrbelkAcRdMSIhQMkHVhwuiAzR_r81FLunf6udSsBf_Zwl4feu5QSB2IkCkNtVrEYDbsGe1a1X8EUA89IEDy5bgjrZxlDgdiWvk-3mKz_5Q8r4ZZuXE75c6xKM6gIbAmVKJat3jwTN8pYJIkJqohYtOQyndcEBihyvI2JwytU8I-yncaJA --kubeconfig=/tmp/ui-admin.kubeconfig User "ui-admin" set. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config set-context ui-admin@yinzhengjie-k8s --cluster=yinzhengjie-k8s --user=ui-admin --kubeconfig=/tmp/ui-admin.kubeconfig Context "ui-admin@yinzhengjie-k8s" created. [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config use-context ui-admin@yinzhengjie-k8s --kubeconfig=/tmp/ui-admin.kubeconfig Switched to context "ui-admin@yinzhengjie-k8s". [root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]# kubectl config view --kubeconfig=/tmp/ui-admin.kubeconfig apiVersion: v1 clusters: - cluster: certificate-authority-data: DATA+OMITTED server: https://172.200.1.200:6443 name: yinzhengjie-k8s contexts: - context: cluster: yinzhengjie-k8s user: ui-admin name: ui-admin@yinzhengjie-k8s current-context: ui-admin@yinzhengjie-k8s kind: Config preferences: {} users: - name: ui-admin user: token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImViN0hUNExFU2dOZ2NhNmZSS0dGMFNIM3JnR0ZQTXN5azlRV2hkS3BPS00ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0 Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi1yZ2g3dCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjFiNjRmYTJkLWFkZTctNGE4ZS05MWM4LWY3M2UyMjRiMDU4YyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.Ap5rByabSmJezjHgh78tpxsqxRvE-uTkOUn_UaW-G9LDX91Bb5WjAv5yQ4tbnC9Y4VjKUI86AO9AI3RMFUNI80A62LuhX8JdxgEVmAEttMsrFc3H2LHCRfjiPYfkobRftk82OX6Ks4cnxRN9bOFTLIOqVIump4Vj9y_5MrbelkAcRdMSIhQMkHVhwuiAzR_r81FLunf6udSsBf_Zwl4feu5QSB2IkCkNtVrEYDbsGe1a1X8EUA89IEDy5bgjrZxlDgdiWvk-3mKz_5Q8r4ZZuXE75c6xKM6gIbAmVKJat3jwTN8pYJIkJqohYtOQyndcEBihyvI2JwytU8I-yncaJA[root@master200.yinzhengjie.org.cn ~]# [root@master200.yinzhengjie.org.cn ~]#
