shiro授权和注解式开发
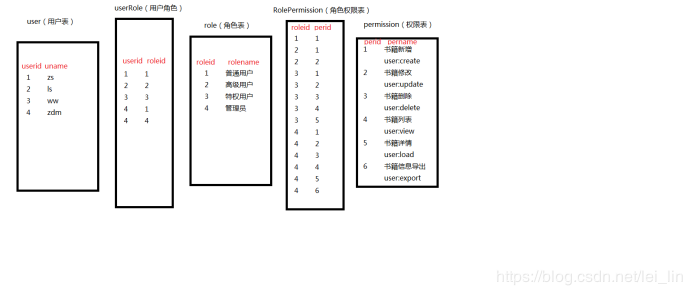
1、shiro授权角色、权限
2、Shiro的注解式开发
ShiroUserMapper.xml
1 <select id="getRolesByUserId" resultType="java.lang.String" parameterType="java.lang.Integer"> 2 select r.roleid from t_shiro_user u,t_shiro_user_role ur,t_shiro_role r 3 where u.userid = ur.userid and ur.roleid = r.roleid 4 and u.userid = #{userid} 5 </select> 6 <select id="getPersByUserId" resultType="java.lang.String" parameterType="java.lang.Integer"> 7 select p.permission from t_shiro_user u,t_shiro_user_role ur,t_shiro_role_permission rp,t_shiro_permission p 8 where u.userid = ur.userid and ur.roleid = rp.roleid and rp.perid = p.perid 9 and u.userid = #{userid} 10 </select>
ShiroUserService
1 /** 2 * 查询角色 3 * @param userid 4 * @return 5 */ 6 Set<String> getRolesByUserId(Integer userid); 7 8 /** 9 * 查询角色权限 10 * @param userid 11 * @return 12 */ 13 Set<String> getPersByUserId(Integer userid);
service实现类
@Override public Set<String> getRolesByUserId(Integer userid) { return shiroUserMapper.getRolesByUserId(userid); } @Override public Set<String> getPersByUserId(Integer userid) { return shiroUserMapper.getPersByUserId(userid); }
重写自定义realm中的授权方法
1 /* 2 授权的方法 3 */ 4 @Override 5 protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principalCollection) { 6 String uname = principalCollection.getPrimaryPrincipal().toString(); 7 ShiroUser shiroUser = this.shiroUserService.queryByName(uname); 8 Set<String> perids = this.shiroUserService.getPersByUserId(shiroUser.getUserid()); 9 Set<String> roleIds = this.shiroUserService.getRolesByUserId(shiroUser.getUserid()); 10 SimpleAuthorizationInfo info = new SimpleAuthorizationInfo(); 11 info.setRoles(roleIds); 12 info.setStringPermissions(perids); 13 return info; 14 15 }
注解式开发
@RequiresUser:表示当前Subject已经身份验证或者通过记住我登录的
@RequiresGuest:表示当前Subject没有身份验证或者通过记住我登录过,即是游客身份
@RequiresRoles(value = {"admin","user"},logical = Logical.AND):表示当前Subject需要角色admin和user
@RequiresPermissions(value = {"user:delete","user:b"},logical = Logical.OR):表示当前Subject需要权限user:delete或者user:b
Controller层
1 @RequiresUser 2 @ResponseBody 3 @RequestMapping("/passUser") 4 public String passUser(){ 5 6 return "身份认证成功,能够访问!!!"; 7 } 8 9 @RequiresRoles(value = {"2","3"}, logical = Logical.OR) //value:不同或者多个的角色,logical:value值的拼接方式可以是AND或者OR 10 @ResponseBody 11 @RequestMapping("/passRole") 12 public String passRole(){ 13 14 return "角色认证成功,能够访问!!!"; 15 } 16 17 @RequiresPermissions(value = {"user:update","user:create"}, logical = Logical.OR) 18 @ResponseBody 19 @RequestMapping("/passPer") 20 public String passPer(){ 21 22 return "权限认证成功,能够访问!!!"; 23 }
springmvc-servlet.xml
1 <bean class="org.springframework.aop.framework.autoproxy.DefaultAdvisorAutoProxyCreator" 2 depends-on="lifecycleBeanPostProcessor"> 3 <property name="proxyTargetClass" value="true"></property> 4 </bean> 5 <bean class="org.apache.shiro.spring.security.interceptor.AuthorizationAttributeSourceAdvisor"> 6 <property name="securityManager" ref="securityManager"/> 7 </bean> 8 9 <bean id="exceptionResolver" class="org.springframework.web.servlet.handler.SimpleMappingExceptionResolver"> 10 <property name="exceptionMappings"> 11 <props> 12 <prop key="org.apache.shiro.authz.UnauthorizedException"> 13 unauthorized 14 </prop> 15 </props> 16 </property> 17 <property name="defaultErrorView" value="unauthorized"/> 18 </bean>
在main.jsp中添加
1 <ul> 2 shiro注解 3 <li> 4 <a href="${pageContext.request.contextPath}/passUser">用户认证</a> 5 </li> 6 <li> 7 <a href="${pageContext.request.contextPath}/passRole">角色</a> 8 </li> 9 <li> 10 <a href="${pageContext.request.contextPath}/passPer">权限认证</a> 11 </li> 12 </ul>
用户zs身份认证,未认证。登录即可访问
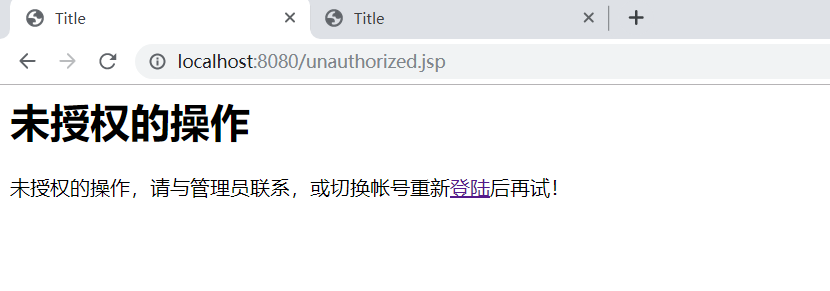
用户ls角色认证,不同角色有不同的访问权限,即使zs登录也不可以访问此页面
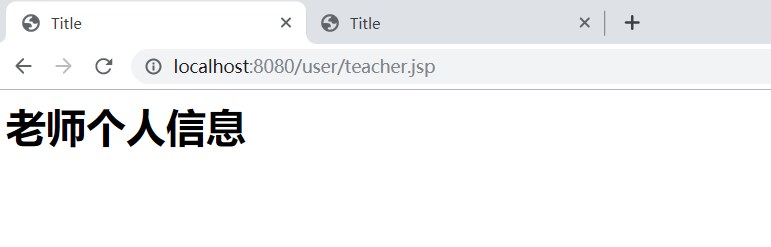
权限认证结果图同上,
从代码来看
@RequiresPermissions(value = {"user:update","user:create"}, logical = Logical.OR)
@ResponseBody
@RequestMapping("/passPer")
public String passPer(){
return "权限认证成功,能够访问!!!";
}
拥有 "user:update","user:create" 这两个权限的即可访问此页面。从顶部的图中可以看出那些用户对应了哪些权限。