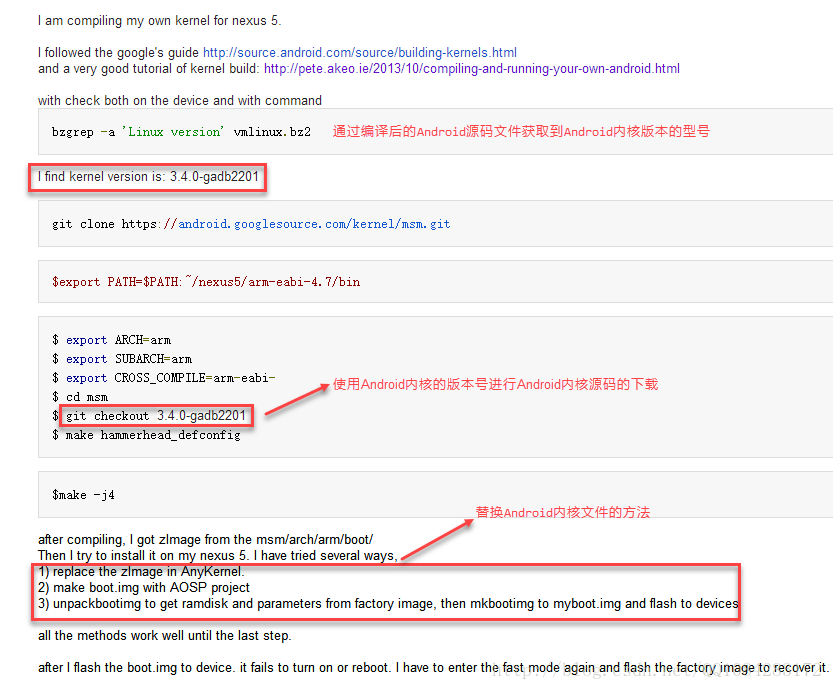
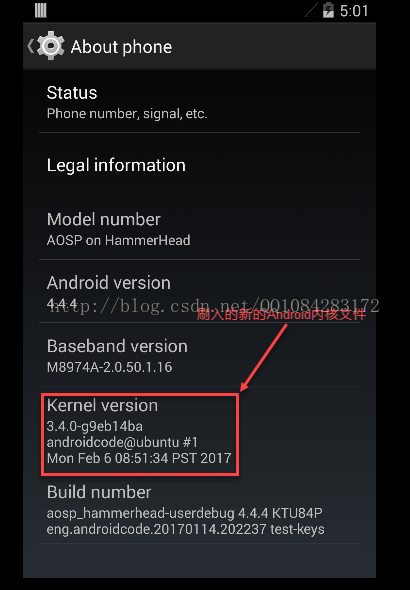
本文博客链接:http://blog.csdn.net/qq1084283172/article/details/54880488
前面的博客中已经记录了Nexus 5手机的Android 4.4.4 r1源码的编译基于 ubuntu 14.04.5,后面在该编译环境下来学习一下Android内核源码的编译基于Nexus 5手机。
一、Android内核源码的下载和编译
有关Android内核源码的下载信息可以参考谷歌官网的地址https://source.android.com/source/building-kernels.html#downloading-sources(需要FQ)相关的说明。
参考谷歌官方的文档了解到 Nexus 5 手机的Android内核源码是在源码分支 https://android.googlesource.com/kernel/msm.git 下。
Downloading sources
Download the source for the kernel you want to build using the appropriate git clone command:
$ git clone https://android.googlesource.com/kernel/common.git
$ git clone https://android.googlesource.com/kernel/hikey-linaro
$ git clone https://android.googlesource.com/kernel/x86_64.git
$ git clone https://android.googlesource.com/kernel/exynos.git
$ git clone https://android.googlesource.com/kernel/goldfish.git
$ git clone https://android.googlesource.com/kernel/msm.git
$ git clone https://android.googlesource.com/kernel/omap.git
$ git clone https://android.googlesource.com/kernel/samsung.git
$ git clone https://android.googlesource.com/kernel/tegra.git
-
The
goldfishproject contains the kernel sources for the emulated platforms. - The
msmproject has the sources for ADP1, ADP2, Nexus One, Nexus 4, Nexus 5, Nexus 6, Nexus 5X, Nexus 6P, Nexus 7 (2013), and can be used as a starting point for work on Qualcomm MSM chipsets. -
The
omapproject is used for PandaBoard and Galaxy Nexus, and can be used as a starting point for work on TI OMAP chipsets. -
The
samsungproject is used for Nexus S, and can be used as a starting point for work on Samsung Hummingbird chipsets. -
The
tegraproject is for Xoom, Nexus 7 (2012), Nexus 9, and can be used as a starting point for work on NVIDIA Tegra chipsets. -
The
exynosproject has the kernel sources for Nexus 10, and can be used as a starting point for work on Samsung Exynos chipsets. -
The
x86_64project has the kernel sources for Nexus Player, and can be used as a starting point for work on Intel x86_64 chipsets. -
The
hikey-linaroproject is used for HiKey reference boards, and can be used as a starting point for work on HiSilicon 620 chipsets.
在 前面文章 Android 4.4.4r1源码(基于ubuntu 14.04.5系统编译)根路径下创建 kernel 文件用于存放Nexus 5手机的Android的内核源码。
androidcode@ubuntu:~$ cd /home/androidcode/AndroidDevlop/android-4.4.4_r1
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1$ mkdir kernel
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1$ cd kernel/git clone 克隆远程Android内核源码的版本库到 Android 4.4.4r1源码的根路径下的kernel文件下。由于谷歌官方提供的下载地址需要FQ,也可以使用清华大学的Android源进行下载 ` git clone https://aosp.tuna.tsinghua.edu.cn/kernel/msm.git`。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel$ git clone https://android.googlesource.com/kernel/msm.git
Cloning into 'msm'...
remote: Sending approximately 1.37 GiB ...
remote: Counting objects: 280, done
remote: Total 5746741 (delta 4780079), reused 5746741 (delta 4780079)
Receiving objects: 100% (5746741/5746741), 1.37 GiB | 330.00 KiB/s, done.
Resolving deltas: 100% (4780079/4780079), done.
Checking connectivity... done.git branch 查看Android内核源码的代码版本分支。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel$ cd msm
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ git branch
* master
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ git branch -a
* master
remotes/origin/HEAD -> origin/master
remotes/origin/android-4.4
remotes/origin/android-4.4.y
remotes/origin/android-msm-2.6.35
remotes/origin/android-msm-3.9-usb-and-mmc-hacks
remotes/origin/android-msm-angler-3.10-marshmallow-dr
remotes/origin/android-msm-angler-3.10-marshmallow-dr1.5
remotes/origin/android-msm-angler-3.10-marshmallow-dr1.6
remotes/origin/android-msm-angler-3.10-marshmallow-dr1.6-1
remotes/origin/android-msm-angler-3.10-marshmallow-mr1
remotes/origin/android-msm-angler-3.10-n-mr1-preview-1
remotes/origin/android-msm-angler-3.10-n-mr1-preview-2
remotes/origin/android-msm-angler-3.10-n-preview-1
remotes/origin/android-msm-angler-3.10-n-preview-2
remotes/origin/android-msm-angler-3.10-n-preview-3
remotes/origin/android-msm-angler-3.10-n-preview-4
remotes/origin/android-msm-angler-3.10-n-preview-5
remotes/origin/android-msm-angler-3.10-nougat
remotes/origin/android-msm-angler-3.10-nougat-hwbinder
remotes/origin/android-msm-angler-3.10-nougat-mr0.5
remotes/origin/android-msm-angler-3.10-nougat-mr1
remotes/origin/android-msm-angler-3.10-nougat-mr1.1
remotes/origin/android-msm-anthias-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-anthias-3.10-lollipop-wear-release
remotes/origin/android-msm-anthias-3.10-marshmallow-dr1-wear-release
remotes/origin/android-msm-anthias-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-asus-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-asus-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-bass-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-bass-3.10-marshmallow-dr1-wear-release
remotes/origin/android-msm-bass-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-bass-3.10-marshmallow-mr1-wear-release-1
remotes/origin/android-msm-bullhead-3.10-marshmallow-dr
remotes/origin/android-msm-bullhead-3.10-marshmallow-dr-0
remotes/origin/android-msm-bullhead-3.10-marshmallow-dr1.5
remotes/origin/android-msm-bullhead-3.10-marshmallow-dr1.6
remotes/origin/android-msm-bullhead-3.10-marshmallow-mr1
remotes/origin/android-msm-bullhead-3.10-marshmallow-mr1-eas
remotes/origin/android-msm-bullhead-3.10-marshmallow-mr2
remotes/origin/android-msm-bullhead-3.10-n-mr1-preview-1
remotes/origin/android-msm-bullhead-3.10-n-mr1-preview-2
remotes/origin/android-msm-bullhead-3.10-n-preview-1
remotes/origin/android-msm-bullhead-3.10-n-preview-2
remotes/origin/android-msm-bullhead-3.10-n-preview-3
remotes/origin/android-msm-bullhead-3.10-n-preview-4
remotes/origin/android-msm-bullhead-3.10-n-preview-5
remotes/origin/android-msm-bullhead-3.10-nougat
remotes/origin/android-msm-bullhead-3.10-nougat-hwbinder
remotes/origin/android-msm-bullhead-3.10-nougat-mr0.5
remotes/origin/android-msm-bullhead-3.10-nougat-mr0.6
remotes/origin/android-msm-bullhead-3.10-nougat-mr1
remotes/origin/android-msm-bullhead-3.10-nougat-mr1.1
remotes/origin/android-msm-dory-3.10-kitkat-wear
remotes/origin/android-msm-dory-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-dory-3.10-lollipop-wear-release
remotes/origin/android-msm-dory-3.10-marshmallow-dr1-wear-release
remotes/origin/android-msm-dory-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-flo-3.4-jb-mr2
remotes/origin/android-msm-flo-3.4-kitkat-mr0
remotes/origin/android-msm-flo-3.4-kitkat-mr1
remotes/origin/android-msm-flo-3.4-kitkat-mr2
remotes/origin/android-msm-flo-3.4-l-preview
remotes/origin/android-msm-flo-3.4-lollipop-mr1
remotes/origin/android-msm-flo-3.4-lollipop-mr1.1
remotes/origin/android-msm-flo-3.4-lollipop-mr1.2
remotes/origin/android-msm-flo-3.4-lollipop-release
remotes/origin/android-msm-flo-3.4-marshmallow
remotes/origin/android-msm-flo-3.4-marshmallow-mr1
remotes/origin/android-msm-flo-3.4-marshmallow-mr2
remotes/origin/android-msm-gar-3.18-marshmallow-dr1-wear-release
remotes/origin/android-msm-gar-3.18-marshmallow-mr1-wear-release
remotes/origin/android-msm-hammerhead-3.4-kitkat-mr1
remotes/origin/android-msm-hammerhead-3.4-kitkat-mr2
remotes/origin/android-msm-hammerhead-3.4-kk-fr1
remotes/origin/android-msm-hammerhead-3.4-kk-fr2
remotes/origin/android-msm-hammerhead-3.4-kk-r1
remotes/origin/android-msm-hammerhead-3.4-l-preview
remotes/origin/android-msm-hammerhead-3.4-lollipop-mr1
remotes/origin/android-msm-hammerhead-3.4-lollipop-mr1.1
remotes/origin/android-msm-hammerhead-3.4-lollipop-release
remotes/origin/android-msm-hammerhead-3.4-m-preview
remotes/origin/android-msm-hammerhead-3.4-marshmallow
remotes/origin/android-msm-hammerhead-3.4-marshmallow-mr1
remotes/origin/android-msm-hammerhead-3.4-marshmallow-mr2
remotes/origin/android-msm-hammerhead-3.4-marshmallow-mr3
remotes/origin/android-msm-huawei-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-huawei-3.10-lollipop-mr1-wear-release-1
remotes/origin/android-msm-huawei-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-huawei-3.10-marshmallow-mr1-wear-release-1
remotes/origin/android-msm-huawei-3.10-marshmallow-mr1-wear-release-2
remotes/origin/android-msm-lego-3.10-marshmallow-dr
remotes/origin/android-msm-lenok-3.10-kitkat-wear
remotes/origin/android-msm-lenok-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-lenok-3.10-lollipop-wear-release
remotes/origin/android-msm-lenok-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-mako-3.4-jb-mr1
remotes/origin/android-msm-mako-3.4-jb-mr1-fr
remotes/origin/android-msm-mako-3.4-jb-mr1-kgsl
remotes/origin/android-msm-mako-3.4-jb-mr1.1
remotes/origin/android-msm-mako-3.4-jb-mr2
remotes/origin/android-msm-mako-3.4-kitkat-mr0
remotes/origin/android-msm-mako-3.4-kitkat-mr1
remotes/origin/android-msm-mako-3.4-kitkat-mr2
remotes/origin/android-msm-mako-3.4-lollipop-mr1
remotes/origin/android-msm-mako-3.4-lollipop-mr1.1
remotes/origin/android-msm-mako-3.4-lollipop-release
remotes/origin/android-msm-marlin-3.18-n-mr1-preview-2
remotes/origin/android-msm-marlin-3.18-nougat-dr1
remotes/origin/android-msm-marlin-3.18-nougat-hwbinder
remotes/origin/android-msm-marlin-3.18-nougat-mr1
remotes/origin/android-msm-marlin-3.18-nougat-mr1-eas-experimental
remotes/origin/android-msm-moto-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-nemo-3.10-marshmallow-dr1-wear-release
remotes/origin/android-msm-nemo-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-nemo-3.10-n-preview-1-wear-release
remotes/origin/android-msm-nemo-3.10-n-preview-2-wear-release
remotes/origin/android-msm-nemo-3.10-n-preview-4-wear-release
remotes/origin/android-msm-sculpin-3.18-marshmallow-dr1-wear-release
remotes/origin/android-msm-sculpin-3.18-marshmallow-mr1-wear-release
remotes/origin/android-msm-seed-3.10-lollipop-mr1
remotes/origin/android-msm-seed-3.10-marshmallow
remotes/origin/android-msm-seed-3.10-marshmallow-mr1
remotes/origin/android-msm-seed-3.10-marshmallow-mr2
remotes/origin/android-msm-seed-3.10-n-mr1-preview-2
remotes/origin/android-msm-seed-3.10-n-preview-2
remotes/origin/android-msm-seed-3.10-n-preview-3
remotes/origin/android-msm-seed-3.10-n-preview-4
remotes/origin/android-msm-seed-3.10-n-preview-5
remotes/origin/android-msm-seed-3.10-nougat
remotes/origin/android-msm-seed-3.10-nougat-mr1
remotes/origin/android-msm-seed-3.10-nougat-mr1.1
remotes/origin/android-msm-shamrock-3.10-nougat-release
remotes/origin/android-msm-shamu-3.10-lollipop-mr1
remotes/origin/android-msm-shamu-3.10-lollipop-release
remotes/origin/android-msm-shamu-3.10-m-preview
remotes/origin/android-msm-shamu-3.10-marshmallow
remotes/origin/android-msm-shamu-3.10-marshmallow-mr1
remotes/origin/android-msm-shamu-3.10-marshmallow-mr1-r0.15
remotes/origin/android-msm-shamu-3.10-marshmallow-mr2
remotes/origin/android-msm-shamu-3.10-n-preview-1
remotes/origin/android-msm-shamu-3.10-n-preview-2
remotes/origin/android-msm-shamu-3.10-n-preview-3
remotes/origin/android-msm-shamu-3.10-n-preview-4
remotes/origin/android-msm-shamu-3.10-n-preview-5
remotes/origin/android-msm-shamu-3.10-nougat-mr0.5
remotes/origin/android-msm-shamu-3.10-nougat-mr1.2
remotes/origin/android-msm-smelt-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-smelt-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-sony-cm-jb-3.0
remotes/origin/android-msm-sparrow-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-sprat-3.10-kitkat-wear
remotes/origin/android-msm-sprat-3.10-lollipop-mr1-wear-release
remotes/origin/android-msm-sprat-3.10-lollipop-wear-release
remotes/origin/android-msm-sprat-3.10-marshmallow-dr1-wear-release
remotes/origin/android-msm-sprat-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-sturgeon-3.10-marshmallow-dr1-wear-release
remotes/origin/android-msm-sturgeon-3.10-marshmallow-mr1-wear-release
remotes/origin/android-msm-sturgeon-3.10-marshmallow-mr1-wear-release-1
remotes/origin/android-msm-sturgeon-3.10-n-preview-1-wear-release
remotes/origin/android-msm-sturgeon-3.10-n-preview-2-wear-release
remotes/origin/android-msm-sturgeon-3.10-n-preview-4-wear-release
remotes/origin/android-msm-swift-3.18-marshmallow-mr1-wear-release
remotes/origin/android-msm-wren-3.10-marshmallow-dr1-wear-release
remotes/origin/android-msm-wren-3.10-marshmallow-mr1-wear-release
remotes/origin/mastergit checkout 下载适用于Nexus 5手机的Android内核源码到本地文件路径 /home/androidcode/AndroidDevlop/android-4.4.4_r1/kernel/msm 下。当然了也可以使用谷歌官方文档中提供的 git checkout -b 的方法下载相应的Android内核源码到本地编译环境的相应文件夹下。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ git checkout origin/android-msm-hammerhead-3.4-kk-r1
Checking out files: 100% (41847/41847), done.
Note: checking out 'origin/android-msm-hammerhead-3.4-kk-r1'.
You are in 'detached HEAD' state. You can look around, make experimental
changes and commit them, and you can discard any commits you make in this
state without impacting any branches by performing another checkout.
If you want to create a new branch to retain commits you create, you may
do so (now or later) by using -b with the checkout command again. Example:
git checkout -b new_branch_name
HEAD is now at 9eb14ba... msm: mdss: wait for ping pong during unblank kickoff
Nexus 5手机的Android内核源码的所有分支:
remotes/origin/android-msm-hammerhead-3.4-kitkat-mr1
remotes/origin/android-msm-hammerhead-3.4-kitkat-mr2
remotes/origin/android-msm-hammerhead-3.4-kk-fr1
remotes/origin/android-msm-hammerhead-3.4-kk-fr2
remotes/origin/android-msm-hammerhead-3.4-kk-r1
remotes/origin/android-msm-hammerhead-3.4-l-preview
remotes/origin/android-msm-hammerhead-3.4-lollipop-mr1
remotes/origin/android-msm-hammerhead-3.4-lollipop-mr1.1
remotes/origin/android-msm-hammerhead-3.4-lollipop-release
remotes/origin/android-msm-hammerhead-3.4-m-preview
remotes/origin/android-msm-hammerhead-3.4-marshmallow
remotes/origin/android-msm-hammerhead-3.4-marshmallow-mr1
remotes/origin/android-msm-hammerhead-3.4-marshmallow-mr2
remotes/origin/android-msm-hammerhead-3.4-marshmallow-mr3
对于Android的源码与Android内核源码版本的对应和适用关系,暂时还没有弄清楚,也不知道怎么根据Nexus 5手机的上面的Android内核的型号来下载对应的Android内核源码,经过谷歌查询,https://groups.google.com/forum/#!topic/android-building/ynU-SnGCTGs 讨论给出了一种方法,适用Nexus系列手机上的Android内核的版本号进行Android内核源码的下载。
有关Android内核源码的版本与Android系统源码选择下载的一些参考依据。
Platform Codenames, Versions, API Levels, and NDK Releases
The code names match the following version numbers, along with API levels and NDK releases provided for convenience:
| Code name | Version | API level |
|---|---|---|
| Nougat | 7.1 | API level 25 |
| Nougat | 7.0 | API level 24 |
| Marshmallow | 6.0 | API level 23 |
| Lollipop | 5.1 | API level 22 |
| Lollipop | 5.0 | API level 21 |
| KitKat | 4.4 - 4.4.4 | API level 19 |
| Jelly Bean | 4.3.x | API level 18 |
| Jelly Bean | 4.2.x | API level 17 |
| Jelly Bean | 4.1.x | API level 16 |
| Ice Cream Sandwich | 4.0.3 - 4.0.4 | API level 15, NDK 8 |
| Ice Cream Sandwich | 4.0.1 - 4.0.2 | API level 14, NDK 7 |
| Honeycomb | 3.2.x | API level 13 |
| Honeycomb | 3.1 | API level 12, NDK 6 |
| Honeycomb | 3.0 | API level 11 |
| Gingerbread | 2.3.3 - 2.3.7 | API level 10 |
| Gingerbread | 2.3 - 2.3.2 | API level 9, NDK 5 |
| Froyo | 2.2.x | API level 8, NDK 4 |
| Eclair | 2.1 | API level 7, NDK 3 |
| Eclair | 2.0.1 | API level 6 |
| Eclair | 2.0 | API level 5 |
| Donut | 1.6 | API level 4, NDK 2 |
| Cupcake | 1.5 | API level 3, NDK 1 |
| (no code name) | 1.1 | API level 2 |
| (no code name) | 1.0 | API level 1 |
因此,这里Nexus 5手机的Android 4.4.4 r1 源码,选择下载的Android内核源码的版本为 android-msm-hammerhead-3.4-kk-r1。
下载编译Android内核源码的编译链接工具,在编译Android内核源码的时候需要配置该编译连接工具的文件路径。
Downloading a prebuilt gcc
Ensure the prebuilt toolchain is in your path:
$ export PATH=$(pwd)/prebuilts/gcc/linux-x86/arm/arm-eabi-4.6/bin:$PATH
or
$ export PATH=$(pwd)/prebuilts/gcc/darwin-x86/arm/arm-eabi-4.6/bin:$PATH
On a Linux host, if you don't have an Android source tree, you can download the prebuilt toolchain from:
$ git clone https://android.googlesource.com/platform/prebuilts/gcc/linux-x86/arm/arm-eabi-4.6
下载Android内核源码的编译链接工具到Android内核源码的msm文件夹下,选择下载的编译链接的工具的版本为arm-eabi-4.7。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ git clone https://android.googlesource.com/platform/prebuilts/gcc/linux-x86/arm/arm-eabi-4.7/
Cloning into 'arm-eabi-4.7'...
remote: Sending approximately 37.12 MiB ...
remote: Counting objects: 39, done
remote: Total 218 (delta 53), reused 218 (delta 53)
Receiving objects: 100% (218/218), 37.12 MiB | 223.00 KiB/s, done.
Resolving deltas: 100% (53/53), done.
Checking connectivity... done.谷歌官方 https://source.android.com/source/building-kernels.html#building 给出的编译Android内核源码的方法的参考说明,但是是arm64的Android内核源码的编译配置。
Building the kernel
When you know the last commit message for a kernel and have successfully downloaded the kernel source and prebuilt gcc, you are ready to build the kernel. The following build commands use the hikey kernel:
$ export ARCH=arm64
$ export CROSS_COMPILE=aarch64-linux-android-
$ cd hikey-linaro
$ git checkout -b android-hikey-linaro-4.1 origin/android-hikey-linaro-4.1
$ make hikey_defconfig
$ make
To build a different kernel, simply replace hikey-linaro with the name of the kernel you want to
build.
在编译Android内核源码之前,通过命令行设置指定目标设备的体系架构和交叉编译器。当然也可以通过修改Android内核源码的Makefile文件来设置 ARCH和CROSS_COMPILE的值来配置,但是感觉比较麻烦。在Android内核源码的 msm 文件下创建 run_this_android.sh 脚本文件。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ gedit run_this_android.sh在run_this_android.sh 脚本文件中添加下面的文件内容(pwd命令的意思是当前文件目录下):
export CC=$(pwd)/arm-eabi-4.7/bin/arm-eabi-
export CROSS_COMPILE=$(pwd)/arm-eabi-4.7/bin/arm-eabi-
export ARCH=arm
export SUBARCH=arm然后保存脚本文件 run_this_android.sh并关闭文件,赋予该脚本文件以可执行权限,然后执行该脚本文件设置编译Android内核源码需要的临时环境变量。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ chmod +x run_this_android.sh
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ source run_this_android.sh根据谷歌官方的参考文档 执行 make hammerhead_defconfig 命令生成后面Android内核编译需要配置文件.config文件中,.config文件是一个隐藏目录,保存着各个目录下Kconfig文件的配置,然后执行 make 编译Android内核源码。
Selecting a kernel
This table lists the name and locations of the kernel sources and binaries:
| Device | Binary location | Source location | Build configuration |
|---|---|---|---|
| hikey | device/linaro/hikey-kernel | kernel/hikey-linaro | hikey_defconfig |
| angler | device/huawei/angler-kernel | kernel/msm | angler_defconfig |
| bullhead | device/lge/bullhead-kernel | kernel/msm | bullhead_defconfig |
| shamu | device/moto/shamu-kernel | kernel/msm | shamu_defconfig |
| fugu | device/asus/fugu-kernel | kernel/x86_64 | fugu_defconfig |
| volantis | device/htc/flounder-kernel | kernel/tegra | flounder_defconfig |
| hammerhead | device/lge/hammerhead-kernel | kernel/msm | hammerhead_defconfig |
| flo | device/asus/flo-kernel/kernel | kernel/msm | flo_defconfig |
| deb | device/asus/flo-kernel/kernel | kernel/msm | flo_defconfig |
| manta | device/samsung/manta/kernel | kernel/exynos | manta_defconfig |
| mako | device/lge/mako-kernel/kernel | kernel/msm | mako_defconfig |
| grouper | device/asus/grouper/kernel | kernel/tegra | tegra3_android_defconfig |
| tilapia | device/asus/grouper/kernel | kernel/tegra | tegra3_android_defconfig |
| maguro | device/samsung/tuna/kernel | kernel/omap | tuna_defconfig |
| toro | device/samsung/tuna/kernel | kernel/omap | tuna_defconfig |
| panda | device/ti/panda/kernel | kernel/omap | panda_defconfig |
| stingray | device/moto/wingray/kernel | kernel/tegra | stingray_defconfig |
| wingray | device/moto/wingray/kernel | kernel/tegra | stingray_defconfig |
| crespo | device/samsung/crespo/kernel | kernel/samsung | herring_defconfig |
| crespo4g | device/samsung/crespo/kernel | kernel/samsung | herring_defconfig |
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ make hammerhead_defconfig
#
# configuration written to .config
#
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ make -j4Android内核源码编译成功了。
OBJCOPY arch/arm/boot/Image
Kernel: arch/arm/boot/Image is ready
AS arch/arm/boot/compressed/head.o
GZIP arch/arm/boot/compressed/piggy.gzip
CC arch/arm/boot/compressed/misc.o
CC arch/arm/boot/compressed/decompress.o
CC arch/arm/boot/compressed/string.o
SHIPPED arch/arm/boot/compressed/lib1funcs.S
SHIPPED arch/arm/boot/compressed/ashldi3.S
AS arch/arm/boot/compressed/lib1funcs.o
AS arch/arm/boot/compressed/ashldi3.o
AS arch/arm/boot/compressed/piggy.gzip.o
LD arch/arm/boot/compressed/vmlinux
OBJCOPY arch/arm/boot/zImage
Kernel: arch/arm/boot/zImage is ready
CAT arch/arm/boot/zImage-dtb
Kernel: arch/arm/boot/zImage-dtb is ready查看Android内核源码编译生成的文件。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ ls arch/arm/boot/
bootp msm8974-hammerhead-rev-10.dtb msm8974-hammerhead-rev-c.dtb
compressed msm8974-hammerhead-rev-11.dtb msm8974-hammerhead-rev-f.dtb
dts msm8974-hammerhead-rev-11j.dtb zImage
Image msm8974-hammerhead-rev-a.dtb zImage-dtb
install.sh msm8974-hammerhead-rev-b.dtb
Makefile msm8974-hammerhead-rev-bn.dtb二、将编译成功的Android内核源码产生的新内核文件替换原来的内核文件
谷歌文件中提到的 将编译成功的Android内核源码产生的内核文件替换原来内核文件生成新的Android内核 boot.img 文件的方法,但是需要设置相关的参数。
The image outputs to the arch/arm64/boot/Image directory;
the kernel binary outputs to thearch/arm64/boot/dts/hisilicon/hi6220-hikey.dtb fle.
Copy the Image directory and the hi6220-hikey.dtb file
to the hikey-kernel directory.
Alternatively, you can include the TARGET_PREBUILT_KERNEL variable while using make
bootimage (or any other makecommand line that builds a boot image). This variable is supported by all devices as it is set up via device/common/populate-new-device.sh.
For example:
$ export TARGET_PREBUILT_KERNEL=$your_kernel_path/arch/arm/boot/zImage-dtb
Note: Kernel names differ by device. To locate the correct filename for your kernel, refer todevice/<vendor>/<name> in the kernel
source.
前面的步骤中已经将 android-msm-hammerhead-3.4-kk-r1版本的Android内核文件编译出来了。下面步骤就是解包Android 4.4.4r1源码编译后的产生的 AndroidDevlop/android-4.4.4_r1/out/target/product/hammerhead/boot.img文件,替换原来的Android内核文件为我们前面的操作中编译产生的android-msm-hammerhead-3.4-kk-r1版本的内核文件。
第一种方法:将编译产生的新的Android内核文件 android-4.4.4_r1/kernel/msm/arch/arm/boot/zImage-dtb 替换掉 Android 4.4.4r1源码中的 android-4.4.4_r1/device/lge/hammerhead-kernel/zImage-dtb文件。这样一来,下次编译Android4.4.4r1源码的时候,使用的就是替换后新的zImage-dtb内核文件。Android 4.4.4r1的源码下载谷歌官方提供的相应的驱动文件进行一次完全编译后,将产生的刷机镜像文件,重启Nexus 5手机进入刷机模式 fastboot flashall -w 刷入手机,Nexus 5手机的内核就更新为我们编译的新Android内核。
第二种方法:解包Android 4.4.4r1源码编译生成的boot.img文件替换内核文件
具体的就是对Android 4.4.4r1源码编译后产生的 android-4.4.4_r1/out/target/product/hammerhead/boot.img 镜像文件进行解包替换原来的Android内核文件然后进行打包。解包打包boot.img文件的工具比较多,这里依次整理几个,熟悉一下解包打包boot.img工具的使用。
1). 使用bootimg-tools工具解包打包boot.img文件替换内核(bootimg-tools工具比较好用--推荐)
下载bootimg-tools解包打包工具到 android-4.4.4_r1/kernel/msm/bootimg-tools文件夹中。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ git clone https://github.com/pbatard/bootimg-tools.git
Cloning into 'bootimg-tools'...
remote: Counting objects: 76, done.
remote: Total 76 (delta 0), reused 0 (delta 0), pack-reused 76
Unpacking objects: 100% (76/76), done.
Checking connectivity... done.androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm$ cd bootimg-tools/
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools$ ls
cpio include libmincrypt LICENSE Makefile mkbootimg README.md
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools$ make
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o libmincrypt/sha.o libmincrypt/sha.c
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o libmincrypt/rsa.o libmincrypt/rsa.c
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o libmincrypt/dsa_sig.o libmincrypt/dsa_sig.c
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o libmincrypt/p256.o libmincrypt/p256.c
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o libmincrypt/p256_ec.o libmincrypt/p256_ec.c
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o libmincrypt/p256_ecdsa.o libmincrypt/p256_ecdsa.c
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o libmincrypt/sha256.o libmincrypt/sha256.c
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o mkbootimg/mkbootimg.o mkbootimg/mkbootimg.c
cc -o mkbootimg/mkbootimg libmincrypt/sha.o libmincrypt/rsa.o libmincrypt/dsa_sig.o libmincrypt/p256.o libmincrypt/p256_ec.o libmincrypt/p256_ecdsa.o libmincrypt/sha256.o mkbootimg/mkbootimg.o
cc -Wall -Wextra -Wno-unused-parameter -pedantic -pipe -std=c99 -D_GNU_SOURCE -Iinclude -c -o mkbootimg/unmkbootimg.o mkbootimg/unmkbootimg.c
cc -o mkbootimg/unmkbootimg mkbootimg/unmkbootimg.o
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools$ ls mkbootimg
bootimg.h mkbootimg.c unmkbootimg unmkbootimg.o
mkbootimg mkbootimg.o unmkbootimg.c将 android-4.4.4_r1/out/target/product/hammerhead/boot.img 文件拷贝到 android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg 文件夹下进行解包处理。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ cp /home/androidcode/AndroidDevlop/android-4.4.4_r1/out/target/product/hammerhead/boot.img .
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ ./unmkbootimg -i boot.img
kernel written to 'kernel' (8405280 bytes)
ramdisk written to 'ramdisk.cpio.gz' (498995 bytes)
To rebuild this boot image, you can use the command:
mkbootimg --base 0 --pagesize 2048 --kernel_offset 0x00008000 --ramdisk_offset 0x02900000 --second_offset 0x00f00000 --tags_offset 0x02700000 --cmdline 'console=ttyHSL0,115200,n8 androidboot.hardware=hammerhead user_debug=31 maxcpus=2 msm_watchdog_v2.enable=1' --kernel kernel --ramdisk ramdisk.cpio.gz -o boot.img
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ ls
boot.img kernel mkbootimg.c ramdisk.cpio.gz unmkbootimg.c
bootimg.h mkbootimg mkbootimg.o unmkbootimg unmkbootimg.o替换原来的kernel内核文件,重新打包生成新的boot.img。当然了为解包和打包boot.img文件方便也可以将 unmkbootimg工具和mkbootimg工具设置成环境变量。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ cp /home/androidcode/AndroidDevlop/android-4.4.4_r1/kernel/msm/arch/arm/boot/zImage-dtb kernel
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ mkbootimg --base 0 --pagesize 2048 --kernel_offset 0x00008000 --ramdisk_offset 0x02900000 --second_offset 0x00f00000 --tags_offset 0x02700000 --cmdline 'console=ttyHSL0,115200,n8 androidboot.hardware=hammerhead user_debug=31 maxcpus=2 msm_watchdog_v2.enable=1' --kernel kernel --ramdisk ramdisk.cpio.gz -o boot.img
mkbootimg: command not found
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ ./mkbootimg --base 0 --pagesize 2048 --kernel_offset 0x00008000 --ramdisk_offset 0x02900000 --second_offset 0x00f00000 --tags_offset 0x02700000 --cmdline 'console=ttyHSL0,115200,n8 androidboot.hardware=hammerhead user_debug=31 maxcpus=2 msm_watchdog_v2.enable=1' --kernel kernel --ramdisk ramdisk.cpio.gz -o boot.imgOK,新的Android系统的镜像文件boot.img生成成功,将生成的 /home/androidcode/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg/boot.img 替换掉Android 4.4.4r1源码生成的 android-4.4.4_r1/out/target/product/hammerhead/boot.img文件,然后重启Nexus 5手机进入刷机状态,单独刷入新的Android镜像文件boot.img。在执行刷机命令 fastboot 时,已经将fastboot刷机工具的文件路径设置为环境变量了。
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ adb reboot bootloader
* daemon not running. starting it now on port 5037 *
* daemon started successfully *
androidcode@ubuntu:~/AndroidDevlop/android-4.4.4_r1/kernel/msm/bootimg-tools/mkbootimg$ fastboot boot boot.img
downloading 'boot.img'...
OKAY [ 1.173s]
booting...
OKAY [ 0.109s]
finished. total time: 1.282s2). 使用bootimg.exe工具解包打包boot.img文件替换Android的内核(推荐)
在windows平台下,解包和打包boot.img文件使用的工具是bootimg.exe,该工具最新的版本支持Android 2.3~5.0的版本,具体的功能如下:
解包命令:bootimg.exe --unpack-bootimg
打包命令:bootimg.exe --repack-bootimg
在Windows的cmd命令环境下执行:bootimg.exe –unpack-bootimg 命令对boot.img文件进行解压处理得到 kernel文件,将我们自己前面编译的kernel/msm/arch/arm/boot/zImage-dtb文件 重命名为 kernel 替换该解压出来的kernel文件,接着执行 bootimg.exe --repack-bootimg 命令重打包生成新的boot.img文件,然后执行 adb reboot-bootloader 重启Nexus 5手机进入刷机模式,执行 fastboot boot boot.img 将新的 boot.img文件刷入Nexus 5手机,这样Nexus 5手机的Android内核就替换为我们自己编译的Android内核版本了。
有关bootimg.exe工具解包和打包boot.img文件的是永恒方法可以参考下面的连接:
《Windows下Nexus
5 改user模式为debug模式》
工具下载链接:https://github.com/cofface/android_bootimg
看雪学习链接:http://bbs.pediy.com/showthread.php?t=198328‘
3).使用前面的博文《Ubuntu下修改Nexus 5的boot.img--改user模式为debug模式》中使用的boot.img解包打包工具替换boot.img文件中的 boot.img-kernel文件 为我们自己编译的生成的重命名为boot.img-kernel的 kernel/msm/arch/arm/boot/zImage-dtb文件,然后将重新打包生成的boot.img文件刷入Nexus 5手机即可。
三、修改Android内核的源过掉Anti-Debug
前面学习Android内核源码的下载编译以及替换Nexus 5手机的内核,主要的目的是为后面学习修改Android内核源码过掉Android的反调试以及进行Android内核层Hook做准备。下面就来学习通过修改Android源码的绕过Android基于进程状态文件/proc/pid/status的反调试,一般的情况下该种反调试都是通过判断TracerPid的状态值来判断。一般情况下,TracerPid的值为0时,当前Android进程认为没有被别的进程调试,其实手动过掉这种应用层反调试也比较简单,只需要守住 open函数即可。通过查找发现TracerPid在Android内核源码的的 /kernel/msm/fs/proc/array.c 文件里,通过下面的修改即可过掉一般情况下的反调试:
/*
* The task state array is a strange "bitmap" of
* reasons to sleep. Thus "running" is zero, and
* you can test for combinations of others with
* simple bit tests.
*/
static const char * const task_state_array[] = {
"R (running)", /* 0 */
"S (sleeping)", /* 1 */
"D (disk sleep)", /* 2 */
"T (stopped)", /* 4 */
"t (tracing stop)", /* 8 此时当前进程被调试了*/
"Z (zombie)", /* 16 */
"X (dead)", /* 32 */
"x (dead)", /* 64 */
"K (wakekill)", /* 128 */
"W (waking)", /* 256 */
};
static inline void task_state(struct seq_file *m, struct pid_namespace *ns,
struct pid *pid, struct task_struct *p)
{
struct group_info *group_info;
int g;
struct fdtable *fdt = NULL;
const struct cred *cred;
pid_t ppid, tpid;
rcu_read_lock();
ppid = pid_alive(p) ?
task_tgid_nr_ns(rcu_dereference(p->real_parent), ns) : 0;
tpid = 0;
if (pid_alive(p)) {
struct task_struct *tracer = ptrace_parent(p);
// 判断当前进程是否被反调试
if (tracer) {
tpid = task_pid_nr_ns(tracer, ns);
// 修改 TracerPid为0,绕过反调试
tpid = 0;
}
}
cred = get_task_cred(p);
seq_printf(m,
"State: %s
"
"Tgid: %d
"
"Pid: %d
"
"PPid: %d
"
"TracerPid: %d
"
"Uid: %d %d %d %d
"
"Gid: %d %d %d %d
",
/***get_task_state(p) 需要修改非t绕过反调试***/ "S",
task_tgid_nr_ns(p, ns),
pid_nr_ns(pid, ns),
ppid, tpid,
cred->uid, cred->euid, cred->suid, cred->fsuid,
cred->gid, cred->egid, cred->sgid, cred->fsgid);
task_lock(p);
if (p->files)
fdt = files_fdtable(p->files);
seq_printf(m,
"FDSize: %d
"
"Groups: ",
fdt ? fdt->max_fds : 0);
rcu_read_unlock();
group_info = cred->group_info;
task_unlock(p);
for (g = 0; g < min(group_info->ngroups, NGROUPS_SMALL); g++)
seq_printf(m, "%d ", GROUP_AT(group_info, g));
put_cred(cred);
seq_putc(m, '
');
}/proc/pid/status
/proc/pid/task/tid/status
/proc/pid/stat
/proc/pid/task/pid/stat
/proc/pid/wchan
/proc/pid/task/pid/wchan
有价值的参考文档:
Building and booting Nexus 5 kernel (推荐)
编译Nexus5内核(推荐)
Compiling and running your own Android kernel on the Nexus 7 2013(推荐)
Compile your own android kernel
Android内核的编译与裁剪(推荐)
如何下载并编译Android4.0内核源码goldfish(图文)
linux驱动基础开发3——linux 内核配置机制(make menuconfig、Kconfig、makefile)讲解
为nexus5编译ubuntu14.04TLSx64(android4.4.4)
Android反调试笔记(推荐)
https://source.android.com/source/building-kernels.html