部署 helm
curl https://raw.githubusercontent.com/kubernetes/helm/master/scripts/get | bash
查看客户端版本:
helm version
安装 tiller 服务端到 kubernetes 集群:
helm init
查看 tiller 是否启动成功: (镜像有问题的话可以修改镜像地址)
kubectl get pods --namespace=kube-system |grep tiller
tiller-deploy-7b88f7db4-vpxtg 1/1 Running 0 18h
选取该镜像 registry.cn-hangzhou.aliyuncs.com/acs/tiller:v2.14.0
默认安装的 tiller 权限很小,我们执行下面的脚本给它加最大权限,这样方便我们可以用 helm 部署应用到任意 namespace 下:
kubectl create serviceaccount --namespace=kube-system tiller
kubectl create clusterrolebinding tiller-cluster-rule --clusterrole=cluster-admin --serviceaccount=kube-system:tiller
kubectl patch deploy --namespace=kube-system tiller-deploy -p '{"spec":{"template":{"spec":{"serviceAccount":"tiller"}}}}'
报错:
[root@yzsjhl-suanfan-master01 ~]# kubectl top node
Error from server (NotFound): the server could not find the requested resource (get services http:heapster:)
解决:
替换镜像:k8s.gcr.io/metrics-server-amd64:v0.3.1 换为 : registry.aliyuncs.com/google_containers/metrics-server-amd64:v0.3.1
git clone https://github.com/kodekloudhub/kubernetes-metrics-server.git
kubectl create -f kubernetes-metrics-server/
部署 cert-manager
# Install the CustomResourceDefinition resources separately
kubectl apply --validate=false -f https://raw.githubusercontent.com/jetstack/cert-manager/release-0.11/deploy/manifests/00-crds.yaml
# Create the namespace for cert-manager
kubectl create namespace cert-manager
# Add the Jetstack Helm repository
helm repo add jetstack https://charts.jetstack.io
# Update your local Helm chart repository cache
helm repo update
# Install the cert-manager Helm chart
helm install
--name cert-manager
--namespace kube-system
--version v0.11.0
jetstack/cert-manager
$ kubectl get pods -n kube-system |grep cert
cert-manager-cainjector-5dfd7c584d-v9ns5 1/1 Running 0 4d3h
cert-manager-dcbb6f5b9-fb944 1/1 Running 0 5d2h
cert-manager-webhook-f6f965745-rnzq2 1/1 Running 0 5d18h
创建 clusterissuer
$ cat cluster.yaml
apiVersion: v1
items:
- apiVersion: certmanager.k8s.io/v1alpha1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
email: lixinliang@donews.com
http01: {}
privateKeySecretRef:
name: letsencrypt-prod
server: https://acme-v02.api.letsencrypt.org/directory
kind: List
metadata:
resourceVersion: ""
selfLink: ""
$kubectl create -f cluster.yaml
如果有报错: unable to recognize no matches for kind "ClusterIssuer" in version "certmanager.k8s.io/v1alpha1"
执行:
kubectl apply -f https://raw.githubusercontent.com/jetstack/cert-manager/release-0.8/deploy/manifests/00-crds.yaml
$ kubectl get clusterissuer
NAME AGE
letsencrypt-prod 24h
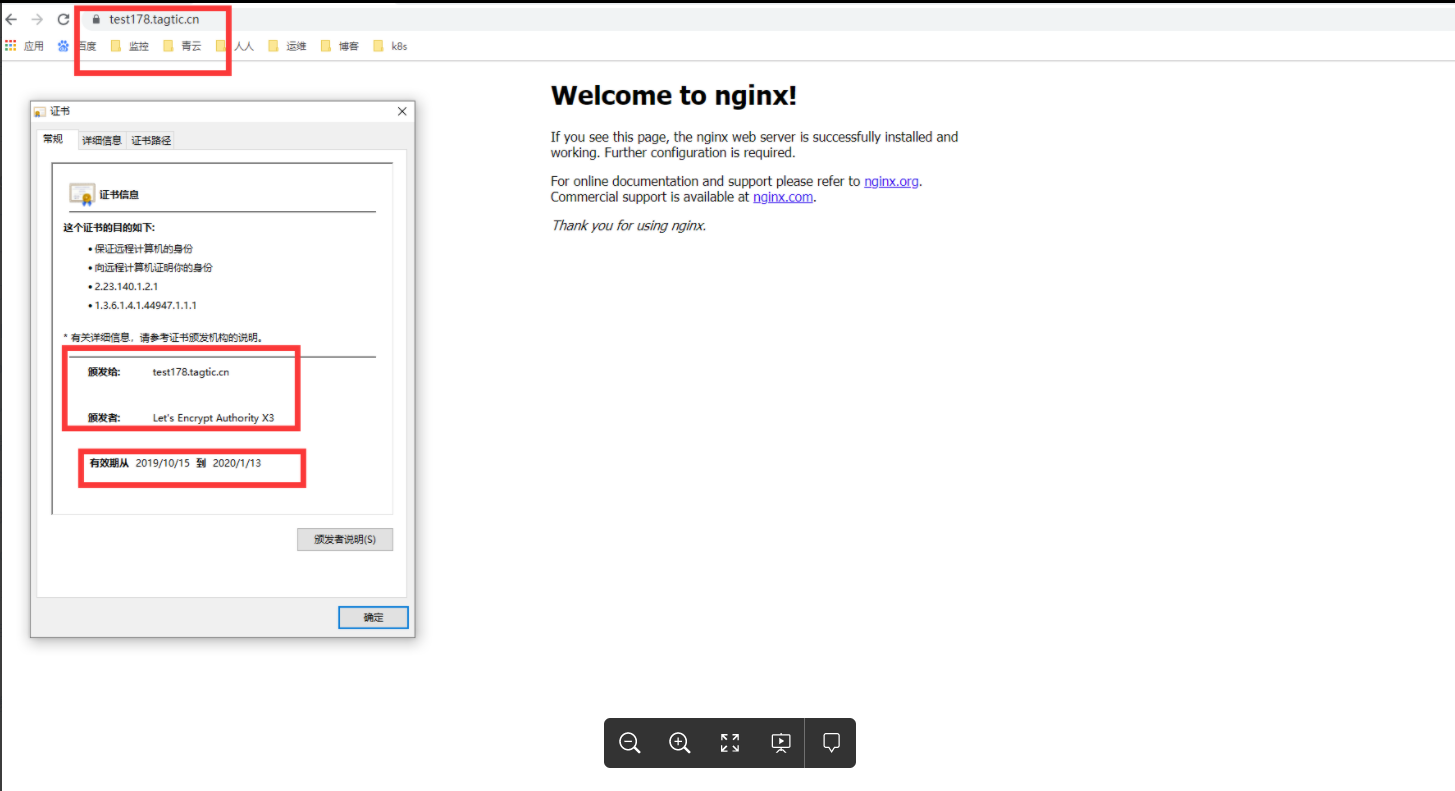
测试 证书: (前提是该域名 test178.tagtic.cn 有公网解析)
$ cat dan-nginx.yaml
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: my-nginx
spec:
replicas: 1
template:
metadata:
labels:
run: my-nginx
spec:
containers:
- name: my-nginx
image: nginx
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: my-nginx
labels:
app: my-nginx
spec:
ports:
- port: 80
protocol: TCP
targetPort: 80
selector:
run: my-nginx
---
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: my-nginx
annotations:
certmanager.k8s.io/cluster-issuer: letsencrypt-prod *重要配置 会生成证书
kubernetes.io/ingress.class: "nginx"
namespace: default
spec:
rules:
- host: test178.tagtic.cn
http:
paths:
- path: '/'
backend:
serviceName: my-nginx
servicePort: 80
tls:
- hosts:
- test178.tagtic.cn
secretName: test178.tagtic.cn
$kubectl create -f dan-nginx.yaml
$ kubectl get certificate
test178.tagtic.cn True test178.tagtic.cn 21h
$ kubectl get secret
test178.tagtic.cn kubernetes.io/tls 3 24h