下载附件查看有两个文件,加密脚本和密文:
加密脚本:
import random from Crypto.Cipher import AES from os import urandom from string import printable from binascii import hexlify from secret import flag random.seed(urandom(32)) key1 = '0'*13 + ''.join([random.choice(printable) for _ in range(3)]) key2 = ''.join([random.choice(printable) for _ in range(3)]) + '0'*13 cipher1 = AES.new(key=key1.encode(), mode=AES.MODE_ECB) cipher2 = AES.new(key=key2.encode(), mode=AES.MODE_ECB) pt = input("You have a chance to get something: ") pt = pt.encode() val = len(pt) % 16 if not val == 0: pt += b'x00'*(16 - val) c1 = cipher1.encrypt(pt) c2 = cipher2.encrypt(c1) print('Your cipher:{}'.format(hexlify(c2))) assert(len(flag) % 16 == 0) c3 = cipher1.encrypt(flag) c4 = cipher2.encrypt(c3) print('Your flag:{}'.format(hexlify(c4)))
输入的密文:
You have a chance to get something: UNCTF2020_Enjoy_Crypto~ Your cipher:b'01a4e429e76db218fa0eb18f03ec69c9200a2362d8b4d7ea46170ce698389bbd' Your flag:b'196cc94c2d685beb54beeaa14c1dc0a6f3794d65fca0d1a1274515166e4255ab367383092e42d774992f74bc138faaad'
审计加密脚本发现是RSA加密,并且密文是执行了两次RSA,且告诉了我们key是16位,且告诉了我们13位
接着我们就可以编写脚本碰撞出key了(第一次加密密文的结果和第二次密文解密的结果碰撞)
from Crypto.Cipher import AES from os import urandom from string import printable from binascii import * import sys #0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"#$%&'()*+,-./:;<=>?@[]^_`{|}~ x0bx0c pt='UNCTF2020_Enjoy_Crypto~' pt = pt.encode() val = len(pt) % 16 if not val == 0: pt += b'x00'*(16 - val) crp=b'01a4e429e76db218fa0eb18f03ec69c9200a2362d8b4d7ea46170ce698389bbd' crp=unhexlify(crp) chr_table=printable table={} for s3 in chr_table: for s2 in chr_table: for s1 in chr_table: trypass=('0'*13 +s3+s2+s1).encode() cipher = AES.new(key=trypass, mode=AES.MODE_ECB).encrypt(pt) table.update({cipher:trypass}) for s3 in chr_table: for s2 in chr_table: for s1 in chr_table: trypass=(s3+s2+s1+'0'*13).encode() cipher = AES.new(key=trypass, mode=AES.MODE_ECB).decrypt(crp) if cipher in table: print("success!!!!!!!!!!!!") key1=table[cipher] key2=trypass with open("key.txt","w") as fp: fp.write(str(key1)) fp.write(str(key2)) sys.exit()
得到key1,和key2

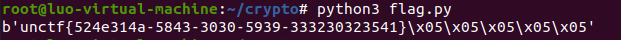
接着编写脚本获取flag
from Crypto.Cipher import AES from binascii import * en=b'196cc94c2d685beb54beeaa14c1dc0a6f3794d65fca0d1a1274515166e4255ab367383092e42d774992f74bc138faaad' en=unhexlify(en) cipher2 = AES.new(key=b'0/i0000000000000', mode=AES.MODE_ECB).decrypt(en) cipher1 = AES.new(key=b'0000000000000W<&', mode=AES.MODE_ECB).decrypt(cipher2) print(cipher1) #b'0000000000000W<&' #b'0/i0000000000000'