Httpd服务入门知识-Httpd服务常见配置案例之基于用户账号实现访问控制
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
一.基于用户的访问控制概述
认证质询:
WWW-Authenticate:响应码为401,拒绝客户端请求,并说明要求客户端提供账号和密码
认证:
Authorization:客户端用户填入账号和密码后再次发送请求报文;认证通过时,则服务器发送响应的资源
认证方式两种: basic:
明文认证,不过可以配合https进行加密传输问题也不大。 digest:
消息摘要认证,兼容性差,有的浏览器可能不支持哟~
安全域:
需要用户认证后方能访问的路径;应该通过名称对其进行标识,以便于告知用户认证的原因
用户的账号和密码 虚拟账号:
仅用于访问某服务时用到的认证标识 存储:
文本文件,SQL数据库,ldap目录存储,nis等
二.基于basic认证配置实战案例
1>.创建测试数据
[root@node101.yinzhengjie.org.cn ~]# mkdir /var/www/html/admin [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# echo "/var/www/html/admin/index.html" > /var/www/html/admin/index.html [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ll /var/www/html/admin total 4 -rw-r--r-- 1 root root 31 Dec 9 06:11 index.html [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/admin/index.html /var/www/html/admin/index.html [root@node101.yinzhengjie.org.cn ~]#
2>.提供账号和密码存储(文本文件)
使用专用命令完成此类文件的创建及用户管理 htpasswd [options] /PATH/HTTPD_PASSWD_FILE username
常用选项: -c:
自动创建文件,仅应该在文件不存在时使用 -p:
明文密码 -d:
CRYPT格式加密,默认 -m:
md5格式加密 -s:
sha格式加密 -D:
删除指定用户
具体使用案例如下图所示。

[root@node101.yinzhengjie.org.cn ~]# htpasswd -c /etc/httpd/conf.d/httpdpasswd jason #创建第一个用户时需要使用"-c"选项创建的用户的同时会自动创建文件,若文件已经存在则清空文件所有内容重新写入咱们新创建的用户。 New password: Re-type new password: Adding password for user jason [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ll /etc/httpd/conf.d/httpdpasswd -rw-r--r-- 1 root root 44 Dec 9 06:15 /etc/httpd/conf.d/httpdpasswd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# date Mon Dec 9 06:15:33 CST 2019 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# htpasswd -s /etc/httpd/conf.d/httpdpasswd jay #创建第二个用户时千万别在使用"-c"选项哟,不过咱们可以使用-s指定加密算法为sha格式加密哟~ New password: Re-type new password: Adding password for user jay [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# chmod 600 /etc/httpd/conf.d/httpdpasswd #为了安全起见,可以将文件权限改小点。 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ll /etc/httpd/conf.d/httpdpasswd -rw------- 1 root root 82 Dec 9 06:20 /etc/httpd/conf.d/httpdpasswd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/httpdpasswd jason:$apr1$fnoHrDaP$Q0ZGtsOj9D4W3xHzIKm9E/ jay:{SHA}o78nbN18sxTgXokaJRMEYOxV5b8= [root@node101.yinzhengjie.org.cn ~]#

3>.修改httpd的配置文件
[root@node101.yinzhengjie.org.cn ~]# ll /var/www/html/admin/ total 4 -rw-r--r-- 1 root root 31 Dec 9 06:11 index.html [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/admin/index.html /var/www/html/admin/index.html [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/auth.conf <Directory "/var/www/html/admin"> AuthType Basic #指明验证方式 AuthName "Welecon to Login" #指定客户端验证时的提示信息 AuthUserFile "/etc/httpd//conf.d/httpdpasswd" #指定账号验证文件,一定要确认httpd运行用户是否对该文件有执行权限哟~ Require user jason #此处我们只写了允许jason用户访问,若果想要jay用户也可以访问则输入"Require user jason jay",如果允许帐号验证文件中所有用户登录访问则这里可以写"Require valid-user" </Directory> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -t Syntax OK [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl reload httpd [root@node101.yinzhengjie.org.cn ~]#
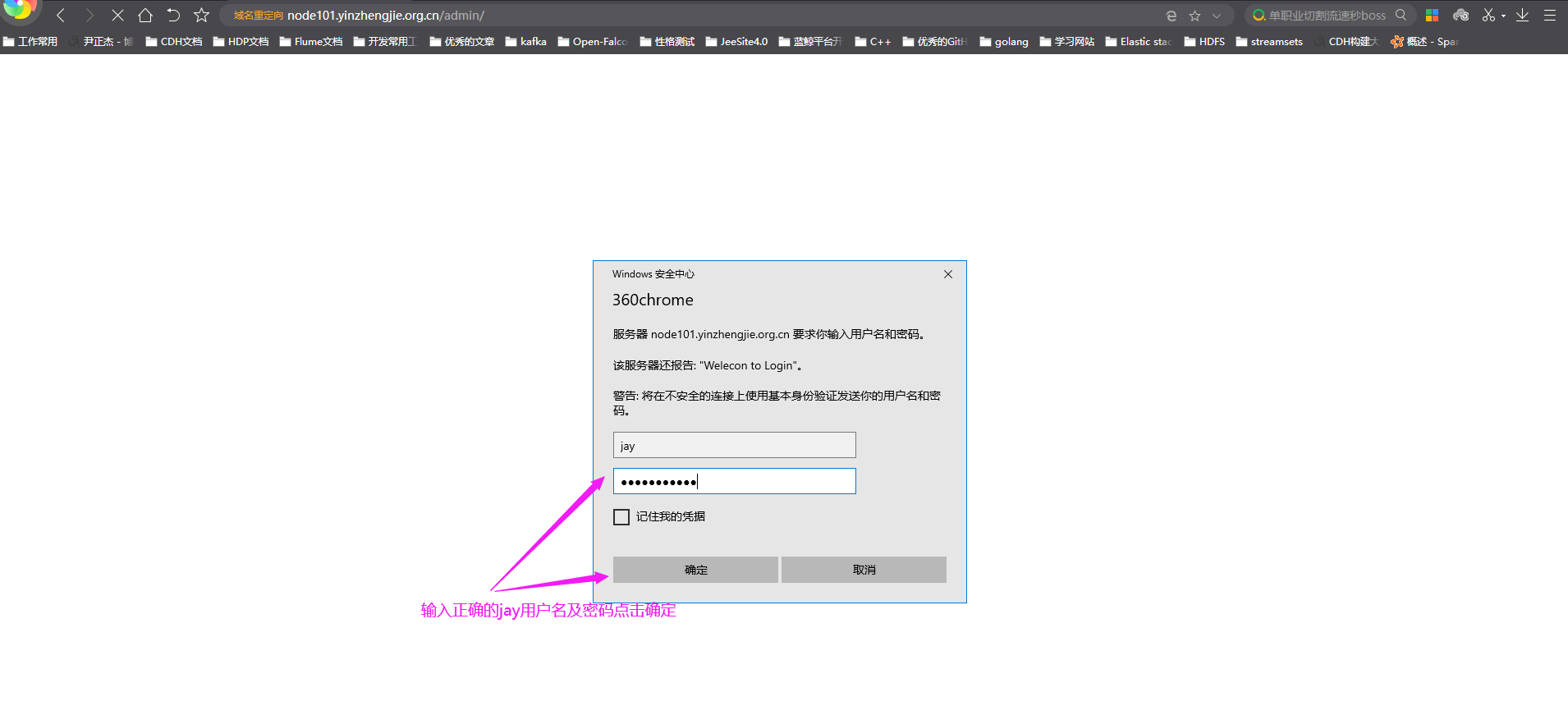
4>.浏览器访问页面并使用jason用户登录
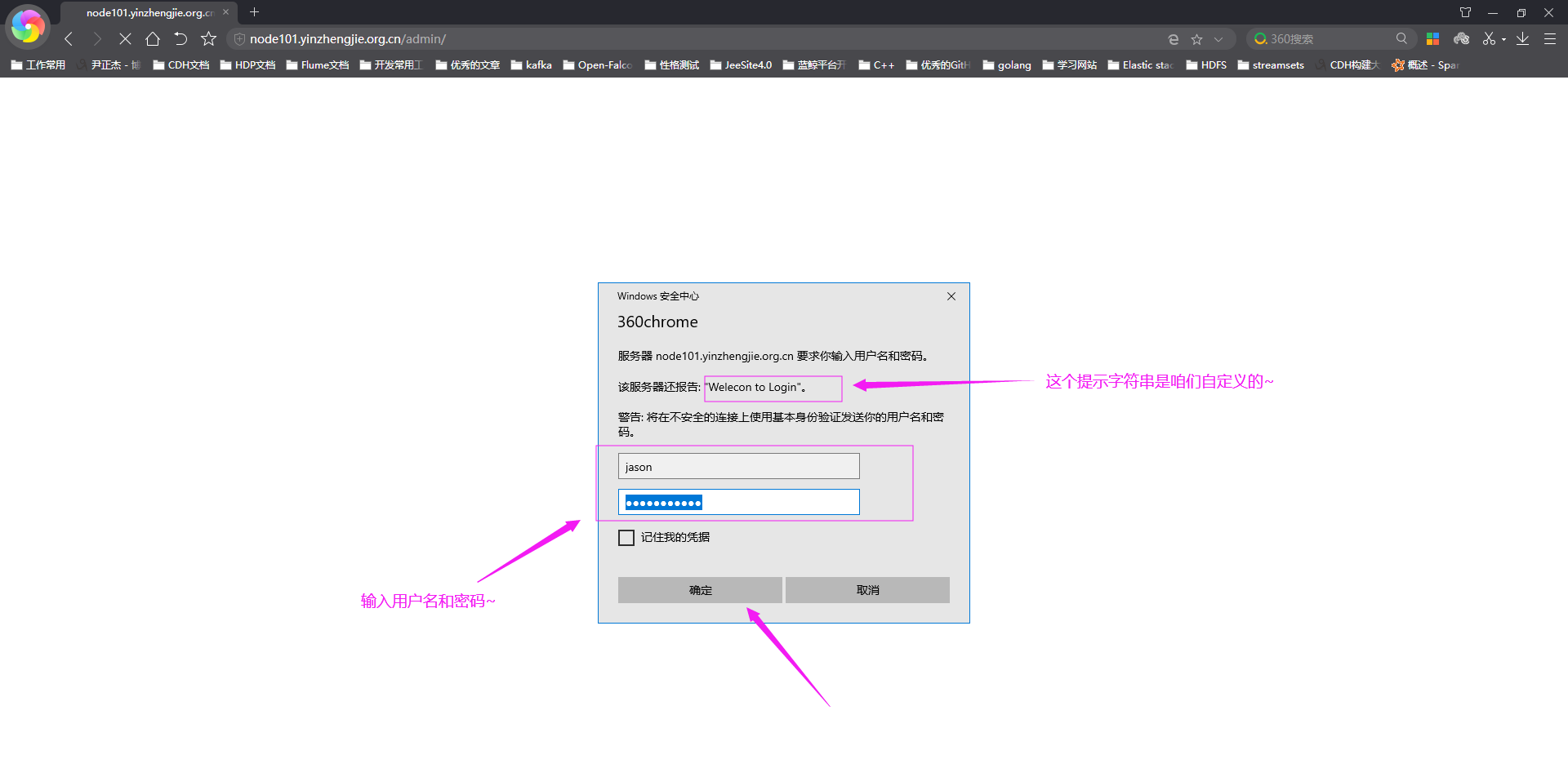
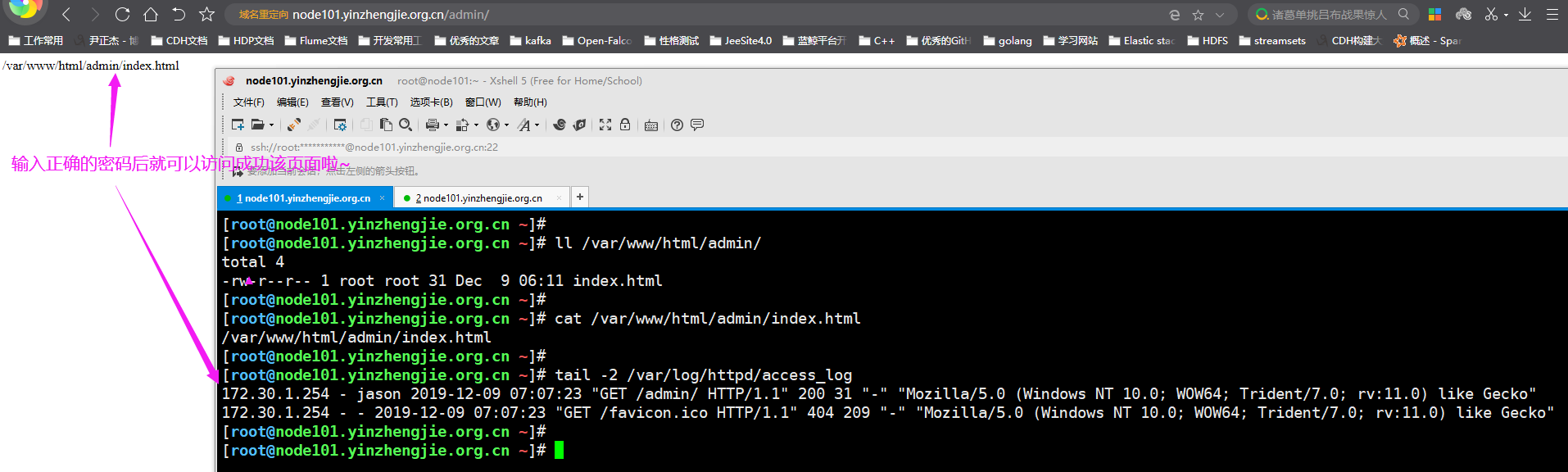
5>.用户名密码验证成功就可以访问成功啦~(如果不能访问的话,错误原因可以自行查看错误日志信息哟~)
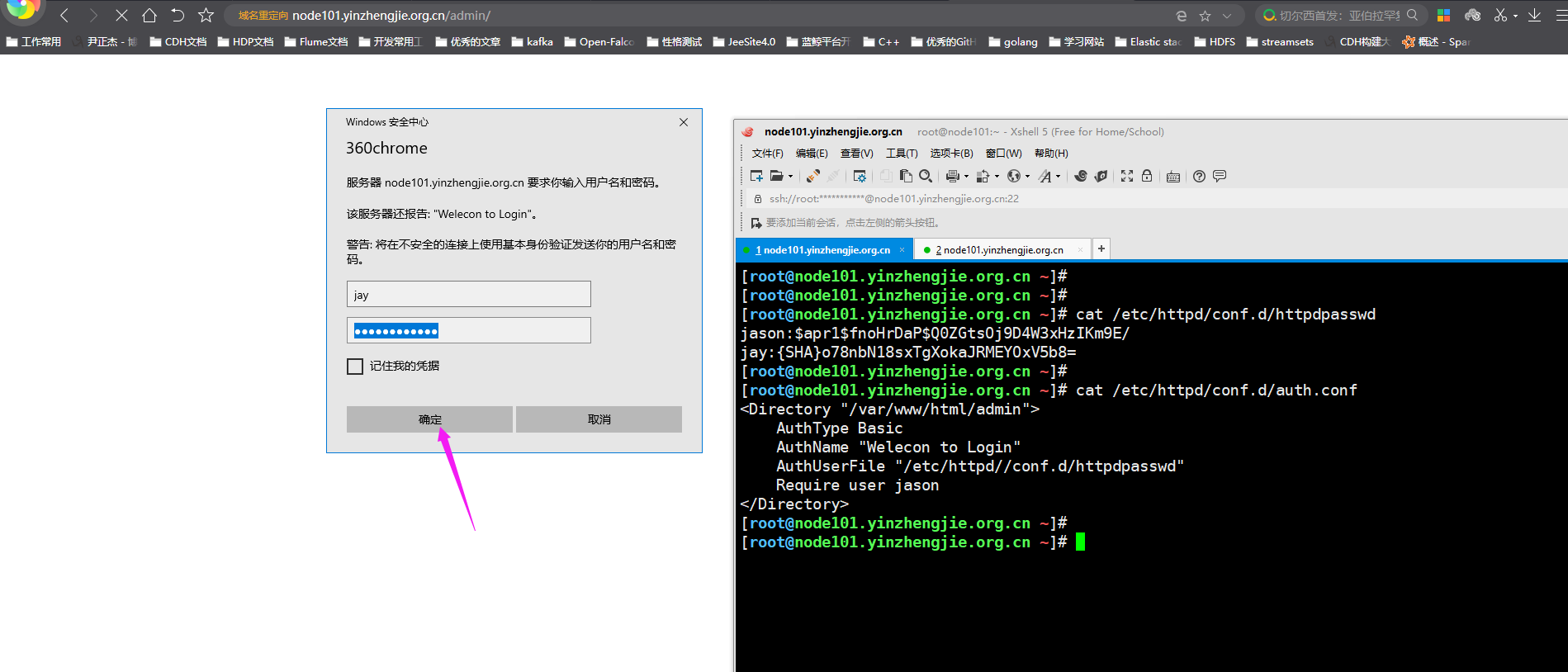
6>.使用jay用户访问并不会成功,因为咱们在httpd的配置文件中配置的是"Require user jason" 表示只允许jason用户访问
7>.在配置文件中定义一个".htaccess"隐藏文件
[root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/auth.conf <Directory "/var/www/html/admin"> AllowOverride AuthConfig #除了AuthConfig的其它指令都无法覆盖,即允许使用权限验证功能。 </Directory> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/admin/.htaccess #将之前的验证信息直接写在这里的隐藏文件即可 AuthType Basic AuthName "Welecon to Login" AuthUserFile "/etc/httpd//conf.d/httpdpasswd" Require user jason jay #此处我们允许jason和jay用户访问,若允许账号验证文件的所有用户均有权限访问可直接写"Require valid-user"即可。 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl reload httpd [root@node101.yinzhengjie.org.cn ~]#
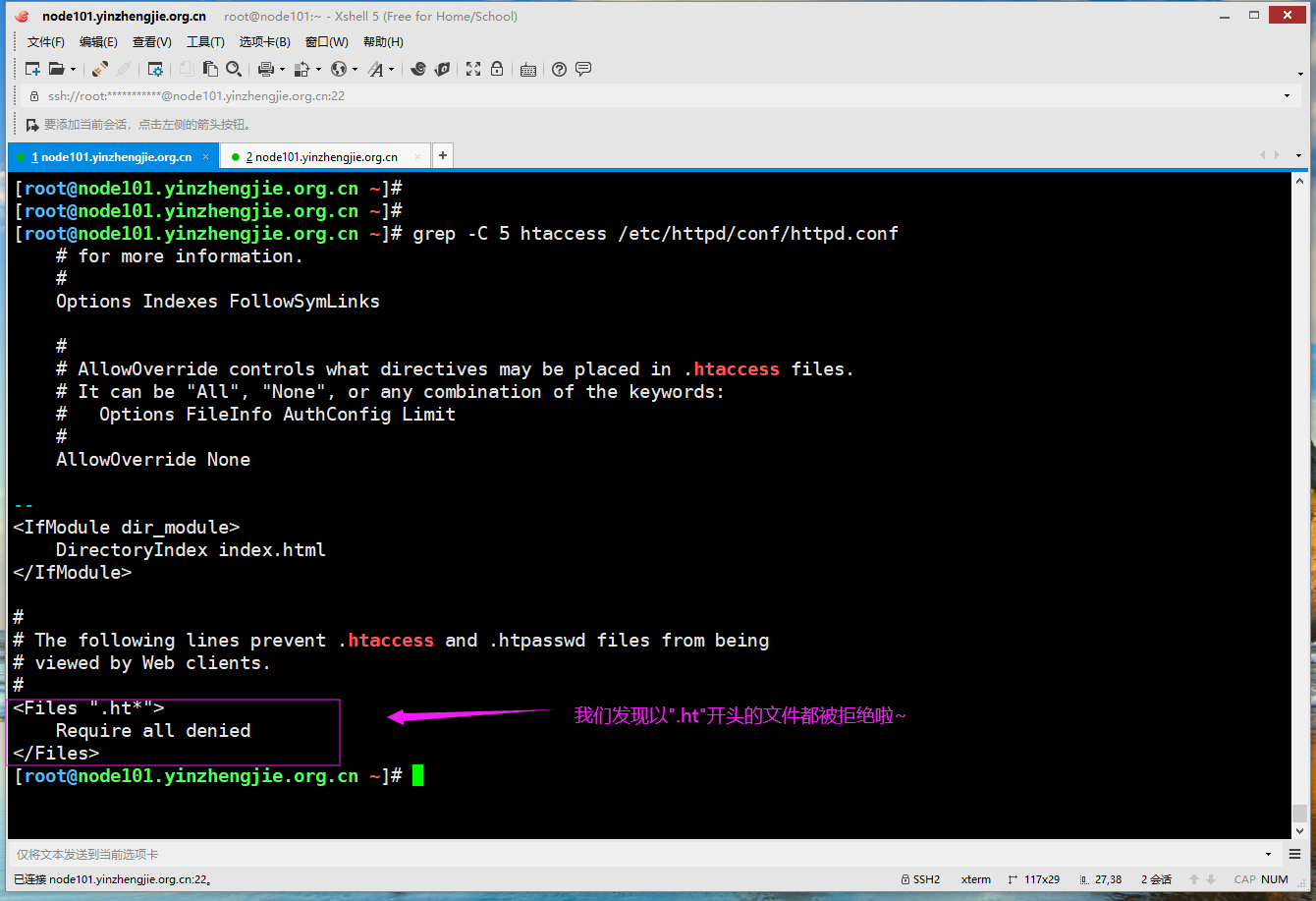
8>.为什么".htaccess"文件客户端看不到呢?(如下图所示,那是因为以".ht*"开头的文件都被拒绝啦~)

[root@node101.yinzhengjie.org.cn ~]# grep -C 5 htaccess /etc/httpd/conf/httpd.conf # for more information. # Options Indexes FollowSymLinks # # AllowOverride controls what directives may be placed in .htaccess files. # It can be "All", "None", or any combination of the keywords: # Options FileInfo AuthConfig Limit # AllowOverride None -- <IfModule dir_module> DirectoryIndex index.html </IfModule> # # The following lines prevent .htaccess and .htpasswd files from being # viewed by Web clients. # <Files ".ht*"> Require all denied </Files> [root@node101.yinzhengjie.org.cn ~]#
三.基于组账号进行认证实战案例
1>.创建用户账号和组账号文件
[root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/httpdpasswd jason:$apr1$fnoHrDaP$Q0ZGtsOj9D4W3xHzIKm9E/ jay:{SHA}o78nbN18sxTgXokaJRMEYOxV5b8= [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# htpasswd /etc/httpd/conf.d/httpdpasswd jerry New password: Re-type new password: Adding password for user jerry [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/httpdpasswd jason:$apr1$fnoHrDaP$Q0ZGtsOj9D4W3xHzIKm9E/ jay:{SHA}o78nbN18sxTgXokaJRMEYOxV5b8= jerry:$apr1$NC0Az6Ga$2ers2ZQZttbW.DPNrie.n0 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# vim /etc/httpd/conf.d/httpdgroup [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/httpdgroup #每一行定义一个组,组中的用户用空格分开 testgroup: jason jerry [root@node101.yinzhengjie.org.cn ~]#
2>.定义安全域
[root@node101.yinzhengjie.org.cn ~]# cat /etc/httpd/conf.d/auth.conf <Directory "/var/www/html/admin"> AllowOverride AuthConfig </Directory> [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# vim /var/www/html/admin/.htaccess [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# cat /var/www/html/admin/.htaccess AuthType Basic AuthName "Welecon to Login" AuthUserFile "/etc/httpd//conf.d/httpdpasswd" AuthGroupFile "/etc/httpd/conf.d/httpdgroup" Require group testgroup [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -t Syntax OK [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# systemctl reload httpd [root@node101.yinzhengjie.org.cn ~]#
3>.使用jerry用户访问
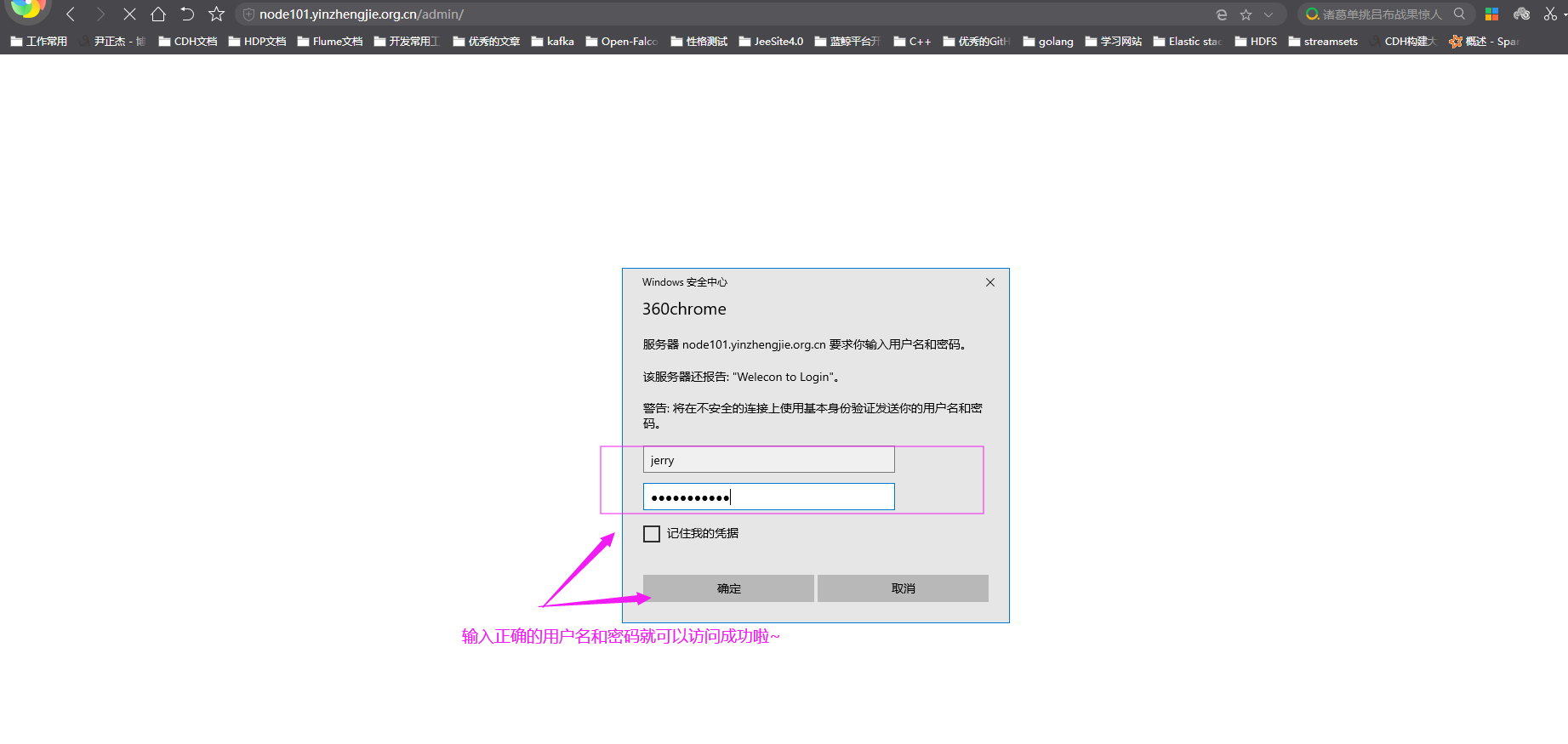
4>.jerry用户访问成功
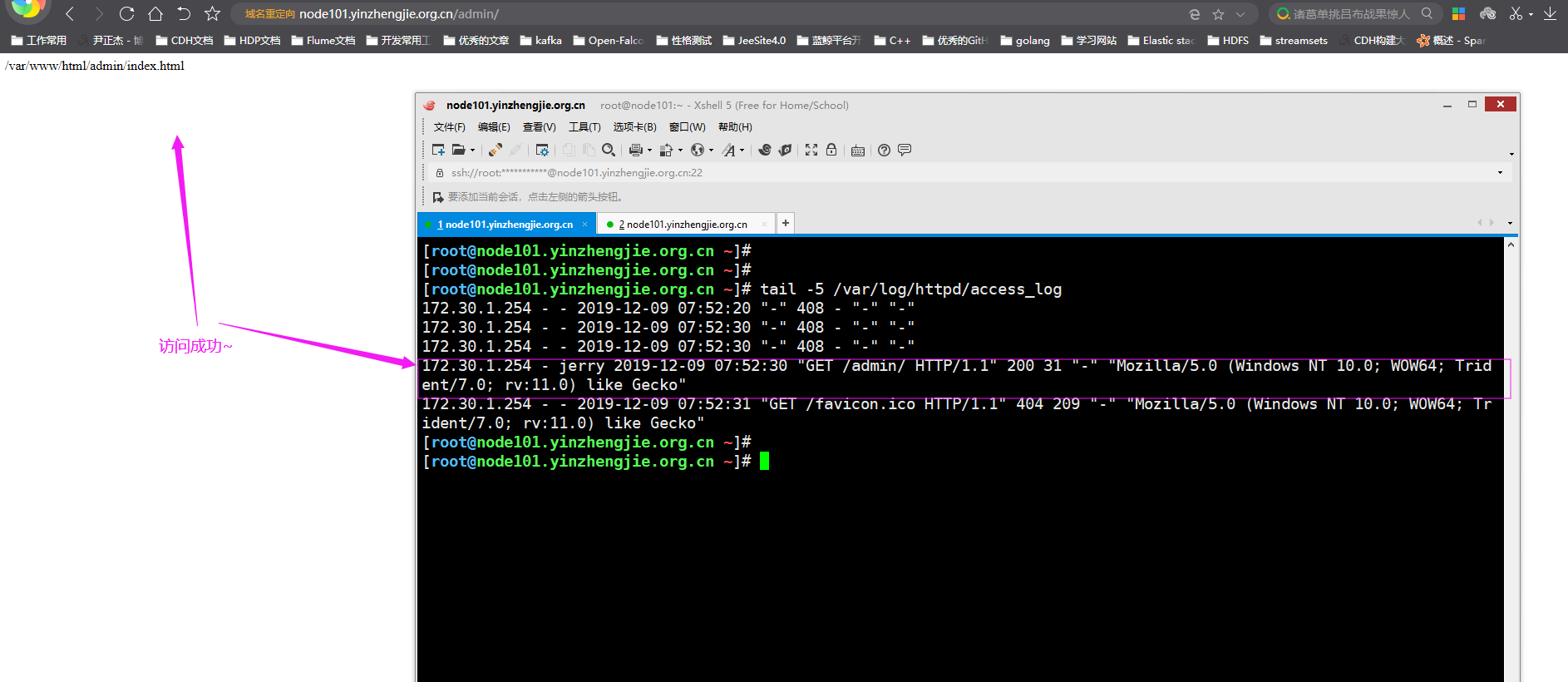
5>.远程客户端和用户验证的控制
Satisfy ALL|Any ALL: 客户机IP和用户验证都需要通过才可以 Any: 客户机IP和用户验证,有一个满足即可 示例: Require valid-user #这种写法是httpd2.2版本的写法,在httpd2.4推荐使用Require all granted Order allow,deny Allow from 192.168.1 Satisfy Any
四.认证时需要启动认证模块(默认是启动的)
1>.禁用基本认证模块
[root@node101.yinzhengjie.org.cn ~]# grep auth_basic_module /etc/httpd/conf.modules.d/00-base.conf #禁用基本的身份验证模块,只需要在前面添加"#"号注释即可。 #LoadModule auth_basic_module modules/mod_auth_basic.so [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -M | grep basic #若没有输出说明动态模块被咱们禁用了 [root@node101.yinzhengjie.org.cn ~]#
2>.禁用认证模块后用户将无法使用认证功能
[root@node101.yinzhengjie.org.cn ~]# tail -10f /var/log/httpd/error_log #错误日志出现如下的报错信息哟~
...... [Mon Dec 09 06:34:58.813900 2019] [authn_core:error] [pid 6337:tid 140393471530752] [client 172.30.1.254:62102] AH01796: AuthType Basic configured without corresponding module
[root@node101.yinzhengjie.org.cn ~]#

3>.启用基本认证模块
[root@node101.yinzhengjie.org.cn ~]# grep auth_basic_module /etc/httpd/conf.modules.d/00-base.conf #"auth_basic_module"是基本的身份验证的模块,默认是开启的。 LoadModule auth_basic_module modules/mod_auth_basic.so #加载模块的指令使用的是LoadModule,加载模块的名称为"auth_basic_module",该模块在磁盘上存放的位置是"modules/mod_auth_basic.so" [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ll /etc/httpd/modules/mod_auth_basic.so #根据上面指定的位置咱们的确可以找到该模块哟~ -rwxr-xr-x 1 root root 15424 Aug 8 19:42 /etc/httpd/modules/mod_auth_basic.so [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# httpd -M | grep basic #该动态模块已经被加载啦 auth_basic_module (shared) [root@node101.yinzhengjie.org.cn ~]#
五.客户端验证失败原因
1>.查看错误日志

[root@node101.yinzhengjie.org.cn ~]# tail /var/log/httpd/access_log 172.30.1.254 - - 2019-12-09 06:46:17 "-" 408 - "-" "-" 172.30.1.254 - jason 2019-12-09 06:47:20 "GET /admin/ HTTP/1.1" 500 527 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - - 2019-12-09 06:47:20 "GET /favicon.ico HTTP/1.1" 404 209 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - jason 2019-12-09 06:48:22 "GET /admin/ HTTP/1.1" 500 527 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - - 2019-12-09 06:48:28 "GET /admin/ HTTP/1.1" 401 381 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - jason 2019-12-09 06:48:34 "GET /admin/ HTTP/1.1" 500 527 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - - 2019-12-09 06:48:34 "GET /favicon.ico HTTP/1.1" 404 209 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - - 2019-12-09 06:50:14 "GET /admin/ HTTP/1.1" 401 381 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - jason 2019-12-09 06:50:18 "GET /admin/ HTTP/1.1" 500 527 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" 172.30.1.254 - - 2019-12-09 06:50:19 "GET /favicon.ico HTTP/1.1" 404 209 "-" "Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko" [root@node101.yinzhengjie.org.cn ~]#

[root@node101.yinzhengjie.org.cn ~]# tail /var/log/httpd/error_log [Mon Dec 09 06:34:58.813900 2019] [authn_core:error] [pid 6337:tid 140393471530752] [client 172.30.1.254:62102] AH01796: AuthType Basic configured without corresponding mod ule[Mon Dec 09 06:43:57.638316 2019] [authn_core:error] [pid 6350:tid 140393488316160] [client 172.30.1.254:62168] AH01796: AuthType Basic configured without corresponding mod ule[Mon Dec 09 06:44:08.559118 2019] [mpm_worker:notice] [pid 6335:tid 140393808160896] AH00297: SIGUSR1 received. Doing graceful restart [Mon Dec 09 06:44:08.567627 2019] [lbmethod_heartbeat:notice] [pid 6335:tid 140393808160896] AH02282: No slotmem from mod_heartmonitor [Mon Dec 09 06:44:08.567967 2019] [mpm_worker:notice] [pid 6335:tid 140393808160896] AH00292: Apache/2.4.6 (CentOS) configured -- resuming normal operations [Mon Dec 09 06:44:08.567977 2019] [core:notice] [pid 6335:tid 140393808160896] AH00094: Command line: '/usr/sbin/httpd -D FOREGROUND' [Mon Dec 09 06:47:20.795627 2019] [authn_file:error] [pid 6504:tid 140393454745344] (13)Permission denied: [client 172.30.1.254:61940] AH01620: Could not open password file : /etc/httpd/conf.d/httpdpasswd[Mon Dec 09 06:48:22.947555 2019] [authn_file:error] [pid 6506:tid 140393471530752] (13)Permission denied: [client 172.30.1.254:61957] AH01620: Could not open password file : /etc/httpd/conf.d/httpdpasswd[Mon Dec 09 06:48:34.561196 2019] [authn_file:error] [pid 6504:tid 140393446352640] (13)Permission denied: [client 172.30.1.254:62007] AH01620: Could not open password file : /etc/httpd/conf.d/httpdpasswd[Mon Dec 09 06:50:18.925494 2019] [authn_file:error] [pid 6505:tid 140393354032896] (13)Permission denied: [client 172.30.1.254:62082] AH01620: Could not open password file : /etc/httpd/conf.d/httpdpasswd[root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#
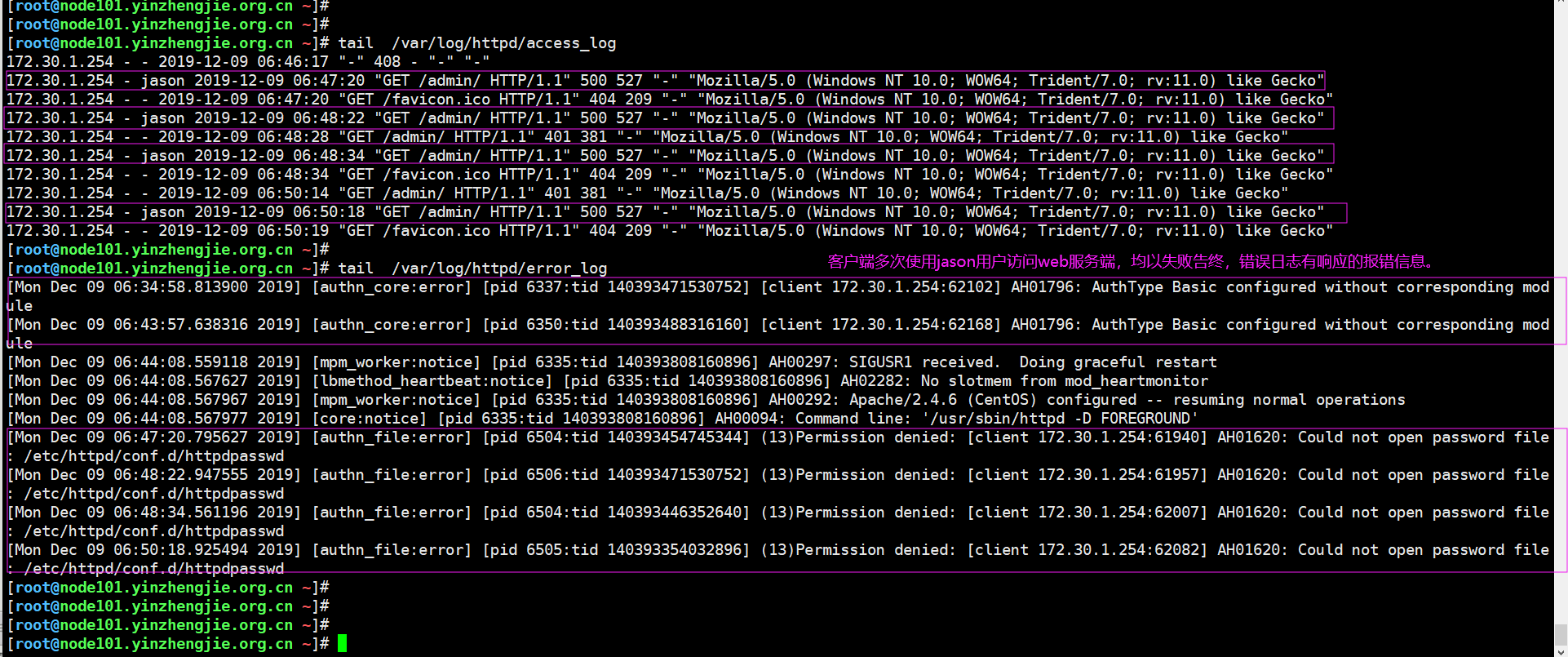
2>.错误原因分析
[root@node101.yinzhengjie.org.cn ~]# ll /etc/httpd/conf.d/httpdpasswd #错误原因可能会是客户端输入了错误密码,但是从上面的日志分析可以看出来应该是权限被拒绝,于是查看该文件发现果不其然,的确是没有权限访问的。 -rw------- 1 root root 82 Dec 9 06:20 /etc/httpd/conf.d/httpdpasswd [root@node101.yinzhengjie.org.cn ~]#
3>.解决方案
[root@node101.yinzhengjie.org.cn ~]# ll /etc/httpd/conf.d/httpdpasswd -rw------- 1 root root 82 Dec 9 06:20 /etc/httpd/conf.d/httpdpasswd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ps aux | grep httpd #需要查明httpd服务是被哪个用户启用的,不难发现是apache用户在运行httpd服务。 root 6335 0.0 0.0 224256 5244 ? Ss 06:34 0:00 /usr/sbin/httpd -DFOREGROUND apache 6503 0.0 0.0 224256 2908 ? S 06:44 0:00 /usr/sbin/httpd -DFOREGROUND apache 6504 0.0 0.0 642156 3952 ? Sl 06:44 0:00 /usr/sbin/httpd -DFOREGROUND apache 6505 0.0 0.0 707692 3688 ? Sl 06:44 0:00 /usr/sbin/httpd -DFOREGROUND apache 6506 0.0 0.0 773228 3692 ? Sl 06:44 0:00 /usr/sbin/httpd -DFOREGROUND apache 6589 0.0 0.0 707692 3692 ? Sl 06:44 0:00 /usr/sbin/httpd -DFOREGROUND root 6687 0.0 0.0 112708 988 pts/0 S+ 06:59 0:00 grep --color=auto httpd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# setfacl -m u:apache:r /etc/httpd/conf.d/httpdpasswd #于是我们需要为httpd服务添加ACL权限 [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# ll /etc/httpd/conf.d/httpdpasswd -rw-r-----+ 1 root root 82 Dec 9 06:20 /etc/httpd/conf.d/httpdpasswd [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]# getfacl /etc/httpd/conf.d/httpdpasswd #再次确认一下httpd的验证文件是否有权限哟~确认有访问权限后再使用浏览器访问就可以成功啦,如下图所示。 getfacl: Removing leading '/' from absolute path names # file: etc/httpd/conf.d/httpdpasswd # owner: root # group: root user::rw- user:apache:r-- group::--- mask::r-- other::--- [root@node101.yinzhengjie.org.cn ~]# [root@node101.yinzhengjie.org.cn ~]#