在没有配置任何nginx下,k8s的nginx默认只支持TLS1.2,不支持TLS1.0和TLS1.1
默认的 nginx-config(部分可能叫 nginx-configuration)的配置如下:
apiVersion: v1 data: allow-backend-server-header: 'true' enable-underscores-in-headers: 'true' generate-request-id: 'true' http-redirect-code: '301' ignore-invalid-headers: 'true' max-worker-connections: '65536' proxy-body-size: 20m proxy-connect-timeout: '10' reuse-port: 'true' server-tokens: 'false' ssl-redirect: 'false' worker-cpu-affinity: auto kind: ConfigMap metadata: annotations: kubectl.kubernetes.io/last-applied-configuration: > {"apiVersion":"v1","data":{"allow-backend-server-header":"true","enable-underscores-in-headers":"true","generate-request-id":"true","ignore-invalid-headers":"true","max-worker-connections":"65536","proxy-body-size":"20m","proxy-connect-timeout":"10","reuse-port":"true","server-tokens":"false","ssl-redirect":"false","worker-cpu-affinity":"auto"},"kind":"ConfigMap","metadata":{"annotations":{},"labels":{"app":"ingress-nginx"},"name":"nginx-configuration","namespace":"kube-system"}} labels: app: ingress-nginx name: nginx-configuration namespace: kube-system selfLink: /api/v1/namespaces/kube-system/configmaps/nginx-configuration
看了下官方的文档,如果需要支持TLS1.0和TLS1.1需要改下 nginx-config 同时重启下容器即可
To provide the most secure baseline configuration possible,
nginx-ingress defaults to using TLS 1.2 only and a secure set of TLS ciphers.
The default configuration, though secure, does not support some older browsers and operating systems. For instance, TLS 1.1+ is only enabled by default from Android 5.0 on. At the time of writing, May 2018, approximately 15% of Android devices are not compatible with nginx-ingress's default configuration. To change this default behavior, use a ConfigMap. A sample ConfigMap fragment to allow these older clients to connect could look something like the following:
kind: ConfigMap apiVersion: v1 metadata: name: nginx-config data: ssl-ciphers: "ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA" ssl-protocols: "TLSv1 TLSv1.1 TLSv1.2"
为了避免影响到之前的配置,切勿直接复制这个yaml配置替换你的配置!!!
在你原有的配置上加上 ssl-ciphers 和 ssl-protocols 配置即可
apiVersion: v1 data: allow-backend-server-header: 'true' enable-underscores-in-headers: 'true' generate-request-id: 'true' http-redirect-code: '301' ignore-invalid-headers: 'true' max-worker-connections: '65536' proxy-body-size: 20m proxy-connect-timeout: '10' reuse-port: 'true' server-tokens: 'false' ssl-ciphers: >- ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA ssl-protocols: TLSv1 TLSv1.1 TLSv1.2 ssl-redirect: 'false' worker-cpu-affinity: auto kind: ConfigMap metadata: annotations: kubectl.kubernetes.io/last-applied-configuration: > {"apiVersion":"v1","data":{"allow-backend-server-header":"true","enable-underscores-in-headers":"true","generate-request-id":"true","ignore-invalid-headers":"true","max-worker-connections":"65536","proxy-body-size":"20m","proxy-connect-timeout":"10","reuse-port":"true","server-tokens":"false","ssl-redirect":"false","worker-cpu-affinity":"auto"},"kind":"ConfigMap","metadata":{"annotations":{},"labels":{"app":"ingress-nginx"},"name":"nginx-configuration","namespace":"kube-system"}} labels: app: ingress-nginx name: nginx-configuration namespace: kube-system selfLink: /api/v1/namespaces/kube-system/configmaps/nginx-configuration
加上配置之后呢,需要重启下容器 nginx-ingress
验证,能正常相应即可:
$ curl -v --tlsv1.0 https://test.com $ curl -v --tlsv1.1 https://test.com $ curl -v --tlsv1.2 https://test.com
下图是成功访问的响应:
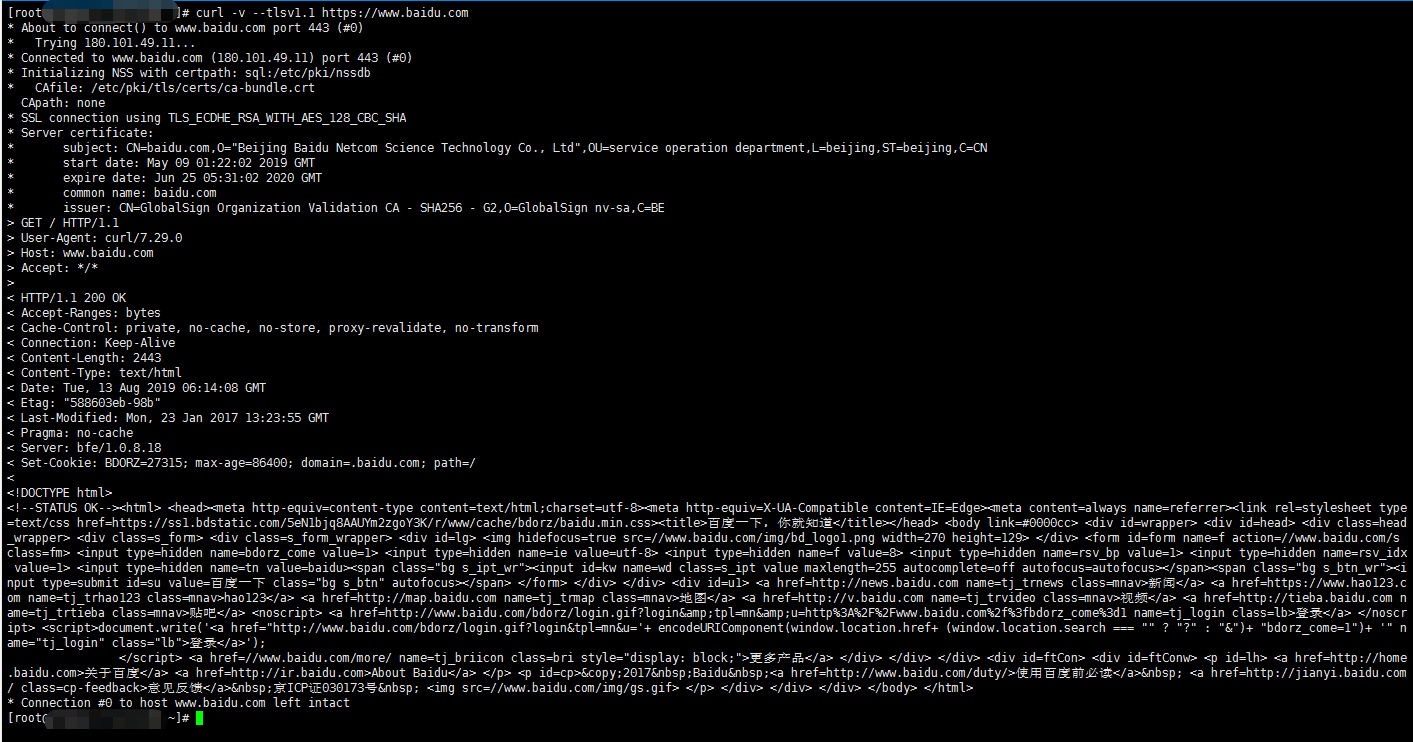
下图是错误的响应:

参考文档:https://kubernetes.github.io/ingress-nginx/user-guide/tls/#legacy-tls