前言
本文介绍istio的安装及使用
dashboard,grafana,prometheus,kiali,jaeger的配置示例.演示通过istio的ingressgateway统一访问入口
Istio简介
下载istio
https://github.com/istio/istio/releases wget https://github.com/istio/istio/releases/download/1.2.2/istio-1.2.2-linux.tar.gz tar xf istio-1.2.2-linux.tar.gz cd /root/istio-1.2.2 cp bin/istioctl /usr/local/bin/
Chart Details
This chart can install multiple Istio components as subcharts: ingressgateway egressgateway sidecarInjectorWebhook galley mixer pilot security(citadel) grafana prometheus tracing(jaeger) kiali To enable or disable each component, change the corresponding enabled flag.
Istio安装
使用helm部署istio服务
安装包内的 Helm 目录中包含了 Istio 的 Chart,官方提供了两种方法:
- 用 Helm 生成
istio.yaml,然后自行安装。 - 用
Tiller直接安装
这里采用第一种方法,通过helm template生成模板文件安装
注意:最新版本有2部分配置分开的,和之前版本有区别,所有要分别生成配置文件 生成Istio的CRDs helm template --name istio-init --namespace istio-system ./install/kubernetes/istio-init > istio-init-1.2.2.yaml 生成istio配置文件 helm template --name istio --namespace istio-system ./install/kubernetes/helm/istio > istio-1.2.2.yaml
以上使用默认配置,有些组件默认是不开启的
vim install/kubernetes/helm/istio/values.yaml
可以手动修改配置文件 修改helm chart默认参数,在生成模板
也可以在命令行添加 --set key=value 覆盖默认值
查看默认参数配置:https://istio.io/docs/reference/config/installation-options/#kiali-options
如下:在命令行直接覆盖默认值:
helm template install/kubernetes/helm/istio --name istio --namespace istio-system --set sidecarInjectorWebhook.enabled=true --set ingress.service.type=NodePort --set gateways.istio-ingressgateway.type=NodePort --set gateways.istio-egressgateway.type=NodePort --set tracing.enabled=true --set servicegraph.enabled=true --set prometheus.enabled=true --set tracing.jaeger.enabled=true --set grafana.enabled=true > istio.yaml
[root@k8s-master istio-1.2.2]# kubectl apply -f istio-init-1.2.2.yaml configmap/istio-crd-10 created configmap/istio-crd-11 created configmap/istio-crd-12 created serviceaccount/istio-init-service-account created clusterrole.rbac.authorization.k8s.io/istio-init-istio-system unchanged clusterrolebinding.rbac.authorization.k8s.io/istio-init-admin-role-binding-istio-system unchanged job.batch/istio-init-crd-10 created job.batch/istio-init-crd-11 created job.batch/istio-init-crd-12 created [root@k8s-master istio-1.2.2]# kubectl apply -f istio-1.2.2.yaml ### [root@k8s-master istio-1.2.2]# kubectl get pods -n istio-system NAME READY STATUS RESTARTS AGE grafana-6575997f54-2lppn 1/1 Running 0 55m istio-citadel-894d98c85-644wd 1/1 Running 0 55m istio-cleanup-secrets-1.2.2-g8568 0/1 Completed 0 55m istio-galley-5b984f89b-l5prq 1/1 Running 2 55m istio-grafana-post-install-1.2.2-xcgtb 0/1 Completed 0 55m istio-ingressgateway-6599d6749-5v9xx 0/1 Running 0 55m istio-init-crd-10-dfjr2 0/1 Completed 0 59m istio-init-crd-11-z28bv 0/1 Completed 0 59m istio-init-crd-12-b9hmw 0/1 Completed 0 59m istio-pilot-7ccff5dbdc-lhvhm 0/2 Pending 0 55m istio-policy-77bbfdbd6-rfgsz 2/2 Running 8 55m istio-security-post-install-1.2.2-tlv6m 0/1 Completed 0 55m istio-sidecar-injector-7b98dd6bcc-kn7z9 1/1 Running 0 55m istio-telemetry-7f8d5c5b74-glft4 2/2 Running 8 55m istio-tracing-555cf644d-g7hsn 1/1 Running 0 55m kiali-6cd6f9dfb5-trzqx 1/1 Running 0 55m prometheus-7d7b9f7844-m7ffd 1/1 Running 0 55m [root@k8s-master istio-1.2.2]# #使用下面命令验证是否有23个istio crds [root@k8s-master istio-1.2.2]# kubectl get crds | grep 'istio.io|certmanager.k8s.io' | wc -l 23 [root@k8s-master istio-1.2.2]#
Istio使用
gateway和virtualserive配置

[root@k8s-master ~]# cat gateway-istio.yaml apiVersion: networking.istio.io/v1alpha3 kind: Gateway metadata: name: gateway-istio namespace: istio-system spec: selector: istio: ingressgateway # use istio default controller servers: - port: number: 80 name: http-istio protocol: HTTP hosts: - "prometheus.test.com" - "kiali.test.com" - "jaeger.test.com" - "dashboard.test.com" - "grafana.test.com" --- apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: jaeger namespace: istio-system spec: hosts: - "jaeger.test.com" gateways: - gateway-istio http: - retries: attempts: 3 perTryTimeout: 2s route: - destination: host: tracing port: number: 80 --- apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: prometheus namespace: istio-system spec: hosts: - "prometheus.test.com" gateways: - gateway-istio http: - retries: attempts: 3 perTryTimeout: 2s route: - destination: host: prometheus port: number: 9090 --- apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: grafana namespace: istio-system spec: hosts: - "grafana.test.com" gateways: - gateway-istio http: - retries: attempts: 3 perTryTimeout: 2s route: - destination: host: grafana port: number: 3000 --- apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: kiali namespace: istio-system spec: hosts: - "kiali.test.com" gateways: - gateway-istio http: - retries: attempts: 3 perTryTimeout: 2s route: - destination: host: kiali port: number: 20001 [root@k8s-master ~]#
使用haproxy代理本机80,443端口到k8s集群istio ingressgateway的31380(http)和31390(https)
haproxy配置请看:https://www.cnblogs.com/xuliang666/p/11136829.html
配置域名如下
(base) xuliang@xuliang-PC:~$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 xuliang-PC # The following lines are desirable for IPv6 capable hosts ::1 ip6-localhost ip6-loopback fe00::0 ip6-localnet ff00::0 ip6-mcastprefix ff02::1 ip6-allnodes ff02::2 ip6-allrouters 10.0.2.51 red.aijiatui.com 192.168.100.29 myapp.test.com 192.168.100.29 prometheus.test.com 192.168.100.29 grafana.test.com 192.168.100.29 kiali.test.com 192.168.100.29 jaeger.test.com (base) xuliang@xuliang-PC:~$
dashboard配置
查看dashboard svc
[root@k8s-master ~]# kubectl get svc -n kube-system|grep dashboard kubernetes-dashboard ClusterIP 10.106.65.78 <none> 9090/TCP 27d [root@k8s-master ~]#
创建gateway和virtualservice

#gateway网关配置: apiVersion: networking.istio.io/v1alpha3 kind: Gateway metadata: name: gateway-dashboard namespace: kube-system spec: selector: istio: ingressgateway # use istio default controller servers: - port: number: 80 name: http-dashboard protocol: HTTP hosts: - "dashboard.test.com" --- apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: dashboard namespace: kube-system spec: hosts: - "dashboard.test.com" gateways: - gateway-dashboard http: - retries: attempts: 3 perTryTimeout: 2s route: - destination: host: kubernetes-dashboard port: number: 9090
在浏览器中输入dashboard.test.com即可访问
jaeger介绍
官网地址:https://www.jaegertracing.io/
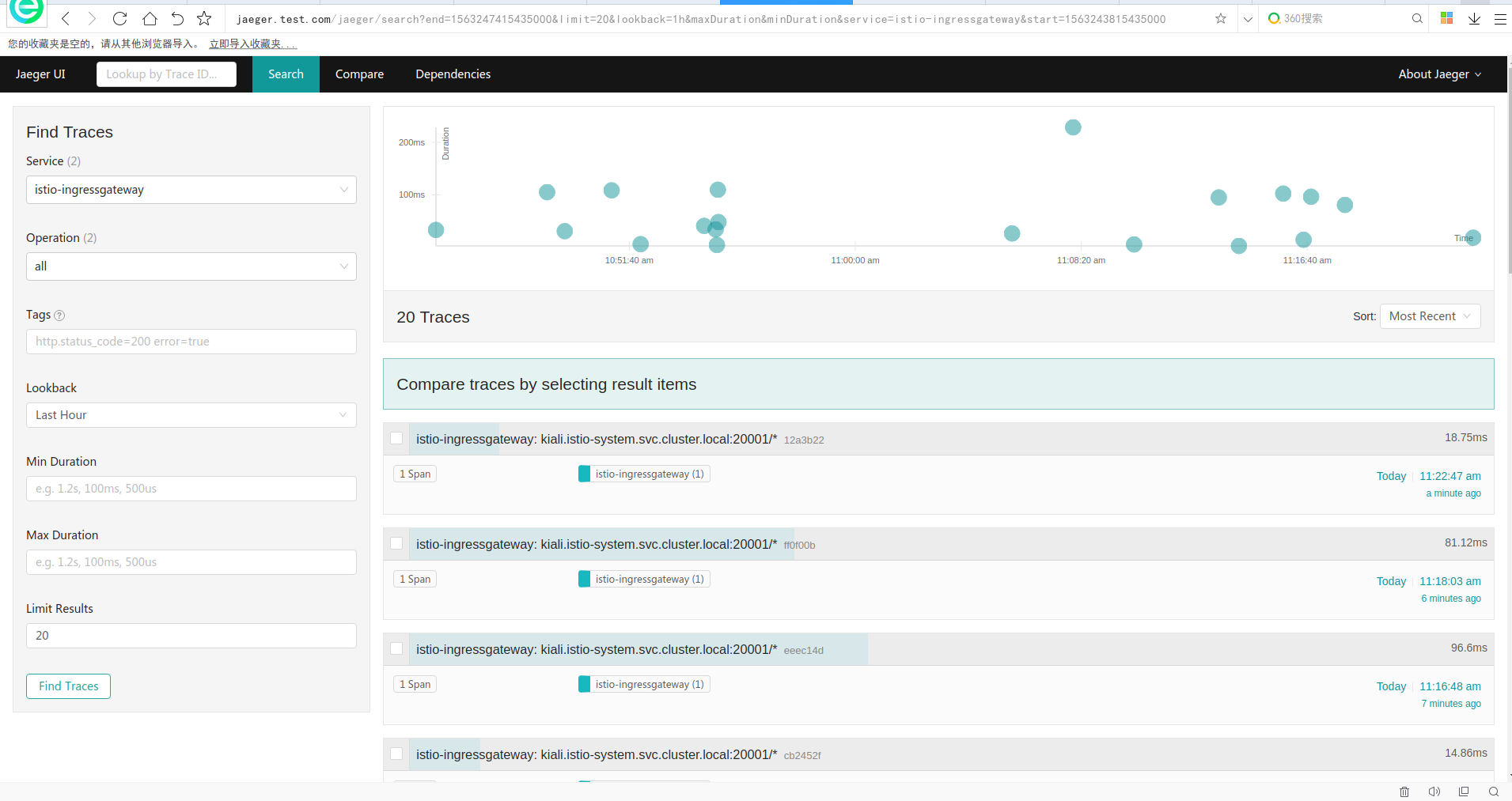
Jaeger受Dapper和OpenZipkin的启发,是Uber Technologies公开发布的分布式跟踪系统。它用于监视和排除基于微服务的分布式系统,包括:
- 分布式上下文传播
- 分布式事务监控
- 根本原因分析
- 服务依赖性分析
- 性能/延迟优化
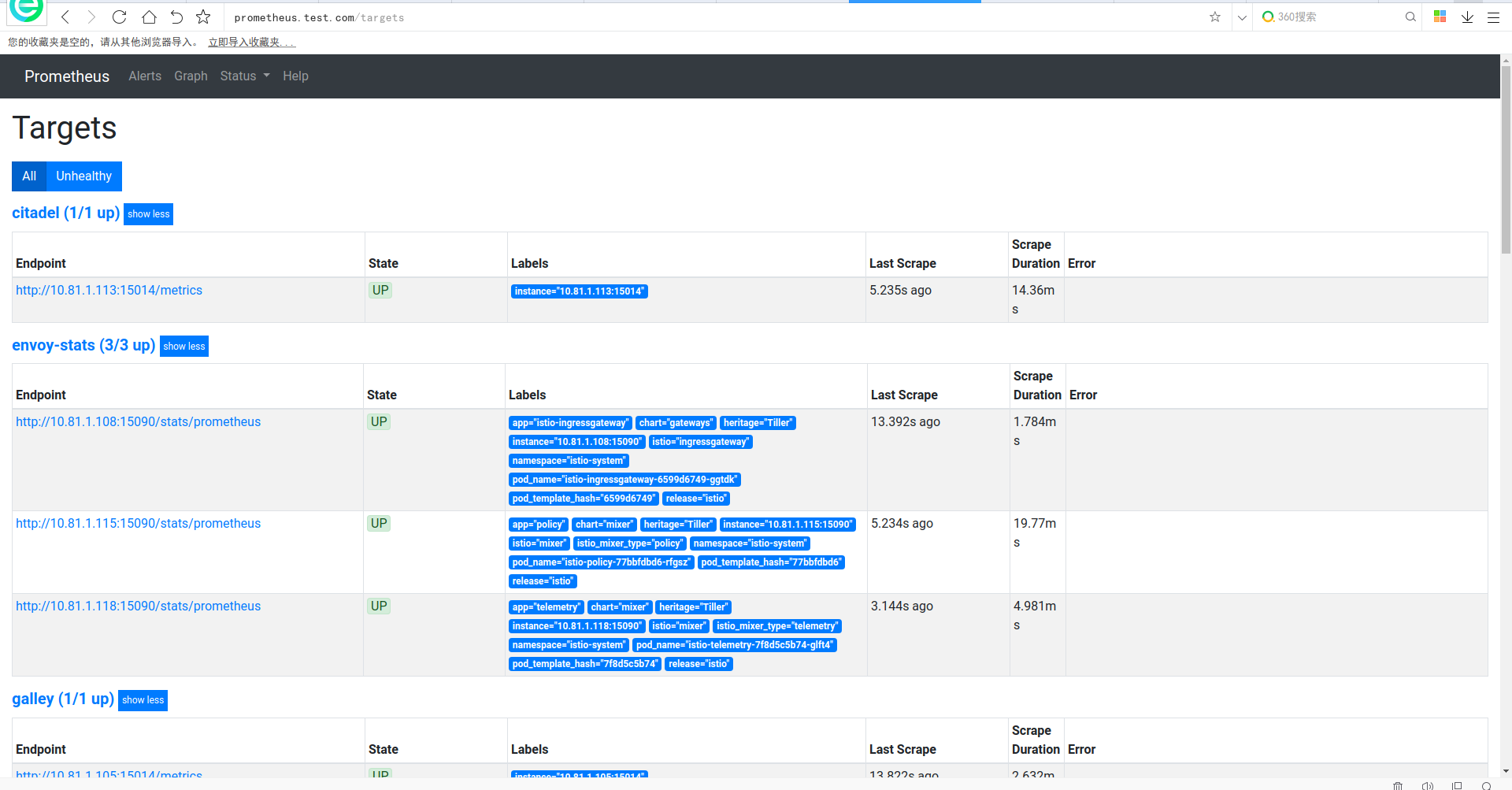
访问地址如下:
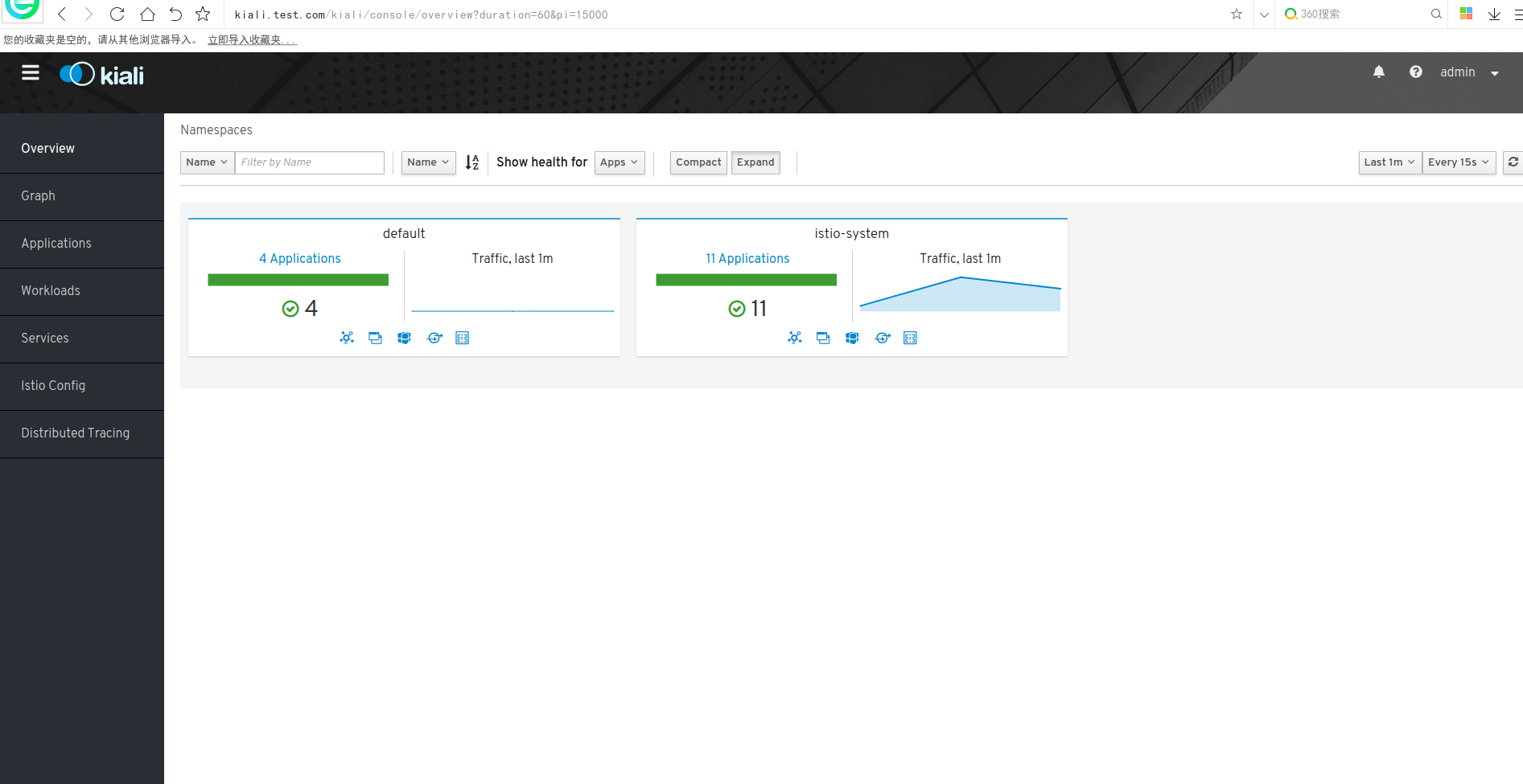
kiali介绍
服务网格可观察性和配置
通过helm模板安装完,是没有账户密码的
helm template
--set kiali.enabled=true
--set "kiali.dashboard.jaegerURL=http://$(kubectl get svc tracing --namespace istio-system -o jsonpath='{.spec.clusterIP}'):80"
--set "kiali.dashboard.grafanaURL=http://$(kubectl get svc grafana --namespace istio-system -o jsonpath='{.spec.clusterIP}'):3000"
install/kubernetes/helm/istio
--name istio --namespace istio-system > istio.yaml
[root@k8s-master ~]# echo -n 'admin' | base64
YWRtaW4=
[root@k8s-master ~]# echo -n 'admin' | base64
YWRtaW4=
[root@k8s-master ~]#
[root@k8s-master ~]# cat kiali.yaml
apiVersion: v1
kind: Secret
metadata:
name: kiali
namespace: istio-system
labels:
app: kiali
type: Opaque
data:
username: YWRtaW4K=
passphrase: YWRtaW4K
[root@k8s-master ~]#
或者
USERNAME=$(echo -n 'admin' | base64) PASSPHRASE=$(echo -n 'admin' | base64) cat <<EOF | kubectl apply -f - apiVersion: v1 kind: Secret metadata: name: kiali namespace: $NAMESPACE labels: app: kiali type: Opaque data: username: $USERNAME passphrase: $PASSPHRASE EOF
查看或修改kiali的配置文件
[root@k8s-master istio-1.2.2]# kubectl get configmap kiali -n istio-system -o yaml
apiVersion: v1
data:
config.yaml: |
istio_namespace: istio-system
auth:
strategy: "login"
server:
port: 20001
web_root: /kiali
external_services:
tracing:
url: http://jaeger.test.com/jaeger
grafana:
url: http://10.100.148.230:3000
prometheus:
url: http://10.109.28.54:9090
kind: ConfigMap
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","data":{"config.yaml":"istio_namespace: istio-system
auth:
strategy: "login"
server:
port: 20001
web_root: /kiali
external_services:
tracing:
url: http://10.100.190.53
grafana:
url: http://10.100.148.230:3000
prometheus:
url: http://10.109.28.54:9090
"},"kind":"ConfigMap","metadata":{"annotations":{},"labels":{"app":"kiali","chart":"kiali","heritage":"Tiller","release":"istio"},"name":"kiali","namespace":"istio-system"}}
creationTimestamp: "2019-07-12T06:40:16Z"
labels:
app: kiali
chart: kiali
heritage: Tiller
release: istio
name: kiali
namespace: istio-system
resourceVersion: "1386411"
selfLink: /api/v1/namespaces/istio-system/configmaps/kiali
uid: f2100d5c-05b4-48ca-92c7-73ebea15401e
[root@k8s-master istio-1.2.2]#
注意:
external_services:
tracing:
url: http://10.100.190.53:80
grafana:
url: http://10.100.148.230:3000
prometheus:
url: http://10.109.28.54:9090
这里的三个地址可以写svc ip也可以写成域名
账户:admin 密码:admin
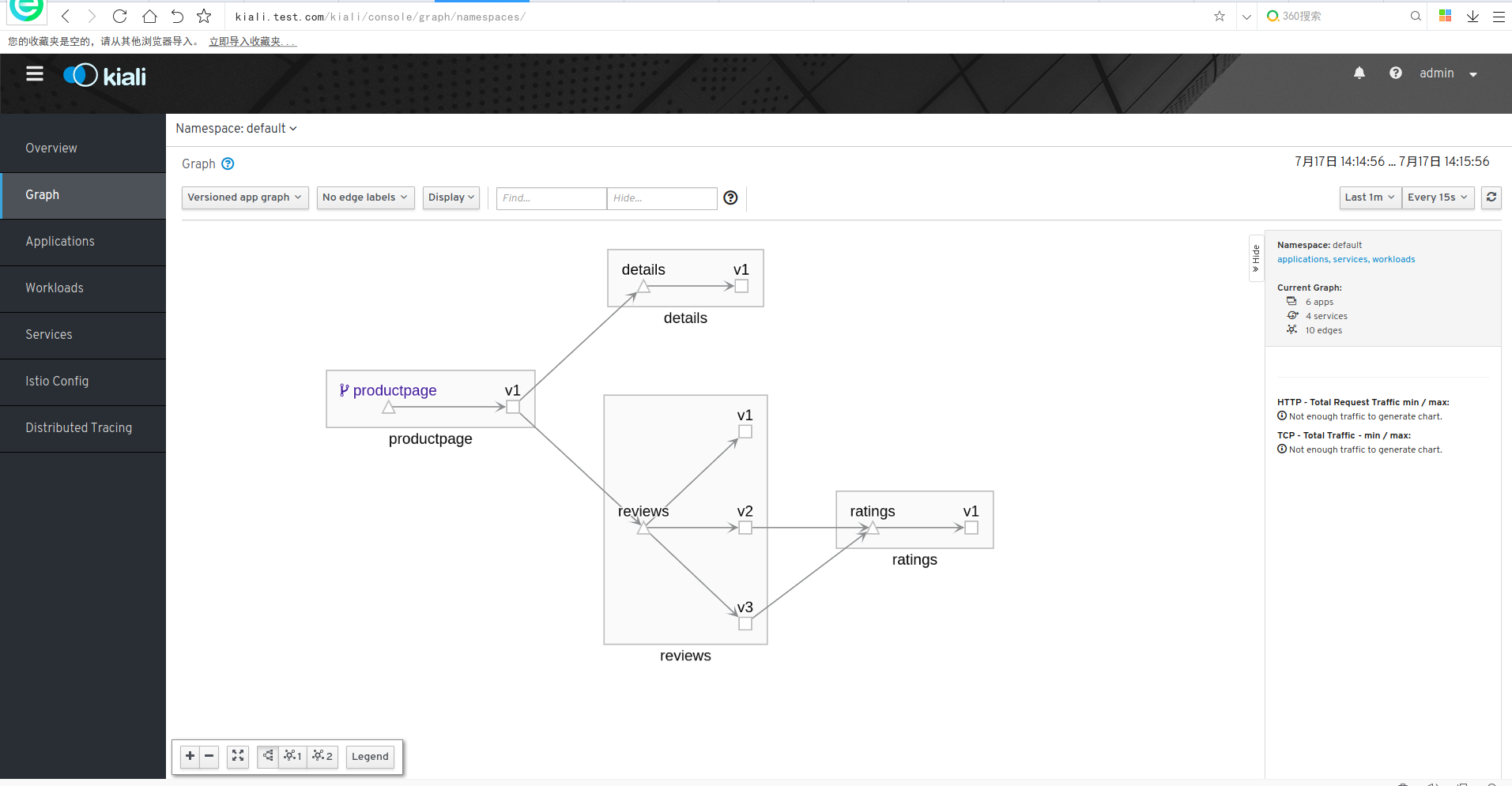
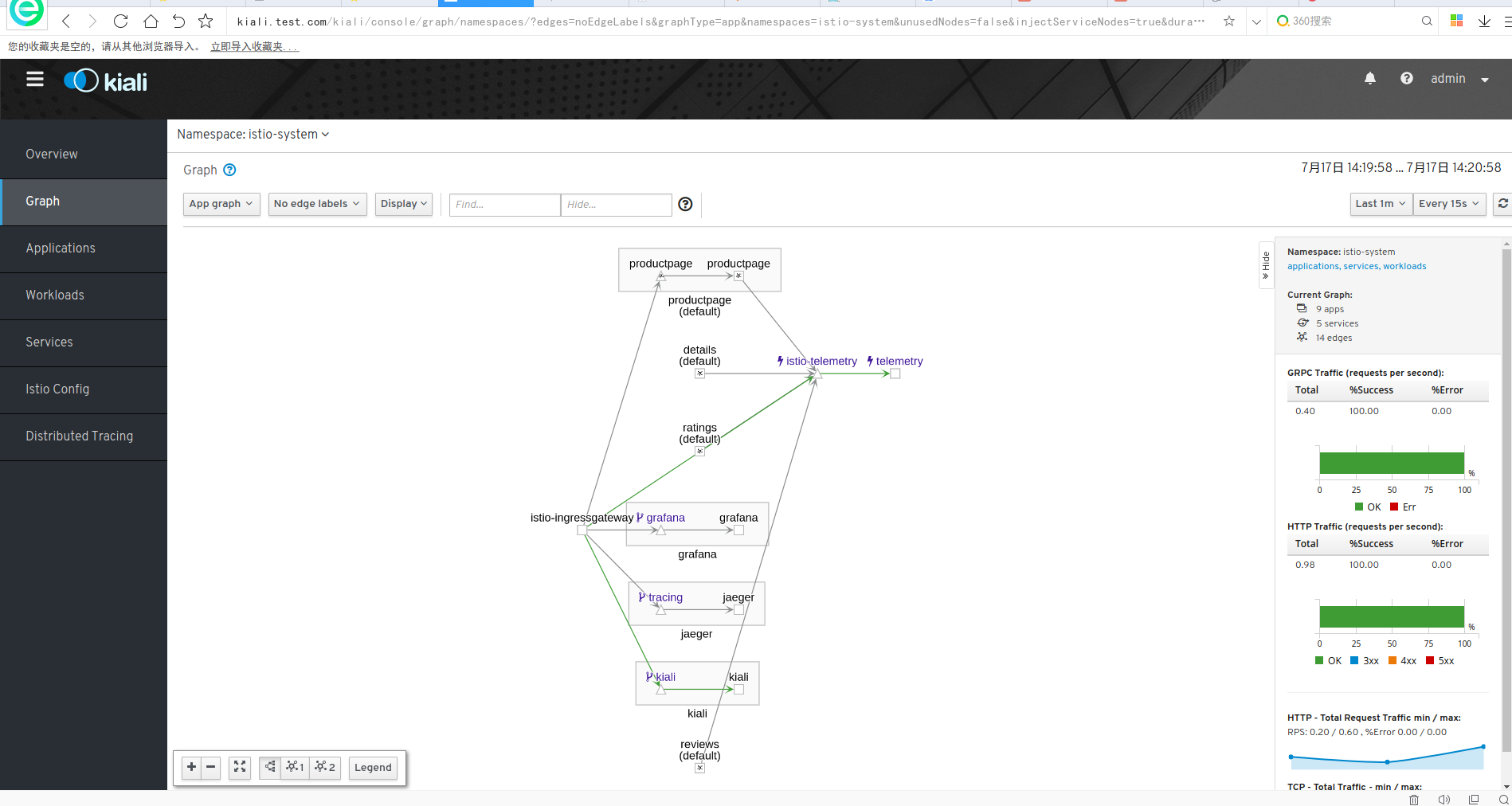
grafana
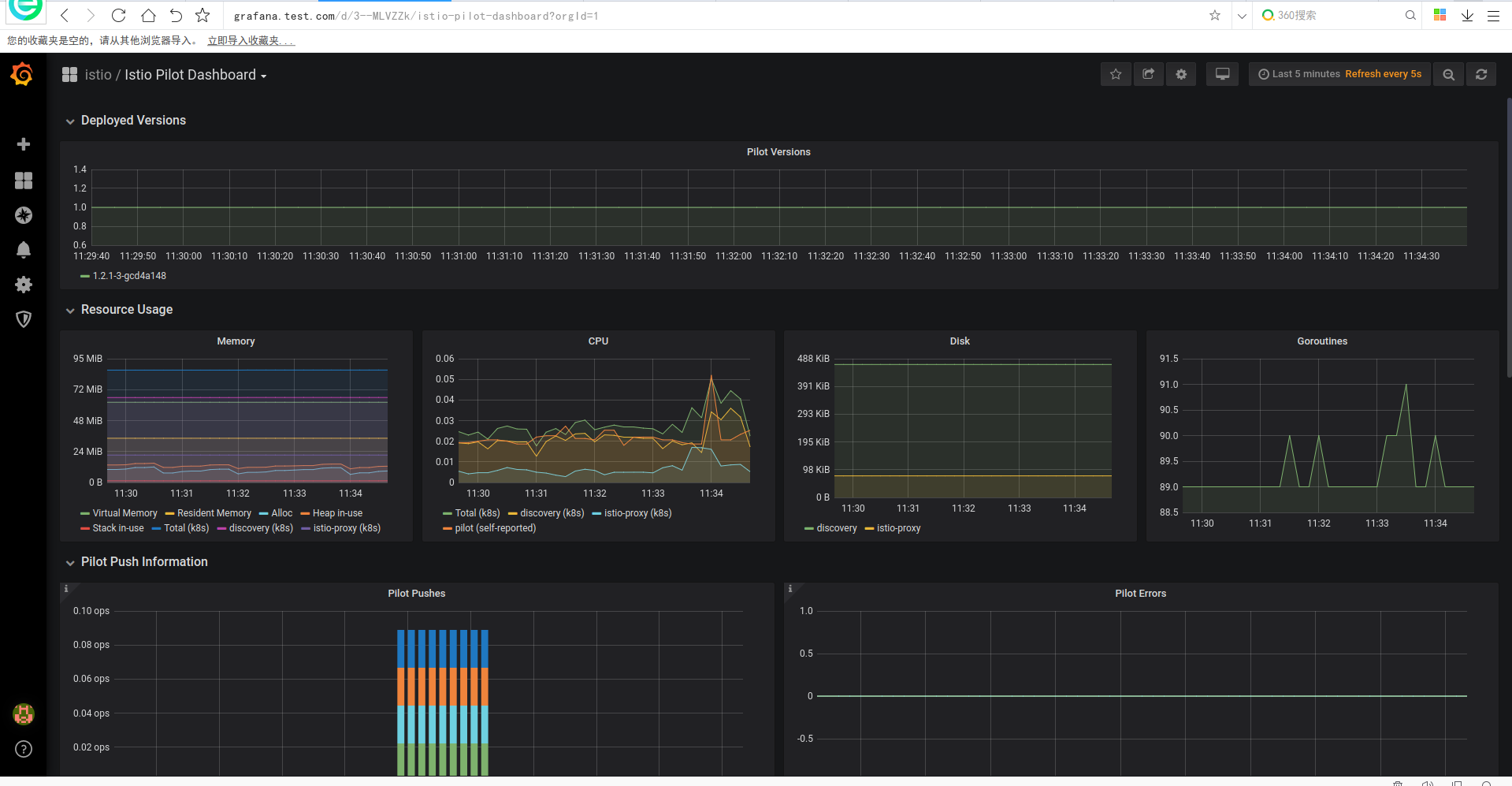
prometheus