一.官网对Wallet的说明
http://docs.oracle.com/cd/E11882_01/network.112/e10746/asowalet.htm
Security administratorsuse Oracle Wallet Manager to manage public key security credentials on Oracleclients and servers. The wallets it creates can be read by Oracle Database,Oracle Application Server 10g, and the Oracle Identity Managementinfrastructure.
Oracle WalletManager is an application that wallet owners use to manage and edit thesecurity credentials in their Oracle wallets. A wallet is a password-protectedcontainer used to store authentication and signing credentials, includingprivate keys, certificates, and trusted certificates needed by SSL.
1.1 Oracle Manager 特性
Oracle Wallet Manager provides thefollowing features:
MicrosoftWindows Registry Wallet Storage
Public-KeyCryptography Standards (PKCS) Support
1.1.1 Wallet Password Management
Oracle walletsare password protected. Oracle Wallet Manager includes an enhanced walletpassword management module that enforces Password Management Policy guidelines,including the following:
(1) Minimum password length (8 characters)
(2) Maximum password length unlimited
(3) Alphanumeric character mix required
Oracle wallets对密码的保护,包含对密码强度的管理:
1. 最少8个字符;
2.密码长度没有最大限制;
3.密码必须是字母和字数的组合。
1.1.2 Strong Wallet Encryption
Oracle WalletManager stores private keys associated with X.509 certificates and usesTriple-DES encryption.
--Oracle Wallet Manager 使用X.509 认证和Triple-DES 加密来存储private key。
1.1.3 Microsoft Windows RegistryWallet Storage
Oracle WalletManager lets you store multiple Oracle wallets in a Windows file managementsystem or in the user profile area of the Microsoft Windows system registry.Storing your wallets in the registry provides the following benefits:
(1)Better Access Control: Wallets stored in the user profile area of the registry areonly accessible by the associated user. User access controls for the systemthus become, by extension, access controls for the wallets. In addition, when auser logs out of a system, access to that user's wallets is effectivelyprecluded.
(2)EasierAdministration: Wallets are associated withspecific user profiles, so no file permissions need to be managed, and thewallets stored in the profile are automatically deleted when the user profileis deleted. You can use Oracle Wallet Manager to create and manage the walletsin the registry.
1.1.4 Backward Compatibility
Oracle Wallet Manager isbackward-compatible to Release 8.1.7.
--Oracle Wallet Manager 兼容性支持到8.1.7.
1.1.5 Public-Key CryptographyStandards (PKCS) Support
RSALaboratories, a division of RSA Security, Inc., has developed, in cooperationwith representatives from industry, academia, and government, a family of basiccryptography standards called Public-Key Cryptography Standards, or PKCS forshort. These standards establish interoperability between computer systems thatuse public-key technology to secure data across intranets and the Internet.
Oracle Wallet Manager stores X.509 certificates and private keys in PKCS #12format, and generates certificate requests according to the PKCS #10specification. These capabilities make the Oracle wallet structureinteroperable with supported third-party PKI applications and provide walletportability across operating systems.
Oracle Wallet Manager wallets can store credentials onhardware security modules that use APIs conforming to the PKCS #11specification. When a wallet is createdwith PKCS11 chosen as the wallet type, then all keys stored in thatwallet are saved to a hardware security module or token. Examples of suchhardware devices include smart cards, PCMCIAcards, smart diskettes, or other portable hardware devices that storeprivate keys or perform cryptographic operations (or both).
1.1.6 Multiple Certificate Support
Oracle WalletManager enables you to store multiple certificatesin each wallet, supporting any of the following OraclePKI certificate usages:
(1) SSL authentication
(2) S/MIME signature
(3) S/MIME encryption
(4) Code-Signing
(5) CA Certificate Signing
Each certificate request you create generates a uniqueprivate/public key pair. The private key stays in thewallet and the public key is sent with the request to a certificate authority.When that certificate authority generates your certificate and signs it, youcan import it only into the wallet that has the corresponding private key.
If the walletalso contains a separate certificate request, the private/public key paircorresponding to that request is of course different from the pair for thefirst certificate request. Sending this separate certificate request to acertificate authority can get you a separate signed certificate, which you canimport into this same wallet
A singlecertificate request can be sent to a certificate authority multiple times toobtain multiple certificates. However, only one certificate corresponding tothat certificate request can be installed in the wallet.
1.1.7 LDAP Directory Support
Oracle WalletManager can upload wallets to and retrieve them from an LDAP-compliantdirectory. Storing wallets in a centralized LDAP-compliant directory lets usersaccess them from multiple locations or devices, ensuring consistent andreliable user authentication while providing centralized wallet management throughoutthe wallet life cycle. To prevent a user from accidentally overwritingfunctional wallets, only wallets containing an installed certificate can beuploaded.
Directory user entries must be defined andconfigured in the LDAP directory before Oracle Wallet Manager can be used toupload or download wallets for a user. If a directory containsOracle8i (or prior) users, then they are automatically upgraded to use thewallet upload and download feature on first use.
Oracle WalletManager downloads a user wallet by using a simple password-based connection tothe LDAP directory. However, for uploads it uses an SSL connection if the openwallet contains a certificate with SSL Oracle PKI certificate usage. If an SSLcertificate is not present in the wallet, password-based authentication isused.
Note:
The directorypassword and the wallet password are independent and can be different. Oraclerecommends that these passwords be maintained to be consistently different,where neither one can logically be derived from the other.
1.2 Starting Oracle Wallet Manager
To start Oracle Wallet Manager:
(1) (Windows)Select Start, Programs, Oracle-HOME_NAME, IntegratedManagement Tools, Wallet Manager
(2) (UNIX) At the command line, enter owm.
--以上2个都是启用图形管理界面。
1.3 How toCreate a Complete Wallet: Process Overview
Wallets providea necessary repository in which you can securely store your user certificatesand the trustpoint you need to validate the certificates of your peers.
The following stepsprovide an overview of the complete wallet creation process:
(1)Use Oracle Wallet Manager to create a new wallet:
(2)Generate a certificate request. Note that when you create a newwallet with Oracle Wallet Manager, the tool automatically prompts you to createa certificate request.
(3)Send the certificate request to the CA you want to use. You can copyand paste the certificate request text into an e-mail message, or you canexport the certificate request to a file. The certificate request becomes partof your wallet. It must remain there until you remove its associatedcertificate.
(4)When the CA sends your signed user certificate and itsassociated trustedcertificate, then you can import these certificates in the following order.The user certificates and trusted certificates in the PKCS #7 format can beimported at the same time.
1)First import the CA's trusted certificateinto your wallet. This step may be optional if the new user certificate hasbeen issued by one of the CAs whose trusted certificate is already present inOracle Wallet Manager by default.
2)After you have successfully imported the trustedcertificate, then import the user certificate that the CA sent to you into yourwallet.
(5)(Optional) Set the auto login feature for your wallet.
Typically, thisfeature, which enables PKI-based access to services without a password, isrequired for most wallets. It is required for database server and clientwallets. It is only optional for products that take the wallet password at thetime of startup.
After completingthe preceding process, you have a wallet that contains a user certificate and itsassociated trust points.
二.管理Wallet
Wallet 可以使用Oracle Wallet Manger工具来创建,也可以使用orapki 命令来创建,也可以使用SQL 语句来创建。这里最方便的是使用SQL语句。
2.1 使用SQL与创建Wallet
在sqlnet.ora 文件里添加: ENCRYPTION_WALLET_LOCATION 和WALLET_LOCATION参数。默认位置是:$ORACLE_BASE/admin/$ORACLE_SID/wallet。
--指定ORACLE WALLET的位置,这里使用ORACLE_HOME/network/admin,在sqlnet.ora里添加如下内容:
WALLET_LOCATION =
(SOURCE =
(METHOD = FILE)
(METHOD_DATA =
(DIRECTORY= /u01/app/oracle/product/11.2.0/db_1/network/admin)
)
)
ENCRYPTION_WALLET_LOCATION =
(SOURCE =
(METHOD = FILE)
(METHOD_DATA =
(DIRECTORY= /u01/app/oracle/admin/dave/wallet)
)
)
SQLNET.WALLET_OVERRIDE = TRUE
SSL_CLIENT_AUTHENTICATION = FALSE
SSL_VERSION = 0
--添加完之后,重启listener,使参数生效。
--创建wallet:包括设置密码、生成信任文件、并启动wallet
CONN / AS SYSDBA
-- 10g version
ALTER SYSTEM SET ENCRYPTIONKEYAUTHENTICATED BY "myPassword";
-- 11g version
ALTER SYSTEM SET ENCRYPTIONKEYIDENTIFIED BY "myPassword";
当实例重启后或者wallet被关闭后,必须重新open wallets,这样才能保护被加密的列.而在Openwallet之前,数据库必须处于mount 状态。官网的说明如下:
The security administrator also needs to open the wallet before performingdatabase recovery operations. This is because background processes may requireaccess to encrypted redo and undo logs. When performing database recovery, thewallet must be opened before opening the database. This is illustrated in thefollowing statements:
SQL>STARTUP MOUNT;
SQL> ALTERSYSTEM SET ENCRYPTION WALLET OPEN IDENTIFIED BY "myPassword";
SQL>ALTER DATABASE OPEN;
-- 10g version
ALTER SYSTEM SET ENCRYPTION WALLET OPEN AUTHENTICATEDBY "myPassword";
-- 11g version
ALTER SYSTEM SET ENCRYPTION WALLET OPEN IDENTIFIEDBY "myPassword";
--关闭Wallet:
ALTER SYSTEM SET ENCRYPTIONWALLET CLOSE IDENTIFIED BY "myPassword";
2.2 使wallet自动登陆
使用SQL 创建的wallet 的问题是不能自动登陆,这样我们在关闭wallet或者重启实例后,都需要手动的来open wallet。 这样有点麻烦,Oracle 提供了wallet 自动登陆功能,可以在创建wallet指定该属性,也可以在创建后使用owm(Oracle wallet manager)来修改。
2.2.1 使用OWM工具修改
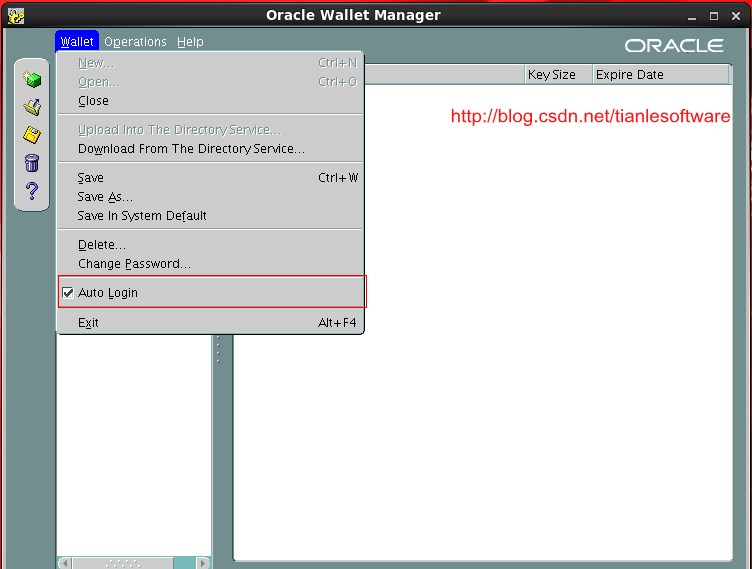
当然OWM 也提供了提的功能,如下:
有关OWM 工具与Wallet 的更多使用说明,参考:
http://docs.oracle.com/cd/E11882_01/network.112/e10746/asowalet.htm
2.2.2 使用orapki 命令
有关该命令的使用说明,参考:
orapki Utility
http://docs.oracle.com/cd/E11882_01/network.112/e10746/asoappf.htm
2.2.2.1 显示wallet
[oracle@dave /]$orapki wallet display -wallet /u01/app/oracle/admin/dave/encryption_wallet
Oracle PKI Tool : Version 11.2.0.3.0 -Production
Copyright (c) 2004, 2011, Oracle and/or itsaffiliates. All rights reserved.
Requested Certificates:
Subject: CN=oracle
User Certificates:
Oracle Secret Store entries:
ORACLE.SECURITY.DB.ENCRYPTION.AWEiNK+nmU+Uv04PUaRYzbEAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
ORACLE.SECURITY.DB.ENCRYPTION.MASTERKEY
ORACLE.SECURITY.TS.ENCRYPTION.BYxe8gX+JaWda5meFCZfAx4CAwAAAAAAAAAAAAAAAAAAAAAAAAAA
Trusted Certificates:
[oracle@dave /]$
这里面的内容和我们通过OWM工具查看的一致。
2.2.2.2 修改wallet 密码
语法如下:
orapki wallet change_pwd -wallet wallet_location[-oldpwd password ] [-newpwd password]
这里可以不指定密码,该命令会提示用户输入旧密码和新密码。 基于安全的考虑,Oracle也推荐在命令行输入口令,而不是在命令中指定密码。
[oracle@dave /]$orapki wallet change_pwd-wallet /u01/app/oracle/admin/dave/encryption_wallet
Oracle PKI Tool : Version 11.2.0.3.0 -Production
Copyright (c) 2004, 2011, Oracle and/or itsaffiliates. All rights reserved.
Enter wallet password:
New password:
Enter wallet password:
[oracle@dave /]
2.2.2.3 创建auto login wallet
创建不需要密码的auto loginwallet(cwallet.sso)的语法如下:
orapki wallet create -wallet wallet_location -auto_login_only
该命令创建auto login wallet(cwallet.sso),在open 时不需要口令。在修改或者删除时同样也不需要密码。
创建使用PKCS#12 的auto login wallet。 该wallet 在open时不需要密码,但在修改或者删除时需要提供密码。任何对PKCS#12的修改都会影响auto login wallet。创建语法如下:
orapki walletcreate -wallet wallet_location -auto_login [-pwd password]
该命令生成auto login enabled (cwallet.sso)和PKCS#12wallet (ewallet.p12)。如果在命令行中没有指定密码,那么会提示我们输入密码。
注意:
wallet目录下的文件(ewallet.p12)不能丢失,否则将导致加密的数据无法访问,会报如下错误:
ORA-28362: master key not found
2.3 Wallet相关的视图
--V$ENCRYPTION_WALLET
SQL> desc V$ENCRYPTION_WALLET
Name Null? Type
----------------------------- ----------------------------
WRL_TYPE VARCHAR2(20)
WRL_PARAMETER VARCHAR2(4000)
STATUS VARCHAR2(18)
--v$wallet
SQL> desc v$wallet
Name Null? Type
----------------------------- ----------------------------
CERT_ID VARCHAR2(52)
DN VARCHAR2(255)
SERIAL_NUM VARCHAR2(40)
ISSUER VARCHAR2(255)
KEYSIZE NUMBER
STATUS VARCHAR2(16)
-- dba_encrypted_columns
SQL> desc dba_encrypted_columns
Name Null? Type
----------------------------- ----------------------------
OWNER NOT NULL VARCHAR2(30)
TABLE_NAME NOT NULL VARCHAR2(30)
COLUMN_NAME NOT NULL VARCHAR2(30)
ENCRYPTION_ALG VARCHAR2(29)
SALT VARCHAR2(3)
INTEGRITY_ALG VARCHAR2(12)
---------------------------------------------------------------------------------------
版权所有,文章允许转载,但必须以链接方式注明源地址,否则追究法律责任!
Skype: tianlesoftware
QQ: tianlesoftware@gmail.com
Email: tianlesoftware@gmail.com
Blog: http://blog.csdn.net/tianlesoftware
Weibo: http://weibo.com/tianlesoftware
Twitter: http://twitter.com/tianlesoftware
Facebook: http://www.facebook.com/tianlesoftware
Linkedin: http://cn.linkedin.com/in/tianlesoftware