这个wp 图片可能不太好看 如果需要看清楚的图片访问我的博客 https://www.o2oxy.cn/?p=741
从昨天早上到晚上十二点打了一场红帽杯,贼痛苦,完全被第一名的高中生虐菜啊,打不过打不过,对于我等菜鸡来说真的打不过。
楼上四百队快合并 是我和crazy 和 tllm 两位老哥一起玩的。下面wp 给大家送上
一、icm

直接分析得到idea算法解密 #include "stdafx.h" #include <stdio.h> /* IDEA.h */ #ifndef IDEA_H #define IDEA_H /* define return status */ #define IDEA_SUCCESS 0 #define IDEA_ERROR 1 /* define data length */ #define IDEA_KEY_LEN 128 #define IDEA_BLOCK_SIZE 64 #define IDEA_SUB_BLOCK_SIZE 16 /* define global variable */ #define IDEA_ADD_MODULAR 65536 #define IDEA_MP_MODULAR 65537 /* define operation mode */ #define ECB 0 #define CBC 1 #define CFB 2 #define OFB 3 /* define data type */ //typedef bool bit_t, status_t; typedef unsigned char byte_t, uint8_t; typedef unsigned short word_t, uint16_t; typedef unsigned int dword_t, uint32_t, status_t; typedef unsigned long long uint64_t; /* declare fuction */ status_t idea_encrypt(uint64_t plaintext, uint16_t key[8], uint64_t *ciphertext); status_t idea_decrypt(uint64_t ciphertext, uint16_t key[8], uint64_t *plaintext); status_t idea_round(uint16_t X[4], uint16_t Z[6], uint16_t out[4]); status_t MA(uint16_t ma_in[2], uint16_t sub_key[2], uint16_t ma_out[2]); status_t subkey_generation(uint16_t key[8], uint16_t sub_key[52]); status_t subdkey_generation(uint16_t key[8], uint16_t sub_dkey[52]); status_t extended_eucild(uint16_t d, uint32_t k, uint32_t *result); #endif /* define operation */ static uint16_t add_mod(uint16_t a, uint16_t b); static uint16_t mp_mod(uint16_t a, uint16_t b); static uint16_t XOR(uint16_t a, uint16_t b); static status_t left_shift(uint16_t key[8], int num); static void swap(uint16_t *a, uint16_t *b); /* addition and mod 65536 */ static uint16_t add_mod(uint16_t a, uint16_t b) { uint32_t tmp = a + b; uint16_t ret = tmp % IDEA_ADD_MODULAR; return ret; } /* multiply and mod 65537 */ static uint16_t mp_mod(uint16_t a, uint16_t b) { /* Note: In IDEA, for purposes of multiplication, a 16 bit word containing all zeroes is considered to represent the number 65,536; * other numbers are represented in conventional unsigned notation, and multiplication is modulo the prime number 65,537 */ uint64_t tmp, tmp_a, tmp_b; //if both a and b are 2^16, the result will be 2^32 which will exceed a 32-bit int tmp_a = a == 0 ? (1 << 16) : a; tmp_b = b == 0 ? (1 << 16) : b; tmp = (tmp_a * tmp_b) % IDEA_MP_MODULAR; return (uint16_t)(tmp); } /* XOR */ static uint16_t XOR(uint16_t a, uint16_t b) { return a^b; } static void swap(uint16_t *a, uint16_t *b) { uint16_t c = 0; c = *a; *a = *b; *b = c; } /* IDEA encryption */ status_t idea_encrypt(uint64_t plaintext, uint16_t key[8], uint64_t *ciphertext) { uint16_t X[4], sub_key[52], out[4]; status_t st; int i, j; /* cut 64-bit plaintext into 4 16-bit sub blocks */ for (i = 0; i < 4; i++) X[i] = (plaintext >> (48 - i * 16)) & 0xffff; /* generate sub keys */ st = subkey_generation(key, sub_key); for (i = 0; i < 8; i++) { idea_round(X, &(sub_key[i * 6]), out); for (j = 0; j < 4; j++) X[j] = out[j]; } /* round 9, do output transform */ //Note that the swap of B and C is not performed after round 8. So we swap them again. swap(&(out[1]), &(out[2])); out[0] = mp_mod(out[0], sub_key[48]); out[1] = add_mod(out[1], sub_key[49]); out[2] = add_mod(out[2], sub_key[50]); out[3] = mp_mod(out[3], sub_key[51]); *ciphertext = out[0]; for (i = 1; i <= 3; i++) *ciphertext = ((*ciphertext) << 16) | out[i]; return st; } /* IDEA decryption */ status_t idea_decrypt(uint64_t ciphertext, uint16_t key[8], uint64_t *plaintext) { status_t st; uint16_t X[4], sub_dkey[52], out[4]; int i, j; for (i = 0; i < 4; i++) X[i] = (ciphertext >> (48 - i * 16)) & 0xffff; /* generate sub keys for decryption*/ st = subdkey_generation(key, sub_dkey); if (st != IDEA_SUCCESS) return st; for (i = 0; i < 8; i++) { idea_round(X, &(sub_dkey[i * 6]), out); for (j = 0; j < 4; j++) X[j] = out[j]; } out[0] = mp_mod(out[0], sub_dkey[48]); out[1] = add_mod(out[1], sub_dkey[49]); out[2] = add_mod(out[2], sub_dkey[50]); out[3] = mp_mod(out[3], sub_dkey[51]); swap(&(out[1]), &(out[2])); //Note that the unswap in decryption is called after transform, that is different from the encryption. *plaintext = out[0]; for (i = 1; i <= 3; i++) *plaintext = ((*plaintext) << 16) | out[i]; return st; } status_t idea_round(uint16_t X[4], uint16_t Z[6], uint16_t out[4]) { status_t st; uint16_t tmp[4], ma_in[2], ma_out[2]; tmp[0] = mp_mod(X[0], Z[0]); //step 1. multiply X1 by 1st sub key tmp[1] = add_mod(X[1], Z[1]); //step 2. add X2 to 2nd sub key tmp[2] = add_mod(X[2], Z[2]); //step 3. add X3 to 3rd sub key tmp[3] = mp_mod(X[3], Z[3]); //step 4. multiply X4 by 4th sub key ma_in[0] = XOR(tmp[0], tmp[2]); //step 5. XOR results in step 1 and step 3 ma_in[1] = XOR(tmp[1], tmp[3]); //step 6. XOR results in step 2 and step 4 st = MA(ma_in, &Z[4], ma_out); //step 7. MA diffusion /* step 8. generate the output*/ out[0] = XOR(tmp[0], ma_out[1]); out[1] = XOR(tmp[1], ma_out[0]); out[2] = XOR(tmp[2], ma_out[1]); out[3] = XOR(tmp[3], ma_out[0]); swap(&(out[1]), &(out[2])); return st; } /* MA diffusion */ status_t MA(uint16_t ma_in[2], uint16_t sub_key[2], uint16_t ma_out[2]) { uint16_t tmp[2]; tmp[0] = mp_mod(ma_in[0], sub_key[0]); tmp[1] = add_mod(ma_in[1], tmp[0]); ma_out[1] = mp_mod(tmp[1], sub_key[1]); ma_out[0] = add_mod(tmp[0], ma_out[1]); return IDEA_SUCCESS; } /* sub keys generation */ status_t subkey_generation(uint16_t key[8], uint16_t sub_key[52]) { int i, j; uint16_t tmp_key[8]; for (i = 0; i < 8; i++) tmp_key[i] = key[i]; for (i = 0; i < 6; i++) { for (j = 0; j < 8; j++) sub_key[i * 8 + j] = tmp_key[j]; left_shift(tmp_key, 25); } for (i = 0; i < 4; i++) sub_key[48 + i] = tmp_key[i]; return IDEA_SUCCESS; } /* sub dkeys generation * *The decryption key schedule is: * *The first four subkeys for decryption are: * *KD(1) = 1/K(49) *KD(2) = -K(50) *KD(3) = -K(51) *KD(4) = 1/K(52) * *and they do not quite follow the same pattern as the remaining subkeys which follow. * *The following is repeated eight times, adding 6 to every decryption key's index and subtracting 6 from every encryption key's index: * *KD(5) = K(47) *KD(6) = K(48) * *KD(7) = 1/K(43) *KD(8) = -K(45) *KD(9) = -K(44) *KD(10) = 1/K(46) * */ status_t subdkey_generation(uint16_t key[8], uint16_t sub_dkey[52]) { status_t st; int i; uint16_t sub_key[52]; uint32_t tmp; st = subkey_generation(key, sub_key); st = extended_eucild(sub_key[48], IDEA_MP_MODULAR, &tmp); if (st != IDEA_SUCCESS) { printf("subdkey_generation error!/n"); return st; } sub_dkey[0] = tmp == 65536 ? 0 : (uint16_t)tmp; sub_dkey[1] = (IDEA_ADD_MODULAR - sub_key[49]) % IDEA_ADD_MODULAR; sub_dkey[2] = (IDEA_ADD_MODULAR - sub_key[50]) % IDEA_ADD_MODULAR; st = extended_eucild(sub_key[51], IDEA_MP_MODULAR, &tmp); if (st != IDEA_SUCCESS) { printf("subdkey_generation error!/n"); return st; } sub_dkey[3] = tmp == 65536 ? 0 : (uint16_t)tmp; for (i = 0; i < 8; i++) //This is awful?!...May be I should make a table. { sub_dkey[4 + i * 6] = sub_key[52 - (i + 1) * 6]; sub_dkey[4 + i * 6 + 1] = sub_key[52 - (i + 1) * 6 + 1]; st = extended_eucild(sub_key[52 - (i + 1) * 6 - 4], IDEA_MP_MODULAR, &tmp); if (st != IDEA_SUCCESS) { printf("subdkey_generation error!/n"); return st; } sub_dkey[4 + i * 6 + 2] = tmp == 65536 ? 0 : (uint16_t)tmp; sub_dkey[4 + i * 6 + 3] = (IDEA_ADD_MODULAR - sub_key[52 - (i + 1) * 6 - 2]) % IDEA_ADD_MODULAR; sub_dkey[4 + i * 6 + 4] = (IDEA_ADD_MODULAR - sub_key[52 - (i + 1) * 6 - 3]) % IDEA_ADD_MODULAR; st = extended_eucild(sub_key[52 - (i + 1) * 6 - 1], IDEA_MP_MODULAR, &tmp); if (st != IDEA_SUCCESS) { printf("subdkey_generation error!/n"); return st; } sub_dkey[4 + i * 6 + 5] = tmp == 65536 ? 0 : (uint16_t)tmp; } return IDEA_SUCCESS; } /* left shift */ static status_t left_shift(uint16_t key[8], int num) { uint16_t copy_key[8]; int i; for (i = 0; i < 8; i++) copy_key[i] = key[i]; for (i = 0; i < 8; i++) key[i] = (copy_key[(i + num / 16) % 8] << (num % 16)) | (copy_key[(i + num / 16 + 1) % 8] >> (16 - num % 16)); return IDEA_SUCCESS; } /* Extended Eucild Algorithm to caculate d^-1 mod k*/ status_t extended_eucild(uint16_t d, uint32_t k, uint32_t *result) { int x[4], y[4], t[4], q; int i; x[1] = x[2] = 0; x[3] = k; y[1] = 0, y[2] = 1; y[3] = d == 0 ? (1 << 16) : d; while (y[3] > 1) { q = x[3] / y[3]; for (i = 1; i <= 3; i++) t[i] = x[i] - q*y[i]; for (i = 1; i <= 3; i++) x[i] = y[i]; for (i = 1; i <= 3; i++) y[i] = t[i]; } if (y[3] == 1) { if (y[2] < 0) y[2] += k; *result = y[2]; return IDEA_SUCCESS; } else return IDEA_ERROR; }
通过加密函数的分组、及具体算法里的swap,mul,add,看出是idea算法。
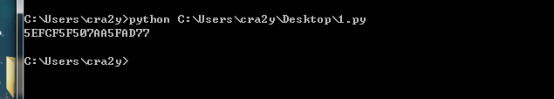
直接dump伪随机数生成的key(hex):18fe9c970a7296f5c2fdeeae147592aa。
通过异或得到加密串
af91d8edba0928255a8d815a3e2d065521afbcd426617f8db44298d5ce7c24423faf66cdbd551fd6caded815f7d33b3c
直接找工具来解密。去掉尾部 得到flag
https://blog.csdn.net/bobozhangyx/article/details/52246235
flag{f53fc1db-b7d3-4643-9b48-725f13129d07}
二、Not only Wireshark
流量包。。。
一开始以为是常规套路,导出图片什么的。后来那个hacker图片没什么用。以为是那个ico的图片。。试了各种图片的套路,也无果。最后看到了底下有个奇怪的东西
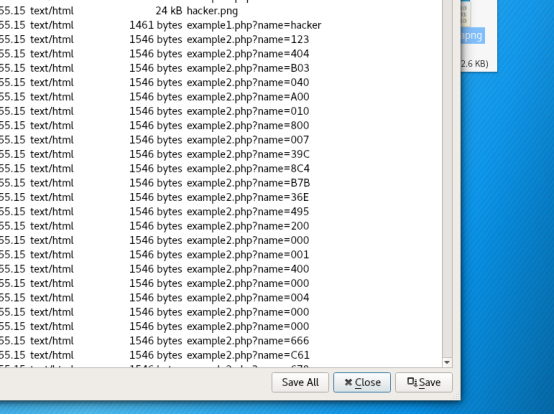
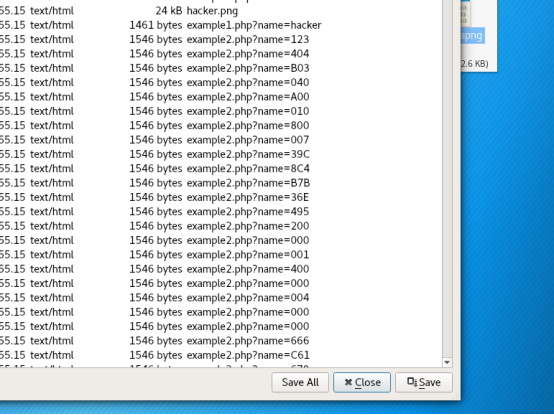
123404B03040A00,如果1234换成5 就是504B0304了。。zip的文件头。。顺序保存了下,发现真的是。但是是加密的压缩包。。卡住了。。最后队友说有个地方感觉可以试试
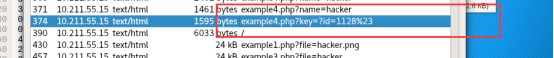
结果发现压缩包密码为这个。。 ?id=1128%23
得出flag
flag{1m_s0_ang4y_1s}
不得不说。。真的脑洞。。。。
三、game server
说下思路: name 输入 255字符 nobel输入255字符 然后修改introduction 可以栈溢出泄露函数地址找到对应的libc 计算system地址 然后再次栈溢出getshell
写了一个py

连接
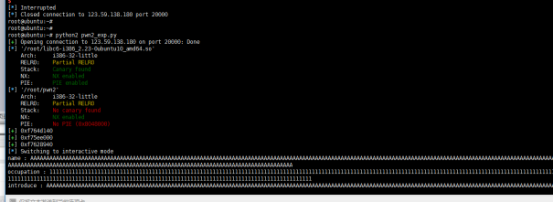
Flag :/home/pwn2/flag.txt

四、这是道web题?
看到这个题目的时候刷刷的打开,竟然发现。这么多数据包怎么分析? 我擦我擦,算了一个个看吧。好像跟Not Only Wireshark 差不多的样子,但是想了下,看看呗
找了差不多半小时终于发现了点线索
78466550-3fc1-11e8-9828-32001505e920.pcapng
这个数据包中,有一个POST请求。看了下

有一个木马文件。继续往下看,
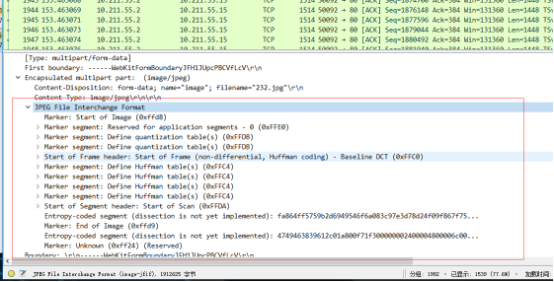
还有一张图片,那么就把图片导出来吧

但是看了一下大小,我擦 1.82MB 发现不对,那就分析一波吧
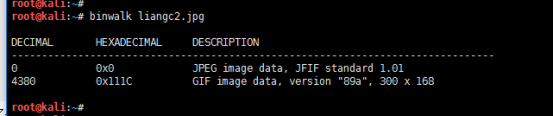
发现一个gif 文件
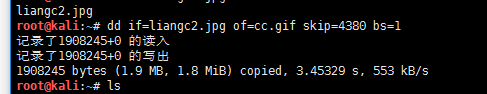
弄出来得到一个动态图片

有意思。有意思
得到url flag
flag{S022y4orr5}
五、biubiubiu
发现有文件包含,可以看文件。想了一下,百度了一下log的路径,读取到了log。
会读取我的UA。修改UA成一句话,成功写入。

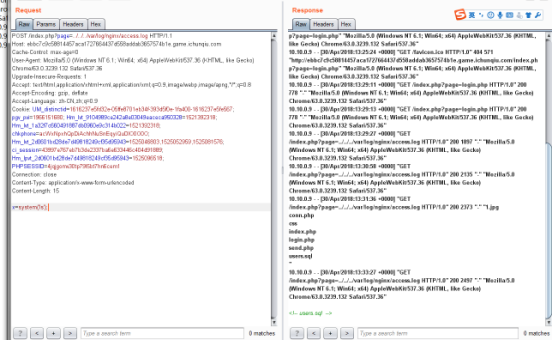
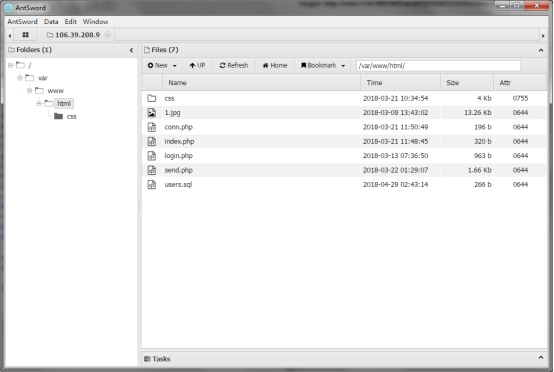
看了一下conn.php 有数据库用户,试了半天,发现密码为空。连上数据库拿到flag


六、shopping log
shopping log访问题目所给url,一片空白,查看源码得到host,访问之后无果。后将http头中的host改为www.tmvb.com。访问后得到

将Referer改为那个域名,302到了一个错误页面,提示只能从日本访问。Ok,明朗了!
头里面xff,把Accept-Language改为Ja,可以被正常显示。看了一下,爆破呗!
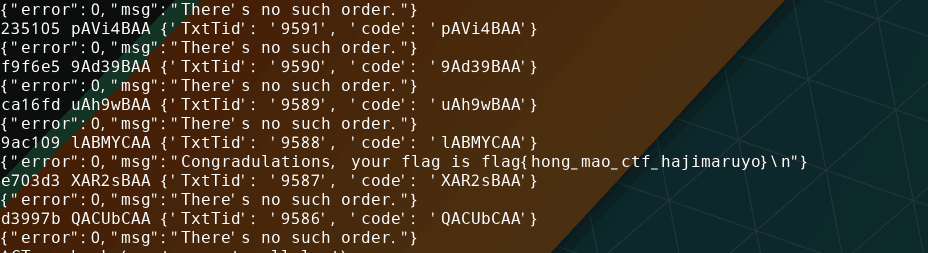
刚开始从0000开始爆,发现真鸡儿慢。想想hint,从9999倒数着爆。Getflag脚本如下:
import requests import proofofwork session = requests.session() headers={"Referer":"www.dww.com", "Accept-Language":"Ja", "Host":"www.tmvb.com"} session.headers = headers for _ in range(9999,0,-1): body = str(session.get('http://120.132.95.234/').text) yzm = body[body.find("=== '")+5:body.find("=== '")+5+6] n = proofofwork.md5(str(yzm)).decode('ascii') data={"TxtTid":"%04d" % _,"code":n} print(yzm,n,data) r = session.post("http://120.132.95.234/api.php?action=report", data=data) print(r.text)
七、simple upload
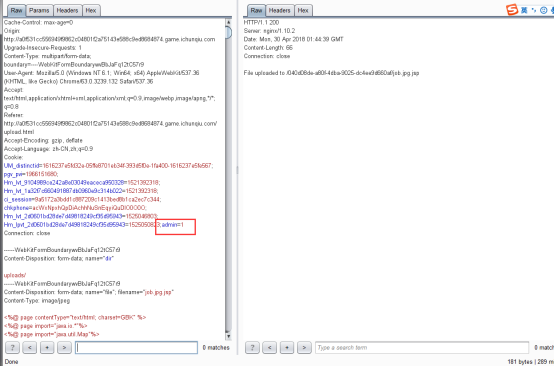
感觉没啥好说的-.-,解析jsp。抓包上传图片,admin=0改成admin=1。得到webshell。然后在根目录发现flag
八、手工爆破
Emmmm。真是全是脑洞
Linux打开这个iso发现有个压缩包和一堆txt,有密码。题目说手工爆破。看了下txt里面的base64不对。。。对比了下md5,都是一样的md5,估计是随机生成的。
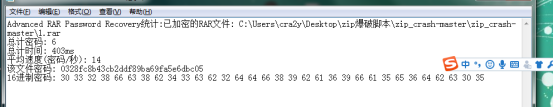
试了一下文件名作为密码。。没对。。想了一下,所有文件名保存一份作为字典,爆破rar。得到zip密码。
得到个docx,各种尝试了。。爆破也无果。。百度找到个
得到了一段神奇的加密。。
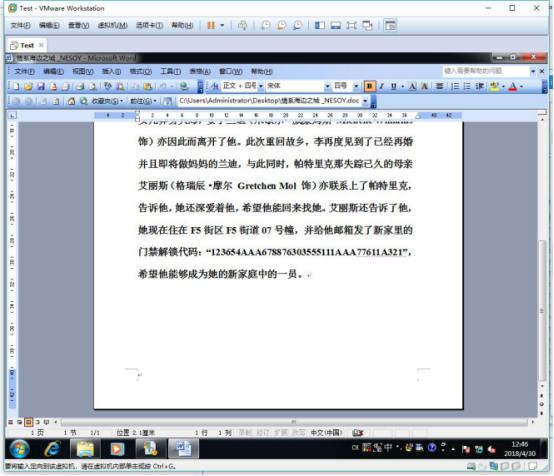
看了一下名字 应该是曼彻斯特密码。用脚本跑了一下。得出了flag