微软今天发布一个紧急补丁KB958644 安全公告 MS08-067 这是一个RPC服务的漏洞,仅仅需要对方客户端开放139,445端口即可远程获得管理员权限。极其类似于冲击波病毒利用的漏洞,主要影响XP和2003,下载地址:http://www.microsoft.com/downloads/details.aspx?displaylang=zh-cn&FamilyID=0d5f9b6e-9265-44b9-a376-2067b73d6a03
一个叫Gimmiv.A 的蠕虫病毒已经开始利用此漏洞进行传播:
Critical vulnerability in Server Service has only been patched by Microsoft (MS08-067), as a new worm called Gimmiv.A has found to be exploiting it in-the-wild.
Once executed, the worm will drop 3 files: winbase.dll, basesvc.dll and syicon.dll into the directory %System%\Wbem\basesvc.dll.
It will then install and start up a new service called BaseSvc with the display name "Windows NT Baseline". The service BaseSvc will force svchost.exe to load the DLL winbase.dll which is specified as a ServiceDll parameter for BaseSvc.
Once loaded, winbase.dll will load 2 additional DLLs into the address space of the system process services.exe: basesvc.dll and syicon.dll.
After dropping and loading the aforementioned DLLs, the worm will collect system information from the compromised computer, collect passwords from the Windows protected storage and Outlook Express passwords cache, and post collected details to a remote host. The details are posted in an encrypted form, by using AES (Rijndael) encryption.
The collected information seems to specify if the following AV products are found to be installed on the compromised system:
- BitDefender Antivirus
- Jiangmin Antivirus
- Kingsoft Internet Security
- Kaspersky Antivirus
- Microsoft's OneCare Protection
- Rising Antivirus
- Trend Micro
Details collected by Gimmiv.A are then posted to a personal profile of the user "perlbody", hosted with http://www.t35.com hosting provider. At this time, the collected details are displayed at this link.
At the time of this writing, there are 3,695 entries in that file. Every line contains an encrypted string, which could potentially conceal current victims' details, indirectly indicating how many victims have been compromised by this worm so far.
The worm also fetches a few files from the following locations:
- http://summertime.1gokurimu.com
- http://perlbody.t35.com
- http://doradora.atzend.com
One of the downloaded files is a GIF image shown below:
![]()
The most interesting part of this worm is implemented in the DLL basesvc.dll. This DLL is responsible for the network propagation of the worm.
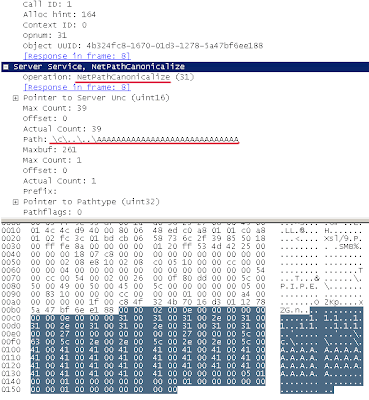
It starts from probing other IPs from the same network by sending them a sequence of bytes "abcde" or "12345". The worm then attempts to exploit other machines by sending them a malformed RPC request and relying on a vulnerable Server service. As known, Server service uses a named pipe SRVSVC as its RPC interface, which is registered with UUID equal to 4b324fc8-1670-01d3-1278-5a47bf6ee188. In order to attack it, the worm firstly attempts to bind SRVSVC by constructing the following RPC request:

Next, Gimmiv.A submits a maliciously crafted RPC request that instructs SRVSVC to canonicalize a path "\c\..\..\AAAAAAAAAAAAAAAAAAAAAAAAAAAAA" by calling the vulnerable RPC request NetPathCanonicalize, as shown in the traffic dump below (thanks to Don Jackson from SecureWorks for the provided dump):
As this is a critical exploit, Microsoft strongly recommends that users apply the update referred to in Security Bulletin MS08-067 immediately.