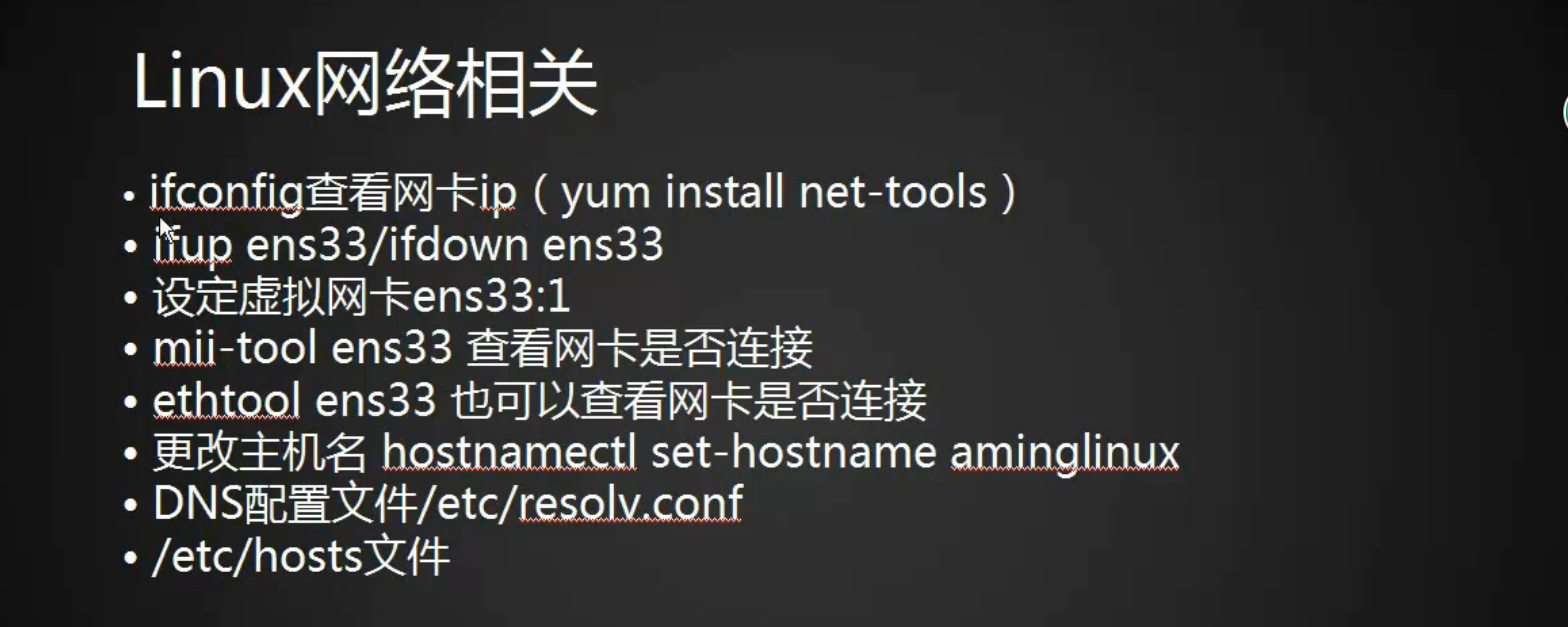
[root@lizhipeng01 ~]# ifconfig -a
eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.5.128 netmask 255.255.255.0 broadcast 192.168.5.255
inet6 fe80::20c:29ff:fe7e:1a2f prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:7e:1a:2f txqueuelen 1000 (Ethernet)
RX packets 90296 bytes 35206086 (33.5 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 306605 bytes 78269419 (74.6 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 0 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@lizhipeng01 ~]# ifdown eno16777736 && ifup eno16777736
Device 'eno16777736' successfully disconnected.
成功激活的连接(D-Bus 激活路径:/org/freedesktop/NetworkManager/ActiveConnection/2)
[root@lizhipeng01 ~]# cd /etc/sysconfig/network-scripts/
[root@lizhipeng01 network-scripts]# ls
ifcfg-eno16777736 ifdown-eth ifdown-isdn ifdown-sit ifup ifup-ib ifup-plip ifup-routes ifup-tunnel network-functions-ipv6
ifcfg-lo ifdown-ib ifdown-post ifdown-Team ifup-aliases ifup-ippp ifup-plusb ifup-sit ifup-wireless
ifdown ifdown-ippp ifdown-ppp ifdown-TeamPort ifup-bnep ifup-ipv6 ifup-post ifup-Team init.ipv6-global
ifdown-bnep ifdown-ipv6 ifdown-routes ifdown-tunnel ifup-eth ifup-isdn ifup-ppp ifup-TeamPort network-functions
[root@lizhipeng01 network-scripts]# cp ifcfg-eno16777736 ifcfg-eno16777736:0
[root@lizhipeng01 ~]# ifdown eno16777736 && ifup eno16777736
Device 'eno16777736' successfully disconnected.
成功激活的连接(D-Bus 激活路径:/org/freedesktop/NetworkManager/ActiveConnection/2)
[root@lizhipeng01 ~]# ifconfig
eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.5.128 netmask 255.255.255.0 broadcast 192.168.5.255
inet6 fe80::20c:29ff:fe7e:1a2f prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:7e:1a:2f txqueuelen 1000 (Ethernet)
RX packets 456 bytes 45573 (44.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 331 bytes 44706 (43.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eno16777736:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.5.150 netmask 255.255.255.0 broadcast 192.168.5.255 多了一个
ether 00:0c:29:7e:1a:2f txqueuelen 1000 (Ethernet)
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 0 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@lizhipeng01 ~]# mii-tool eno16777736
eno16777736: negotiated 1000baseT-FD flow-control, link ok 连接了网线
[root@lizhipeng01 ~]# hostnamectl set-hostname lizhipenglinux01 更改主机名
[root@lizhipeng01 ~]# hostname
lizhipenglinux01
[root@lizhipeng01 ~]# bash 进入一个子进程
[root@lizhipenglinux01 ~]# exit
exit
[root@lizhipeng01 ~]# cat /etc/hostname
lizhipenglinux01
[root@lizhipeng01 ~]# cat /etc/resolv.conf
# Generated by NetworkManager
nameserver 119.29.29.29
[root@lizhipeng01 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
[root@lizhipeng01 ~]# vi /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.5.150 www.qq123.com
[root@lizhipeng01 ~]# ping www.qq123.com
PING www.qq123.com (192.168.5.150) 56(84) bytes of data.
64 bytes from www.qq123.com (192.168.5.150): icmp_seq=1 ttl=64 time=0.041 ms
64 bytes from www.qq123.com (192.168.5.150): icmp_seq=2 ttl=64 time=0.073 ms
64 bytes from www.qq123.com (192.168.5.150): icmp_seq=3 ttl=64 time=0.041 ms
64 bytes from www.qq123.com (192.168.5.150): icmp_seq=4 ttl=64 time=0.078 ms

[root@lizhipeng01 ~]# systemctl stop firewalld 关闭firewalld服务
[root@lizhipeng01 ~]# systemctl disable firewalld 禁止firewalld服务开机启动
[root@lizhipeng01 ~]# yum install -y iptables-services 安装iptables-services,这样就可以使用之前版本的iptables
[root@lizhipeng01 ~]# systemctl enable iptables 让它开机启动
[root@lizhipeng01 ~]# systemctl start iptables 启动iptables服务
[root@lizhipeng01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
344 23716 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
19 1633 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 200 packets, 21776 bytes)
pkts bytes target prot opt in out source destination
netfilter的5个表
filter表主要用于过滤包,是系统预设的表。该表内建3个链:INPUT、OUTPUT和FORWARD。input链作用于进入本机的包,output链作用于本机送出的包,forward链作用于那些跟本机无关的包。
nat表主要用于网络地址的转换,它也有3个链。prerouting链的作用是在包刚刚到达防火墙时改变它的目的地址,output链的作用是改变本地产生的包的目的地址,postrouting链的作用是在包即将离开防火墙时改变其源地址
mangle表主要用于给数据包做标记。
raw表可以实现不追踪某些数据包,默认系统的数据包都会被追踪,但追踪势必消耗一定的资源,所以可以用raw表来指定某些端口的包不被追踪。
security 表在centos6中是没有的,它用于强制访问控制(MAC)的网络规则。
netfilter的5个链
5个链分别为PREROUTING,INPUT,FORWARD,OUTPUT,POSTROUTING。
PREROUTING:数据包进入路由表之前。
INPUT:通过路由表后目的地本机。
FORWARDING:通过路由表后,目的地不为本机
OUTPUT:由本机产生,向外转发。
POSTROUTING:发送到网卡接口之前

iptables基本语法
(1)查看规则以及清楚规则
[root@lizhipenglinux01 ~]# iptables -nvL 默认的规则
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
146 13775 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
1 52 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
166 14005 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 121 packets, 10677 bytes)
pkts bytes target prot opt in out source destination
[root@lizhipenglinux01 ~]# service iptables restart 重启服务
Redirecting to /bin/systemctl restart iptables.service
[root@lizhipenglinux01 ~]# cat /etc/sysconfig/iptables 规则保存在该路径下
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
[root@lizhipenglinux01 ~]# iptables -F 清空规则
[root@lizhipenglinux01 ~]# iptables -nvL 查看,没有了,但是实际文件里面还有,如下 cat /etc/sysconfig/iptables
Chain INPUT (policy ACCEPT 40 packets, 2640 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 21 packets, 2044 bytes)
pkts bytes target prot opt in out source destination
[root@lizhipenglinux01 ~]# cat /etc/sysconfig/iptables
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
[root@lizhipenglinux01 ~]# service iptables restart 重启服务
Redirecting to /bin/systemctl restart iptables.service 配置文件里面的规则会重新加载
[root@lizhipenglinux01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
28 1848 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 15 packets, 1444 bytes)
pkts bytes target prot opt in out source destination
[root@lizhipenglinux01 ~]# iptables -t filter -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
81 5476 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 47 packets, 5244 bytes)
pkts bytes target prot opt in out source destination
[root@lizhipenglinux01 ~]# iptables -Z; iptables -nvL -Z,清空数据pkts byte
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
(2)增加/删除一条规则,其用法如下:
iptables -A INPUT -s 192.168.188.1 -p tcp --sport 1234 -d 192.168.188.128 --dport 80 -j DROP
没有加-t选项,所有针对的是filter表。这条规则中各个选项的作用如下。
-A/-D:表示增加/删除一条规则。
-I:表示插入一条规则,其实效果跟-A一样。
-p:表示指定协议,可以是tcp、udp或icmp。
--dport:跟-p一起使用,表示指定目标端口。
--sport:跟-p一起使用,表示指定源端口。
-s:表示指定源IP(可以是一个IP段)
-d:表示指定目的IP(可以是一个IP段)
-j:后面跟动作,其中ACCEPT表示允许包,DROP表示丢掉包,REJECT表示拒绝包。
-i:表示指定网卡
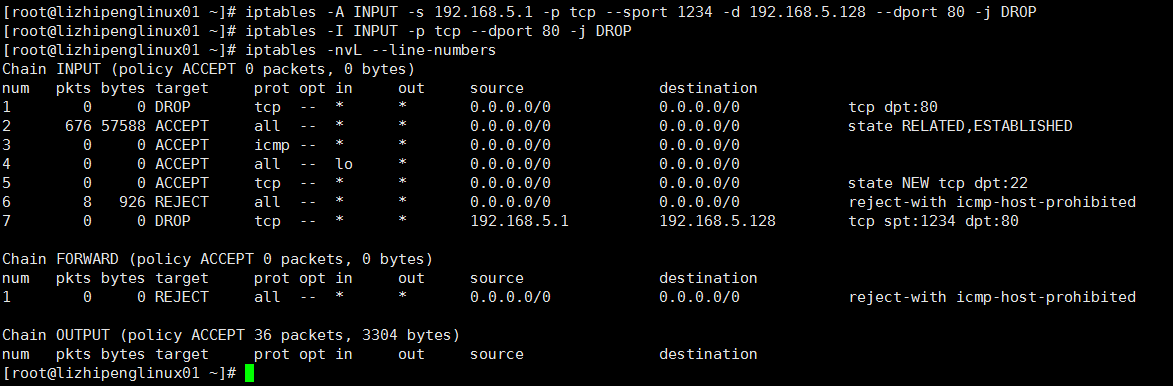
[root@lizhipenglinux01 ~]# iptables -A INPUT -s 192.168.5.1 -p tcp --sport 1234 -d 192.168.5.128 --dport 80 -j DROP
[root@lizhipenglinux01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
147 12832 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
7 697 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.5.1 192.168.5.128 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 15 packets, 1444 bytes)
pkts bytes target prot opt in out source destination
[root@lizhipenglinux01 ~]# iptables -I INPUT -p tcp --dport 80 -j DROP
[root@lizhipenglinux01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 -I 排在前面,类似于插队,优先过滤
286 22188 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
7 697 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.5.1 192.168.5.128 tcp spt:1234 dpt:80 -A 排在后面
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 20 packets, 1936 bytes)
pkts bytes target prot opt in out source destination
[root@lizhipenglinux01 ~]# iptables -D INPUT -p tcp --dport 80 -j DROP -D:删除
[root@lizhipenglinux01 ~]# iptables -nvL 第一条没有了
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
345 27516 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
8 926 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
0 0 DROP tcp -- * * 192.168.5.1 192.168.5.128 tcp spt:1234 dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 528 bytes)
pkts bytes target prot opt in out source destination
[root@lizhipenglinux01 ~]# iptables -D INPUT -s 192.168.5.1 -p tcp --sport 1234 -d 192.168.5.128 --dport 80 -j DROP
[root@lizhipenglinux01 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
452 37888 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
8 926 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 4 packets, 656 bytes)
pkts bytes target prot opt in out source destination
有时候服务器上的iptables过多,想删除一条规则,但是又不容易掌握创建时的规则。有一种比较简单的方法,先查看iptables。
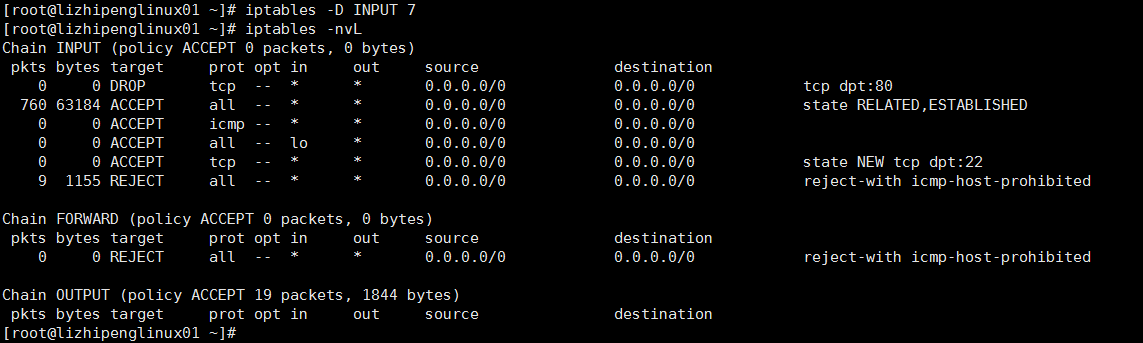
-----------------------
[root@lizhipenglinux01 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
-t选项后面跟表名,-nvL表示查看该表的规则,其中-n表示不针对IP反解析主机名,-L表示列出,-v表示列出的信息更加详细。如果不加-t选项,则打印filter表的相关信息
清除规则的命令中,用的最多的就是下面2个
iptables -F
iptables -Z
-F表示把所有规则全部删除,如果不加-t指定表,默认只清除filter表的规则。-Z表示把包以及流量计数器置零。