Linux防火墙iptables命令管理入门
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.iptables命令概述
1>.iptables是一个高度模块化工具

[root@hdp101.yinzhengjie.org.cn ~]# yum info iptables Loaded plugins: fastestmirror Determining fastest mirrors * base: mirrors.tuna.tsinghua.edu.cn * extras: mirrors.huaweicloud.com * updates: mirror.bit.edu.cn Installed Packages Name : iptables Arch : x86_64 Version : 1.4.21 Release : 28.el7 Size : 1.5 M Repo : installed From repo : anaconda Summary : Tools for managing Linux kernel packet filtering capabilities URL : http://www.netfilter.org/ License : GPLv2 Description : The iptables utility controls the network packet filtering code in the : Linux kernel. If you need to set up firewalls and/or IP masquerading, : you should install this package. Available Packages Name : iptables Arch : i686 Version : 1.4.21 Release : 33.el7 Size : 424 k Repo : base/7/x86_64 Summary : Tools for managing Linux kernel packet filtering capabilities URL : http://www.netfilter.org/ License : GPLv2 Description : The iptables utility controls the network packet filtering code in the : Linux kernel. If you need to set up firewalls and/or IP masquerading, : you should install this package. Name : iptables Arch : x86_64 Version : 1.4.21 Release : 33.el7 Size : 433 k Repo : base/7/x86_64 Summary : Tools for managing Linux kernel packet filtering capabilities URL : http://www.netfilter.org/ License : GPLv2 Description : The iptables utility controls the network packet filtering code in the : Linux kernel. If you need to set up firewalls and/or IP masquerading, : you should install this package. [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# rpm -ql iptables /etc/sysconfig/ip6tables-config /etc/sysconfig/iptables-config /usr/bin/iptables-xml /usr/lib64/libip4tc.so.0 /usr/lib64/libip4tc.so.0.1.0 /usr/lib64/libip6tc.so.0 /usr/lib64/libip6tc.so.0.1.0 /usr/lib64/libiptc.so.0 /usr/lib64/libiptc.so.0.0.0 /usr/lib64/libxtables.so.10 /usr/lib64/libxtables.so.10.0.0 /usr/lib64/xtables /usr/lib64/xtables/libip6t_DNAT.so /usr/lib64/xtables/libip6t_DNPT.so /usr/lib64/xtables/libip6t_HL.so /usr/lib64/xtables/libip6t_LOG.so /usr/lib64/xtables/libip6t_MASQUERADE.so /usr/lib64/xtables/libip6t_NETMAP.so /usr/lib64/xtables/libip6t_REDIRECT.so /usr/lib64/xtables/libip6t_REJECT.so /usr/lib64/xtables/libip6t_SNAT.so /usr/lib64/xtables/libip6t_SNPT.so /usr/lib64/xtables/libip6t_ah.so /usr/lib64/xtables/libip6t_dst.so /usr/lib64/xtables/libip6t_eui64.so /usr/lib64/xtables/libip6t_frag.so /usr/lib64/xtables/libip6t_hbh.so /usr/lib64/xtables/libip6t_hl.so /usr/lib64/xtables/libip6t_icmp6.so /usr/lib64/xtables/libip6t_ipv6header.so /usr/lib64/xtables/libip6t_mh.so /usr/lib64/xtables/libip6t_rt.so /usr/lib64/xtables/libipt_CLUSTERIP.so /usr/lib64/xtables/libipt_DNAT.so /usr/lib64/xtables/libipt_ECN.so /usr/lib64/xtables/libipt_LOG.so /usr/lib64/xtables/libipt_MASQUERADE.so /usr/lib64/xtables/libipt_MIRROR.so /usr/lib64/xtables/libipt_NETMAP.so /usr/lib64/xtables/libipt_REDIRECT.so /usr/lib64/xtables/libipt_REJECT.so /usr/lib64/xtables/libipt_SAME.so /usr/lib64/xtables/libipt_SNAT.so /usr/lib64/xtables/libipt_TTL.so /usr/lib64/xtables/libipt_ULOG.so /usr/lib64/xtables/libipt_ah.so /usr/lib64/xtables/libipt_icmp.so /usr/lib64/xtables/libipt_realm.so /usr/lib64/xtables/libipt_ttl.so /usr/lib64/xtables/libipt_unclean.so /usr/lib64/xtables/libxt_AUDIT.so /usr/lib64/xtables/libxt_CHECKSUM.so /usr/lib64/xtables/libxt_CLASSIFY.so /usr/lib64/xtables/libxt_CONNMARK.so /usr/lib64/xtables/libxt_CONNSECMARK.so /usr/lib64/xtables/libxt_CT.so /usr/lib64/xtables/libxt_DSCP.so /usr/lib64/xtables/libxt_HMARK.so /usr/lib64/xtables/libxt_IDLETIMER.so /usr/lib64/xtables/libxt_LED.so /usr/lib64/xtables/libxt_MARK.so /usr/lib64/xtables/libxt_NFLOG.so /usr/lib64/xtables/libxt_NFQUEUE.so /usr/lib64/xtables/libxt_NOTRACK.so /usr/lib64/xtables/libxt_RATEEST.so /usr/lib64/xtables/libxt_SECMARK.so /usr/lib64/xtables/libxt_SET.so /usr/lib64/xtables/libxt_SYNPROXY.so /usr/lib64/xtables/libxt_TCPMSS.so /usr/lib64/xtables/libxt_TCPOPTSTRIP.so /usr/lib64/xtables/libxt_TEE.so /usr/lib64/xtables/libxt_TOS.so /usr/lib64/xtables/libxt_TPROXY.so /usr/lib64/xtables/libxt_TRACE.so /usr/lib64/xtables/libxt_addrtype.so /usr/lib64/xtables/libxt_bpf.so /usr/lib64/xtables/libxt_cgroup.so /usr/lib64/xtables/libxt_cluster.so /usr/lib64/xtables/libxt_comment.so /usr/lib64/xtables/libxt_connbytes.so /usr/lib64/xtables/libxt_connlabel.so /usr/lib64/xtables/libxt_connlimit.so /usr/lib64/xtables/libxt_connmark.so /usr/lib64/xtables/libxt_conntrack.so /usr/lib64/xtables/libxt_cpu.so /usr/lib64/xtables/libxt_dccp.so /usr/lib64/xtables/libxt_devgroup.so /usr/lib64/xtables/libxt_dscp.so /usr/lib64/xtables/libxt_ecn.so /usr/lib64/xtables/libxt_esp.so /usr/lib64/xtables/libxt_hashlimit.so /usr/lib64/xtables/libxt_helper.so /usr/lib64/xtables/libxt_iprange.so /usr/lib64/xtables/libxt_ipvs.so /usr/lib64/xtables/libxt_length.so /usr/lib64/xtables/libxt_limit.so /usr/lib64/xtables/libxt_mac.so /usr/lib64/xtables/libxt_mark.so /usr/lib64/xtables/libxt_multiport.so /usr/lib64/xtables/libxt_nfacct.so /usr/lib64/xtables/libxt_osf.so /usr/lib64/xtables/libxt_owner.so /usr/lib64/xtables/libxt_physdev.so /usr/lib64/xtables/libxt_pkttype.so /usr/lib64/xtables/libxt_policy.so /usr/lib64/xtables/libxt_quota.so /usr/lib64/xtables/libxt_rateest.so /usr/lib64/xtables/libxt_recent.so /usr/lib64/xtables/libxt_rpfilter.so /usr/lib64/xtables/libxt_sctp.so /usr/lib64/xtables/libxt_set.so /usr/lib64/xtables/libxt_socket.so /usr/lib64/xtables/libxt_standard.so /usr/lib64/xtables/libxt_state.so /usr/lib64/xtables/libxt_statistic.so /usr/lib64/xtables/libxt_string.so /usr/lib64/xtables/libxt_tcp.so /usr/lib64/xtables/libxt_tcpmss.so /usr/lib64/xtables/libxt_time.so /usr/lib64/xtables/libxt_tos.so /usr/lib64/xtables/libxt_u32.so /usr/lib64/xtables/libxt_udp.so /usr/sbin/ip6tables /usr/sbin/ip6tables-restore /usr/sbin/ip6tables-save /usr/sbin/iptables /usr/sbin/iptables-restore /usr/sbin/iptables-save /usr/sbin/xtables-multi /usr/share/doc/iptables-1.4.21 /usr/share/doc/iptables-1.4.21/COPYING /usr/share/doc/iptables-1.4.21/INCOMPATIBILITIES /usr/share/man/man1/iptables-xml.1.gz /usr/share/man/man8/ip6tables-restore.8.gz /usr/share/man/man8/ip6tables-save.8.gz /usr/share/man/man8/ip6tables.8.gz /usr/share/man/man8/iptables-extensions.8.gz /usr/share/man/man8/iptables-restore.8.gz /usr/share/man/man8/iptables-save.8.gz /usr/share/man/man8/iptables.8.gz [root@hdp101.yinzhengjie.org.cn ~]#
如果你不是自己编译Linux内核安装的操作系统基本上常见的Linux发行版默认就已经安装了iptables工具了,如果你是CentOS操作系系统可以直接使用"yum -y install iptables"进行安装。
iptables命令是一个高度模块化工具,由诸多扩展模块实现其检查条件或处理动作的定义,我们通过"rpm -ql iptables"命令可以查看到"/usr/lib64/xtables/"目录下有很多iptables的文件,其中以"libip6t_*"开头的文件是用于处理IPV6的扩展匹配条件或扩展动作处理的,而以"libipt_*"或者"libxt_*"的文件则是用于处理IPV4的扩展匹配条件或扩展动作处理的。
2>.iptables的语法格式
查看"man iptables"可以查看到iptables命令的帮助信息,如下图所示。
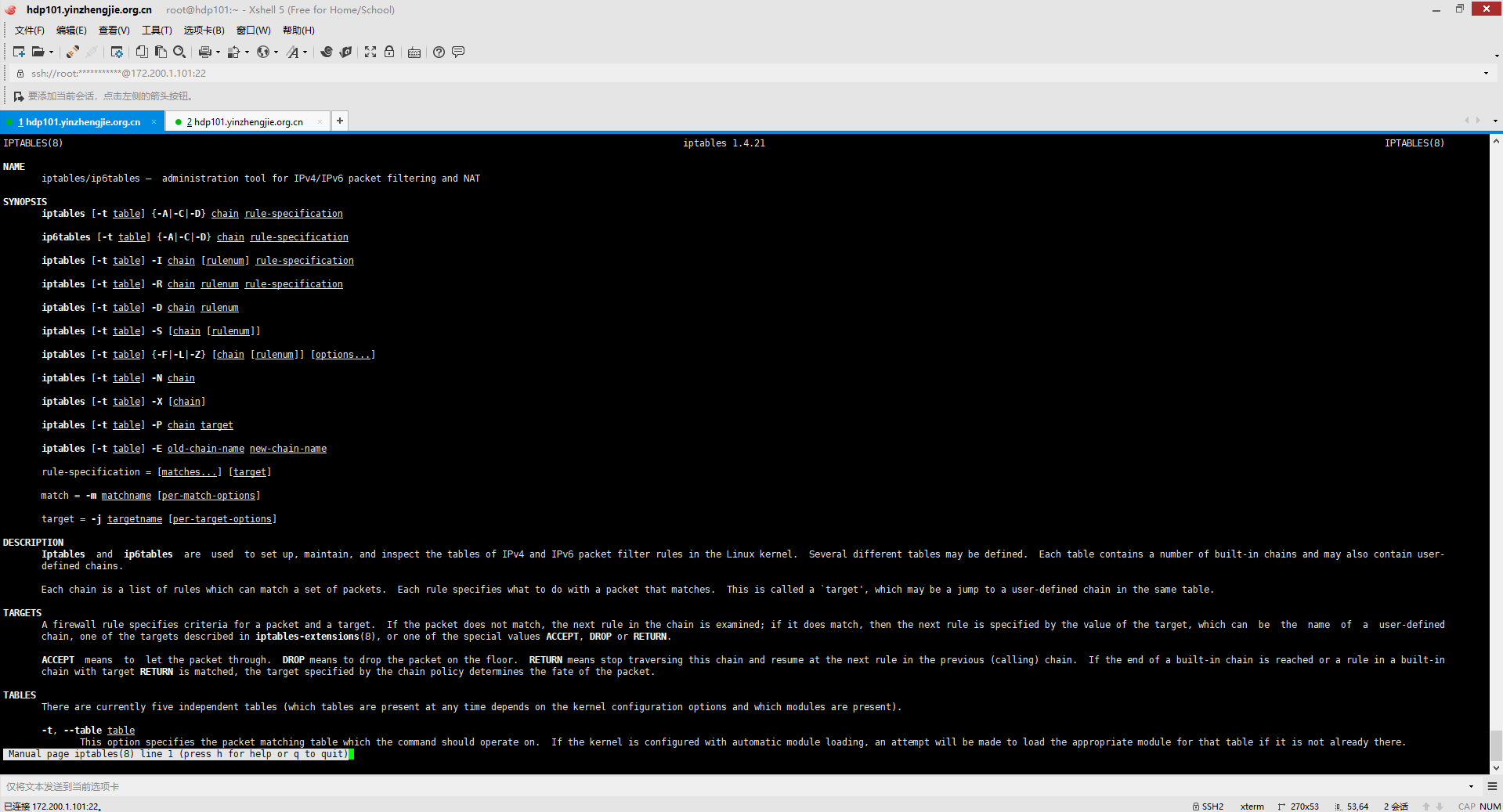
3>.当我们关闭防火墙时,默认规则时允许(ACCEPT)的

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL Chain INPUT (policy ACCEPT 618 packets, 74197 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 581 packets, 75073 bytes) pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]#

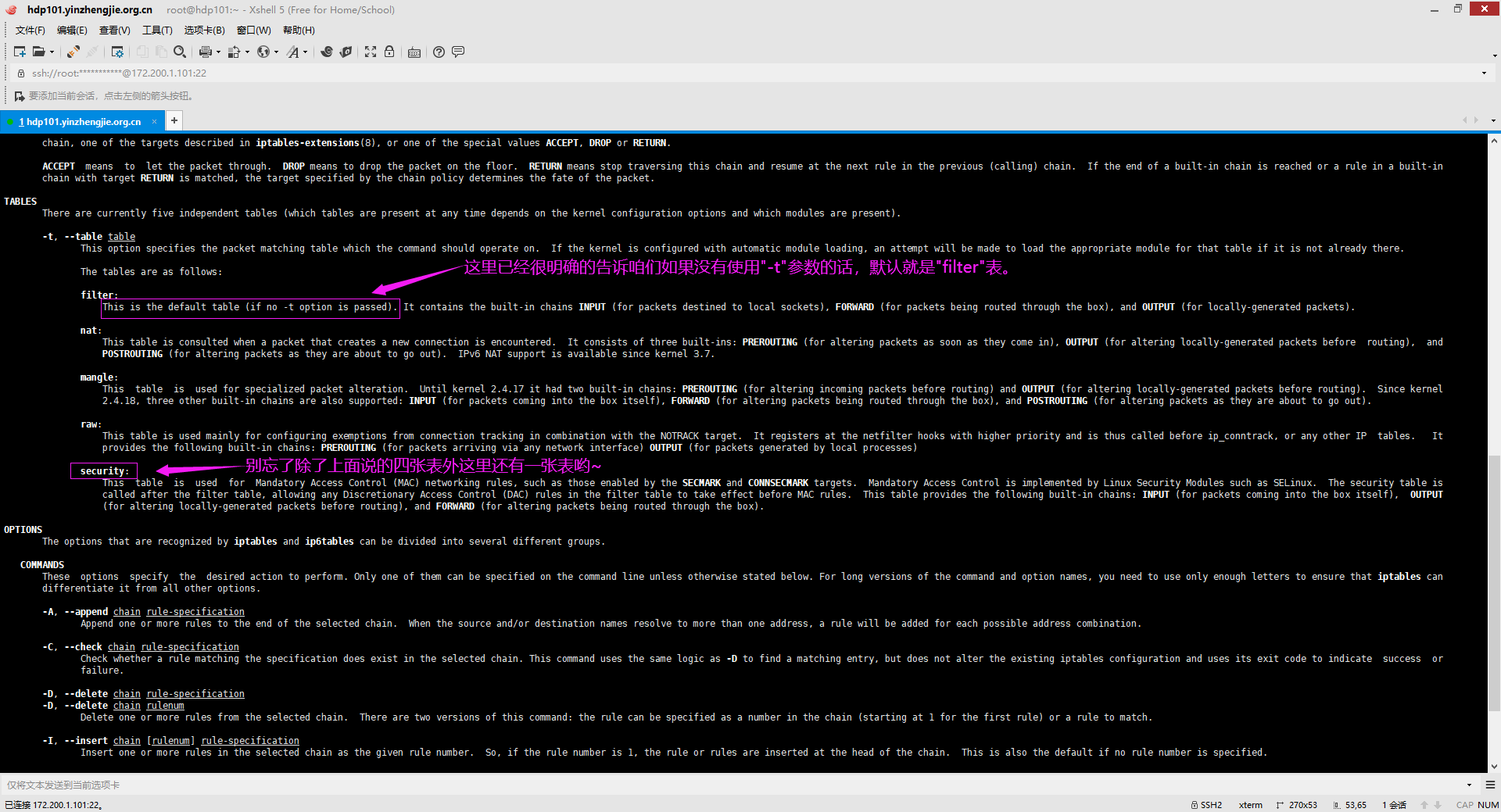
4>.查看"-t"参数支持的选项
通过"man iptables"中的文档可知,"-t"参数等效于"--table",即指定表名,可选的表面如下图所示。
5>."COMMANDS"的分类
通过"man iptables"可以查看到COMMANDS支持的各种参数,我们可以对齐分为以下三类。 链(chain)管理: -N: 等效于"--new-chain"选项,即自定义一条新的规则链。新创建的链引用计数默认为0。 -X: 等效于"--delete-chain"选项,即删除自定义的规则链。注意,仅能删除用户自定义引用计数为0且规则为空(没有定义规则)的链。 -P: 等效于"--policy"选项,即设置默认策略,对于filter表中的链而言,其默认策略有:ACCEPT(接收),DROP(丢弃),REJECT(拒绝)。 -E: 等效于"--rename-chain"选项,即重命名自定义链,引用计数不为0的自定义链不能够被重命名,也不能被删除。 规则管理: -A: 等效于"--append"选项,即最佳一条规则。 -I: 等效于"--insert"选项,即插入规则,可以指定插入的位置,省略时表示将新增的规则插入到第一条。 -D: 等效于"--delete"选项,即指明删除规则序号或规则本身。 -R: 等效于"--replace"选项,即替换指定链上的指定规则。 -F: 等效于"--flush"选项,即清空指定的规则链。 -Z: 等效于"--zero"选项,即将规则的计数器清空(即置零)。 iptables的每条规则都有两个计数器,一个是匹配到的报文个数(pkts),另一个是匹配到的所有报文的大小之和(bytes) 查看: -L: 等效于"--list"选项,列出指定键上的所有规则。它还支持以下选项: -n: 即numberic,表示以数字格式显式地址和端口号。如果不指定该参数默认情况下,iptables会将IP地址反解成主机名。使用-n参数后则不会进行反解操作,就以IP地址的形式显示。 -v: 即verbose,表示显式详细信息,会显示计数器(iptables的每条规则都有两个计数器,一个是匹配到的报文个数(pkts),另一个是匹配到的所有报文的大小之和(bytes))。 你甚至还可以些"-vv","--vvv"显式更详细的信息哟~ -x: 即exactly,表示显式计数器结果的精确值。 --line-numbers: 表示显式规则的行号。

6>.iptales的常用参数
基本匹配条件: 无需加载任何模块,由iptables/netfilter自行提供。 -s:
等效于"--source"选项,即检查报文中的源IP地址是否符合此处指定的地址或范围。
-d:
等效于"--destination"选项,即检查报文中目标地址是否符合此处指定的地址或范围,匹配所有地址可以使用"0.0.0.0/0"
-p:
等效于"--protocol"选项,即指定协议,支持指定的协议有:tcp, udp, udplite, icmp, icmpv6,esp, ah, sctp, mh or the special keyword "all"。如果不指定协议默认则是"all",表示所有协议。
-i:
等效于"--in-interface"选项,即数据报文流入的接口,只能应用于数据报文流入的环节,只能应用于PREROUTING,INPUT和FORWARD链。
-o:
等效于"--out-interface"选项,即数据报文流出的接口,只能应用于数据报文流出的环节,只能应用于FORWARD,OUTPUT和POSTROUTING链。
-j:
等效于"--jump"选项,即表示如何处理规则的动作,如ACCEPT,REJECT,DROP。 扩展匹配条件: 需要加载扩展模块,方可生效。
隐式扩展:
不需要手动加载扩展模块,因为它们是对协议的扩展,所以,但凡使用"-p"指明了协议,就表示已经指明了要扩展的模块;
tcp:
"--spirce-port,--sport port[:prot]":
匹配报文的源端口,也可以是端口范围。
"--destination-port,--dport port[:prot]":
匹配报文的目标端口,可以是端口范围。
"--tcp-flags mask comp":
例如"--tcp-flages SYN,ACK,FIN,RST SYN"表示,要检查的标志位为SYN,ACK,FIN,RST四个,其中SYN必须为1,余下的必须为0。
udp:
7>.
二.使用iptables进行基础的查询操作
1>.查看filter表中的规则

[root@hdp101.yinzhengjie.org.cn ~]# systemctl status firewalld ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled) Active: inactive (dead) Docs: man:firewalld(1) Feb 11 18:00:37 hdp101.yinzhengjie.org.cn systemd[1]: Starting firewalld - dynamic firewall daemon... Feb 11 18:00:37 hdp101.yinzhengjie.org.cn systemd[1]: Started firewalld - dynamic firewall daemon. Feb 11 18:01:04 hdp101.yinzhengjie.org.cn systemd[1]: Stopping firewalld - dynamic firewall daemon... Feb 11 18:01:04 hdp101.yinzhengjie.org.cn systemd[1]: Stopped firewalld - dynamic firewall daemon. [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# systemctl start firewalld #为了看到实验效果,我们暂时把防火墙功能打开 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# systemctl status firewalld ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vendor preset: enabled) Active: active (running) since Tue 2020-02-11 18:01:18 CST; 1s ago Docs: man:firewalld(1) Main PID: 18613 (firewalld) CGroup: /system.slice/firewalld.service └─18613 /usr/bin/python2 -Es /usr/sbin/firewalld --nofork --nopid Feb 11 18:01:17 hdp101.yinzhengjie.org.cn systemd[1]: Starting firewalld - dynamic firewall daemon... Feb 11 18:01:18 hdp101.yinzhengjie.org.cn systemd[1]: Started firewalld - dynamic firewall daemon. [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t filter -L Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere INPUT_ZONES_SOURCE all -- anywhere anywhere INPUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALID REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere FORWARD_direct all -- anywhere anywhere FORWARD_IN_ZONES_SOURCE all -- anywhere anywhere FORWARD_IN_ZONES all -- anywhere anywhere FORWARD_OUT_ZONES_SOURCE all -- anywhere anywhere FORWARD_OUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALID REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere OUTPUT_direct all -- anywhere anywhere Chain FORWARD_IN_ZONES (1 references) target prot opt source destination FWDI_public all -- anywhere anywhere [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_OUT_ZONES (1 references) target prot opt source destination FWDO_public all -- anywhere anywhere [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_direct (1 references) target prot opt source destination Chain FWDI_public (1 references) target prot opt source destination FWDI_public_log all -- anywhere anywhere FWDI_public_deny all -- anywhere anywhere FWDI_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain FWDI_public_allow (1 references) target prot opt source destination Chain FWDI_public_deny (1 references) target prot opt source destination Chain FWDI_public_log (1 references) target prot opt source destination Chain FWDO_public (1 references) target prot opt source destination FWDO_public_log all -- anywhere anywhere FWDO_public_deny all -- anywhere anywhere FWDO_public_allow all -- anywhere anywhere Chain FWDO_public_allow (1 references) target prot opt source destination Chain FWDO_public_deny (1 references) target prot opt source destination Chain FWDO_public_log (1 references) target prot opt source destination Chain INPUT_ZONES (1 references) target prot opt source destination IN_public all -- anywhere anywhere [goto] Chain INPUT_ZONES_SOURCE (1 references) target prot opt source destination Chain INPUT_direct (1 references) target prot opt source destination Chain IN_public (1 references) target prot opt source destination IN_public_log all -- anywhere anywhere IN_public_deny all -- anywhere anywhere IN_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain IN_public_allow (1 references) target prot opt source destination ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) target prot opt source destination Chain IN_public_log (1 references) target prot opt source destination Chain OUTPUT_direct (1 references) target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere INPUT_ZONES_SOURCE all -- anywhere anywhere INPUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALID REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere FORWARD_direct all -- anywhere anywhere FORWARD_IN_ZONES_SOURCE all -- anywhere anywhere FORWARD_IN_ZONES all -- anywhere anywhere FORWARD_OUT_ZONES_SOURCE all -- anywhere anywhere FORWARD_OUT_ZONES all -- anywhere anywhere DROP all -- anywhere anywhere ctstate INVALID REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere OUTPUT_direct all -- anywhere anywhere Chain FORWARD_IN_ZONES (1 references) target prot opt source destination FWDI_public all -- anywhere anywhere [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_OUT_ZONES (1 references) target prot opt source destination FWDO_public all -- anywhere anywhere [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_direct (1 references) target prot opt source destination Chain FWDI_public (1 references) target prot opt source destination FWDI_public_log all -- anywhere anywhere FWDI_public_deny all -- anywhere anywhere FWDI_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain FWDI_public_allow (1 references) target prot opt source destination Chain FWDI_public_deny (1 references) target prot opt source destination Chain FWDI_public_log (1 references) target prot opt source destination Chain FWDO_public (1 references) target prot opt source destination FWDO_public_log all -- anywhere anywhere FWDO_public_deny all -- anywhere anywhere FWDO_public_allow all -- anywhere anywhere Chain FWDO_public_allow (1 references) target prot opt source destination Chain FWDO_public_deny (1 references) target prot opt source destination Chain FWDO_public_log (1 references) target prot opt source destination Chain INPUT_ZONES (1 references) target prot opt source destination IN_public all -- anywhere anywhere [goto] Chain INPUT_ZONES_SOURCE (1 references) target prot opt source destination Chain INPUT_direct (1 references) target prot opt source destination Chain IN_public (1 references) target prot opt source destination IN_public_log all -- anywhere anywhere IN_public_deny all -- anywhere anywhere IN_public_allow all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere Chain IN_public_allow (1 references) target prot opt source destination ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) target prot opt source destination Chain IN_public_log (1 references) target prot opt source destination Chain OUTPUT_direct (1 references) target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -L -n Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 INPUT_direct all -- 0.0.0.0/0 0.0.0.0/0 INPUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 INPUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0 DROP all -- 0.0.0.0/0 0.0.0.0/0 ctstate INVALID REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_direct all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_IN_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_IN_ZONES all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_OUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 FORWARD_OUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0 DROP all -- 0.0.0.0/0 0.0.0.0/0 ctstate INVALID REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 OUTPUT_direct all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) target prot opt source destination FWDI_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_OUT_ZONES (1 references) target prot opt source destination FWDO_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_direct (1 references) target prot opt source destination Chain FWDI_public (1 references) target prot opt source destination FWDI_public_log all -- 0.0.0.0/0 0.0.0.0/0 FWDI_public_deny all -- 0.0.0.0/0 0.0.0.0/0 FWDI_public_allow all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) target prot opt source destination Chain FWDI_public_deny (1 references) target prot opt source destination Chain FWDI_public_log (1 references) target prot opt source destination Chain FWDO_public (1 references) target prot opt source destination FWDO_public_log all -- 0.0.0.0/0 0.0.0.0/0 FWDO_public_deny all -- 0.0.0.0/0 0.0.0.0/0 FWDO_public_allow all -- 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) target prot opt source destination Chain FWDO_public_deny (1 references) target prot opt source destination Chain FWDO_public_log (1 references) target prot opt source destination Chain INPUT_ZONES (1 references) target prot opt source destination IN_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) target prot opt source destination Chain INPUT_direct (1 references) target prot opt source destination Chain IN_public (1 references) target prot opt source destination IN_public_log all -- 0.0.0.0/0 0.0.0.0/0 IN_public_deny all -- 0.0.0.0/0 0.0.0.0/0 IN_public_allow all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) target prot opt source destination ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) target prot opt source destination Chain IN_public_log (1 references) target prot opt source destination Chain OUTPUT_direct (1 references) target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -nL --line-numbers Chain INPUT (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 3 INPUT_direct all -- 0.0.0.0/0 0.0.0.0/0 4 INPUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 5 INPUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0 6 DROP all -- 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 3 FORWARD_direct all -- 0.0.0.0/0 0.0.0.0/0 4 FORWARD_IN_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 5 FORWARD_IN_ZONES all -- 0.0.0.0/0 0.0.0.0/0 6 FORWARD_OUT_ZONES_SOURCE all -- 0.0.0.0/0 0.0.0.0/0 7 FORWARD_OUT_ZONES all -- 0.0.0.0/0 0.0.0.0/0 8 DROP all -- 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 2 OUTPUT_direct all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) num target prot opt source destination 1 FWDI_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) num target prot opt source destination Chain FORWARD_OUT_ZONES (1 references) num target prot opt source destination 1 FWDO_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) num target prot opt source destination Chain FORWARD_direct (1 references) num target prot opt source destination Chain FWDI_public (1 references) num target prot opt source destination 1 FWDI_public_log all -- 0.0.0.0/0 0.0.0.0/0 2 FWDI_public_deny all -- 0.0.0.0/0 0.0.0.0/0 3 FWDI_public_allow all -- 0.0.0.0/0 0.0.0.0/0 4 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) num target prot opt source destination Chain FWDI_public_deny (1 references) num target prot opt source destination Chain FWDI_public_log (1 references) num target prot opt source destination Chain FWDO_public (1 references) num target prot opt source destination 1 FWDO_public_log all -- 0.0.0.0/0 0.0.0.0/0 2 FWDO_public_deny all -- 0.0.0.0/0 0.0.0.0/0 3 FWDO_public_allow all -- 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) num target prot opt source destination Chain FWDO_public_deny (1 references) num target prot opt source destination Chain FWDO_public_log (1 references) num target prot opt source destination Chain INPUT_ZONES (1 references) num target prot opt source destination 1 IN_public all -- 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) num target prot opt source destination Chain INPUT_direct (1 references) num target prot opt source destination Chain IN_public (1 references) num target prot opt source destination 1 IN_public_log all -- 0.0.0.0/0 0.0.0.0/0 2 IN_public_deny all -- 0.0.0.0/0 0.0.0.0/0 3 IN_public_allow all -- 0.0.0.0/0 0.0.0.0/0 4 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) num target prot opt source destination 1 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) num target prot opt source destination Chain IN_public_log (1 references) num target prot opt source destination Chain OUTPUT_direct (1 references) num target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -nL --line-numbers -v Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 30990 4292K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 598 31815 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 1 92 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 1 92 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 1 92 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 436 packets, 182K bytes) num pkts bytes target prot opt in out source destination 1 31049 4288K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0 2 436 182K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 1 92 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain IN_public (1 references) num pkts bytes target prot opt in out source destination 1 1 92 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 1 92 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 1 92 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) num pkts bytes target prot opt in out source destination 1 1 92 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -nL --line-numbers -vv Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 31442 4349K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 599 31891 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 1 92 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 1 92 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 1 92 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 449 packets, 190K bytes) num pkts bytes target prot opt in out source destination 1 31483 4345K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0 2 449 190K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 1 92 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain IN_public (1 references) num pkts bytes target prot opt in out source destination 1 1 92 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 1 92 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 1 92 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) num pkts bytes target prot opt in out source destination 1 1 92 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination libiptc vlibxtables.so.10. 13584 bytes. Table `filter' Hooks: pre/in/fwd/out/post = ffffffff/0/650/dd0/ffffffff Underflows: pre/in/fwd/out/post = ffffffff/5b8/d38/f00/ffffffff Entry 0 (0): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 31442 packets, 4349425 bytes Cache: 00000000 Match name: `conntrack' Target name: `' [40] verdict=NF_ACCEPT Entry 1 (352): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `lo'/XXX.............to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 599 packets, 31891 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 2 (504): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=10608 Entry 3 (656): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=10280 Entry 4 (808): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=9800 Entry 5 (960): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Match name: `conntrack' Target name: `' [40] verdict=NF_DROP Entry 6 (1312): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `REJECT' [40] Entry 7 (1464): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 8 (1616): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Match name: `conntrack' Target name: `' [40] verdict=NF_ACCEPT Entry 9 (1968): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `lo'/XXX.............to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 10 (2120): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=5784 Entry 11 (2272): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=4648 Entry 12 (2424): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=4168 Entry 13 (2576): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=5456 Entry 14 (2728): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=4976 Entry 15 (2880): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Match name: `conntrack' Target name: `' [40] verdict=NF_DROP Entry 16 (3232): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `REJECT' [40] Entry 17 (3384): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 18 (3536): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `lo'/XXX............. Protocol: 0 Flags: 00 Invflags: 00 Counters: 31483 packets, 4344956 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 19 (3688): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 449 packets, 190168 bytes Cache: 00000000 Target name: `' [40] verdict=13256 Entry 20 (3840): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 449 packets, 190168 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 21 (3992): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FORWARD_IN_ZONES' Entry 22 (4168): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `+'/................to `'/................ Protocol: 0 Flags: 02 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=6112 Entry 23 (4320): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 24 (4472): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FORWARD_IN_ZONES_SOURCE' Entry 25 (4648): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 26 (4800): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FORWARD_OUT_ZONES' Entry 27 (4976): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `+'/................ Protocol: 0 Flags: 02 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=8032 Entry 28 (5128): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 29 (5280): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FORWARD_OUT_ZONES_SOURCE' Entry 30 (5456): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 31 (5608): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FORWARD_direct' Entry 32 (5784): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 33 (5936): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDI_public' Entry 34 (6112): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=7704 Entry 35 (6264): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=7376 Entry 36 (6416): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=7048 Entry 37 (6568): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 1 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 38 (6720): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 39 (6872): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDI_public_allow' Entry 40 (7048): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 41 (7200): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDI_public_deny' Entry 42 (7376): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 43 (7528): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDI_public_log' Entry 44 (7704): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 45 (7856): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDO_public' Entry 46 (8032): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=9472 Entry 47 (8184): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=9144 Entry 48 (8336): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=8816 Entry 49 (8488): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 50 (8640): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDO_public_allow' Entry 51 (8816): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 52 (8968): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDO_public_deny' Entry 53 (9144): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 54 (9296): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`FWDO_public_log' Entry 55 (9472): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 56 (9624): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`INPUT_ZONES' Entry 57 (9800): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `+'/................to `'/................ Protocol: 0 Flags: 02 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=10936 Entry 58 (9952): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 59 (10104): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`INPUT_ZONES_SOURCE' Entry 60 (10280): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 61 (10432): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`INPUT_direct' Entry 62 (10608): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 63 (10760): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`IN_public' Entry 64 (10936): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=12928 Entry 65 (11088): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=12600 Entry 66 (11240): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=11872 Entry 67 (11392): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 1 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=NF_ACCEPT Entry 68 (11544): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 69 (11696): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`IN_public_allow' Entry 70 (11872): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 6 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Match name: `tcp' Match name: `conntrack' Target name: `' [40] verdict=NF_ACCEPT Entry 71 (12272): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 72 (12424): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`IN_public_deny' Entry 73 (12600): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 74 (12752): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`IN_public_log' Entry 75 (12928): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 1 packets, 92 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 76 (13080): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`OUTPUT_direct' Entry 77 (13256): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 449 packets, 190168 bytes Cache: 00000000 Target name: `' [40] verdict=RETURN Entry 78 (13408): SRC IP: 0.0.0.0/0.0.0.0 DST IP: 0.0.0.0/0.0.0.0 Interface: `'/................to `'/................ Protocol: 0 Flags: 00 Invflags: 00 Counters: 0 packets, 0 bytes Cache: 00000000 Target name: `ERROR' [64] error=`ERROR' [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 34735 4806K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 668 35479 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 1 92 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 1 92 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 1 92 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 687 packets, 324K bytes) num pkts bytes target prot opt in out source destination 1 34559 4785K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0 2 687 324K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 1 92 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain IN_public (1 references) num pkts bytes target prot opt in out source destination 1 1 92 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 1 92 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 1 92 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) num pkts bytes target prot opt in out source destination 1 1 92 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL INPUT --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 37538 5177K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 711 37739 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 1 92 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 1 92 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 1 92 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
2>.查看mangle表中的规则

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t mangle -L Chain PREROUTING (policy ACCEPT) target prot opt source destination PREROUTING_direct all -- anywhere anywhere PREROUTING_ZONES_SOURCE all -- anywhere anywhere PREROUTING_ZONES all -- anywhere anywhere Chain INPUT (policy ACCEPT) target prot opt source destination INPUT_direct all -- anywhere anywhere Chain FORWARD (policy ACCEPT) target prot opt source destination FORWARD_direct all -- anywhere anywhere Chain OUTPUT (policy ACCEPT) target prot opt source destination OUTPUT_direct all -- anywhere anywhere Chain POSTROUTING (policy ACCEPT) target prot opt source destination POSTROUTING_direct all -- anywhere anywhere Chain FORWARD_direct (1 references) target prot opt source destination Chain INPUT_direct (1 references) target prot opt source destination Chain OUTPUT_direct (1 references) target prot opt source destination Chain POSTROUTING_direct (1 references) target prot opt source destination Chain PREROUTING_ZONES (1 references) target prot opt source destination PRE_public all -- anywhere anywhere [goto] Chain PREROUTING_ZONES_SOURCE (1 references) target prot opt source destination Chain PREROUTING_direct (1 references) target prot opt source destination Chain PRE_public (1 references) target prot opt source destination PRE_public_log all -- anywhere anywhere PRE_public_deny all -- anywhere anywhere PRE_public_allow all -- anywhere anywhere Chain PRE_public_allow (1 references) target prot opt source destination Chain PRE_public_deny (1 references) target prot opt source destination Chain PRE_public_log (1 references) target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t mangle -vnL --line-numbers Chain PREROUTING (policy ACCEPT 40397 packets, 5497K bytes) num pkts bytes target prot opt in out source destination 1 40397 5497K PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 2 40397 5497K PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 3 40397 5497K PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 Chain INPUT (policy ACCEPT 40397 packets, 5497K bytes) num pkts bytes target prot opt in out source destination 1 40397 5497K INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 40198 packets, 5779K bytes) num pkts bytes target prot opt in out source destination 1 40198 5779K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain POSTROUTING (policy ACCEPT 40198 packets, 5779K bytes) num pkts bytes target prot opt in out source destination 1 40198 5779K POSTROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain POSTROUTING_direct (1 references) num pkts bytes target prot opt in out source destination Chain PREROUTING_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 40397 5497K PRE_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain PREROUTING_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain PREROUTING_direct (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public (1 references) num pkts bytes target prot opt in out source destination 1 40397 5497K PRE_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 40397 5497K PRE_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 40397 5497K PRE_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain PRE_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public_log (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t mangle -vnL PREROUTING --line-numbers Chain PREROUTING (policy ACCEPT 41276 packets, 5653K bytes) num pkts bytes target prot opt in out source destination 1 41276 5653K PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 2 41276 5653K PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 3 41276 5653K PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
3>.查看nat表中的规则

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t nat -L Chain PREROUTING (policy ACCEPT) target prot opt source destination PREROUTING_direct all -- anywhere anywhere PREROUTING_ZONES_SOURCE all -- anywhere anywhere PREROUTING_ZONES all -- anywhere anywhere Chain INPUT (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination OUTPUT_direct all -- anywhere anywhere Chain POSTROUTING (policy ACCEPT) target prot opt source destination POSTROUTING_direct all -- anywhere anywhere POSTROUTING_ZONES_SOURCE all -- anywhere anywhere POSTROUTING_ZONES all -- anywhere anywhere Chain OUTPUT_direct (1 references) target prot opt source destination Chain POSTROUTING_ZONES (1 references) target prot opt source destination POST_public all -- anywhere anywhere [goto] Chain POSTROUTING_ZONES_SOURCE (1 references) target prot opt source destination Chain POSTROUTING_direct (1 references) target prot opt source destination Chain POST_public (1 references) target prot opt source destination POST_public_log all -- anywhere anywhere POST_public_deny all -- anywhere anywhere POST_public_allow all -- anywhere anywhere Chain POST_public_allow (1 references) target prot opt source destination Chain POST_public_deny (1 references) target prot opt source destination Chain POST_public_log (1 references) target prot opt source destination Chain PREROUTING_ZONES (1 references) target prot opt source destination PRE_public all -- anywhere anywhere [goto] Chain PREROUTING_ZONES_SOURCE (1 references) target prot opt source destination Chain PREROUTING_direct (1 references) target prot opt source destination Chain PRE_public (1 references) target prot opt source destination PRE_public_log all -- anywhere anywhere PRE_public_deny all -- anywhere anywhere PRE_public_allow all -- anywhere anywhere Chain PRE_public_allow (1 references) target prot opt source destination Chain PRE_public_deny (1 references) target prot opt source destination Chain PRE_public_log (1 references) target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t nat -vnL --line-numbers Chain PREROUTING (policy ACCEPT 1 packets, 92 bytes) num pkts bytes target prot opt in out source destination 1 1 92 PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 2 1 92 PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 3 1 92 PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 Chain INPUT (policy ACCEPT 1 packets, 92 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 834 packets, 44111 bytes) num pkts bytes target prot opt in out source destination 1 834 44111 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain POSTROUTING (policy ACCEPT 834 packets, 44111 bytes) num pkts bytes target prot opt in out source destination 1 834 44111 POSTROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 2 834 44111 POSTROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 3 834 44111 POSTROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain POSTROUTING_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 834 44111 POST_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain POSTROUTING_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain POSTROUTING_direct (1 references) num pkts bytes target prot opt in out source destination Chain POST_public (1 references) num pkts bytes target prot opt in out source destination 1 834 44111 POST_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 834 44111 POST_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 834 44111 POST_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain POST_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain POST_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain POST_public_log (1 references) num pkts bytes target prot opt in out source destination Chain PREROUTING_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 1 92 PRE_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain PREROUTING_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain PREROUTING_direct (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public (1 references) num pkts bytes target prot opt in out source destination 1 1 92 PRE_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 1 92 PRE_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 1 92 PRE_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain PRE_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public_log (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t nat -vnL PREROUTING --line-numbers Chain PREROUTING (policy ACCEPT 1 packets, 92 bytes) num pkts bytes target prot opt in out source destination 1 1 92 PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 2 1 92 PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 3 1 92 PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
4>.查看raw表中的规则

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t raw -L Chain PREROUTING (policy ACCEPT) target prot opt source destination PREROUTING_direct all -- anywhere anywhere PREROUTING_ZONES_SOURCE all -- anywhere anywhere PREROUTING_ZONES all -- anywhere anywhere Chain OUTPUT (policy ACCEPT) target prot opt source destination OUTPUT_direct all -- anywhere anywhere Chain OUTPUT_direct (1 references) target prot opt source destination Chain PREROUTING_ZONES (1 references) target prot opt source destination PRE_public all -- anywhere anywhere [goto] Chain PREROUTING_ZONES_SOURCE (1 references) target prot opt source destination Chain PREROUTING_direct (1 references) target prot opt source destination Chain PRE_public (1 references) target prot opt source destination PRE_public_log all -- anywhere anywhere PRE_public_deny all -- anywhere anywhere PRE_public_allow all -- anywhere anywhere Chain PRE_public_allow (1 references) target prot opt source destination Chain PRE_public_deny (1 references) target prot opt source destination Chain PRE_public_log (1 references) target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t raw -vnL --line-numbers Chain PREROUTING (policy ACCEPT 43083 packets, 5881K bytes) num pkts bytes target prot opt in out source destination 1 43083 5881K PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 2 43083 5881K PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 3 43083 5881K PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 42826 packets, 6174K bytes) num pkts bytes target prot opt in out source destination 1 42826 6174K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain PREROUTING_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 43083 5881K PRE_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain PREROUTING_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain PREROUTING_direct (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public (1 references) num pkts bytes target prot opt in out source destination 1 43083 5881K PRE_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 43083 5881K PRE_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 43083 5881K PRE_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain PRE_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain PRE_public_log (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t raw -vnL PREROUTING --line-numbers Chain PREROUTING (policy ACCEPT 43471 packets, 5932K bytes) num pkts bytes target prot opt in out source destination 1 43471 5932K PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0 2 43471 5932K PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 3 43471 5932K PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 [root@hdp101.yinzhengjie.org.cn ~]#
5>.查看security表中的规则

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t security -L Chain INPUT (policy ACCEPT) target prot opt source destination INPUT_direct all -- anywhere anywhere Chain FORWARD (policy ACCEPT) target prot opt source destination FORWARD_direct all -- anywhere anywhere Chain OUTPUT (policy ACCEPT) target prot opt source destination OUTPUT_direct all -- anywhere anywhere Chain FORWARD_direct (1 references) target prot opt source destination Chain INPUT_direct (1 references) target prot opt source destination Chain OUTPUT_direct (1 references) target prot opt source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t security -vnL --line-numbers Chain INPUT (policy ACCEPT 44201 packets, 6030K bytes) num pkts bytes target prot opt in out source destination 1 44201 6030K INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain OUTPUT (policy ACCEPT 43906 packets, 6326K bytes) num pkts bytes target prot opt in out source destination 1 43906 6326K OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -t security -vnL FORWARD --line-numbers Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
三.使用iptables进行链(chain)管理操作
1>.创建一个自定义链

[root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# systemctl stop firewalld [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 3493 packets, 475K bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 3466 packets, 475K bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -N in_myweb_rules [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 35 packets, 4480 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 32 packets, 4620 bytes) num pkts bytes target prot opt in out source destination Chain in_myweb_rules (0 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

2>.删除自定义链(只能删除自定义的链,还必须符合两个条件,即该链的引用计数为0且该链中没有规则。内置的链是无法删除的哟)

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 71 packets, 8948 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 66 packets, 9864 bytes) num pkts bytes target prot opt in out source destination Chain in_myweb_rules (0 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -X in_myweb_rules [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 36 packets, 4520 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 33 packets, 4660 bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
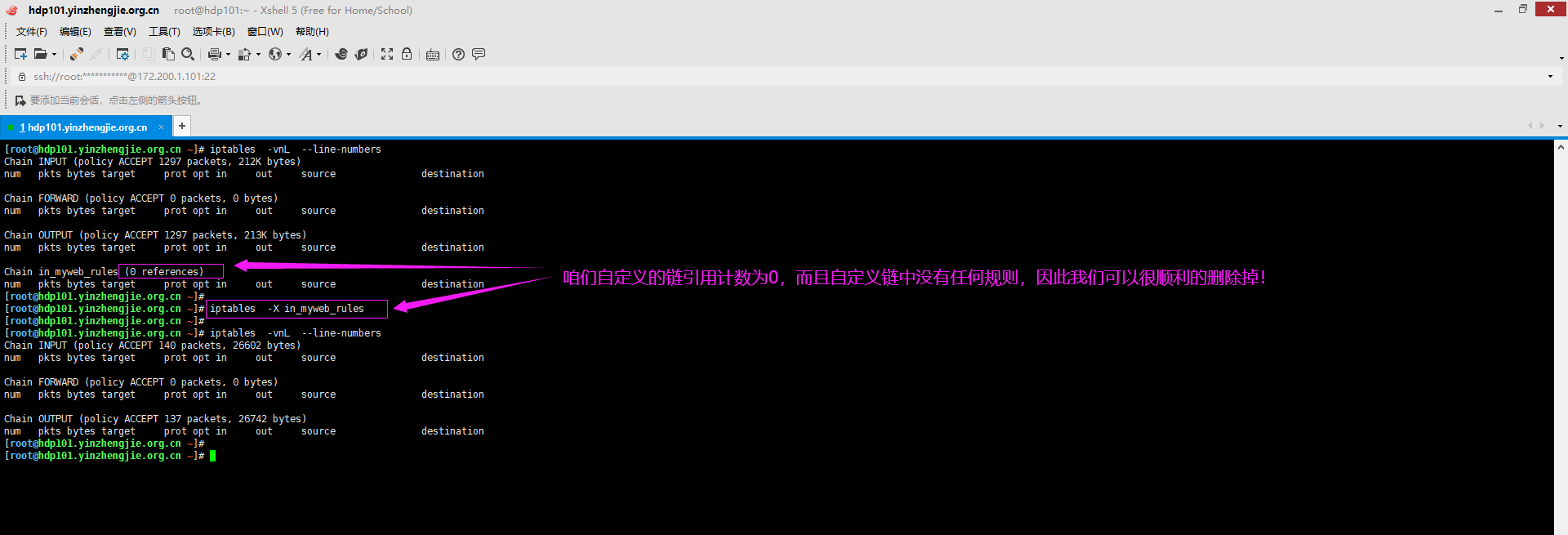
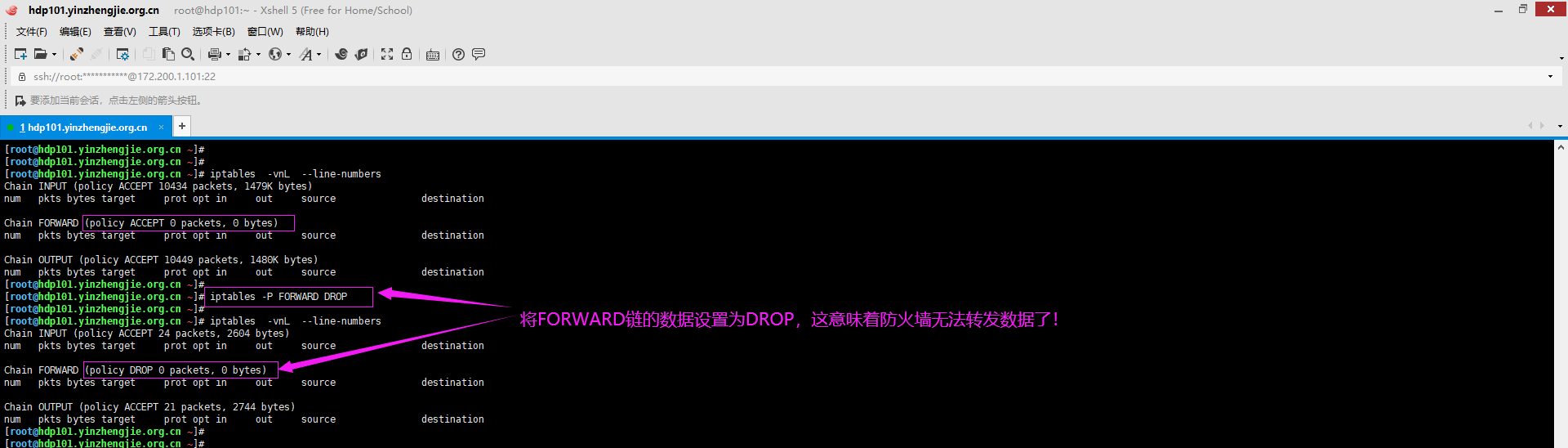
3>.设置默认策略

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 10434 packets, 1479K bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 10449 packets, 1480K bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -P FORWARD DROP [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 24 packets, 2604 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 21 packets, 2744 bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
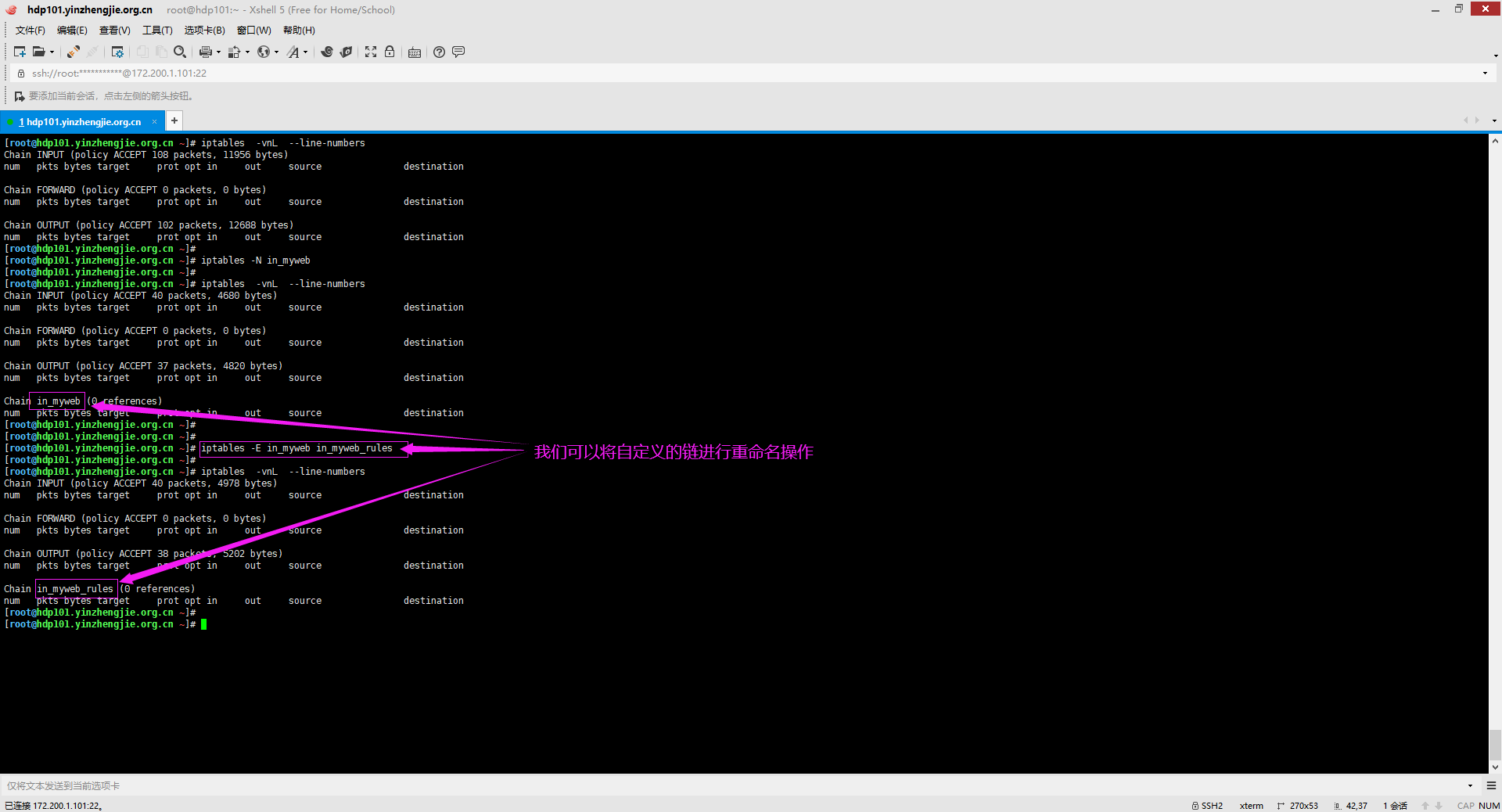
4>.重命名自定义链

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 108 packets, 11956 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 102 packets, 12688 bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -N in_myweb [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 40 packets, 4680 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 37 packets, 4820 bytes) num pkts bytes target prot opt in out source destination Chain in_myweb (0 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -E in_myweb in_myweb_rules [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 40 packets, 4978 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 38 packets, 5202 bytes) num pkts bytes target prot opt in out source destination Chain in_myweb_rules (0 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
四.使用iptables对链(chain)的规则管理操作
1>.将规则的计数器清零

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 64 7232 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 11 packets, 8048 bytes) num pkts bytes target prot opt in out source destination 1 48 6228 ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0 2 11 8048 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain IN_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -Z [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 41 4772 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 6 packets, 728 bytes) num pkts bytes target prot opt in out source destination 1 32 4152 ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0 2 6 728 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) num pkts bytes target prot opt in out source destination Chain IN_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL INPUT --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 3957 565K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 70 3664 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -Z INPUT [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL INPUT --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 52 6894 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL INPUT --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 1457 210K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 24 1248 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -Z INPUT 2 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL INPUT --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 1606 230K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
2>.清空规则

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 2227 packets, 282K bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 71 packets, 15232 bytes) num pkts bytes target prot opt in out source destination 1 14208 1983K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0 2 337 71020 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) num pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES (0 references) num pkts bytes target prot opt in out source destination 1 0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (0 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (0 references) num pkts bytes target prot opt in out source destination Chain IN_public (1 references) num pkts bytes target prot opt in out source destination 1 0 0 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 2 0 0 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 3 0 0 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW,UNTRACKED Chain IN_public_deny (1 references) num pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -F [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 22 packets, 2524 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 19 packets, 2632 bytes) num pkts bytes target prot opt in out source destination Chain FORWARD_IN_ZONES (0 references) num pkts bytes target prot opt in out source destination Chain FORWARD_IN_ZONES_SOURCE (0 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (0 references) num pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES_SOURCE (0 references) num pkts bytes target prot opt in out source destination Chain FORWARD_direct (0 references) num pkts bytes target prot opt in out source destination Chain FWDI_public (0 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_allow (0 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_deny (0 references) num pkts bytes target prot opt in out source destination Chain FWDI_public_log (0 references) num pkts bytes target prot opt in out source destination Chain FWDO_public (0 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_allow (0 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_deny (0 references) num pkts bytes target prot opt in out source destination Chain FWDO_public_log (0 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES (0 references) num pkts bytes target prot opt in out source destination Chain INPUT_ZONES_SOURCE (0 references) num pkts bytes target prot opt in out source destination Chain INPUT_direct (0 references) num pkts bytes target prot opt in out source destination Chain IN_public (0 references) num pkts bytes target prot opt in out source destination Chain IN_public_allow (0 references) num pkts bytes target prot opt in out source destination Chain IN_public_deny (0 references) num pkts bytes target prot opt in out source destination Chain IN_public_log (0 references) num pkts bytes target prot opt in out source destination Chain OUTPUT_direct (0 references) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL INPUT --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 7512 1049K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 105 5484 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -F INPUT [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL INPUT --line-numbers Chain INPUT (policy ACCEPT 92 packets, 6596 bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
3>.删除规则

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL FORWARD --line-numbers Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 9 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -D FORWARD 9 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL FORWARD --line-numbers Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 2 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 3 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 4 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 5 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 6 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 7 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 8 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#
4>.使用追加的方式添加规则

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 978 packets, 158K bytes) num pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 962 packets, 159K bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# hostname -i 172.200.1.101 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -t filter -A INPUT -s 172.200.0.0/21 -d 172.200.1.101 -p tcp -j ACCEPT [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 58 6888 ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 54 packets, 7164 bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 7 packets, 552 bytes) num pkts bytes target prot opt in out source destination 1 4107 535K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 4066 packets, 537K bytes) num pkts bytes target prot opt in out source destination [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# hostname -i 172.200.1.101 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -t filter -A OUTPUT -s 172.200.1.101 -d 172.200.0.0/21 -p tcp -j ACCEPT [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 4890 678K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 132 16938 ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL Chain INPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 45325 6269K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 40437 5867K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# hostname -i 172.200.1.101 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -A INPUT -d 172.200.1.101 -p icmp -j ACCEPT [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL Chain INPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 52599 6957K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 3 252 ACCEPT icmp -- * * 0.0.0.0/0 172.200.1.101 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 3 packets, 252 bytes) pkts bytes target prot opt in out source destination 51595 8407K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# tcpdump -i bond0 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on bond0, link-type EN10MB (Ethernet), capture size 262144 bytes 21:11:26.214130 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 64, length 64 21:11:27.214353 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 65, length 64 21:11:28.214509 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 66, length 64 21:11:29.213624 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 67, length 64 21:11:30.213814 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 68, length 64 21:11:31.214005 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 69, length 64 21:11:32.213895 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 70, length 64 21:11:33.214398 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 71, length 64 21:11:34.213683 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 72, length 64 21:11:35.214754 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 73, length 64 21:11:36.214345 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 74, length 64 21:11:37.214123 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 75, length 64 21:11:38.214719 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 76, length 64 21:11:39.213834 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 77, length 64 21:11:40.214129 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 78, length 64 21:11:41.214279 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 79, length 64 21:11:42.214275 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 80, length 64 21:11:43.214430 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 81, length 64 21:11:44.214727 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 82, length 64 21:11:45.216510 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 83, length 64 21:11:46.216987 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 84, length 64 21:11:47.216764 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 85, length 64 21:11:48.217472 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 86, length 64 21:11:49.217079 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 87, length 64 21:11:50.216659 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 88, length 64 21:11:51.217251 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 89, length 64 21:11:52.217264 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 90, length 64 21:11:53.217378 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 91, length 64 21:11:54.216939 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 92, length 64 21:11:55.216957 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 93, length 64 21:11:56.217391 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 94, length 64 21:11:57.217054 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 95, length 64 21:11:58.217050 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 96, length 64 ^C 33 packets captured 33 packets received by filter 0 packets dropped by kernel [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL Chain INPUT (policy DROP 1 packets, 76 bytes) pkts bytes target prot opt in out source destination 56892 7571K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 217 18228 ACCEPT icmp -- * * 0.0.0.0/0 172.200.1.101 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 227 packets, 19024 bytes) pkts bytes target prot opt in out source destination 55870 9021K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -A OUTPUT -s 172.200.1.101 -p icmp -j ACCEPT [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL Chain INPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 58615 7791K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 299 25116 ACCEPT icmp -- * * 0.0.0.0/0 172.200.1.101 Chain FORWARD (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 57536 9242K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 10 840 ACCEPT icmp -- * * 172.200.1.101 0.0.0.0/0 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# tcpdump -i bond0 -nn icmp tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on bond0, link-type EN10MB (Ethernet), capture size 262144 bytes 21:17:05.259185 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 403, length 64 21:17:05.259210 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 403, length 64 21:17:06.260314 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 404, length 64 21:17:06.260345 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 404, length 64 21:17:07.260832 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 405, length 64 21:17:07.260875 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 405, length 64 21:17:08.262111 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 406, length 64 21:17:08.262252 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 406, length 64 21:17:09.263647 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 407, length 64 21:17:09.263677 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 407, length 64 21:17:10.263923 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 408, length 64 21:17:10.263943 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 408, length 64 21:17:11.264841 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 409, length 64 21:17:11.264881 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 409, length 64 21:17:12.265289 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 410, length 64 21:17:12.265311 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 410, length 64 21:17:13.265793 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 411, length 64 21:17:13.265813 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 411, length 64 21:17:14.266599 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 412, length 64 21:17:14.266624 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 412, length 64 21:17:15.266876 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 413, length 64 21:17:15.266898 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 413, length 64 21:17:16.268890 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 414, length 64 21:17:16.268924 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 414, length 64 21:17:17.270586 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 415, length 64 21:17:17.270618 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 415, length 64 21:17:18.271096 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 416, length 64 21:17:18.271132 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 416, length 64 21:17:19.271688 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 417, length 64 21:17:19.271722 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 417, length 64 21:17:20.271945 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 418, length 64 21:17:20.272018 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 418, length 64 21:17:21.272795 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 419, length 64 21:17:21.272827 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 419, length 64 21:17:22.272480 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 420, length 64 21:17:22.272512 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 420, length 64 21:17:23.272638 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 421, length 64 21:17:23.272672 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 421, length 64 21:17:24.273863 IP 172.200.1.102 > 172.200.1.101: ICMP echo request, id 5881, seq 422, length 64 21:17:24.273894 IP 172.200.1.101 > 172.200.1.102: ICMP echo reply, id 5881, seq 422, length 64 ^C 40 packets captured 40 packets received by filter 0 packets dropped by kernel [root@hdp101.yinzhengjie.org.cn ~]#
5>.设置默认策略

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy ACCEPT 6 packets, 472 bytes) num pkts bytes target prot opt in out source destination 1 8535 1169K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 6 packets, 472 bytes) num pkts bytes target prot opt in out source destination 1 3780 509K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -P INPUT DROP [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 9678 1315K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 4892 655K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy DROP 3 packets, 240 bytes) num pkts bytes target prot opt in out source destination 1 10556 1463K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 3 packets, 240 bytes) num pkts bytes target prot opt in out source destination 1 5770 804K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -P FORWARD DROP [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 10751 1487K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 5955 829K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]#

[root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy DROP 3 packets, 236 bytes) num pkts bytes target prot opt in out source destination 1 11517 1592K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 3 packets, 236 bytes) num pkts bytes target prot opt in out source destination 1 6720 934K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -P OUTPUT DROP [root@hdp101.yinzhengjie.org.cn ~]# [root@hdp101.yinzhengjie.org.cn ~]# iptables -vnL --line-numbers Chain INPUT (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 11833 1627K ACCEPT tcp -- * * 172.200.0.0/21 172.200.1.101 Chain FORWARD (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination Chain OUTPUT (policy DROP 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 7024 971K ACCEPT tcp -- * * 172.200.1.101 172.200.0.0/21 [root@hdp101.yinzhengjie.org.cn ~]#
6>.
7>.
五.
