原文链接:http://msdn.microsoft.com/en-us/library/ms537343.aspx
文中红色标注为相关解释。
关键字:隐私、策略、安全、Cookies、P3P
To successfully use cookies, the privacy features of Microsoft Internet Explorer 6 require XML Web services to deploy compact policies, as defined by the Platform for Privacy Preferences (P3P) developed by the World Wide Web Consortium. The Internet Explorer 6 privacy features filter cookies based on these compact policies, as well as the user's privacy settings. This overview educates Web services on the privacy requirements of cookies associated with their sites and on the cookie filtering implemented in Internet Explorer 6. Some cookies might not require a compact policy; however, implementing policies for all cookies is strongly recommended.
解释:Compact policies (privacy) IE中翻译为“精简隐私策略”,相关功能可以在IE的“隐私”选项卡里面看到。
As of the release of this article, the Platform for Privacy Preferences 1.0 (P3P1.0) Specification, which defines P3P and compact policies, is a candidate recommendation. The current working version of the P3P specification can be found at http://www.w3c.org/tr/p3p. This article provides some information on deploying P3P policies; consult the P3P specification and The Platform for Privacy Preferences Deployment Guide for complete details.
Additional Windows Internet Explorer Privacy References:
- How to Deploy P3P Privacy Policies on Your Web Site
- How to Create a Customized Privacy Import File
- Internet Explorer 6 Privacy Feature FAQ
- Privacy Reference Documentation
Contents
- Background on Privacy
- Persistent vs. Session Cookies
- First and Third-Party Context
- P3P and Compact Policies
- Cookie Filtering
- Unsatisfactory Cookies
- Internet Explorer Privacy Preference Settings
- Legacy Cookies
- Cookie Filtering and the Internet Explorer Security Zones
- Other Key Privacy Features in Internet Explorer
- What if the Privacy Features 'Broke' My Site?
- What Web Services Need To Do for Internet Explorer
- Related topics
Background on Privacy
The Problem
Web users are increasingly concerned that Web sites can locate them in the physical world, profile them in the virtual world, and correlate this information to form a "complete" identity. Web users also express concerns over Web sites sharing their personal data with other parties, such as marketing contacts, for unexpected purposes such as online behavior analysis. The problem is exacerbated by the fact that many users are often unaware of such data collection practices.
Cookies are widely used in data collection. Simply disabling cookies, however, is not a workable solution, because many applications depend on them. Similarly, prompting the user for each cookie download is not feasible because users are typically annoyed with such interruptions.
解释:初衷为何?当互联网广为使用的时候,个人隐私的保护显得更加重要,一些网站可能窃取用户的个人隐私来谋取暴利,cookies通常包含个人隐私信息。简单粗暴地将它关闭显然是不行的,一堆应用要求你必须使用Cookies,每次都让用户来决定是否可以读取/写入Cookies,也不合适,用户会被烦死。P3P就是为了解决这个问题而诞生的。
The Solution
The privacy features of Internet Explorer focus on advanced cookie filtering as a major step toward empowering users to protect their privacy. Although solving the cookie problem is not a panacea, it is an industry-leading step in addressing consumer anxiety over privacy concerns.
Advanced cookie filtering works by evaluating a Web site's privacy practices and deciding which cookies are acceptable based on the site's compact policies and on the user's own preferences. In the default settings, cookies that are used to collect personally identifiable information and do not allow users a choice in their use are considered "unsatisfactory." By default, unsatisfactory cookies are deleted in the first-party context when the browsing session ends and are rejected in the third-party context. In this way, users can choose to enjoy the benefits of cookies, while protecting themselves from unsatisfactory cookies. The full details of cookie filtering are discussed in the sections that follow.
The Internet Explorer technology for understanding a Web site's privacy policy is built on the P3P Specification. Using XML, P3P provides a common syntax and transport mechanism that enables Web sites to communicate their privacy practices to Internet Explorer (or any other user agent). Internet Explorer can then inform users of what is happening behind the scenes and assist them by filtering out unsatisfactory cookies.
Users can easily adjust the cookie filtering sensitivity of Internet Explorer by using a slider interface with six levels. Cookie filtering can also be fully customized in the following ways:
- Accept or deny cookies from specific Web sites
- Import custom cookie filtering settings
- Enable advanced controls for other cookie options
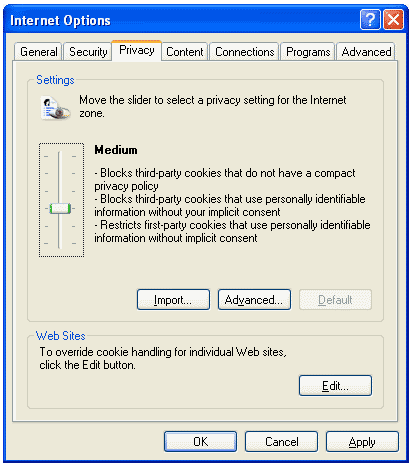
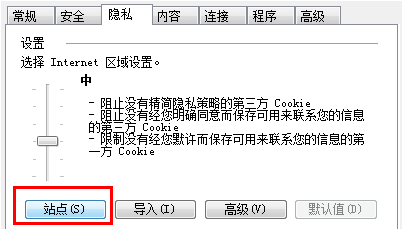
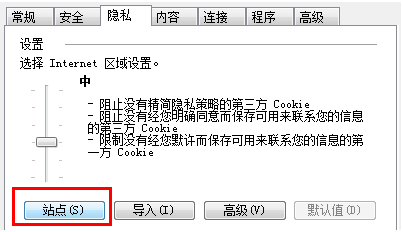
The following screen shot shows the interface that users can use to set cookie filtering options.
Figure 1. Privacy Tab
Persistent vs. Session Cookies
To discuss how Internet Explorer handles cookies, it is useful to know the difference between persistent and session cookies. Persistent cookies are discarded when they reach their defined expiration time. Cookies that do not have a specified expiration time are regarded as session cookies and are discarded when Internet Explorer is closed.
解释:持久化Cookies 和 会话Cookies,持久化Cookies是指有过期时间的Cookies,直到过期时间后清除,会话Cookies没有过期时间,在浏览器关闭后就清除。
First and Third-Party Context
Internet Explorer defines first-party content as content associated with the host domain. Third-party content originates from any other domain. For example, suppose a user visits www.wideworldimporters.com by typing this URL in the address bar, and www.wingtiptoys.com has a banner ad on this page. If these two sites set cookies, the cookies from www.wideworldimporters.com are in a first-party context while the cookies from www.wingtiptoys.com are in a third-party context.
解释:第一方内容和第三方内容的概念(该翻译参考IE中Internet选项,隐私选项卡中的翻译)。当前域的Cookies为第一方,除此之外的域为第三方。如从地址栏中访问www.wideworldimporters.com页面,在页面中嵌入了www.wingtiptoys.com站点的广告栏,那么www.wideworldimporters.com属于第一方,www.wingtiptoys.com就属于第三方。
Often commercial Web pages are an amalgamation of first- and third-party content. The Internet Explorer privacy features distinguish between first- and third-party content. The underlying assumption is that users have a different relationship with first parties than with third parties. In fact, users might not be aware of the third party or be given a choice of whether to have a relationship with it. For this reason, default privacy settings for third parties are more stringent than for first parties.
Note The URLs www.wideworldimporters.com and toys.wideworldimporters.com both contain the same minimal domain, wideworldimporters.com. Content that shares the same minimal domain as the host domain is considered first-party content. Likewise, cookies set from these domains are considered first-party cookies. Minimal domains must have the same top-level domain (TLD). Some common examples of TLDs are .com, .net, and .org.
解释:注意 www.wideworldimporters.com和 toys.wideworldimporters.com 站点拥有相同的”最小域“wideworldimporters.com(或者说是根域),他们都被认定为第一方,来自他们的Cookies也会被认定为第一方。
P3P and Compact Policies
The P3P specification standardizes the way Web sites summarize and represent policy information regarding their privacy practices. P3P policies are composed of XML statements that describe the data categories, the purposes of data collection, and the recipients of the data collected. P3P policies also contain other information, such as whom to contact for privacy-related disputes, the lifetime of the privacy policy, how a user can access the data collected, and what remedies can be taken for policy breaches. Different P3P policies can be specified for different aspects of a Web service. For example, a Web site can have different policies for its home page and its search page.
Note When making privacy statements about cookies, the statements must address any information stored in the cookies or made accessible by the cookies. For example, if a database is accessible through identifiers stored in cookies, then the privacy policy must govern the data collection practices of the data made accessible when using those identifiers.
P3P policies covering the use of cookies can be expressed in a condensed form called a compact policy. Essentially, the elements of the P3P policy are mapped to short tokens and aggregated to form a compact policy. Following is a brief example of how this works. Again, please consult the P3P Specification for full details.
Suppose Blue Yonder Airlines creates a P3P policy with two statements about its data collection practices. In the first statement, Blue Yonder Airlines specifies that it collects demographic information that includes gender, country, and zip code, for pseudonymous analysis (determining user habits and interests without association to a natural person) and that it shares this information with other recipients. The second statement specifies that Blue Yonder Airlines collects online information, specifically an e-mail address, on receiving the user's affirmative response, which is used exclusively for later contact. Each statement specifies that Blue Yonder Airlines uses cookies to facilitate these transactions. Also included in the policy is the access element, which specifies that users have access to the contact information collected from them. Blue Yonder Airlines' full P3P policy might look something like this:
<POLICY xmlns="http://www.w3.org/2000/12/P3Pv1"
discuri="http://www.blueyonderairlines.com/ourprivacypolicy.html"
opturi="http://www.blueyonderairlines.com/optin.html">
<ENTITY>
<DATA-GROUP>
<DATA ref="#business.name">Blue Yonder Airlines</DATA>
<DATA ref="#business.contact-info.postal.street">3456 Main St.</DATA>
<DATA ref="#business.contact-info.postal.city">Tampa</DATA>
<DATA ref="#business.contact-info.postal.stateprov">Fl</DATA>
<DATA ref="#business.contact-info.postal.postalcode">77062</DATA>
<DATA ref="#business.contact-info.postal.country">USA</DATA>
<DATA ref="#business.contact-info.online.email">molly@blueyonderairlines.com</DATA>
<DATA ref="#business.contact-info.telecom.telephone.intcode">1</DATA>
<DATA ref="#business.contact-info.telecom.telephone.loccode">800</DATA>
<DATA ref="#business.contact-info.telecom.telephone.number">5550158</DATA>
</DATA-GROUP>
</ENTITY>
<ACCESS><contact-and-other/></ACCESS>
<STATEMENT>
<PURPOSE><pseudo-analysis/></PURPOSE>
<RECIPIENT><other-recipient/></RECIPIENT>
<RETENTION><business-practices/></RETENTION>
<DATA-GROUP>
<DATA ref="#user.home-info.postal.country" optional="yes"/>
<DATA ref="#user.home-info.postal.postalcode" optional="yes"/>
<DATA ref="#user.gender" optional="yes"/>
<DATA ref="#dynamic.cookies" optional="yes">
<CATEGORIES><demographic/></CATEGORIES>
</DATA>
</DATA-GROUP>
</STATEMENT>
<STATEMENT>
<PURPOSE><contact required="opt-in"/></PURPOSE>
<RECIPIENT><ours/></RECIPIENT>
<RETENTION><stated-purpose/></RETENTION>
<DATA-GROUP>
<DATA ref="#user.home-info.online.email" optional="yes"/>
<DATA ref="#dynamic.cookies" optional="yes">
<CATEGORIES><online/></CATEGORIES>
</DATA>
</DATA-GROUP>
</STATEMENT>
</POLICY>
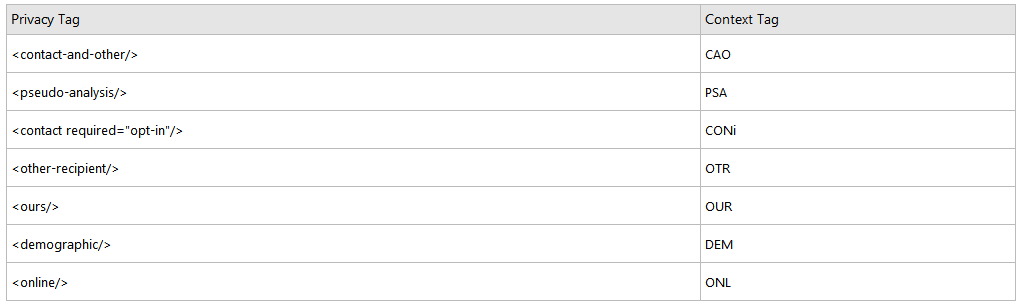
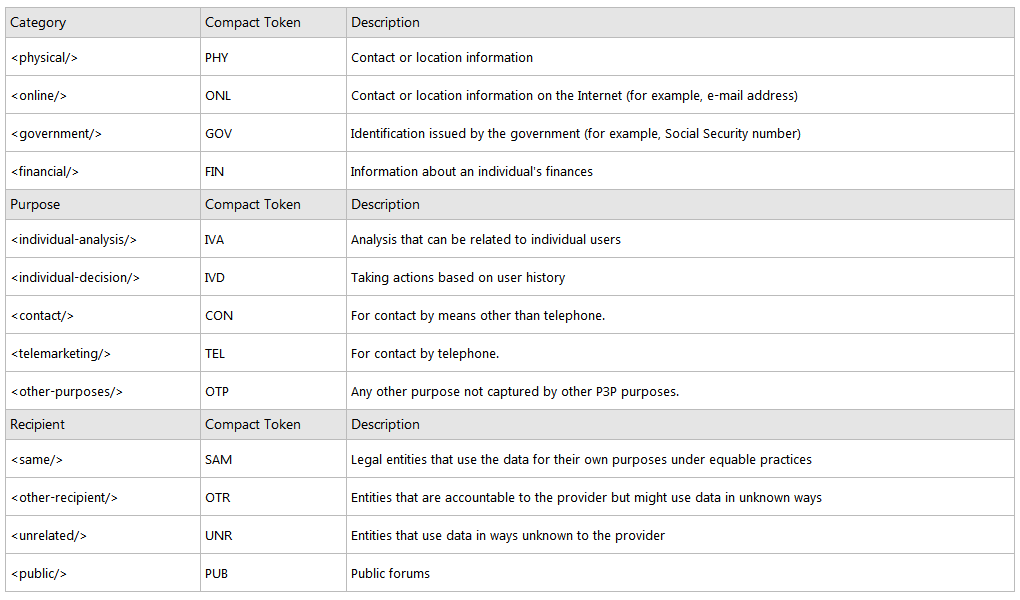
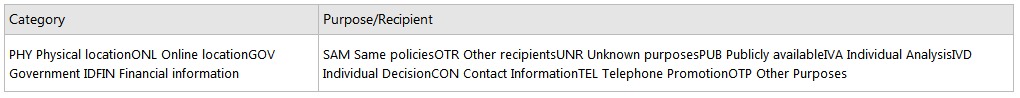
For each statement element, the category, purpose, and recipient element each have an associated compact form. The access element also has a compact form. The table below shows the compact tokens associated with each of the elements in this example.
We can form a compact policy for our example by aggregating these purpose, recipient, category, and access tokens. Compact policies are sent using a custom HTTP response header, with the syntax shown in the following example.
P3P: CP="CAO PSA CONi OTR OUR DEM ONL"
This header can be added to an HTTP response using Active Server Pages (ASP), or through the computer management console on Windows 2000 server and other popular Web servers. It is important to note that cookie compact policies are sent from the server along with the cookie data on HTTP responses, but that decisions and settings regarding cookies are made on the client (Internet Explorer).
Note The cookie filtering of Internet Explorer does not make use of full P3P policies. Compact policies are required for cookies. Cookies set through script or the meta element are governed by the compact policies on the associated HTTP response. Cookies without a compact policy are regarded by Internet Explorer as not having a policy.
The purpose tags and recipient tags of a P3P policy have an optional attribute that can take the value of "opt-in", "opt-out", or "always". The use of "opt-in" denotes that users must approve the purpose of use or recipient of the data. The use of "opt-out" denotes that data is used for the purpose or recipient specified unless the user chooses not to allow it; that is, the user opts out. Using "always" indicates that the purpose or recipient is always required. "Always" is the default if this attribute is not specified. Within compact policies, this attribute is abbreviated by a single letter and appended to the token. In our example, the "i" appended to the CON token indicates that users have to "opt-in" to have their online information used for contact purposes ("always" is abbreviated as "a" and "opt-out" as "o"). Tokens which do not include a single letter abbreviation are handled in the same way as tokens with an "a". For example, CON and CONa are treated the same.
Note It is important to note that the grouping of data categories, purposes, and recipients found in the P3P policy is lost in the aggregation process used to form a compact policy. This can lead to compact policies that have unintended consequences. In our example, the compact policy, "CAO PSA CONi OTR OUR DEM ONL", suggests that contact information can be shared with other recipients, when this might not necessarily be true. You can minimize ambiguity of this kind by creating individual P3P policies for cookies in different data-collection scenarios.
In our example, the policies for cookies used for pseudonymous analysis and those used for collection of personal information can be separated into different P3P policies with different compact policy forms. The two compact policies would then be "CAO PSA OTR DEM" and "CAO CONi ONL OUR" and would clearly express the intention of each type of cookie.
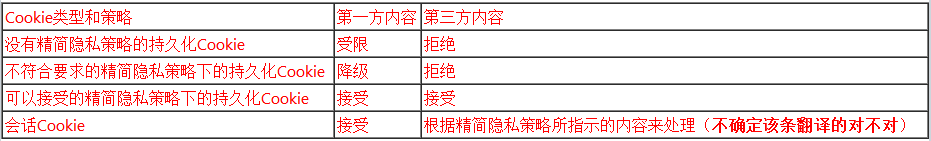
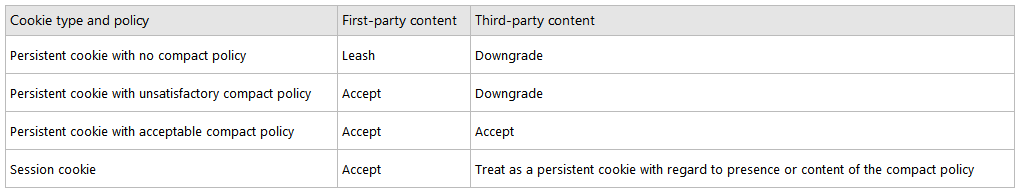
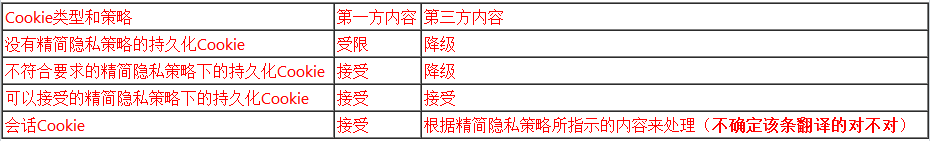
Cookie Filtering
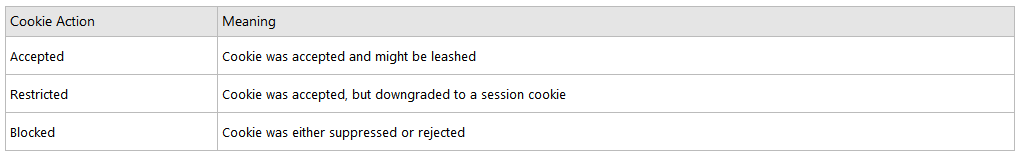
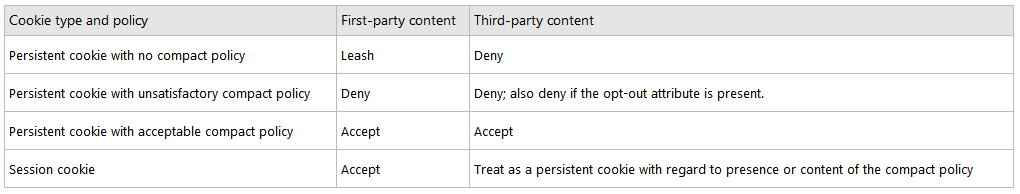
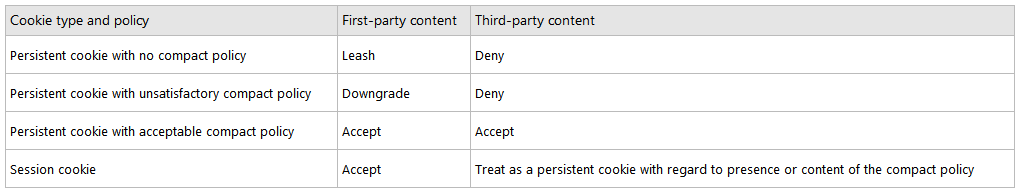
Internet Explorer takes action on cookies based on the context in which the cookie was sent and on the content of its compact policy. Depending on the situation, Internet Explorer will accept, deny, downgrade, or leash the cookie. A downgraded cookie is a persistent cookie that is deleted when the browsing session ends or the cookie expires, whichever comes first. A leashed cookie is one that is sent only on the request to download first-party content. When requests are made for third-party content, these cookies are suppressed; that is, they are not sent. For example, suppose tbat www.wingtiptoys.com is in the first-party context and sets a cookie in Internet Explorer. Suppose also that this cookie is leashed. When www.wingtiptoys.com is later present in a third-party context, the cookie is suppressed.
A small icon on the status bar informs the user when Internet Explorer has denied, downgraded, or suppressed cookies. The following screen shot shows this icon.

Clicking the icon brings the user to a privacy report dialog box summarizing the actions made by Internet Explorer on cookies. From the dialog box, users can choose to view full P3P policies in a user friendly format and grant "allow" or "block" cookie privileges to specific Web sites.
The following table lists the potential cookie action values that might be found in the privacy report dialog box and their meanings.
Unsatisfactory Cookies
解释:不符合要求的Cookies
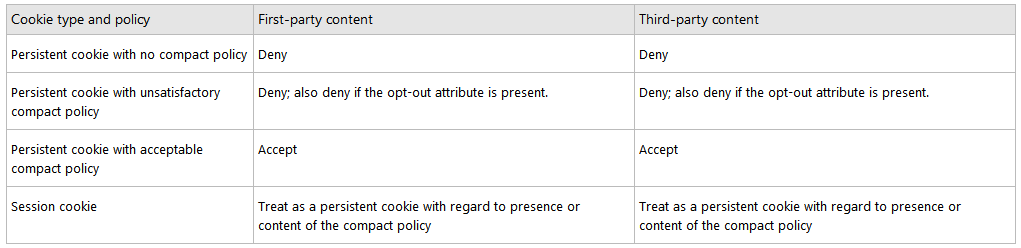
According to Internet Explorer, an unsatisfactory cookie contains or allows access to personally identifiable information that is used for unstated purposes or is provided to unstated recipients without user consent. An unsatisfactory cookie's category, and either the purpose or recipient, are contained in the following lists with neither opt-in nor opt-out specified. These categories, purposes, and recipients are only a subset of those in P3P used by Internet Explorer.
Note This list includes short descriptions and the compact tokens for the data categories, purposes, and recipients of unsatisfactory cookies. Consult the Platform for Privacy Preferences (P3P) specification for detailed definitions.
In summary, unsatisfactory cookies are those where the policy contains a token from both columns in the following table and where the purpose/recipient token does not contain the optional attributes, "i" or "o." As an example, a cookie with a compact policy that contains the tokens PHY and OTR is an unsatisfactory cookie, whereas a cookie with the compact policy that contains PHY and OTRo is acceptable.
解释:就是在“分类”以及“目的/接受者(二选其一)”,有一个包含i或者o(可选标记的字母),才算合格,如果都没有标记可选标记,则为不符合要求的Cookies。
Unsatisfactory Cookie Tags
Internet Explorer Privacy Preference Settings
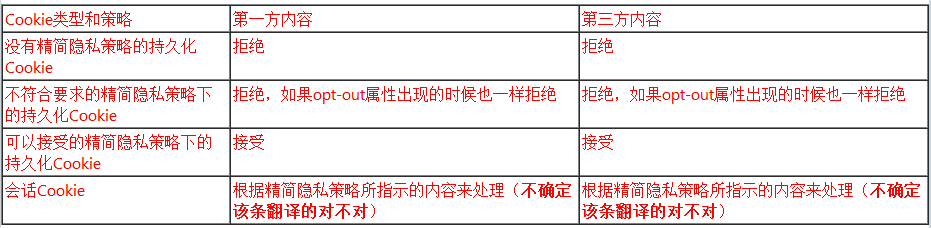
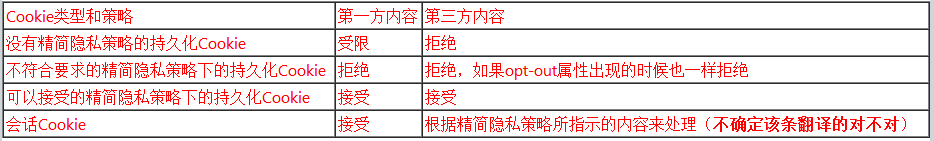
Users can change their privacy preferences by using a slider on the Privacy tab in Internet Options. The slider has six levels: Block All Cookies, High, Medium High, Medium (default level), Low, and Accept All Cookies. In the intermediate settings, compact policies are required of third-party cookies but not first-party cookies. However, first-party cookies without compact policies are leashed. This prohibits Web sites from setting a cookie without a compact policy in the first-party context for later use in a third-party context. First-party cookies are most effective when accompanied by a compact policy, so that they are reachable in the third-party context.
解释:在IE中一共分了六级隐私设置,从高到低,中间的部分都只要求”阻止没有第三方精简隐私策略的第三方Cookies“(从IE9的设置中看,只有”中高“、”中“、”低“三个是该特征,而”高“是”阻止没有第三方精简隐私策略的所有Cookies“。
当设置中是”阻止没有第三方精简隐私策略的第三方Cookies“的时候,只会影响第三方Cookies而不会影响第一方Cookies,因此第一方Cookies所在站点理论上不设置精简隐私策略对自己站点读取/写入Cookies并没有影响。但是第一方Cookies写入精简隐私策略是有意义的,因为只有在第一方中设置了精简隐私策略后,在第三方上下文中才能访问第一方Cookies。
A change in privacy settings does not affect nonlegacy cookies set prior to this change, except when set to Block All Cookies and Accept All Cookies. To ensure that all cookies follow the new settings, the user can delete all cookies before changing the privacy settings.
解释:用户在改变选项之前,可以将之前的Cookies删除,否则之前的Cookies的策略不受最新的策略影响。
The user also has the option to define cookie management practices on a per-site basis. These per-site settings override all the default privacy preferences set with the slider, except for Block All Cookies or Accept All Cookies.
The following sections describe the actions taken for first- and third-party cookies for each of the default privacy settings of the Internet zone.
Block all Cookies
This privacy setting is defined by the following:
- Deny all cookies.
- Do not send any cookies.
- Cookies already present are not deleted when this option is selected.
- This setting overrules any per-site cookie settings defined by the user.
解释:当选择”阻止所有Cookies“的时候:
- 拒绝所有的Cookies
- 不发送任何Cookies
- 当选择”阻止所有Cookies“选项的时候,之前已经存在的Cookies不会进行删除。(这也是上文中为何提到the user can delete all cookies before changing the privacy settings.的缘故)
- 任何“站点”中设置的选项,在这里均不生效。
High
Note The High setting uses a more stringent definition of unsatisfactory compact policies. First- and third-party cookies with compact policies that use the "opt-out" attribute with any of the purposes or recipients listed in the table of unsatisfactory tags are denied.
Medium High
Note The Medium High setting uses a more stringent definition of unsatisfactory compact policies. Third-party cookies with policies that use the "opt-out" attribute with any of the purposes or recipients listed in the table of unsatisfactory tags are denied.
Medium (Default)
Low
Accept all Cookies
This privacy setting is defined by the following:
- Accept all cookies regardless of the presence of a compact policy.
- Send all cookies.
- This setting overrides any per-site cookie settings defined by the user.
解释:
- 不管精简隐私策略如何统统接受
- 发送所有Cookies
- 任何“站点”中设置的选项,在这里均不生效。
Legacy Cookies
Internet Explorer defines a legacy cookie as a cookie that exists on the user's computer at the time Internet Explorer is installed or that is imported from another browser using the Import/Export Wizard under the File menu of Internet Explorer. Legacy cookies are not deleted during installation.
Legacy cookies are leashed when the default privacy setting is set to High, Medium High, Medium, or Low. Under the Block All Cookies or Accept All Cookies settings, legacy cookies are treated the same as other cookies and are unconditionally blocked or accepted, respectively.
Unless the user's privacy setting is set to Accept All Cookies, legacy cookies are accessible only in a first-party context.
Special Provision for Legacy Opt-Out Cookies
Internet Explorer has made a special provision for opt-out legacy cookies. Often when a user opts out of some online service, an opt-out cookie is used by the Web service to facilitate this choice. The success of this transaction sometimes relies on the ability of the browser to send this cookie in both first- and third-party contexts. However, with Internet Explorer, legacy cookies are leashed and are not sent in the third-party context. In response to this problem, Internet Explorer does not leash cookies where the name/value pair is "ID=OPT_OUT". (Please note that this name/value string is case- and space-sensitive.) Web sites should upgrade their opt-out cookies to use this syntax to ensure that legacy opt-out cookies are effective in Internet Explorer. Once Internet Explorer is installed, new opt-out cookies are handled just like any other non-legacy cookie.
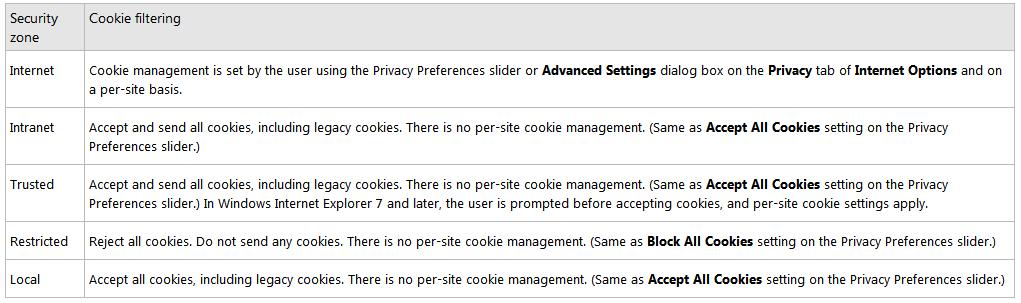
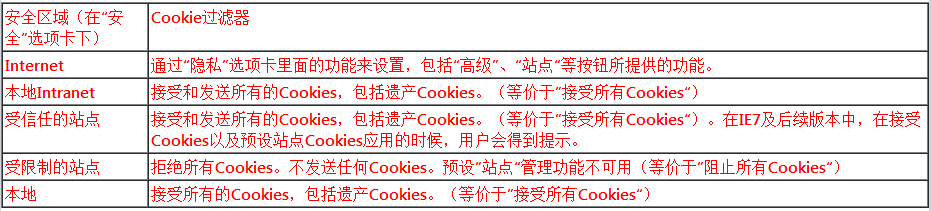
Cookie Filtering and the Internet Explorer Security Zones
Up until now, we have been talking about the Internet zone. However, the new privacy features also affect cookie handling in the other security zones. The following table describes the cookie management practices for each of the security zones.
Other Key Privacy Features in Internet Explorer
- P3P Privacy Policy Display: Internet Explorer retrieves full P3P policies and displays them in a user-friendly format.
- Per-Site Cookie Management: Through the Privacy Tab in the Internet Options dialog box, users can accept or deny cookies from individual Web sites. All existing cookies for a site are deleted when that site is added to the per-site list with the instruction to Deny all cookies from that site.
- Advanced Settings: Users can accept, deny, or be prompted for cookies in both the first- and third-party contexts. The user can also choose to always allow session cookies. When a user chooses to be prompted, a dialog box appears so that a user can accept or reject a cookie. The dialog box also offers the user a chance to examine the cookie's name/value pair, expiration, compact policy, and whether it was sent in a first- or third-party context.
- Import: Users can import an XML file that can customize cookie handling for compact policies in all security zones, except for the Restricted and Local zones, and on a per-site basis. For more information, see How to Create a Customized Privacy Import File.
What if the Privacy Features 'Broke' My Site?
It is likely that the Web site's behavior is dependent on cookies that are unexpectedly being rejected or suppressed. To avoid this, users can move the privacy preferences slider down to Accept All Cookies, or they can explicitly choose to allow a Web site's cookies by clicking the Site button on the Privacy tab of Internet Options and adding the site to the per-site list.
What Web Services Need To Do for Internet Explorer
To continue the successful deployment of cookies for use with Internet Explorer or its public preview, the best thing to do is to deploy P3P on your site. This involves first assessing your business practices, and then creating a comprehensive policy. Visit the P3P Project Web site and take advantage of the tools and resources. Many cookies without compact policies will be rejected by default, so deploying P3P with compact policies is critical for maintaining your Web services. Addressing Internet privacy is the responsibility of the entire industry, and now is the time to take steps toward these sensible, interoperable solutions.
Related topics
- Conceptual
- How to Deploy P3P Privacy Policies on Your Web Site
- How to Create a Customized Privacy Import File
- Internet Explorer Privacy Feature FAQ
- Privacy Reference Documentation
- Other Resources
- W3C: Platform for Privacy Preferences (P3P) Project
- candidate recommendation
- Platform for Privacy Preferences (P3P) specification
- The Platform for Privacy Preferences Deployment Guide