一、创建sftp相关用户和目录
[root@mail samba]# useradd -s /sbin/nologin -M sftp_user #创建一个系统用户,按需设置登录的shell和家目录 [root@mail samba]# passwd sftp_user #设置密码,也是sftp登录的密码,公网上尽可能复杂点 [root@mail samba]# mkdir /var/sftp/sftp_user -pv #创建sftp的根目录 [root@mail samba]# chown root:root -R /var/sftp/sftp_user #将属组和属主都设置为root,必须,这里最容易出错 [root@mail sftp_user]# cd /var/sftp/sftp_user/ [root@mail sftp_user]# mkdir public #创建共享目录 [root@mail sftp_user]# chown sftp_user:sftp_user -R /var/sftp/sftp_user/public/ #将共享目录的属组属主设为我们的sftp用户
二、编辑sshd配置文件,内容如下
# $OpenBSD: sshd_config,v 1.80 2008/07/02 02:24:18 djm Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
# This sshd was compiled with PATH=/usr/local/bin:/bin:/usr/bin
# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options change a
# default value.
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::
# Disable legacy (protocol version 1) support in the server for new
# installations. In future the default will change to require explicit
# activation of protocol 1
Protocol 2 #支持的SSH协议的版本号
# HostKey for protocol version 1
#HostKey /etc/ssh/ssh_host_key
# HostKeys for protocol version 2
#HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_dsa_key
# Lifetime and size of ephemeral version 1 server key
#KeyRegenerationInterval 1h
#ServerKeyBits 1024
# Logging
# obsoletes QuietMode and FascistLogging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV #将日志消息通过哪个日志子系统(facility)发送
#LogLevel INFO
# Authentication:
#LoginGraceTime 2m
#PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10
#RSAAuthentication yes
#PubkeyAuthentication yes
#AuthorizedKeysFile .ssh/authorized_keys
#AuthorizedKeysCommand none
#AuthorizedKeysCommandRunAs nobody
# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#RhostsRSAAuthentication no
# similar for protocol version 2
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# RhostsRSAAuthentication and HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes
# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication yes #允许通过密码进行登录
# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no #是否允许质疑-应答(challenge-response)认证。默认值是"yes"。
# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes
# GSSAPI options
#GSSAPICleanupCredentials yes
GSSAPICleanupCredentials yes #是否在用户退出登录后自动销毁用户凭证缓存。默认值是"yes"。仅用于SSH-2。
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
#UsePAM no
UsePAM yes #是否启用pam认证
# Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES #指定客户端发送的哪些环境变量将会被传递到会话环境中。[注意]只有SSH-2协议支持环境变量的传递,可以设置多个
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS
#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
#X11Forwarding no
X11Forwarding yes #是否允许进行 X11 转发。默认值是"no",设为"yes"表示允许
#X11DisplayOffset 10
#X11UseLocalhost yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#UsePrivilegeSeparation yes
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#ShowPatchLevel no
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
# no default banner path
#Banner none
# override default of no subsystems
#Subsystem sftp /usr/libexec/openssh/sftp-server
Subsystem sftp internal-sftp #配置一个外部子系统,仅用于SSH-2协议。值是一个子系统的名字和对应的命令行(含选项和参数)。比如"sftp /usr/libexec/openssh/sftp-server"。,###这里配置为内部的
# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# ForceCommand cvs server
GSSAPIAuthentication no #是否允许使用基于 GSSAPI 的用户认证。默认值为"no"。仅用于SSH-2。
UseDNS no #是否对远程主机名进行反向解析
AllowTcpForwarding yes #是否允许TCP转发
Compression yes #是否对通信数据进行加密,还是延迟到认证成功之后再对通信数据加密
MaxAuthTries 6 #指定每个连接最大允许的认证次数。默认值是 6
PermitRootLogin yes #是否允许 root 登录
PrintMotd yes #是否在每一次交互式登录时打印 /etc/motd 文件的内容
PubkeyAuthentication yes #是否允许公钥认证。仅可以用于SSH-2。默认值为"yes"。
RSAAuthentication no #是否允许使用纯 RSA 公钥认证。仅用于SSH-1。默认值是"yes"
Match User sftp_user #对特定的用户单独配置,匹配到的用户会强制使用/bin/false shell,只能以sftp登录,无法使用ssh登录服务器,没有匹配到的用户或组可以直接sftp登录,但是根目录为自己的家目录,无法指定具体的根目录。也可以设置为组,例如:Match Group sftp
ChrootDirectory /var/sftp/sftp_user/ #限定用户的根目录
X11Forwarding no
AllowTcpForwarding yes
ForceCommand internal-sftp #强制执行这里指定的命令而忽略客户端提供的任何命令
重启sshd服务
[root@mail sftp_user]# /etc/init.d/sshd restart
停止 sshd: [确定]
正在启动 sshd: [确定]
测试登录,这里使用winscp这款软件
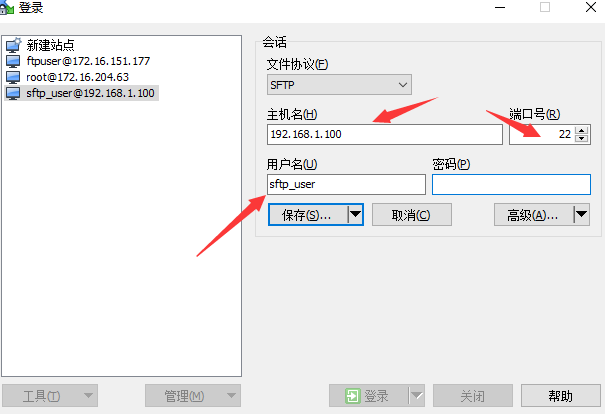
输入我们之前设置的密码
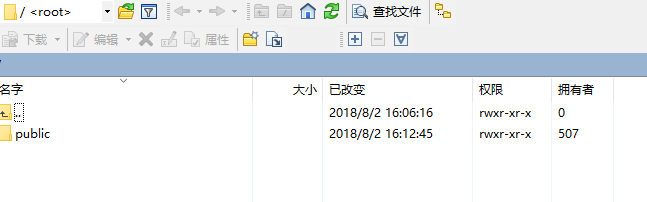
登录成功