1.根据P4教程,将basic和basic_tunnel两个案例程序补充完整,成功运行。
(1)补充并运行basic代码
/* -*- P4_16 -*- */
#include <core.p4>
#include <v1model.p4>
const bit<16> TYPE_IPV4 = 0x800;
/*************************************************************************
*********************** H E A D E R S ***********************************
*************************************************************************/
typedef bit<9> egressSpec_t;
typedef bit<48> macAddr_t;
typedef bit<32> ip4Addr_t;
header ethernet_t {
macAddr_t dstAddr;
macAddr_t srcAddr;
bit<16> etherType;
}
header ipv4_t {
bit<4> version;
bit<4> ihl;
bit<8> diffserv;
bit<16> totalLen;
bit<16> identification;
bit<3> flags;
bit<13> fragOffset;
bit<8> ttl;
bit<8> protocol;
bit<16> hdrChecksum;
ip4Addr_t srcAddr;
ip4Addr_t dstAddr;
}
struct metadata {
/* empty */
}
struct headers {
ethernet_t ethernet;
ipv4_t ipv4;
}
/*************************************************************************
*********************** P A R S E R ***********************************
*************************************************************************/
parser MyParser(packet_in packet,
out headers hdr,
inout metadata meta,
inout standard_metadata_t standard_metadata){
state start {
transition parser_ethernet; //转移到以太网包头的状态
}
state packet_ethernet{
packet.extract(hdr.ethernet); //提取以太网包头
transition select(hdr.ethernet.etherType){ //由协议转移到相关状态
0x0800: parser_ipv4; //ipv4协议
default: accept;
}
}
state parser_ipv4{
packet.extract(hdr.ipv4); //提取ipv4包头
transition accept;
}
}
/*************************************************************************
************ C H E C K S U M V E R I F I C A T I O N *************
*************************************************************************/
control MyVerifyChecksum(inout headers hdr, inout metadata meta) {
apply { }
}
/*************************************************************************
************** I N G R E S S P R O C E S S I N G *******************
*************************************************************************/
control MyIngress(inout headers hdr,
inout metadata meta,
inout standard_metadata_t standard_metadata) {
action drop() {
mark_to_drop(standard_metadata);
}
action ipv4_forward(macAddr_t dstAddr, egressSpec_t port) {
//转发步骤
standard_metadata.egress_spec = port; //设置下一跳的出口端口
hdr.ethernet.srcAddr = hdr.ethernet.dstAddr; //更新源地址(到达下一跳)
hdr.ethernet.dstAddr = dstAddr; //更新目标地址
hdr.ipv4.ttl = hdr.ipv4.ttl - 1; //ttl减1
}
table ipv4_lpm {
key = {
hdr.ipv4.dstAddr: lpm;
}
actions = {
ipv4_forward;
drop;
NoAction;
}
size = 1024;
default_action = NoAction();
}
apply {
if (hdr.ipv4.isValid()) {
ipv4_lpm.apply();
}
}
}
/*************************************************************************
**************** E G R E S S P R O C E S S I N G *******************
*************************************************************************/
control MyEgress(inout headers hdr,
inout metadata meta,
inout standard_metadata_t standard_metadata) {
apply { }
}
/*************************************************************************
************* C H E C K S U M C O M P U T A T I O N **************
*************************************************************************/
control MyComputeChecksum(inout headers hdr, inout metadata meta) {
apply {
update_checksum(
hdr.ipv4.isValid(),
{ hdr.ipv4.version,
hdr.ipv4.ihl,
hdr.ipv4.diffserv,
hdr.ipv4.totalLen,
hdr.ipv4.identification,
hdr.ipv4.flags,
hdr.ipv4.fragOffset,
hdr.ipv4.ttl,
hdr.ipv4.protocol,
hdr.ipv4.srcAddr,
hdr.ipv4.dstAddr },
hdr.ipv4.hdrChecksum,
HashAlgorithm.csum16);
}
}
/*************************************************************************
*********************** D E P A R S E R *******************************
*************************************************************************/
control MyDeparser(packet_out packet, in headers hdr) {
//数据包重组
apply {
packet.emit(hdr.ethernet); // 这里要注意先后顺序
packet.emit(hdr.ipv4);
}
}
/*************************************************************************
*********************** S W I T C H *******************************
*************************************************************************/
V1Switch(
MyParser(),
MyVerifyChecksum(),
MyIngress(),
MyEgress(),
MyComputeChecksum(),
MyDeparser()
) main;


(2)补充并运行支持基本隧道协议的basic_tunnel代码
/* -*- P4_16 -*- */
#include <core.p4>
#include <v1model.p4>
// NOTE: new type added here
const bit<16> TYPE_MYTUNNEL = 0x1212;
const bit<16> TYPE_IPV4 = 0x800;
/*************************************************************************
*********************** H E A D E R S ***********************************
*************************************************************************/
typedef bit<9> egressSpec_t;
typedef bit<48> macAddr_t;
typedef bit<32> ip4Addr_t;
header ethernet_t {
macAddr_t dstAddr;
macAddr_t srcAddr;
bit<16> etherType;
}
// NOTE: added new header type
header myTunnel_t {
bit<16> proto_id;
bit<16> dst_id;
}
header ipv4_t {
bit<4> version;
bit<4> ihl;
bit<8> diffserv;
bit<16> totalLen;
bit<16> identification;
bit<3> flags;
bit<13> fragOffset;
bit<8> ttl;
bit<8> protocol;
bit<16> hdrChecksum;
ip4Addr_t srcAddr;
ip4Addr_t dstAddr;
}
struct metadata {
/* empty */
}
// NOTE: Added new header type to headers struct
struct headers {
ethernet_t ethernet;
myTunnel_t myTunnel;
ipv4_t ipv4;
}
/*************************************************************************
*********************** P A R S E R ***********************************
*************************************************************************/
parser MyParser(packet_in packet,
out headers hdr,
inout metadata meta,
inout standard_metadata_t standard_metadata) {
state start {
transition parse_ethernet;
}
state parse_ethernet {
packet.extract(hdr.ethernet);
transition select(hdr.ethernet.etherType) {
TYPE_MYTUNNEL: parse_myTunnel; //转向隧道状态
TYPE_IPV4 : parse_ipv4;
default : accept;
}
}
state parse_ipv4 {
packet.extract(hdr.ipv4);
transition accept;
}
state parse_myTunnel { //隧道状态
packet.extract(hdr.myTunnel);
transition select(hdr.myTunnel.proto_id) {
TYPE_IPV4: parse_ipv4;
default: accept;
}
}
}
/*************************************************************************
************ C H E C K S U M V E R I F I C A T I O N *************
*************************************************************************/
control MyVerifyChecksum(inout headers hdr, inout metadata meta) {
apply { }
}
/*************************************************************************
************** I N G R E S S P R O C E S S I N G *******************
*************************************************************************/
control MyIngress(inout headers hdr,
inout metadata meta,
inout standard_metadata_t standard_metadata) {
action drop() {
mark_to_drop(standard_metadata);
}
action ipv4_forward(macAddr_t dstAddr, egressSpec_t port) {
standard_metadata.egress_spec = port;
hdr.ethernet.srcAddr = hdr.ethernet.dstAddr;
hdr.ethernet.dstAddr = dstAddr;
hdr.ipv4.ttl = hdr.ipv4.ttl - 1;
}
table ipv4_lpm {
key = {
hdr.ipv4.dstAddr: lpm;
}
actions = {
ipv4_forward;
drop;
NoAction;
}
size = 1024;
default_action = drop();
}
//将出口端口号设置为控制平面提供的端口号
action myTunnel_forward(egressSpec_t port){
standard_metadata.egress_spec = port;
}
//如果表中myTunnel_forward存在匹配项,则该表应调用该drop动作,否则应调用该动作。
table myTunnel_exact{
key = {
hdr.myTunnel.dst_id: exact; //要匹配的动作和模式,exact是精准匹配
}
actions = { //可选动作
myTunnel_forward;
drop;
}
size = 1024;
default_action = drop(); //默认动作
}
apply {
// 只允许不是通道和是ipv4的包
if (hdr.ipv4.isValid() && !hdr.myTunnel.isValid()) {
ipv4_lpm.apply();
}
// 隧道包
if (hdr.myTunnel.isValid()) {
myTunnel_exact.apply();
}
}
}
/*************************************************************************
**************** E G R E S S P R O C E S S I N G *******************
*************************************************************************/
control MyEgress(inout headers hdr,
inout metadata meta,
inout standard_metadata_t standard_metadata) {
apply { }
}
/*************************************************************************
************* C H E C K S U M C O M P U T A T I O N **************
*************************************************************************/
control MyComputeChecksum(inout headers hdr, inout metadata meta) {
apply {
update_checksum(
hdr.ipv4.isValid(),
{ hdr.ipv4.version,
hdr.ipv4.ihl,
hdr.ipv4.diffserv,
hdr.ipv4.totalLen,
hdr.ipv4.identification,
hdr.ipv4.flags,
hdr.ipv4.fragOffset,
hdr.ipv4.ttl,
hdr.ipv4.protocol,
hdr.ipv4.srcAddr,
hdr.ipv4.dstAddr },
hdr.ipv4.hdrChecksum,
HashAlgorithm.csum16);
}
}
/*************************************************************************
*********************** D E P A R S E R *******************************
*************************************************************************/
control MyDeparser(packet_out packet, in headers hdr) {
apply {
packet.emit(hdr.ethernet);
packet.emit(hdr.myTunnel); //加上隧道包
packet.emit(hdr.ipv4);
}
}
/*************************************************************************
*********************** S W I T C H *******************************
*************************************************************************/
V1Switch(
MyParser(),
MyVerifyChecksum(),
MyIngress(),
MyEgress(),
MyComputeChecksum(),
MyDeparser()
) main;
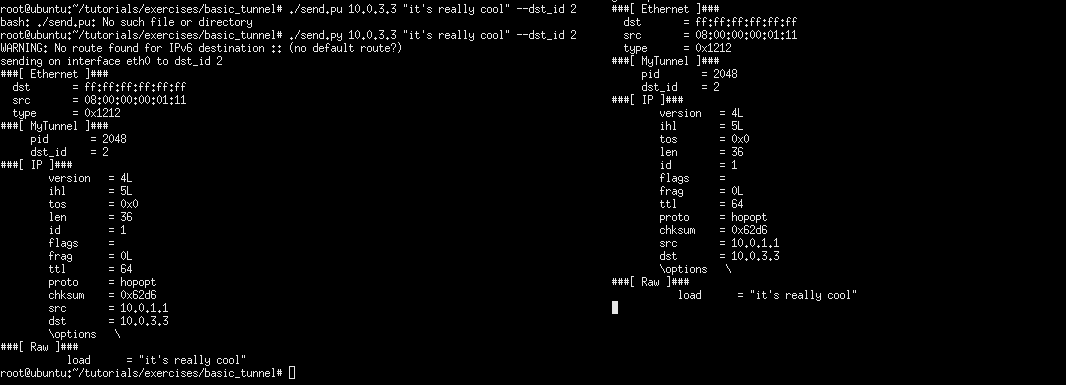
使用xterm命令打开h1,h2终端
h2
./receive.py
h1
./send.py 10.0.2.2 "it's cool"

修改发送目的地址,添加额外隧道
./send.py 10.0.3.3 "it's really cool" --dst_id 2
h2收到消息,走的是已经设置好的隧道
2.说明案例程序的编译执行流程。
1.对于basic.p4
在运行make run之后,自动完成编译basic.p4,在Mininet中启动pod-topo,并使用适当的P4程序+表条目配置所有交换机,使用pod-topo/topology.json中列出的命令配置所有主机
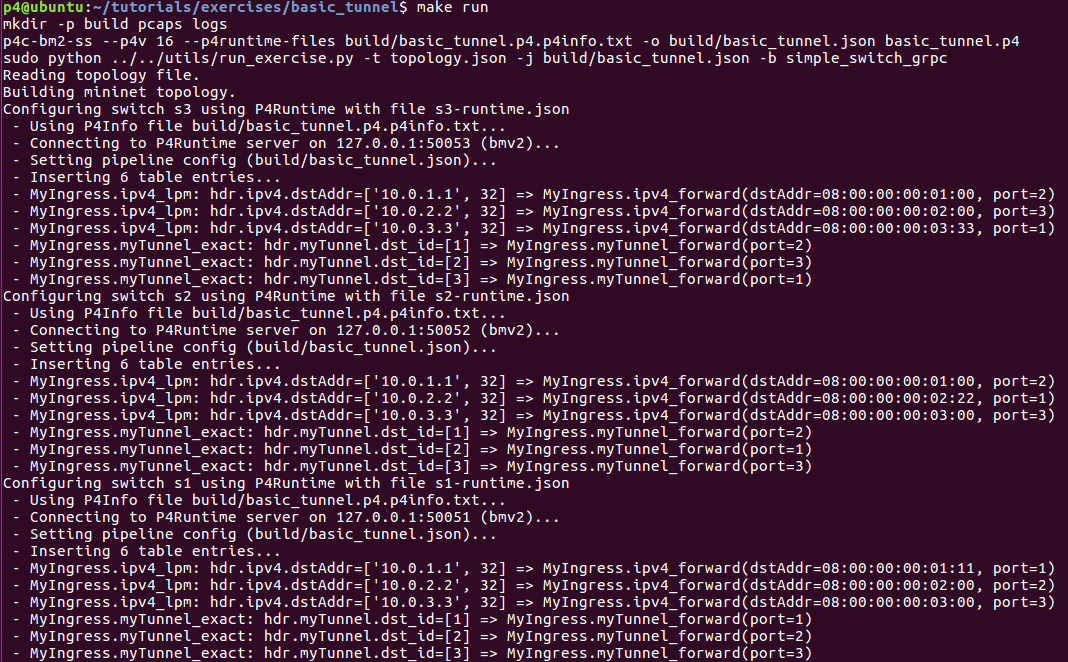
2.对于basic_tunnel.p4
在运行make run之后,自动完成编译basic_tunnel.p4,启动一个Mininet实例与三个开关(s1,s2,s3),被配置成三角形,每个连接到一个主机(h1,h2,和h3),该主机被分配的IP地址10.0.1.1,10.0.2.2和10.0.3.3
3.提交你对P4的认识和体会。
P4是一种高级的数据面编程语言,称为数据面编程,它定义一个匹配字段,定义自己的动作类型,定义自己的流程图,甚至形成一行。因此,P4可以更好地补偿OpenFULL,并且只能通过现有协议定义流项,但是P4不同于OpenFLASH定位。学习能力有限,无法理解和解读openflow和P4。但是openflow更容易。
4.完成教程的其他任意一个案例(选做)。
选择mycontroller案例来完成
#!/usr/bin/env python2
import argparse
import grpc
import os
import sys
from time import sleep
# Import P4Runtime lib from parent utils dir
# Probably there's a better way of doing this.
sys.path.append(
os.path.join(os.path.dirname(os.path.abspath(__file__)),
'../../utils/'))
import p4runtime_lib.bmv2
from p4runtime_lib.switch import ShutdownAllSwitchConnections
import p4runtime_lib.helper
SWITCH_TO_HOST_PORT = 1
SWITCH_TO_SWITCH_PORT = 2
def writeTunnelRules(p4info_helper, ingress_sw, egress_sw, tunnel_id,
dst_eth_addr, dst_ip_addr):
"""
Installs three rules:
1) An tunnel ingress rule on the ingress switch in the ipv4_lpm table that
encapsulates traffic into a tunnel with the specified ID
2) A transit rule on the ingress switch that forwards traffic based on
the specified ID
3) An tunnel egress rule on the egress switch that decapsulates traffic
with the specified ID and sends it to the host
:param p4info_helper: the P4Info helper
:param ingress_sw: the ingress switch connection
:param egress_sw: the egress switch connection
:param tunnel_id: the specified tunnel ID
:param dst_eth_addr: the destination IP to match in the ingress rule
:param dst_ip_addr: the destination Ethernet address to write in the
egress rule
"""
# 1) Tunnel Ingress Rule
table_entry = p4info_helper.buildTableEntry(
table_name="MyIngress.ipv4_lpm",
match_fields={
"hdr.ipv4.dstAddr": (dst_ip_addr, 32)
},
action_name="MyIngress.myTunnel_ingress",
action_params={
"dst_id": tunnel_id,
})
ingress_sw.WriteTableEntry(table_entry)
print "Installed ingress tunnel rule on %s" % ingress_sw.name
# 2) Tunnel Transit Rule
# The rule will need to be added to the myTunnel_exact table and match on
# the tunnel ID (hdr.myTunnel.dst_id). Traffic will need to be forwarded
# using the myTunnel_forward action on the port connected to the next switch.
#
# For our simple topology, switch 1 and switch 2 are connected using a
# link attached to port 2 on both switches. We have defined a variable at
# the top of the file, SWITCH_TO_SWITCH_PORT, that you can use as the output
# port for this action.
#
# We will only need a transit rule on the ingress switch because we are
# using a simple topology. In general, you'll need on transit rule for
# each switch in the path (except the last switch, which has the egress rule),
# and you will need to select the port dynamically for each switch based on
# your topology.
# TODO build the transit rule
# TODO install the transit rule on the ingress switch
table_entry = p4info_helper.buildTableEntry(
table_name="MyIngress.myTunnel_exact",
match_fields={
"hdr.myTunnel.dst_id": tunnel_id
},
action_name="MyIngress.myTunnel_forward",
action_params={
"port": SWITCH_TO_SWITCH_PORT
})
ingress_sw.WriteTableEntry(table_entry)
print "Installed transit tunnel rule on %s" % ingress_sw.name
# 3) Tunnel Egress Rule
# For our simple topology, the host will always be located on the
# SWITCH_TO_HOST_PORT (port 1).
# In general, you will need to keep track of which port the host is
# connected to.
table_entry = p4info_helper.buildTableEntry(
table_name="MyIngress.myTunnel_exact",
match_fields={
"hdr.myTunnel.dst_id": tunnel_id
},
action_name="MyIngress.myTunnel_egress",
action_params={
"dstAddr": dst_eth_addr,
"port": SWITCH_TO_HOST_PORT
})
egress_sw.WriteTableEntry(table_entry)
print "Installed egress tunnel rule on %s" % egress_sw.name
def readTableRules(p4info_helper, sw):
"""
Reads the table entries from all tables on the switch.
:param p4info_helper: the P4Info helper
:param sw: the switch connection
"""
print '
----- Reading tables rules for %s -----' % sw.name
for response in sw.ReadTableEntries():
for entity in response.entities:
entry = entity.table_entry
# TODO For extra credit, you can use the p4info_helper to translate
# the IDs in the entry to names
table_name = p4info_helper.get_tables_name(entry.table_id)
print '%s: ' % table_name,
for m in entry.match:
print p4info_helper.get_match_field_name(table_name, m.field_id),
print '%r' % (p4info_helper.get_match_field_value(m),),
action = entry.action.action
action_name = p4info_helper.get_actions_name(action.action_id)
print '->', action_name,
for p in action.params:
print p4info_helper.get_action_param_name(action_name, p.param_id),
print '%r' % p.value,
print
def printCounter(p4info_helper, sw, counter_name, index):
"""
Reads the specified counter at the specified index from the switch. In our
program, the index is the tunnel ID. If the index is 0, it will return all
values from the counter.
:param p4info_helper: the P4Info helper
:param sw: the switch connection
:param counter_name: the name of the counter from the P4 program
:param index: the counter index (in our case, the tunnel ID)
"""
for response in sw.ReadCounters(p4info_helper.get_counters_id(counter_name), index):
for entity in response.entities:
counter = entity.counter_entry
print "%s %s %d: %d packets (%d bytes)" % (
sw.name, counter_name, index,
counter.data.packet_count, counter.data.byte_count
)
def printGrpcError(e):
print "gRPC Error:", e.details(),
status_code = e.code()
print "(%s)" % status_code.name,
traceback = sys.exc_info()[2]
print "[%s:%d]" % (traceback.tb_frame.f_code.co_filename, traceback.tb_lineno)
def main(p4info_file_path, bmv2_file_path):
# Instantiate a P4Runtime helper from the p4info file
p4info_helper = p4runtime_lib.helper.P4InfoHelper(p4info_file_path)
try:
# Create a switch connection object for s1 and s2;
# this is backed by a P4Runtime gRPC connection.
# Also, dump all P4Runtime messages sent to switch to given txt files.
s1 = p4runtime_lib.bmv2.Bmv2SwitchConnection(
name='s1',
address='127.0.0.1:50051',
device_id=0,
proto_dump_file='logs/s1-p4runtime-requests.txt')
s2 = p4runtime_lib.bmv2.Bmv2SwitchConnection(
name='s2',
address='127.0.0.1:50052',
device_id=1,
proto_dump_file='logs/s2-p4runtime-requests.txt')
# Send master arbitration update message to establish this controller as
# master (required by P4Runtime before performing any other write operation)
s1.MasterArbitrationUpdate()
s2.MasterArbitrationUpdate()
# Install the P4 program on the switches
s1.SetForwardingPipelineConfig(p4info=p4info_helper.p4info,
bmv2_json_file_path=bmv2_file_path)
print "Installed P4 Program using SetForwardingPipelineConfig on s1"
s2.SetForwardingPipelineConfig(p4info=p4info_helper.p4info,
bmv2_json_file_path=bmv2_file_path)
print "Installed P4 Program using SetForwardingPipelineConfig on s2"
# Write the rules that tunnel traffic from h1 to h2
writeTunnelRules(p4info_helper, ingress_sw=s1, egress_sw=s2, tunnel_id=100,
dst_eth_addr="08:00:00:00:02:22", dst_ip_addr="10.0.2.2")
# Write the rules that tunnel traffic from h2 to h1
writeTunnelRules(p4info_helper, ingress_sw=s2, egress_sw=s1, tunnel_id=200,
dst_eth_addr="08:00:00:00:01:11", dst_ip_addr="10.0.1.1")
# TODO Uncomment the following two lines to read table entries from s1 and s2
readTableRules(p4info_helper, s1)
readTableRules(p4info_helper, s2)
# Print the tunnel counters every 2 seconds
while True:
sleep(2)
print '
----- Reading tunnel counters -----'
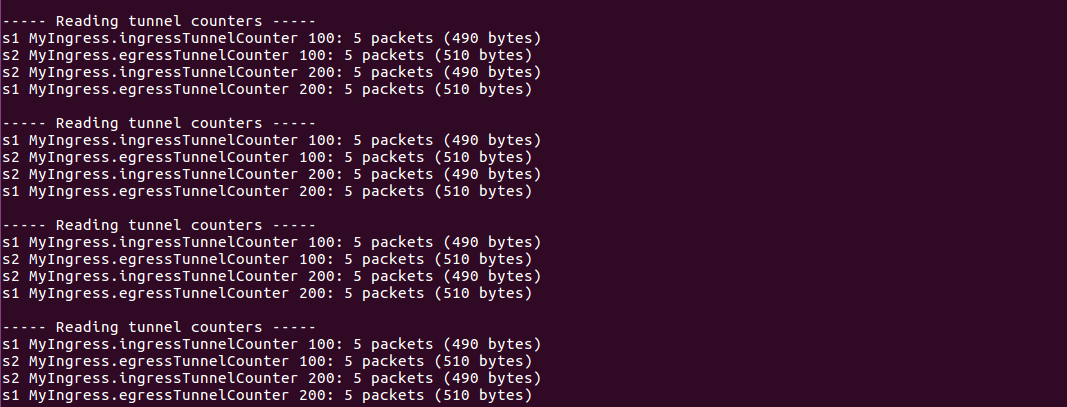
printCounter(p4info_helper, s1, "MyIngress.ingressTunnelCounter", 100)
printCounter(p4info_helper, s2, "MyIngress.egressTunnelCounter", 100)
printCounter(p4info_helper, s2, "MyIngress.ingressTunnelCounter", 200)
printCounter(p4info_helper, s1, "MyIngress.egressTunnelCounter", 200)
except KeyboardInterrupt:
print " Shutting down."
except grpc.RpcError as e:
printGrpcError(e)
ShutdownAllSwitchConnections()
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='P4Runtime Controller')
parser.add_argument('--p4info', help='p4info proto in text format from p4c',
type=str, action="store", required=False,
default='./build/advanced_tunnel.p4.p4info.txt')
parser.add_argument('--bmv2-json', help='BMv2 JSON file from p4c',
type=str, action="store", required=False,
default='./build/advanced_tunnel.json')
args = parser.parse_args()
if not os.path.exists(args.p4info):
parser.print_help()
print "
p4info file not found: %s
Have you run 'make'?" % args.p4info
parser.exit(1)
if not os.path.exists(args.bmv2_json):
parser.print_help()
print "
BMv2 JSON file not found: %s
Have you run 'make'?" % args.bmv2_json
parser.exit(1)
main(args.p4info, args.bmv2_json)
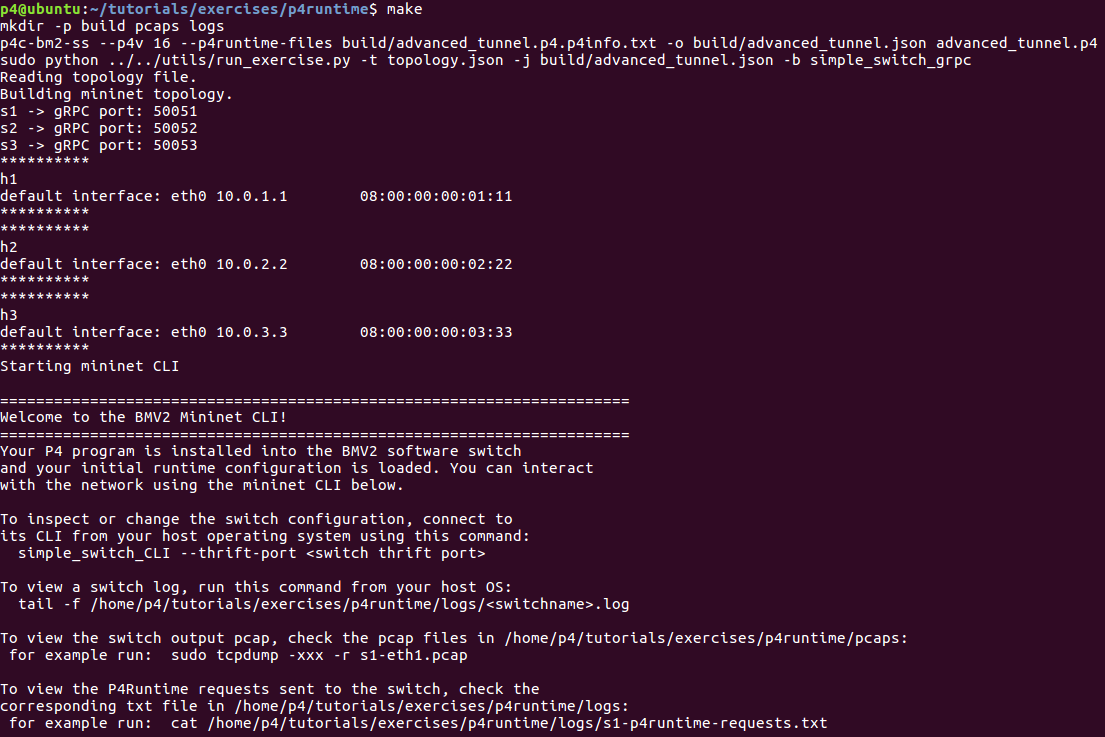
启动网络
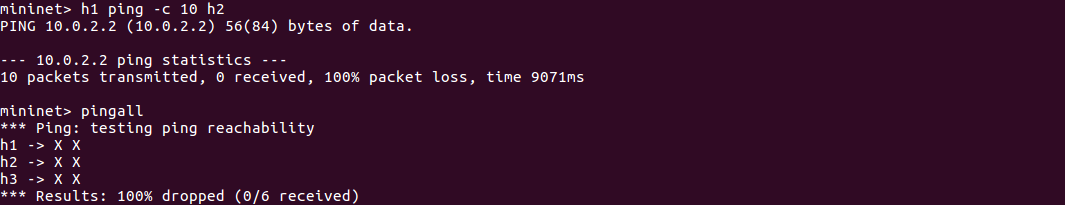
试试h1 ping h2和pingall。因为交换机中没有规则,所以所有Ping都不能成功。
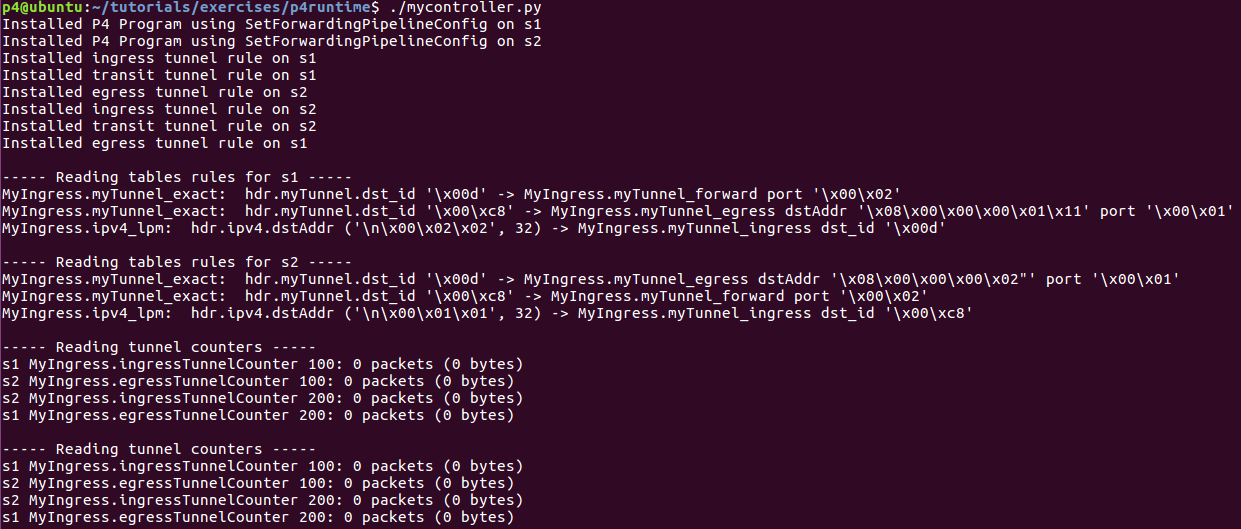
打开另一个终端。输入命令打开控制器。每隔一秒打印隧道入口和出口计数器。
cd ~/tutorials/exercises/p4runtime
./mycontroller.py
在第一个终端上再次尝试ping命令后,会发现ping路径,并且终端2计数器会更改。