文/玄魂

目录
Kali Linux Web 渗透测试— 第十二课-websploit............................................... 1
Websploit 简介........................................................................................... 2
主要功能....................................................................................................... 2
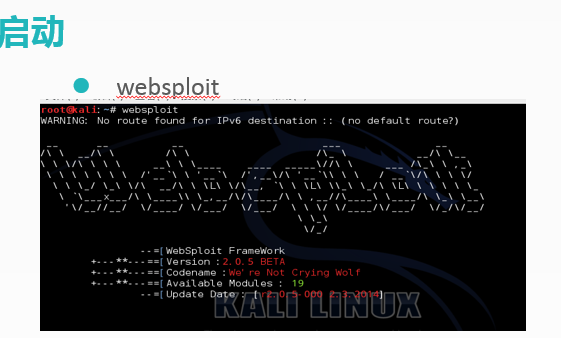
启动............................................................................................................... 3
show modules................................................................................................ 4
基本使用流程............................................................................................... 4
demo1-web/pma 模块使用......................................................................... 5
demo2-exploit/java applet 示例.................................................................. 5
demo-3 network/ mitm................................................................................. 5
教程地址:http://edu.51cto.com/course/course_id-1887.html
l 一个综合性的,高级的中间人漏洞攻击框架。
l 由python编写的开源项目。
l 源代码:https://github.com/websploit/websploit
l 项目地址:http://sourceforge.net/projects/websploit/
l # [+]Autopwn - Used From Metasploit For Scan and Exploit Target Service
l # [+]Browser AutoPWN - Exploit Victim Browser
l # [+]wmap - Scan,Crawler Target Used From Metasploit wmap plugin
l # [+]format infector - inject reverse & bind payload into file format
l # [+]MLITM,XSS Phishing - Man Left In The Middle Attack
l # [+]MITM - Man In The Middle Attack
l # [+]USB Infection Attack - Create Executable Backdoor For Windows
l # [+]Java Applet Attack Vector
l # [+]ARP DOS - ARP Cache Denial Of Service Attack With Random MAC
l # [+]Directory Scanner - Scan Target Directorys
l # [+]Apache US - Scan Apache users
l # [+]PHPMyAdmin - Scan PHPMyAdmin Login Page
l # [+]Web Killer - Using From The TCPKill For Down Your WebSite On Network
l # [+]Fake AP - Fake Access Point
l # [+]FakeUpdate - Fake update attack
l # [+]Wifi Jammer - Wifi Jammer Attack
l # [+]Wifi Dos - Wifi Dos RQ Attack
l # [+]Wifi Mass De-authentication attack
l web
l network
l exploit
l wireless /bluetooth
l 1.确定攻击目标
l 2.查找可用模块
l 3.use 使用模块
l 4. show options 显示配置项
l 5.set 配置选项
l 6.run 开始执行
l 7.如果成功,权限获取

l 中间人攻击

ps:对此文章感兴趣的读者,可以加qq群:Hacking:303242737;Hacking-2群:147098303;Hacking-3群:31371755;hacking-4群:201891680;Hacking-5群:316885176
