一、渗透测试
1、信息收集类
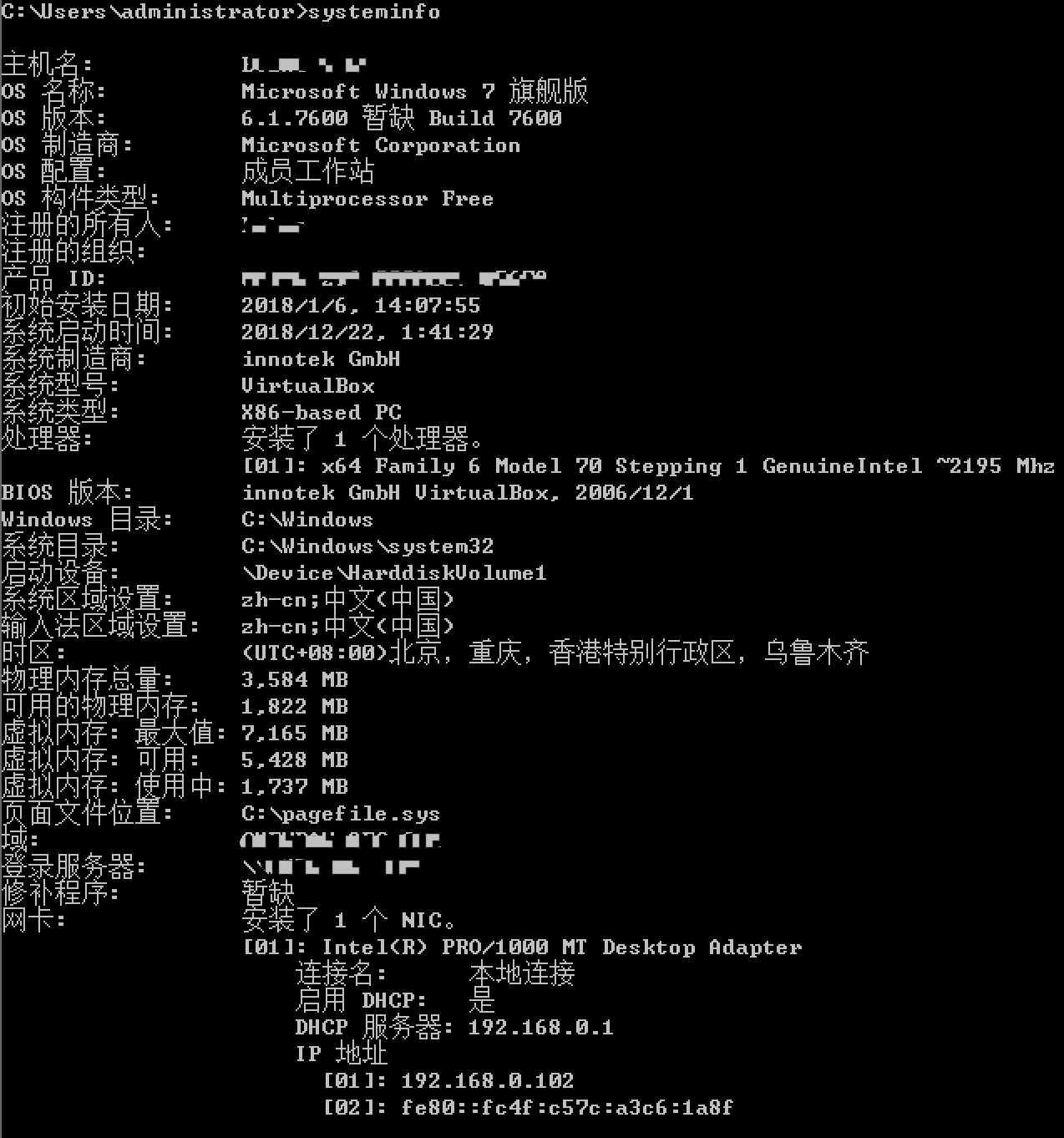
#查看系统信息
>systeminfo
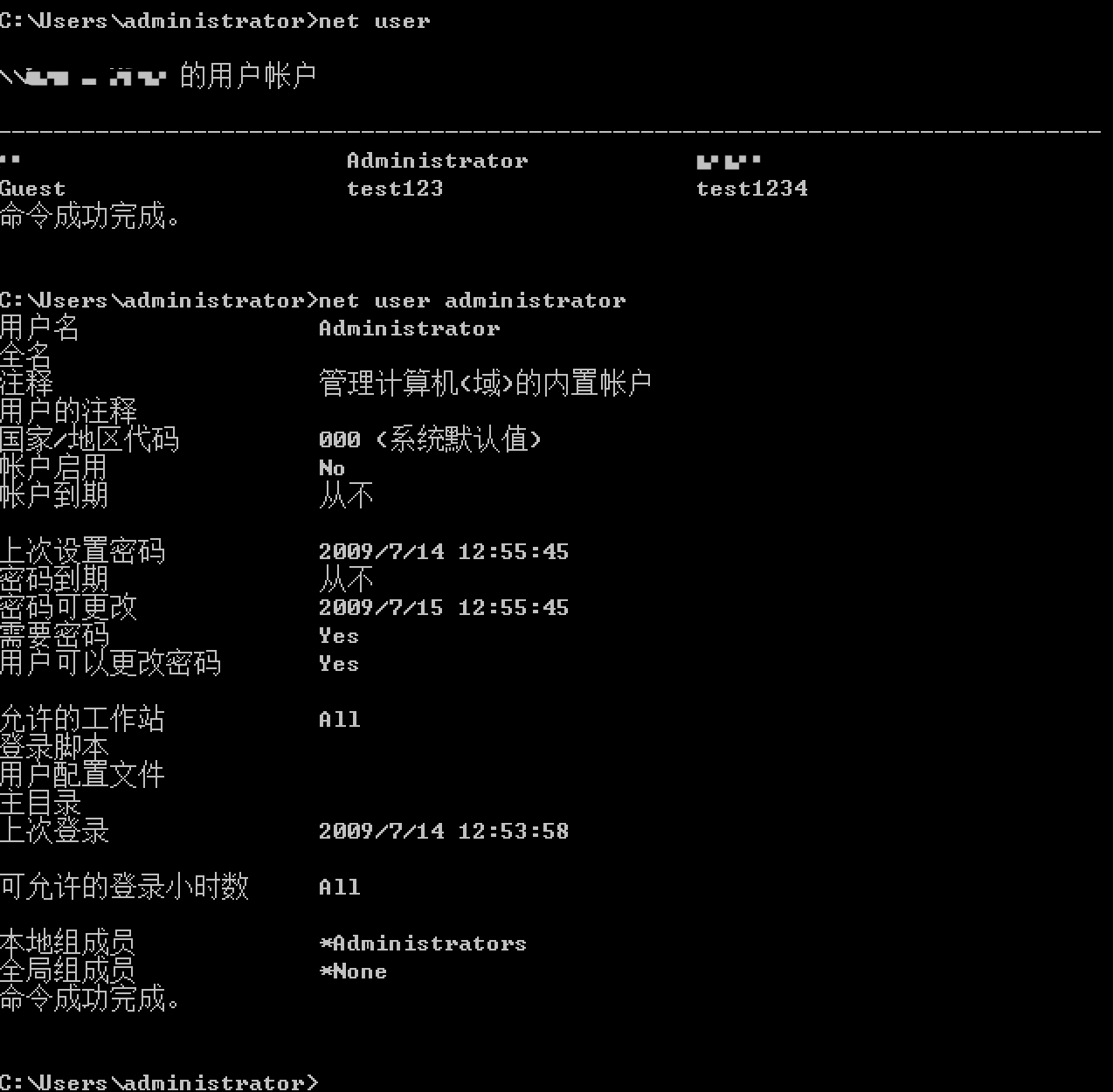
#查看用户信息
>net user
>net user xxx
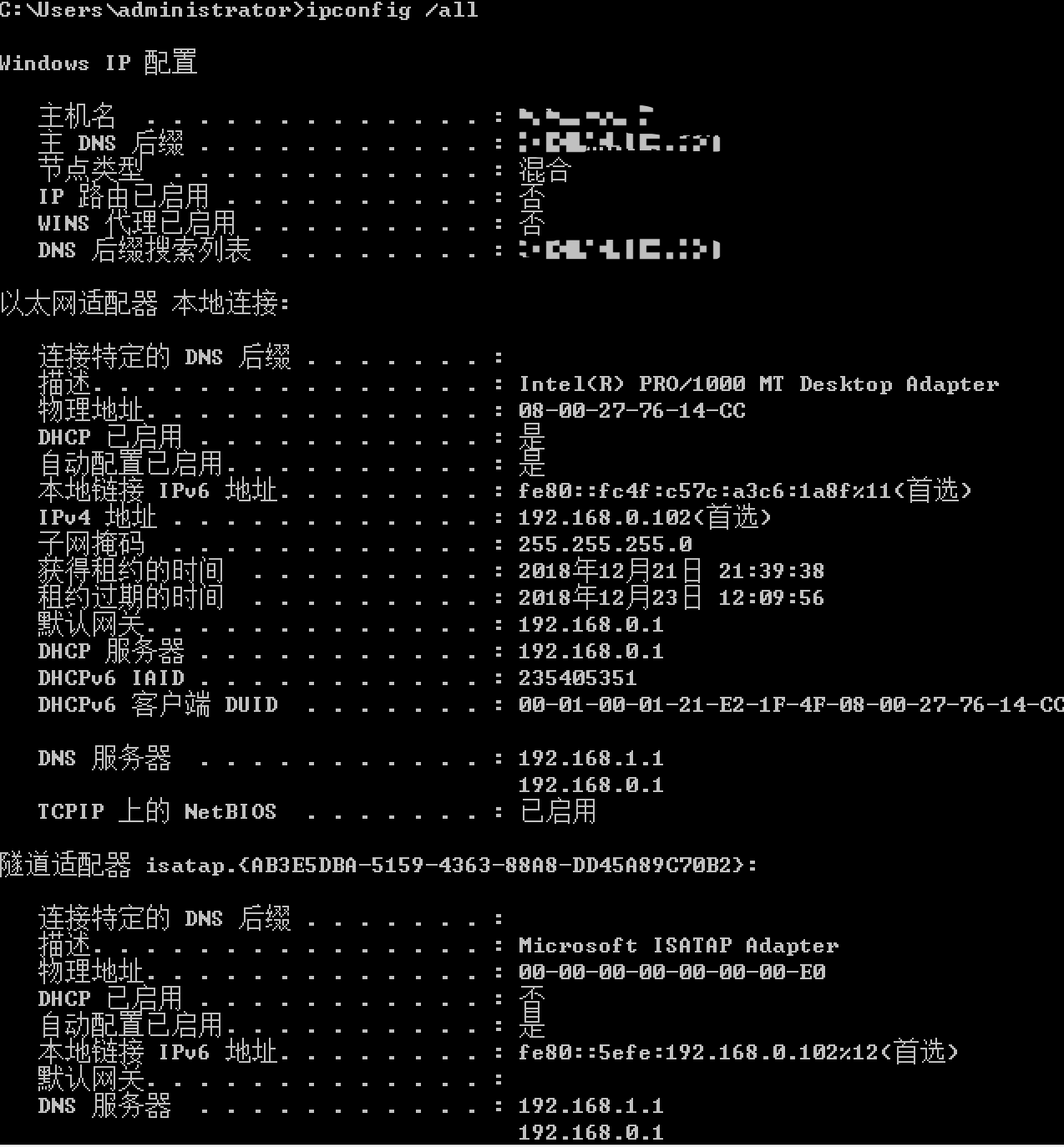
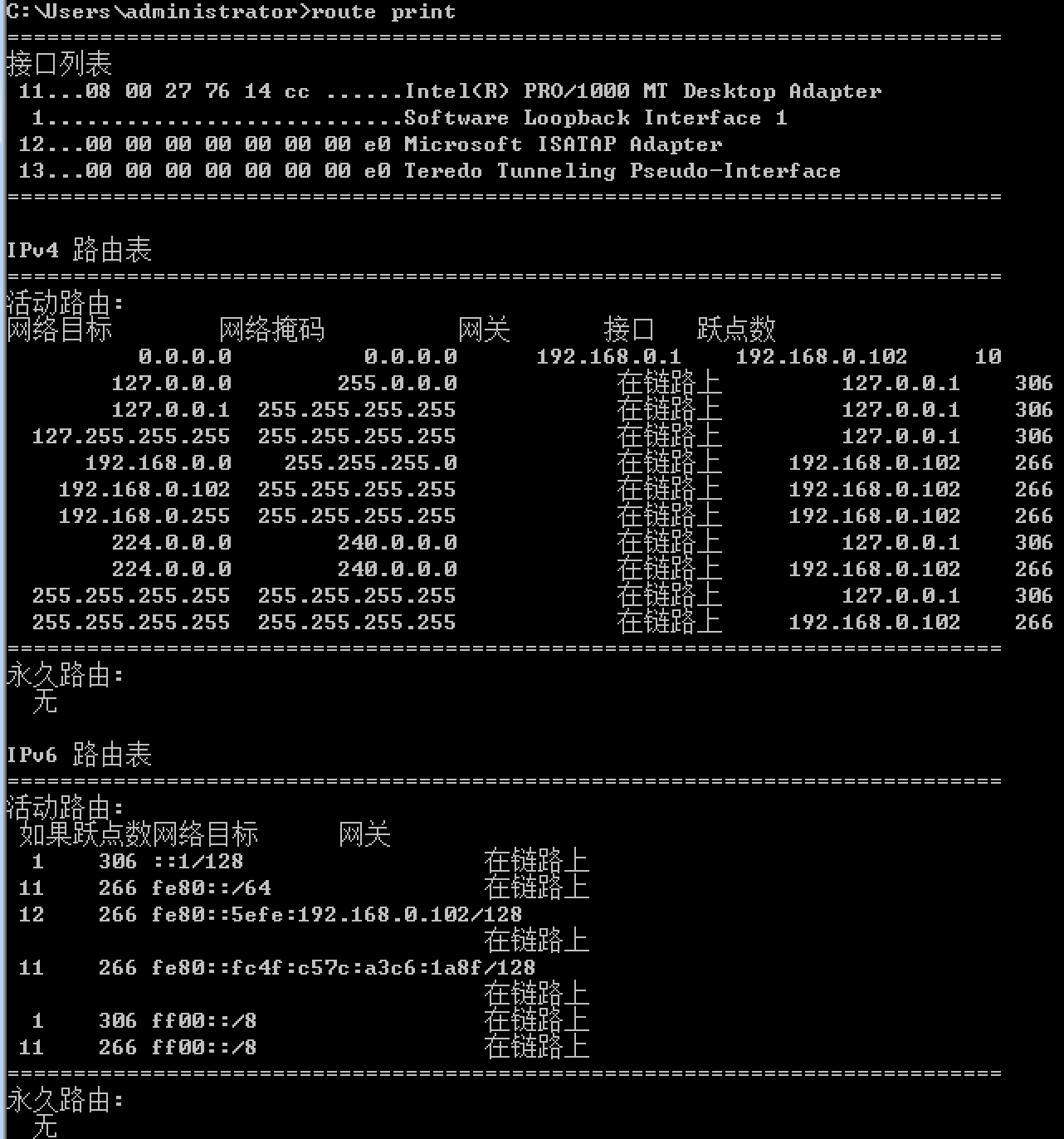
#查看网络信息
>ipconfig /all
>route print
>netstat -abon
>netstat -s
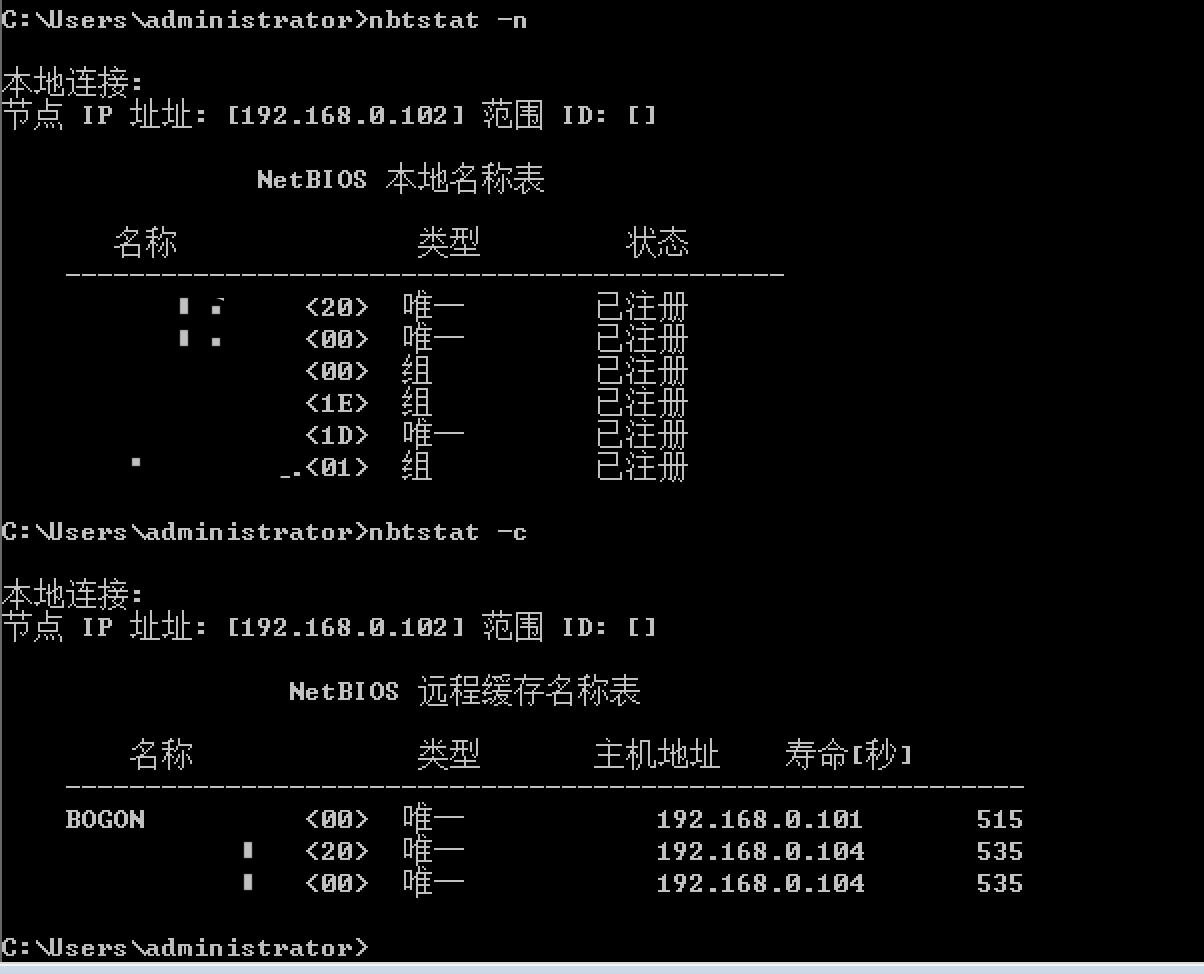
>nbtstat -c
>nbtstat -n
>arp -a
#查询域信息
>net time /domain
>net view /domain
>net user /domain
>net group "domain admins" /domain
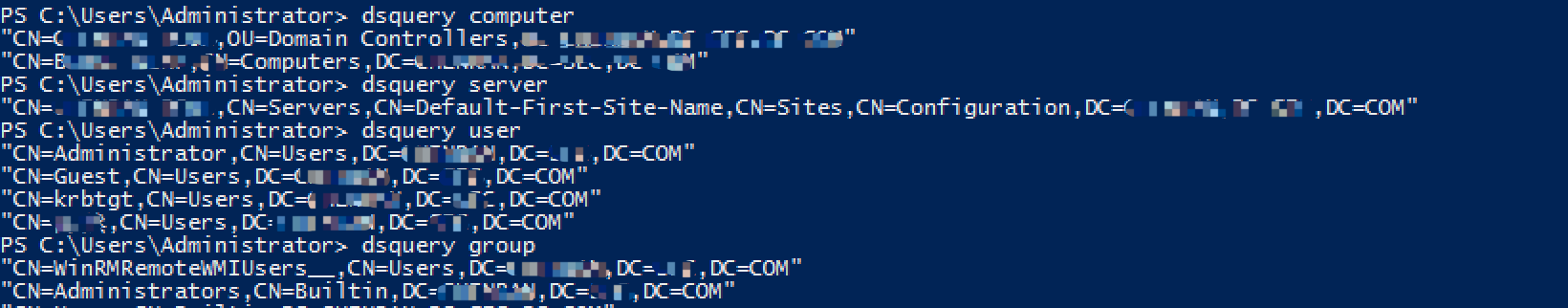
>dsquery comoputer
>dsquery server
>dsquery group
>dsquery user
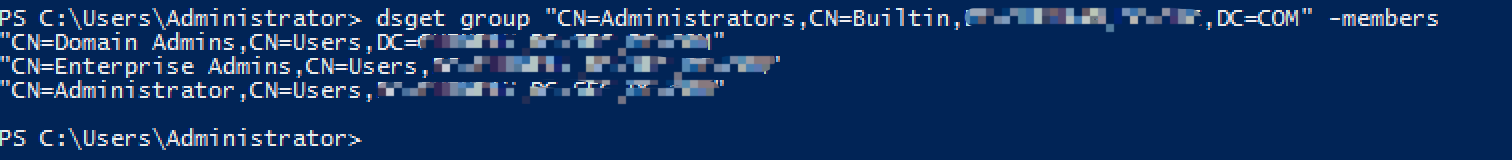
>dsget group "CN=Administrators,CN=Builtin,DC=foo,DC=com" -members

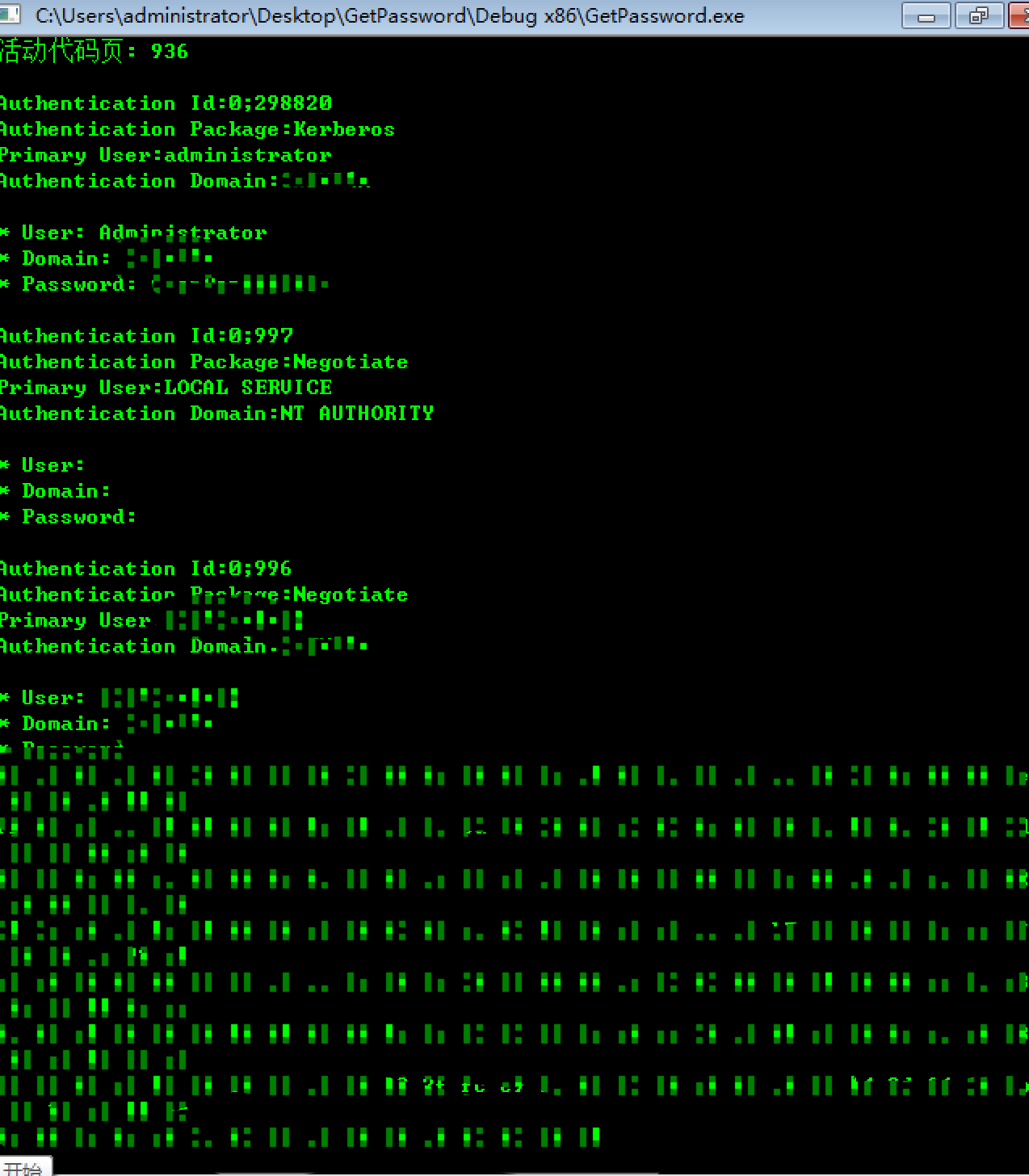
# 抓取认证信息
>.getpassword
2、操作类
#用户的添加、删除、配置权限组(加$符号在最后能起到隐藏效果)、切换用户
>net user pentest 123456 /add
>net localgroup administrators pentest /add
>net user pentest /del
>runas /noprofile /user:administrator [command]
#网络类操作
>netsh interface ip set address name="本地连接" source=static addr=192.168.0.106 mask=255.255.255.0
>netsh interface ip set address name="本地连接" gateway=192.168.0.1 gwmetric=0
>netsh interface ip set dns name="本地连接" source=static addr=114.114.114.114 register=PRIMARY
>netsh interface portproxy add v4tov4 listenport=3340 listenaddress=a.b.c.d connectport=3389 connectaddress=w.x.y.z #端口转发
>netsh advfirewall firewall add rule name=”forwarded_RDPport_3340” protocol=TCP dir=in localip=w.x.y.z localport=3340 action=allow#修改防火墙
>arp -d #清除arp表
#IPC控制类
>net use \ipipc$ [password] /user:[username] #username 和 password均为空的时候建立的空连接
>net use h: \ipc:$
>net view \ip
>net share #查看本地共享
>net share ipc$ [/del]#开启关闭ipc共享
>net share c$ [/del]#开启关闭c共享
二、应急响应类(功能类似的以介绍wmic为主)
1、系统信息类:
>systeminfo
>wmic os
>wmic cpu
>wmic nteventlog #系统事件日志
>wmic computersystem
2、进程、服务类
>tasklist #查看进程
>tasklist | findstr "evil.exe"
>taskkill /f /t /im evil.exe
>wmic process list full
>wmic process get xxx,xxx,xxx
>wmic process where processid="2345" delete #删除进程
>wmic process call create "C:Program FilesTencentQQQQ.exe" #创建进程
>wmic process where name="jqs.exe" get executablepath #查看进程执行路径
>wmic service [list full] [get xxxx,xxxx]
>wmic service where name="xxx" call [startservice | stopservice | pauseservice | delete ]
3、账户、域、工作组类
>wmic useraccount
>wmic sysaccount
>wmic computersystem get domain #查看域工作组
>wmic group
>wmic netlogin #网络登录信息
>wmic logon #登录日志
4、共享、远程、启动项类
>wmic /node:"a.b.c.d /password:"xxxxxx" /user:"administrator" #远程连接对方
>wmic share
>wmic share where name='x$' call delete
>wmic share call create "","xxx","3","TestShareName","","c:xxxxxx",0 #开启共享
>wmic startup list #检查启动项
5、小工具代码
批处理代码,很简单,用作应急响应的快速信息收集,亲测有效
for /F %%i in ('whoami') do ( set commitid=%%i)
set path1=C:Users
set path3=Desktop
set path2=%commitid:~6%
set path4=%path1%%path2%%path3%
set floder=report
set var=%path4%%floder%
mkdir %var%
set path5=info.txt
set var1=%var%%path5%
cd %var%
systeminfo >> info.txt
netstat -abo >> netflow.txt
netstat -abo >> netflow.txt
netstat -abo >> netflow.txt
netstat -abo >> netflow.txt
netstat -abo >> netflow.txt
wmic process list full /format:hform >> process.html
wmic service list full /format:hform >> services.html
wmic useraccount list full /format:hform >> user.html
wmic sysaccount list full /format:hform >> sysaccount.html
wmic group list full /format:hform >> group.html
wmic logon list full /format:hform >> logonlog.html
wmic netlogin list full /format:hform >> netloginlog.html
wmic job list full /format:hform >> job.html