这个迷宫多解是没有想到的
放入IDA 有几处 jb jnb 花指令 nop5次就可以了
password1是一个迷宫
***** ***** ****. ****. **s.. *..** ****. ****. ***** ***** *..** *..** ..#*. .***. .***. ***** ***** ***** ***** .**.. ***** **..* *...* ..*.* .**.*
我直接sxss跑过去,没想到flag不是多解
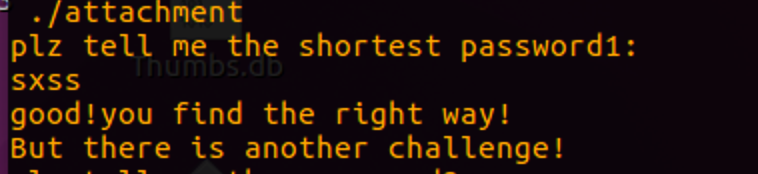
百度了一下傻逼走法 ddwwxxssxaxwwaasasyywwdd 这真能绕我是没有想到的
password2是一个算法处理后和'sctf_9012' 比较 这里看他的处理有 <<6 还有数量为3的if 判断为basedecode
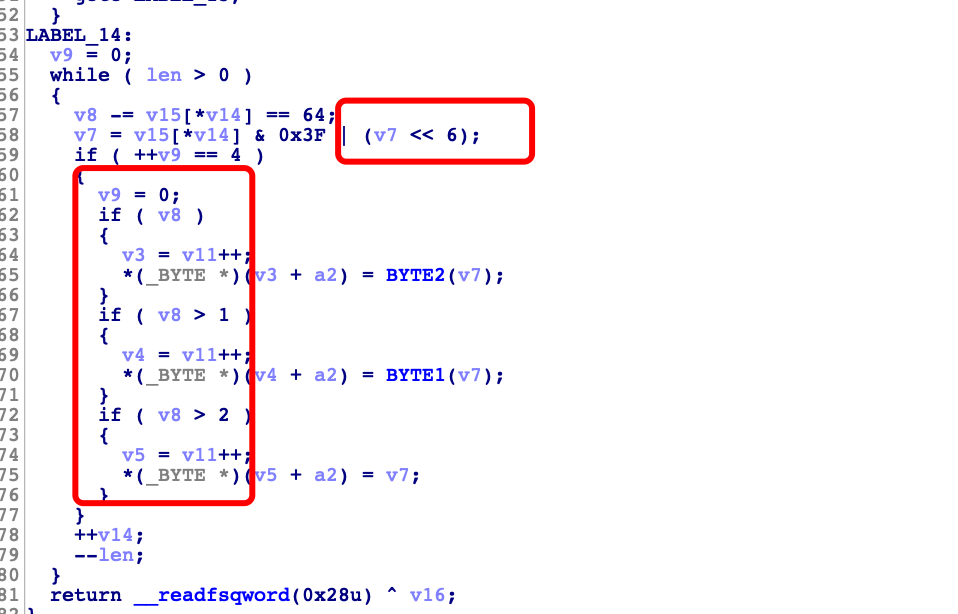
得到password2 c2N0Zl85MTAy
第三部分是一个可逆的加密
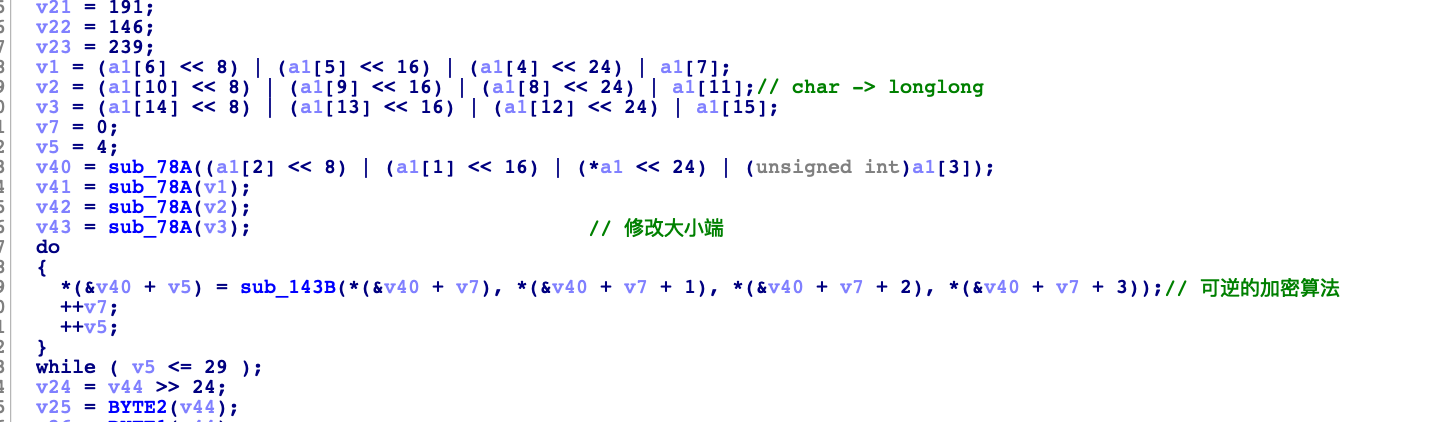
写脚本跑一跑就行了 不过用python实现ROL和ROR的时候 记得&0xffffffff 因为python里面的int不是32bit

k = [] f = open('so.in') for i in range(68): s = f.readline() for j in range(16): if j % 4 == 0: k.append(int(s[j*3:j*3+2],16)) def ROL(x,y): return ((x << y) | (x >> (32 - y))) & 0xffffffff def ROR(x,y): return ((x >> y) | (x << (32 - y))) & 0xffffffff def func2(a1): b1 = a1 & 0xff b2 = (a1 >> 8) & 0xff b3 = (a1 >> 16) & 0xff b4 = (a1 >> 24) & 0xff v1 = (k[b1]) | (k[b2] << 8) | (k[b3] << 16) | (k[b4] << 24) return ROL(v1,12) ^ ROL(v1,8) ^ ROR(v1,2) ^ ROR(v1,6) def func1(a1,a2,a3,a4): return a1 ^ func2(a2 ^ a3 ^ a4) a = [0]*26 a.append(0xBE040680) a.append(0xC5AF7647) a.append(0x9FCC401F) a.append(0xD8BF92EF) for i in range(25,-1,-1): a[i] = func1(a[i+4],a[i+1],a[i+2],a[i+3]) print hex(a[0])[2:].decode('hex')[::-1] print hex(a[1])[2:].decode('hex')[::-1] print hex(a[2])[2:].decode('hex')[::-1] print hex(a[3])[2:].decode('hex')[::-1] # fl4g_is_s0_ug1y!

so.in D6 00 00 00 90 00 00 00 E9 00 00 00 FE 00 00 00 CC 00 00 00 E1 00 00 00 3D 00 00 00 B7 00 00 00 16 00 00 00 B6 00 00 00 14 00 00 00 C2 00 00 00 28 00 00 00 FB 00 00 00 2C 00 00 00 05 00 00 00 2B 00 00 00 67 00 00 00 9A 00 00 00 76 00 00 00 2A 00 00 00 BE 00 00 00 04 00 00 00 C3 00 00 00 AA 00 00 00 44 00 00 00 13 00 00 00 26 00 00 00 49 00 00 00 86 00 00 00 06 00 00 00 99 00 00 00 9C 00 00 00 42 00 00 00 50 00 00 00 F4 00 00 00 91 00 00 00 EF 00 00 00 98 00 00 00 7A 00 00 00 33 00 00 00 54 00 00 00 0B 00 00 00 43 00 00 00 ED 00 00 00 CF 00 00 00 AC 00 00 00 62 00 00 00 E4 00 00 00 B3 00 00 00 1C 00 00 00 A9 00 00 00 C9 00 00 00 08 00 00 00 E8 00 00 00 95 00 00 00 80 00 00 00 DF 00 00 00 94 00 00 00 FA 00 00 00 75 00 00 00 8F 00 00 00 3F 00 00 00 A6 00 00 00 47 00 00 00 07 00 00 00 A7 00 00 00 FC 00 00 00 F3 00 00 00 73 00 00 00 17 00 00 00 BA 00 00 00 83 00 00 00 59 00 00 00 3C 00 00 00 19 00 00 00 E6 00 00 00 85 00 00 00 4F 00 00 00 A8 00 00 00 68 00 00 00 6B 00 00 00 81 00 00 00 B2 00 00 00 71 00 00 00 64 00 00 00 DA 00 00 00 8B 00 00 00 F8 00 00 00 EB 00 00 00 0F 00 00 00 4B 00 00 00 70 00 00 00 56 00 00 00 9D 00 00 00 35 00 00 00 1E 00 00 00 24 00 00 00 0E 00 00 00 5E 00 00 00 63 00 00 00 58 00 00 00 D1 00 00 00 A2 00 00 00 25 00 00 00 22 00 00 00 7C 00 00 00 3B 00 00 00 01 00 00 00 21 00 00 00 78 00 00 00 87 00 00 00 D4 00 00 00 00 00 00 00 46 00 00 00 57 00 00 00 9F 00 00 00 D3 00 00 00 27 00 00 00 52 00 00 00 4C 00 00 00 36 00 00 00 02 00 00 00 E7 00 00 00 A0 00 00 00 C4 00 00 00 C8 00 00 00 9E 00 00 00 EA 00 00 00 BF 00 00 00 8A 00 00 00 D2 00 00 00 40 00 00 00 C7 00 00 00 38 00 00 00 B5 00 00 00 A3 00 00 00 F7 00 00 00 F2 00 00 00 CE 00 00 00 F9 00 00 00 61 00 00 00 15 00 00 00 A1 00 00 00 E0 00 00 00 AE 00 00 00 5D 00 00 00 A4 00 00 00 9B 00 00 00 34 00 00 00 1A 00 00 00 55 00 00 00 AD 00 00 00 93 00 00 00 32 00 00 00 30 00 00 00 F5 00 00 00 8C 00 00 00 B1 00 00 00 E3 00 00 00 1D 00 00 00 F6 00 00 00 E2 00 00 00 2E 00 00 00 82 00 00 00 66 00 00 00 CA 00 00 00 60 00 00 00 C0 00 00 00 29 00 00 00 23 00 00 00 AB 00 00 00 0D 00 00 00 53 00 00 00 4E 00 00 00 6F 00 00 00 D5 00 00 00 DB 00 00 00 37 00 00 00 45 00 00 00 DE 00 00 00 FD 00 00 00 8E 00 00 00 2F 00 00 00 03 00 00 00 FF 00 00 00 6A 00 00 00 72 00 00 00 6D 00 00 00 6C 00 00 00 5B 00 00 00 51 00 00 00 8D 00 00 00 1B 00 00 00 AF 00 00 00 92 00 00 00 BB 00 00 00 DD 00 00 00 BC 00 00 00 7F 00 00 00 11 00 00 00 D9 00 00 00 5C 00 00 00 41 00 00 00 1F 00 00 00 10 00 00 00 5A 00 00 00 D8 00 00 00 0A 00 00 00 C1 00 00 00 31 00 00 00 88 00 00 00 A5 00 00 00 CD 00 00 00 7B 00 00 00 BD 00 00 00 2D 00 00 00 74 00 00 00 D0 00 00 00 12 00 00 00 B8 00 00 00 E5 00 00 00 B4 00 00 00 B0 00 00 00 89 00 00 00 69 00 00 00 97 00 00 00 4A 00 00 00 0C 00 00 00 96 00 00 00 77 00 00 00 7E 00 00 00 65 00 00 00 B9 00 00 00 F1 00 00 00 09 00 00 00 C5 00 00 00 6E 00 00 00 C6 00 00 00 84 00 00 00 18 00 00 00 F0 00 00 00 7D 00 00 00 EC 00 00 00 3A 00 00 00 DC 00 00 00 4D 00 00 00 20 00 00 00 79 00 00 00 EE 00 00 00 5F 00 00 00 3E 00 00 00 D7 00 00 00 CB 00 00 00 39 00 00 00 48 00 00 00 C6 00 00 00 BA 00 00 00 B1 00 00 00 A3 00 00 00 50 00 00 00 33 00 00 00 AA 00 00 00 56 00 00 00 97 00 00 00 91 00 00 00 7D 00 00 00 67 00 00 00 DC 00 00 00 22 00 00 00 70 00 00 00 B2 00 00 00
