Ingress简介
ingress是什么?
上篇文章介绍service时有说了暴露了service的三种方式ClusterIP、NodePort与LoadBalance,这几种方式都是在service的维度提供的,service的作用体现在两个方面,对集群内部,它不断跟踪pod的变化,更新endpoint中对应pod的对象,提供了ip不断变化的pod的服务发现机制,对集群外部,他类似负载均衡器,可以在集群内外部对pod进行访问。但是,单独用service暴露服务的方式,在实际生产环境中不太合适:
ClusterIP的方式只能在集群内部访问
NodePort方式的话,测试环境使用还行,当有几十上百的服务在集群中运行时,NodePort的端口管理是灾难。
LoadBalance方式受限于云平台,且通常在云平台部署ELB还需要额外的费用。
所幸k8s还提供了一种集群维度暴露服务的方式,也就是ingress。ingress可以简单理解为service的service,他通过独立的ingress对象来制定请求转发的规则,把请求路由到一个或多个service中。这样就把服务与请求规则解耦了,可以从业务维度统一考虑业务的暴露,而不用为每个service单独考虑。
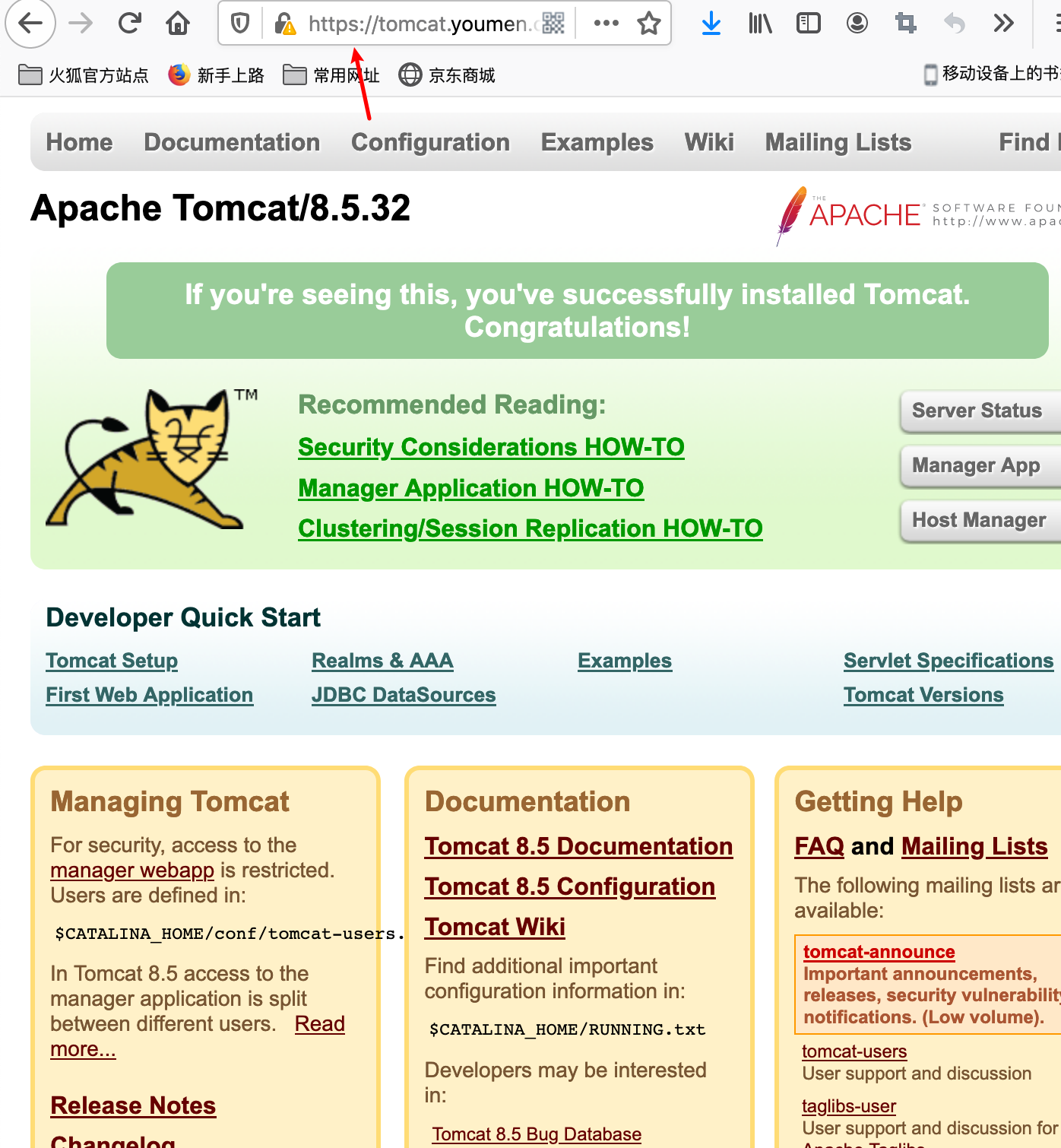
举个例子,现在集群有api、文件存储、前端3个service,可以通过一个ingress对象来实现图中的请求转发
)
Ingress规则是很灵活的,可以根据不同域名,不同path转发请求到不同的service,并且支持https/http.
Ingress与Ingress-controller
要理解ingress,需要区分两个概念,ingress和ingress-controller:
Ingress对象:
指的是k8s中的一个api对象,一般用yaml配置,作用是定义请求如何转发到service的规则,可以理解为配置模板;
Ingress-controller
具体实现反向代理及负载均衡的程序,对ingress定义的规则进行解析,根据配置的规则来实现请求转发;
简单来说,Ingress-controller才是负责转发的组件,通过各种方式将他暴露在集群入口,外部对集群的请求流量会先到Ingress-controller,而Ingress对象是用来告诉Ingress-controller该如何转发请求,比如那些域名那些path要转发到那些服务等.
Ingress-controller
# 他跟Deployment等控制器不一样,其他控制器都属于Master三大组件之一,而Ingress是独立的一个控制器.
# Nginx
# Trefik (微服务)
# Envoy
Ingress-controller并不是k8s自带的组件,实际上ingress-controller只是一个统称,用户可以选择不同的Ingress-controller实现,目前,由K8S维护的Ingress-controller只有google云的GCE与Ingress-nginx两个,其他还有第三方维护的ingress-controller,但不管采用哪种Ingress-controller,实现的机制都大同小异,只是在具体配置上有差异,一般来说,Ingress-controller的形式都是一个Pod,里面跑着daemon程序和反向代理程序,daemon负责不断监控集群的变化,根据Ingress对象生成配置并应用新配置到反向代理,比如nginx-ingress就是动态生成nginx配置,动态更新upstream,并在需要视乎reload程序应用新配置,为了方便,后面的例子都已k8s官方维护的nginx-ingress为例.
Ingress应用
Ingress是一个API对象,和其他对象一样,通过yaml文件来配置,Ingress通过http或https暴露集群内部service,给service提供外部URL、负载均衡、SSL/TLS能力以及基于host的方向代理,Ingress要依靠Ingress-controller来具体实现以上功能.大概就是如下配置:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: abc-ingress
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/use-regex: "true"
spec:
tls:
- hosts:
- api.abc.com
secretName: abc-tls
rules:
- host: api.abc.com
http:
paths:
- backend:
serviceName: apiserver
servicePort: 80
- host: www.abc.com
http:
paths:
- path: /image/*
backend:
serviceName: fileserver
servicePort: 80
- host: www.abc.com
http:
paths:
- backend:
serviceName: feserver
servicePort: 8080
与其他k8s对象一样,ingress配置也包含了apiVersion、kind、meatdata、spec等关键字段,有几个关注的spec字段中,tls用于定义https密钥、证书。rule用于指定请求路由规则,这里指的关注的是metadata.annotations字段,在ingress配置中,annotations很重要,前面有说ingress-controller有很多不同的实现,而不同的Ingress-controller就可以根据"kubernetes.io/ingress.class"来判断要使用那些ingress配置,同时,不同的ingress-controller也有对应的annotations配置,用于自定义一些参数,例如上面配置的'nginx.ingress.kubernetes.io/use-regex: "true"',最终是在生成nginx配置中,会采用location ~来表示正则匹配
Ingress部署
Ingress的部署,需要考虑两个方面:
# 1 . ingress-controller是作为Pod来运行的,以什么方式部署比较好
# 2 . ingress解决了如何请求路由到集群内部,那他自己怎么暴露给外部比较好
下面列举一些目前常用的部署和暴露方式,具体使用哪种方式还得根据实际需要考虑来决定
Deployment+LoadBalancer模式的Service
如果要把ingress部署在公有云,那用这种方式比较合适。用Deployment部署ingress-controller,创建一个type为LoadBalancer的service关联这组pod。大部分公有云,都会为LoadBalancer的service自动创建一个负载均衡器,通常还绑定了公网地址。只要把域名解析指向该地址,就实现了集群服务的对外暴露。
Deployment+NodePort模式的Service
同样用deployment模式部署ingress-controller,并创建对应的服务,但是type为NodePort。这样,ingress就会暴露在集群节点ip的特定端口上。由于nodeport暴露的端口是随机端口,一般会在前面再搭建一套负载均衡器来转发请求。该方式一般用于宿主机是相对固定的环境ip地址不变的场景。
NodePort方式暴露ingress虽然简单方便,但是NodePort多了一层NAT,在请求量级很大时可能对性能会有一定影响。
DaemonSet+HostNetwork+nodeSelector
用DaemonSet结合nodeselector来部署ingress-controller到特定的node上,然后使用HostNetwork直接把该pod与宿主机node的网络打通,直接使用宿主机的80/433端口就能访问服务。这时,ingress-controller所在的node机器就很类似传统架构的边缘节点,比如机房入口的nginx服务器。该方式整个请求链路最简单,性能相对NodePort模式更好。缺点是由于直接利用宿主机节点的网络和端口,一个node只能部署一个ingress-controller pod。比较适合大并发的生产环境使用。
for file in configmap.yaml namespace.yaml mandatory.yaml rbac.yaml with-rbac.yaml; do wget https://github.com/kubernetes/ingress-nginx/tree/master/deploy/static/$file ;done
cat mandatory.yaml
apiVersion: v1
kind: Namespace
metadata:
name: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: nginx-configuration
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: tcp-services
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: udp-services
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRole
metadata:
name: nginx-ingress-clusterrole
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- "extensions"
- "networking.k8s.io"
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- "extensions"
- "networking.k8s.io"
resources:
- ingresses/status
verbs:
- update
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: Role
metadata:
name: nginx-ingress-role
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
resourceNames:
# Defaults to "<election-id>-<ingress-class>"
# Here: "<ingress-controller-leader>-<nginx>"
# This has to be adapted if you change either parameter
# when launching the nginx-ingress-controller.
- "ingress-controller-leader-nginx"
verbs:
- get
- update
- apiGroups:
- ""
resources:
- configmaps
verbs:
- create
- apiGroups:
- ""
resources:
- endpoints
verbs:
- get
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: RoleBinding
metadata:
name: nginx-ingress-role-nisa-binding
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: nginx-ingress-role
subjects:
- kind: ServiceAccount
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: nginx-ingress-clusterrole-nisa-binding
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: nginx-ingress-clusterrole
subjects:
- kind: ServiceAccount
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-ingress-controller
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
replicas: 1
selector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
annotations:
prometheus.io/port: "10254"
prometheus.io/scrape: "true"
spec:
# wait up to five minutes for the drain of connections
terminationGracePeriodSeconds: 300
serviceAccountName: nginx-ingress-serviceaccount
nodeSelector:
kubernetes.io/os: linux
containers:
- name: nginx-ingress-controller
image: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.26.1
args:
- /nginx-ingress-controller
- --configmap=$(POD_NAMESPACE)/nginx-configuration
- --tcp-services-configmap=$(POD_NAMESPACE)/tcp-services
- --udp-services-configmap=$(POD_NAMESPACE)/udp-services
- --publish-service=$(POD_NAMESPACE)/ingress-nginx
- --annotations-prefix=nginx.ingress.kubernetes.io
securityContext:
allowPrivilegeEscalation: true
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
# www-data -> 33
runAsUser: 33
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
ports:
- name: http
containerPort: 80
protocol: TCP
- name: https
containerPort: 443
protocol: TCP
livenessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 10
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 10
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
---
apiVersion: v1
kind: LimitRange
metadata:
name: ingress-nginx
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
limits:
- default:
min:
memory: 90Mi
cpu: 100m
type: Container
kubectl apply -f mandatory.yaml
kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
nginx-ingress-controller-568867bf56-wwgqx 1/1 Running 0 4m10s
如果是裸机的话需要创建一个Nodeport暴露端口
https://kubernetes.github.io/ingress-nginx/deploy/#bare-metal
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/provider/baremetal/service-nodeport.yaml
# 为了让暴露端口不是随机的,我们指定一下.
cat service-nodeport.yaml
apiVersion: v1
kind: Service
metadata:
name: ingress-nginx
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
type: NodePort
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
nodePort: 30080
- name: https
port: 443
targetPort: 443
protocol: TCP
nodePort: 30443
selector:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kubectl apply -f service-nodeport.yaml
kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx NodePort 10.96.120.168 <none> 80:30080/TCP,443:30443/TCP 6m19s
# 我们使用集群外的一台机器访问看一下
接下来我们将之前的myapp应用给发布出去
cat ingress-myapp.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-myapp
namespace: default
annotations:
kubernetes.io/ingress.class: "nginx"
spec:
rules:
- host: myapp.youmen.com
http:
paths:
- path:
backend:
serviceName: redis
servicePort: 80
kubectl apply -f ingress-myapp.yaml
# 我们一旦创建ingress就会立刻将环境注入到nginx
kubectl exec -n ingress-nginx -it nginx-ingress-controller-568867bf56-wwgqx /bin/bash
cat nginx.conf |grep youmen
## start server myapp.youmen.com
server_name myapp.youmen.com ;
## end server myapp.youmen.com
# 接下来我们去修改本地主机的hosts文件
Windows: C:WindowsSystem32driversetc
Linux: /etc/hosts
172.19.0.26 myapp.youmen.com
# 浏览器访问即可出现下面页面

发布Tomcat应用(http)
创建tomcatDeployment和service
cat tomcat-deploy.yaml
apiVersion: v1
kind: Service
metadata:
name: tomcat
namespace: default
spec:
selector:
app: tomcat
release: canary
ports:
- name: http
targetPort: 8080
port: 8080
- name: ajp
targetPort: 8009
port: 8009
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: tomcat-deploy
namespace: default
spec:
replicas: 3
selector:
matchLabels:
app: tomcat
release: canary
template:
metadata:
labels:
app: tomcat
release: canary
spec:
containers:
- name: tomcat
image: tomcat:8.5.32-jre8-alpine
ports:
- name: http
containerPort: 8080
- name: ajp
containerPort: 8009
创建Ingress-tomcat.yaml
cat ingress-tomcat.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-tomcat
namespace: default
annotations:
kubernetes.io/ingress.class: "nginx"
spec:
rules:
- host: tomcat.youmen.com
http:
paths:
- path:
backend:
serviceName: tomcat
servicePort: 8080
# 跟上面步骤一样做域名解析,然后访问浏览器IP:30080
https加密tomcat
# mkdir encryption
# cd encryption
openssl genrsa -out tls.key 2048
# Generating RSA private key, 2048 bit long modulus
# .............................+++
# ...+++
# e is 65537 (0x10001)
openssl req -new -x509 -key tls.key -out tls.crt
-subj /C=CN/ST=Beijing/L=Beijing/O=DevOps/CN=tomcat.youmen.com
ls
# tls.crt tls.key
# 我们用来https加密的证书不能直接放到Pod需要将他转换成secret格式,他也是一个k8s对象.
kubectl create secret tls tomcat-ingress-secret --cert=tls.crt --key=tls.key
kubectl get secret
NAME TYPE DATA AGE
default-token-j9thc kubernetes.io/service-account-token 3 5d23h
tomcat-ingress-secret kubernetes.io/tls 2 6s
kubectl describe secret tomcat-ingress-secret
Name: tomcat-ingress-secret
Namespace: default
Labels: <none>
Annotations: <none>
Type: kubernetes.io/tls
Data
====
tls.crt: 1294 bytes
tls.key: 1675 bytes
cat ingress-tomcat-tls.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-tomcat-tls
namespace: default
annotations:
kubernetes.io/ingress.class: "nginx"
spec:
tls:
- hosts:
- tomcat.youmen.com
secretName: tomcat-ingress-secret
rules:
- host: tomcat.youmen.com
http:
paths:
- path:
backend:
serviceName: tomcat
servicePort: 8080
apply Ingress-tomcat-tls.yaml
kubectl describe ingress ingress-tomcat-tls
Name: ingress-tomcat-tls
Namespace: default
Address: 10.96.120.168
Default backend: default-http-backend:80 (<none>)
TLS:
tomcat-ingress-secret terminates tomcat.youmen.com
Rules:
Host Path Backends
---- ---- --------
tomcat.youmen.com
tomcat:8080 (10.244.1.45:8080,10.244.1.46:8080,10.244.2.35:8080)
Annotations:
kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"extensions/v1beta1","kind":
"Ingress","metadata":{"annotations":{"kubernetes.io/ingress.class":"nginx"},"name":"
ingress-tomcat-tls","namespace":"default"},"spec":{"rules":[{"host":"tomcat.youmen.com",
"http":{"paths":[{"backend":{"serviceName":"tomcat","servicePort":8080},"path":null}]}}],
"tls":[{"hosts":["tomcat.youmen.com"],"secretName":"tomcat-ingress-secret"}]}}
kubernetes.io/ingress.class: nginx
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal CREATE <invalid> nginx-ingress-controller Ingress default/ingress-tomcat-tls
Normal UPDATE <invalid> nginx-ingress-controller Ingress default/ingress-tomcat-tls
kubectl get secret
NAME TYPE DATA AGE
default-token-j9thc kubernetes.io/service-account-token 3 5d23h
tomcat-ingress-secret kubernetes.io/tls 2 10m
# 我们去ingress-nginx查看一下证书有没有注入进来
kubectl exec -n ingress-nginx -it nginx-ingress-controller-568867bf56-wwgqx /bin/bash
www-data@nginx-ingress-controller-5688f56-wwgqx:/etc/nginx$ cat nginx.conf |grep ssl_certificate_*
ssl_certificate /etc/ingress-controller/ssl/default-fake-certificate.pem;
ssl_certificate_key /etc/ingress-controller/ssl/default-fake-certificate.pem;
# 接下来浏览器访问https//域名:30443即可